SSO / OIDC ?
-
Looks like there is some kind of support at least for okta https://cal.com/docs/how-to-guides/how-to-setup-oidc-with-okta
Not quite sure what the extra saml database requirement is though. If anyone has better links on OpenID support, would be welcome.
-
a little above my pay grade to make an educated comment here

https://cal.com/docs/introduction/quick-start/self-hosting/sso-setup
-
Hey there. Worked on Cal.com for a while, see my Cloudron Forum username be picked up in the updates of the package here https://forum.cloudron.io/topic/9924/cal-com-package-updates as I'm using the same username as GitHub

Here is the SSO docs just in case, https://cal.com/docs/introduction/quick-start/self-hosting/sso-setup
-
Also, I'm pretty sure that to be able to use SSO you need a license: https://cal.com/enterprise
-
@SadieHintz said in SSO / OIDC ?:
Absolutely! The inclusion of SSO and OIDC in the upstream Docker image is a promising development. Implementing these features would indeed enhance user experience, security, and overall accessibility. It's a great consideration for improving the platform.
The Cloudron Outline app already has OIDC included:
-
The SSO docs are in the Self Sosting Quickstart section of the docs and doesn't say anything about being enterprise only. The instructions looks pretty simple; quoted with edits:
Setting up OIDC login
- Set SAML_DATABASE_URL to a Postgres database. Please use a different database than the main Cal instance since the migrations are separate for this database. (snip)
- Set SAML_ADMINS to a comma separated list of admin emails who can configure the OIDC.
- Keep handy the Client Secret, Client ID and Well Known URL with you for the next step.
- Spin up cal.com on your server and login with the Admin user (the email ID of which was provided in step 2 for SAML_ADMINS environment variable).
- Visit {BASE_URL}/settings/security/sso
- Click on Configure SSO with OIDC, and then enter the Client Secret, Client ID and Well known URL from the Step 3, and click save.
- That's it.
The only thing that gives me pause is that it's asking for a separate Postgres database connection info, and I'm not sure if cloudron is able to do that. Maybe we can make the main app db and saml db use different pg schemas?
(Side note: the fact that the only way to configure OIDC and SAML through the web ui is... insane. Their OIDC E2E test scenario literally scripts the settings page to enter credentials; there's no way to configure it automatically 🤯
 )
) -
doesn't say anything about being enterprise only
Oh
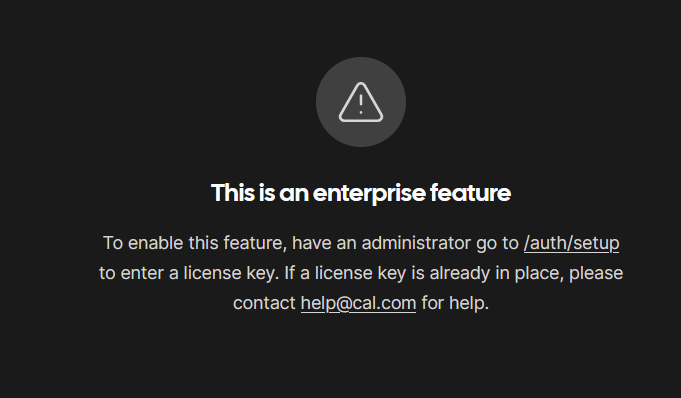
Nevermind then.
As far as the trick for an app that needs multiple pg databases, I think creating multiple schemas might work depending on if the db library used by the app supports setting the schema in the url or otherwise. Support for this feature seems patchy.
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login