Nextcloud OIDC integration
-
@joseph I have tried to test the openid server with curl https://my.domain.com/.well-known/openid-configuration from the Nextcloud terminal, and it didnt give any response I have upgraded to the latest Cloudron 8.2.3
I also try to install new cloudron server with new NC just for testing, and it gives response with curl https://my.domain.com/.well-known/openid-configuration
-
@jdaviescoates the plugin doesn't support setting the button name unfortunately. we have to raise issues for these upstream. For example, in the OIDC settings dialog which you posted earlier, you can see that the name comes from the provider type and there is no explicit label configuration. If you open a bug report upstream, please link here.
@girish said in Nextcloud OIDC integration:
For example, in the OIDC settings dialog which you posted earlier, you can see that the name comes from the provider type and there is no explicit label configuration. If you open a bug report upstream, please link here.
Aha, I see. I think I will report this upstream.
Are you able to share what the missing OIDC field name/ value is actually called that e.g. the PeerTube OIDC plugin is picking up but the Nextcloud one isn't? Thanks!
-
Just checked the logs (they are absolutely full):
LocalServerException Host "127.0.1.1" (my.tld.onl:80) violates local access rules Could not reach the provider at URL https://my.tld.onl/openid/.well-known/openid-configuration -
Just checked the logs (they are absolutely full):
LocalServerException Host "127.0.1.1" (my.tld.onl:80) violates local access rules Could not reach the provider at URL https://my.tld.onl/openid/.well-known/openid-configuration@andreasdueren said in Nextcloud OIDC integration:
From the terminal,
curl https://my.tld.onl/openid/.well-known/openid-configurationworks but setting up a separate openID provider (or changing the pre-setup one) will result in this error: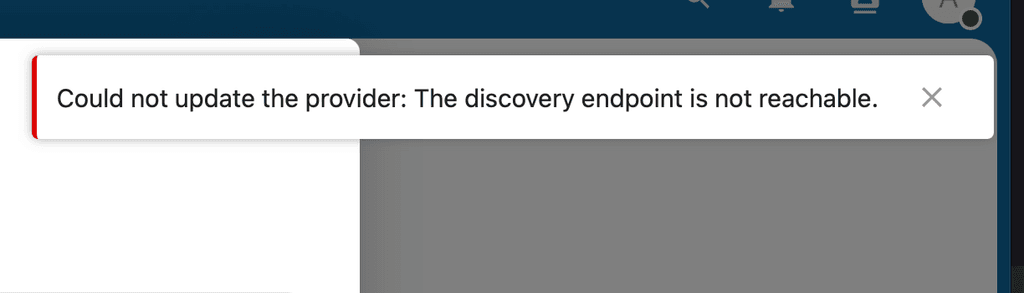
-
@andreasdueren said in Nextcloud OIDC integration:
From the terminal,
curl https://my.tld.onl/openid/.well-known/openid-configurationworks but setting up a separate openID provider (or changing the pre-setup one) will result in this error:
@andreasdueren Not that adding 127.0.1.1 to the proxies did the trick but rebooting the app will reset this section in the config file.
-
Do you have any nextcloud extension or other configs, which might have a blocklist or other security features added? If curl works, this must be some nextcloud code blocking the outgoing request?
@nebulon Unlikely but I can check. This is a pretty fresh installation without any users or data. Don't remember setting anything up
Edit: these are the installed apps now (I disabled a bunch but they were all standard apps)
-
@andreasdueren Not that adding 127.0.1.1 to the proxies did the trick but rebooting the app will reset this section in the config file.
@andreasdueren said in Nextcloud OIDC integration:
@andreasdueren Not that adding 127.0.1.1 to the proxies did the trick but rebooting the app will reset this section in the config file.
What proxy are you referring to here?
-
@andreasdueren said in Nextcloud OIDC integration:
@andreasdueren Not that adding 127.0.1.1 to the proxies did the trick but rebooting the app will reset this section in the config file.
What proxy are you referring to here?
-
Just checked the logs (they are absolutely full):
LocalServerException Host "127.0.1.1" (my.tld.onl:80) violates local access rules Could not reach the provider at URL https://my.tld.onl/openid/.well-known/openid-configuration@andreasdueren said in Nextcloud OIDC integration:
Just checked the logs (they are absolutely full):
LocalServerException Host "127.0.1.1" (my.tld.onl:80) violates local access rules Could not reach the provider at URL https://my.tld.onl/openid/.well-known/openid-configuration@joseph said in Nextcloud OIDC integration:
@andreasdueren can you tell me what made you add
127.0.1.1? Not sure what that IP isThe console complained about it
-
Did you apply any extra configs to Nextcloud? It is still unclear to me who prints this
LocalServerExceptionand why Nextcloud would refuse to connect to that endpoint. Have you looked in the Nextcloud forum/issue tracker about this?Given that you mentioned, that curl to that endpoint from within the nextcloud container works fine, it is somethign within Nextcloud it seems.
-
Did you apply any extra configs to Nextcloud? It is still unclear to me who prints this
LocalServerExceptionand why Nextcloud would refuse to connect to that endpoint. Have you looked in the Nextcloud forum/issue tracker about this?Given that you mentioned, that curl to that endpoint from within the nextcloud container works fine, it is somethign within Nextcloud it seems.
-
Best to reach out at support@cloudron.io , it seems hard to debug . Atleast, fresh instances on all our servers and demo instances seem to work fine.
-
@Joseph Is this something you're interested in debugging? Otherwise I'll just wipe the machine and install fresh
-
@andreasdueren thanks for the access! I am making a new package to fix the issue.
For those interested, here is the technical information:
-
On some VPS providers, when you create a VM with hostname
my.foo.com, it will put an entry in /etc/hosts of the server with 127.0.1.1 . -
Starting Cloudron 8, we started using Docker for the DNS resolution. Docker reads /etc/hosts and starts resolving my.foo.com to 127.0.1.1 .
-
This meant that for apps (which are running in containers) using the domain name my.foo.com (like OIDC service) does not work. This is because it's resolving to 127.0.1.1.
-
To workaround this, we added ExtraHosts to container config. Docker simply adds entries to /etc/hosts of the container. Now, when apps try to resolve my.foo.com they will resolve to 172.18.0.1 because /etc/hosts has more priority than DNS look up.
-
This works for all apps... except nextcloud has decided to implement some DNS pinning protection which I think is to prevent against DNS Rebinding attacks. This code looks up DNS directly (thus skipping /etc/hosts lookup) and thus ends up with 127.0.1.1
 It blocks the access thinking it's an attack.
It blocks the access thinking it's an attack. -
Luckily, there is a config
dns_pinningto disable this functionality.
-
-
@andreasdueren thanks for the access! I am making a new package to fix the issue.
For those interested, here is the technical information:
-
On some VPS providers, when you create a VM with hostname
my.foo.com, it will put an entry in /etc/hosts of the server with 127.0.1.1 . -
Starting Cloudron 8, we started using Docker for the DNS resolution. Docker reads /etc/hosts and starts resolving my.foo.com to 127.0.1.1 .
-
This meant that for apps (which are running in containers) using the domain name my.foo.com (like OIDC service) does not work. This is because it's resolving to 127.0.1.1.
-
To workaround this, we added ExtraHosts to container config. Docker simply adds entries to /etc/hosts of the container. Now, when apps try to resolve my.foo.com they will resolve to 172.18.0.1 because /etc/hosts has more priority than DNS look up.
-
This works for all apps... except nextcloud has decided to implement some DNS pinning protection which I think is to prevent against DNS Rebinding attacks. This code looks up DNS directly (thus skipping /etc/hosts lookup) and thus ends up with 127.0.1.1
 It blocks the access thinking it's an attack.
It blocks the access thinking it's an attack. -
Luckily, there is a config
dns_pinningto disable this functionality.
-
-
@girish So I should add
'dns_pinning' => false,to the config file?
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login