[💡 Guide] How to move Nextcloud to an encrypted volume
-
Hi folks, I am playing with Nextcloud some more and wanted to move an app to an encrypted volume without the root volume being encrypted. Please see my other post on how to encrypt the entire Cloudron. I'm sharing this with you in case you find it useful and look forward to your comments.
*** This guide comes without warranties and is not supported by Cloudron - Caveat emptor! ***
Step 1: Install cryFS
See https://www.cryfs.org/tutorial for more details on this awesome Open Source project. I have chosen it because of how easy and lightweight it is. Let me know which other ways you have tried or can recommend.
sudo apt update && sudo apt install cryfsStep 2: Create a folder and mount it
In this example, I am creating the place where the data is actually stored in /root/baseDir and mount it to /mnt/nextcloud
You can choose what ever suits your needs and if the baseDir folder is not already in existence it will prompt you to have it created.
sudo cryfs /root/baseDir /mnt/nextcloud -o allow_otherStep 3: Create a sub-folder to store your data in
The reason for this is because we cannot set permissions the way we need to on the mount's root folder.
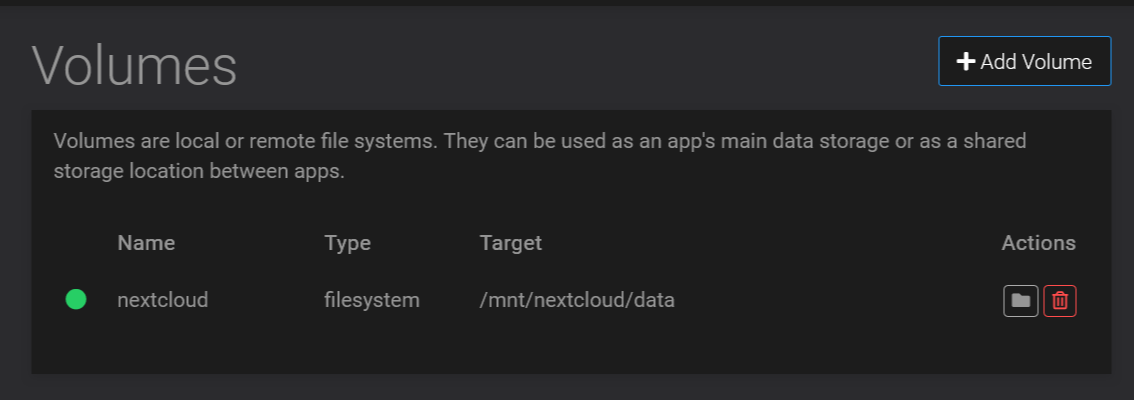
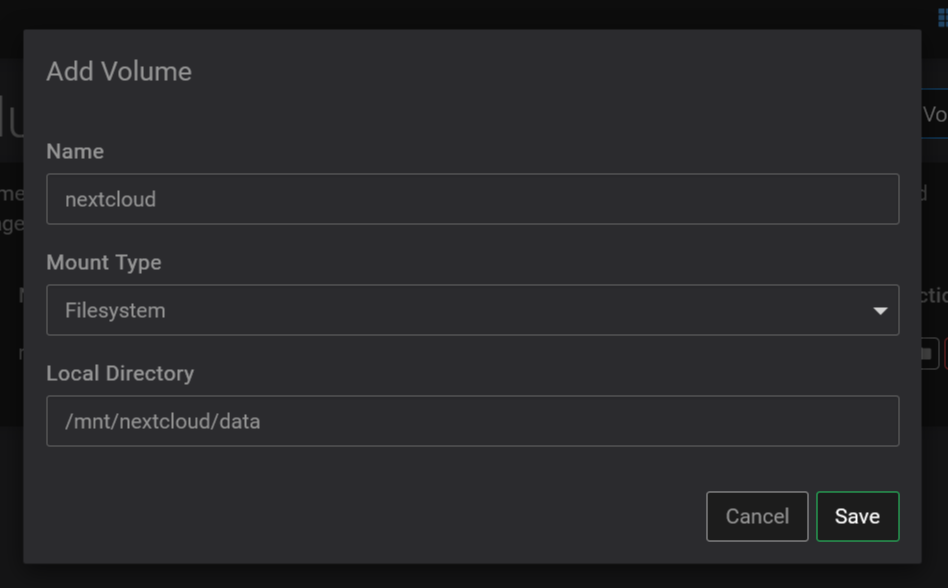
sudo mkdir /mnt/nextcloud/data && sudo chown -R yellowtent:yellowtent /mnt/nextcloud/dataStep 4: Add the volume to Cloudron
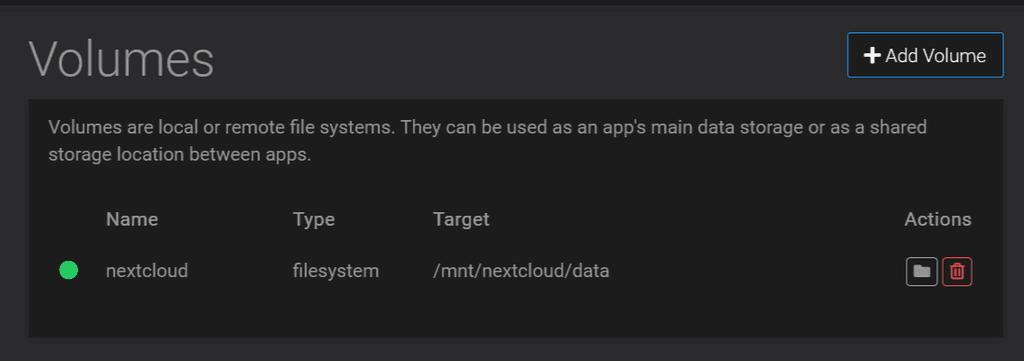
https://your.cloudron.cloud/#/volumesThen add your volume using the 'Filesystem' mount type and full path to /mnt/nextcloud/data
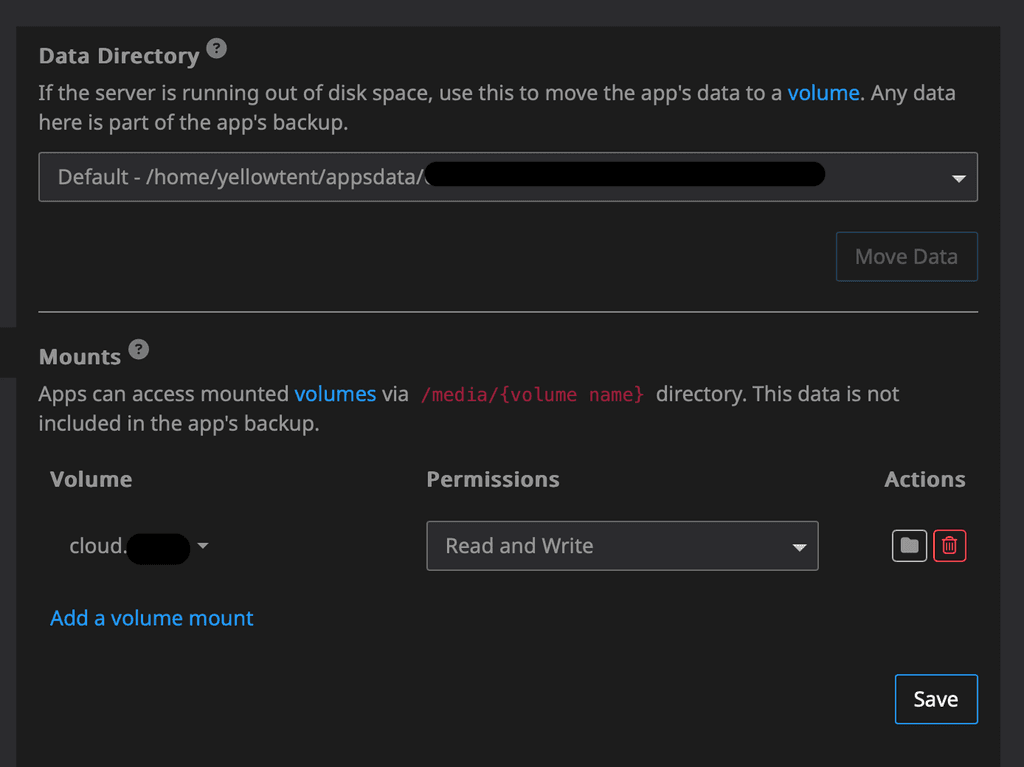
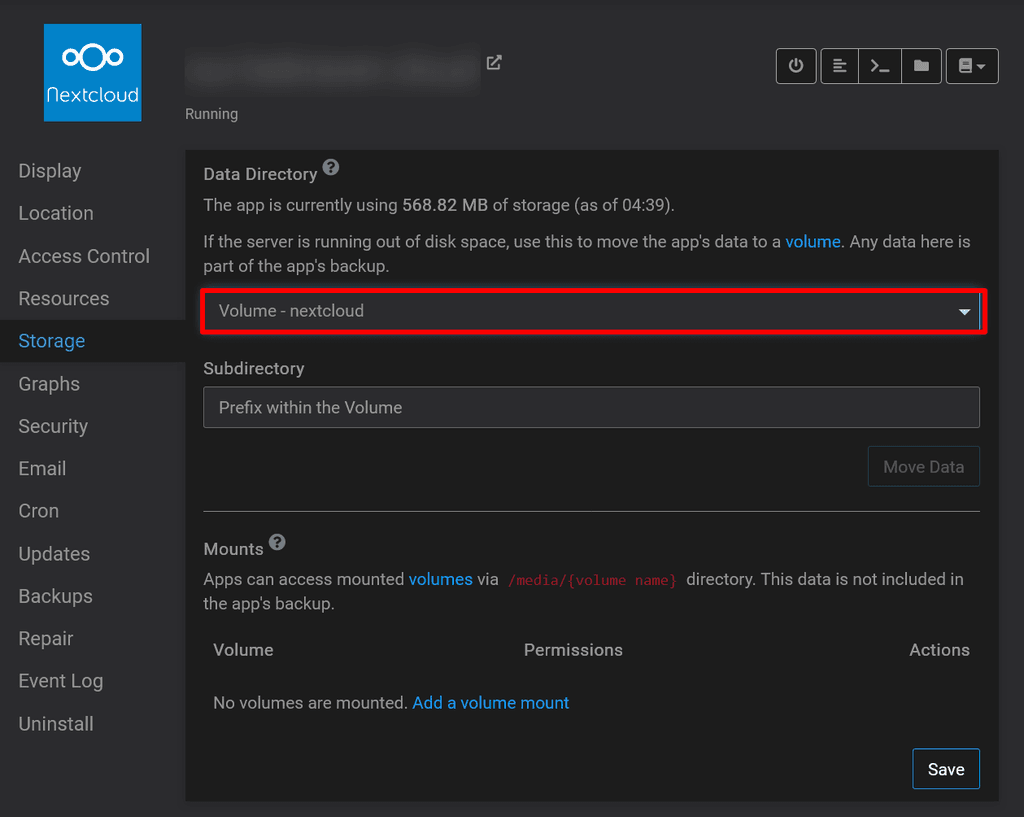
Step 5: Move your Nextcloud app's data directory
Go to Settings, then Storage for your app and select the volume we created from the dropdown. Hit move and get yourself a cup of tea

Notes:
- Content will be included in your backups
- You will manually need to mount this volume using the same command as in Step 2 when you restart your Cloudron!
- This will not protect you from anyone who has root access to your server or to your Nextcloud app. It just encrypts data at rest.
- Make sure to stop the Nextcloud app before you reboot and disable automatic reboots
Let me know what you think about this approach and how you keep your Nextcloud secure

-
 3 3246 referenced this topic on
3 3246 referenced this topic on
-
Hi folks, I am playing with Nextcloud some more and wanted to move an app to an encrypted volume without the root volume being encrypted. Please see my other post on how to encrypt the entire Cloudron. I'm sharing this with you in case you find it useful and look forward to your comments.
*** This guide comes without warranties and is not supported by Cloudron - Caveat emptor! ***
Step 1: Install cryFS
See https://www.cryfs.org/tutorial for more details on this awesome Open Source project. I have chosen it because of how easy and lightweight it is. Let me know which other ways you have tried or can recommend.
sudo apt update && sudo apt install cryfsStep 2: Create a folder and mount it
In this example, I am creating the place where the data is actually stored in /root/baseDir and mount it to /mnt/nextcloud
You can choose what ever suits your needs and if the baseDir folder is not already in existence it will prompt you to have it created.
sudo cryfs /root/baseDir /mnt/nextcloud -o allow_otherStep 3: Create a sub-folder to store your data in
The reason for this is because we cannot set permissions the way we need to on the mount's root folder.
sudo mkdir /mnt/nextcloud/data && sudo chown -R yellowtent:yellowtent /mnt/nextcloud/dataStep 4: Add the volume to Cloudron
https://your.cloudron.cloud/#/volumesThen add your volume using the 'Filesystem' mount type and full path to /mnt/nextcloud/data


Step 5: Move your Nextcloud app's data directory
Go to Settings, then Storage for your app and select the volume we created from the dropdown. Hit move and get yourself a cup of tea


Notes:
- Content will be included in your backups
- You will manually need to mount this volume using the same command as in Step 2 when you restart your Cloudron!
- This will not protect you from anyone who has root access to your server or to your Nextcloud app. It just encrypts data at rest.
- Make sure to stop the Nextcloud app before you reboot and disable automatic reboots
Let me know what you think about this approach and how you keep your Nextcloud secure

-
@3246 said in [
 Guide] How to move Nextcloud to an encrypted volume:
Guide] How to move Nextcloud to an encrypted volume:You will manually need to mount this volume using the same command as in Step 2 when you restart your Cloudron!
Perhaps improve Step 2 with
fstabautomounting -
@robi that's an idea, although I think it is somewhat insecure to automatically mount the encrypted volume

-
@3246 right, then it's more about key management than convenience, and what you're actually preventing.
If the idea is to protect from offline data theft and disk imaging, then it's less relevant if it's (auto)mounted or not.
As long as it's online & mounted, it's readable.
Thanks for the great guide!
-
@3246 right, then it's more about key management than convenience, and what you're actually preventing.
If the idea is to protect from offline data theft and disk imaging, then it's less relevant if it's (auto)mounted or not.
As long as it's online & mounted, it's readable.
Thanks for the great guide!
@robi you are welcome, glad you found it useful and thanks for your feedback.
I want to prevent unauthorised access to the volume when the server is offline as well as somebody who might take the server out of its rack and boot it. If the volume automatically mounts, they have full access to the data if they can circumnavigate the login cough recovery mode cough
That's covering for physical access to the machine, in what likely would be a read-only, forensic access scenario by a 'bad' actor. In my case, it's a virtualised server, so not as likely to matter, unless they move the VM to a dedicated slice to get busy with it.
Granted, this is somewhat unlikely but being paranoid is better than being sorry

I am in the UK and storing professional data abroad (in nasty Europe no less - just kidding!) means encryption can cover the requirements nicely (as far as I know - I am not an expert in that field, so somebody please correct me if I'm wrong).
-
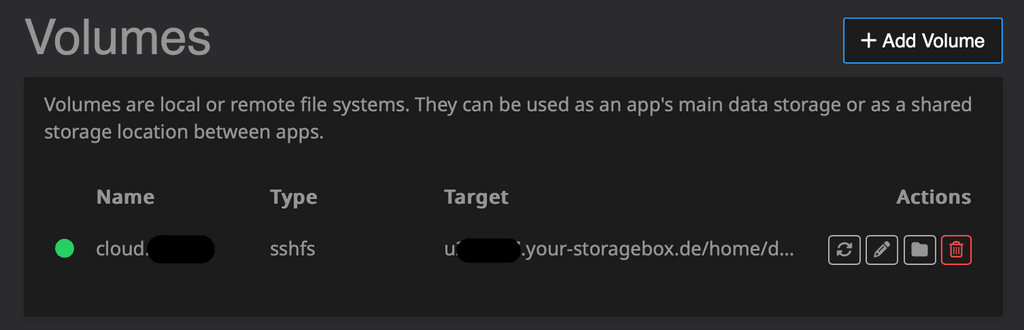
Hi @3246 Are you still using this setup? I'm interested in how it would work with an externally mounted Storage Box
-
Hi @3246 Are you still using this setup? I'm interested in how it would work with an externally mounted Storage Box
@andreasdueren said in [
 Guide] How to move Nextcloud to an encrypted volume:
Guide] How to move Nextcloud to an encrypted volume:how it would work with an externally mounted Storage Box
I don't think that would be possible as I don't think it's possible to use storage boxes for the data directory
Only volumes with Mount Type EXT4 and NFS can be used as the data directory, as other Mount Types do not properly support file permissions.
-
@andreasdueren said in [
 Guide] How to move Nextcloud to an encrypted volume:
Guide] How to move Nextcloud to an encrypted volume:how it would work with an externally mounted Storage Box
I don't think that would be possible as I don't think it's possible to use storage boxes for the data directory
Only volumes with Mount Type EXT4 and NFS can be used as the data directory, as other Mount Types do not properly support file permissions.
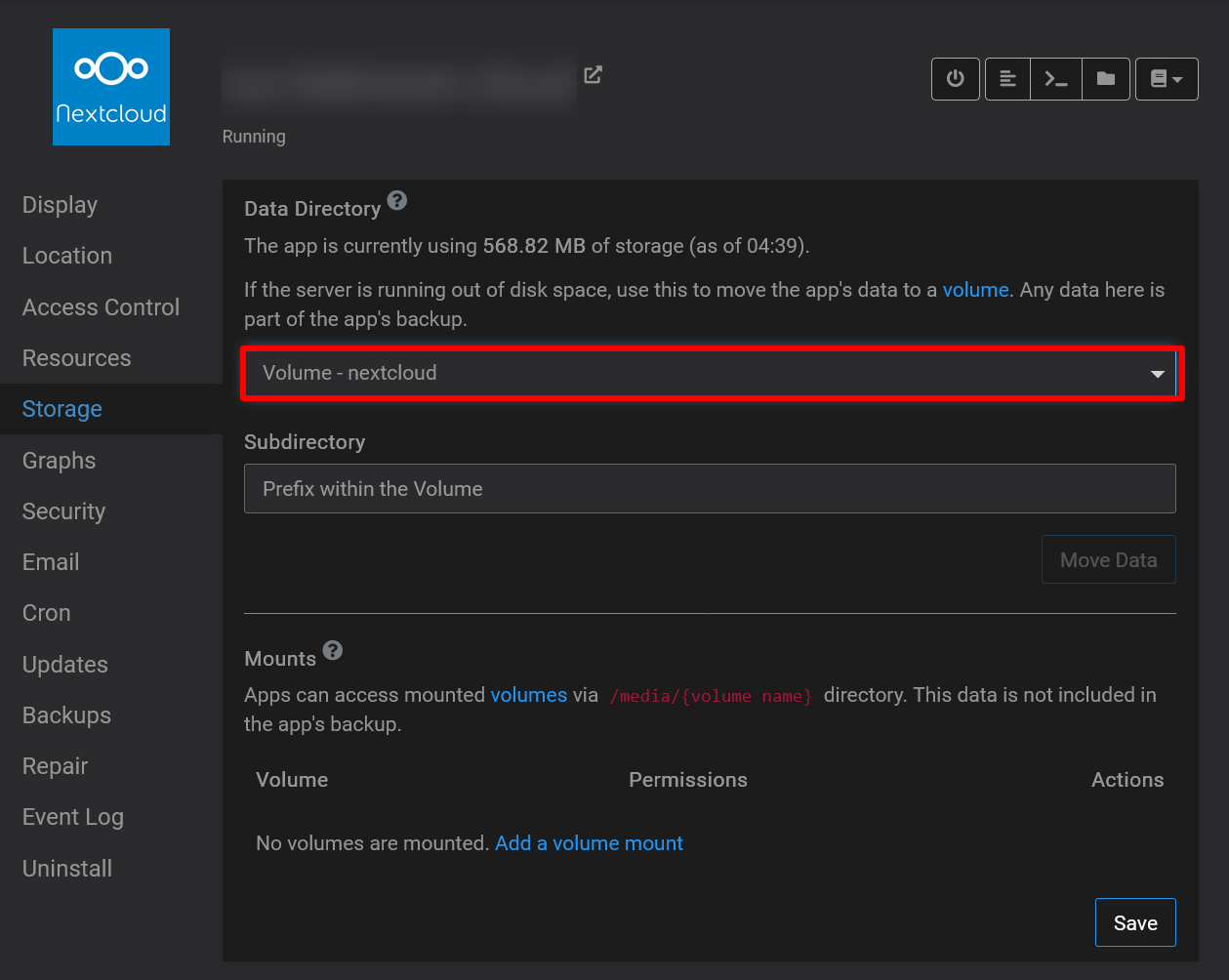
@jdaviescoates I've been using it for my Nextcloud storage directory for a few years without problems now. Highly recommend.
-
@jdaviescoates I've been using it for my Nextcloud storage directory for a few years without problems now. Highly recommend.
@andreasdueren said in [
 Guide] How to move Nextcloud to an encrypted volume:
Guide] How to move Nextcloud to an encrypted volume:storage directory
Storage directory isn't the same as data directory though (and I noted "Step 5: Move your Nextcloud app's data directory")
-
@andreasdueren said in [
 Guide] How to move Nextcloud to an encrypted volume:
Guide] How to move Nextcloud to an encrypted volume:storage directory
Storage directory isn't the same as data directory though (and I noted "Step 5: Move your Nextcloud app's data directory")
@jdaviescoates Yes it's something else. But works well and I have never encountered any problems with Nextcloud and file permissions. This is my setup: