But that points to how important the e2e read back step is.
philkunz
Posts
-
Backups still not verified or what? -
Backups still not verified or what?Has to be a cifs problem related to large backups. NFS works, Otherwise same setup.
-
Backups still not verified or what?I think it has something to do with bigger backups like upwards 20GB of data
-
Backups still not verified or what?Yes, smb3. recreating the site config does not help. Then errors out as Password/Mac mismatch on restoration.
-
Backups still not verified or what?Interesting part is -> I tested with another cloudron instance that runs on another company account, but uses the same Synology backup target -> that one works. Really strange. Yet there is another user in the linked thread that has the same problem...
-
Backups still not verified or what?The only reason I can think of, why this is not done already by default would be bandwidth and s3 egress cost, otherwise it should be the default tbh, to at least read back what was stored.
-
Backups still not verified or what?@girish -> The question is: How many people using CIFS actually try to use backups? And how many are complaining? I'll write an email, just one quick question -> Would it be possible to have an option to read back the file after backup to compare it with the hash then? How else would one detect a backup problem at scale? Cause my understanding is, right now the hash does nothing, except show wether a backup is broken when I need it (which is too late to do anything about it, causing potential data loss)
-
Backups still not verified or what? -
Backups still not verified or what?To put it bluntly: Working Backups are more important than a refined UI, new features, or a new app. If mismatching hashes are not even detected automatically, there is work to be done before doing anything else. Otherwise this in my view is unresponsible negligence for a product like this.
-
Backups still not verified or what?Even for my usecase, mostly gitea instances, it would be shitty to loose data. Good thing I save everything on various levels...
-
Backups still not verified or what?Like take invoiceninja: What do you tell someone who relies on your cloudron solution and who has not taken appropriate measures to save financial data otherwise, because he thought: "I have backups."
-
Backups still not verified or what?Its like you roll the dice with your customers.
-
Backups still not verified or what?So essentially, you are not even comparing backup hashes by reading back the file you just stored, or why is there no warning prior to needing a backup? How can this be considered "verifying" backups?
-
Backups still not verified or what?I needed exactly 2 backups to work from 2 different apps in the last 3 month. Both did not work. The question is: What exactly are you hashing? Where are you creating the hash? How are you creating the hash? A hash is simply a function that can tell you with a certain probability, that a certain input is equal to another input if the hash matches. It tells you nothing about wether the backup works or not. It might increase your odds, but nothing more.
Just tested with another app -> also failing. And yes, there are hash mismatches. Just tested a few. Hashes do not match.
-
Backups still not verified or what?My CIFS mount is on a Synology RS2423RP+ rack mounted unit with ECC usinf Btrfs... I doubt that Synology messes up the file with something essential like this, when this is the basic thing they sell to SMEs.
-
Backups still not verified or what?There is indication now, that CIFS mounts might a have a problem of some sorts.
-
Backups still not verified or what?Wait, you are simply creating a hash? Verification means you create a snapshot of the live filesystem, then actually unpack the tar and check wether that matches, after each backup. Simply saving a hash does nothing.
-
Backups still not verified or what?Again ProxMox saves the day... Its a bad feeling knowing I can't rely on Cloudron to have my back at the moment.
-
Backups still not verified or what?https://forum.cloudron.io/post/114219 -> Here it is specifically said v9 verifies backups. So is it being done? Or not? Another user posted problems with CIFS. Either way -> I doubt you are verifying backups if this still happens and there is no error otherwise.
-
Backups still not verified or what?I thought v9 was to verify backups?
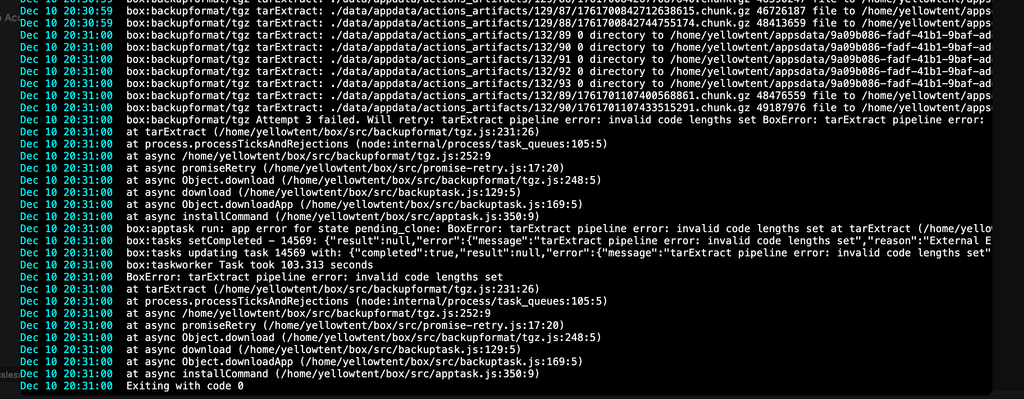
That is kinda shitty tbh, that are still issues like this.
