Insecure KDF iterations settings
-
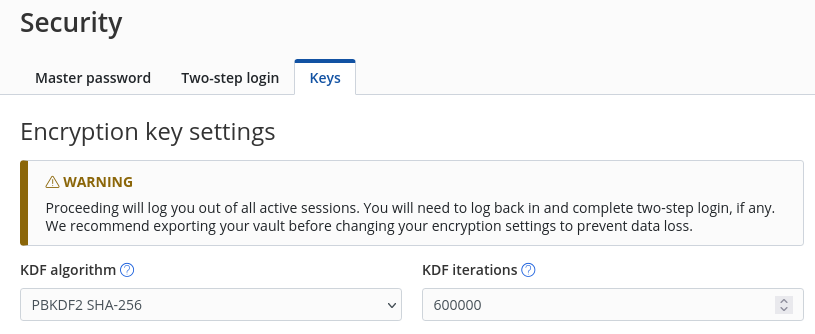
Vaultwarden is installed by default with non-secure kdf iterations settings - would you please, set it up to 600.000 as a minimum please? Ideally - have it set up till 2.000.000
@potemkin_ai said in Insecure KDF iterations settings:
600.000 as a minimum please?
Yeah, is the default on Bitwarden according to https://bitwarden.com/help/kdf-algorithms/
-
@potemkin_ai said in Insecure KDF iterations settings:
600.000 as a minimum please?
Yeah, is the default on Bitwarden according to https://bitwarden.com/help/kdf-algorithms/
@jdaviescoates it was not in case of my server setup, and I didn't touch a thing since it was installed!
-
One more thing:
You are using a plain text
ADMIN_TOKENwhich is insecure.
Please generate a secure Argon2 PHC string by usingvaultwarden hashorargon2.Admin token - which enables full access - is indeed stored plain text and accessible for cloudron admin.
-
here is an official doc, just in case: https://github.com/dani-garcia/vaultwarden/wiki/Enabling-admin-page#secure-the-admin_token
-
One more thing:
You are using a plain text
ADMIN_TOKENwhich is insecure.
Please generate a secure Argon2 PHC string by usingvaultwarden hashorargon2.Admin token - which enables full access - is indeed stored plain text and accessible for cloudron admin.
@potemkin_ai said in Insecure KDF iterations settings:
Admin token - which enables full access - is indeed stored plain text and accessible for cloudron admin.
I think you have to regenerate it like https://docs.cloudron.io/apps/vaultwarden/#admin which already uses argon
-
@girish said in Insecure KDF iterations settings:
The default install has 60k, so maybe I am missing something with this report.
The default Cloudron install (now) has even 600k, not only 60k.
But I think it wasn't always like this (see https://forum.cloudron.io/topic/11194/vaultwarden-security-enhancement-tip/) and @potemkin_ai has an old install? -
@girish said in Insecure KDF iterations settings:
The default install has 60k, so maybe I am missing something with this report.
The default Cloudron install (now) has even 600k, not only 60k.
But I think it wasn't always like this (see https://forum.cloudron.io/topic/11194/vaultwarden-security-enhancement-tip/) and @potemkin_ai has an old install?@necrevistonnezr said in Insecure KDF iterations settings:
The default Cloudron install (now) has even 600k, not only 60k.
ah, even in my screenshot it is 600k. I misread it!
-
@girish said in Insecure KDF iterations settings:
The default install has 60k, so maybe I am missing something with this report.
The default Cloudron install (now) has even 600k, not only 60k.
But I think it wasn't always like this (see https://forum.cloudron.io/topic/11194/vaultwarden-security-enhancement-tip/) and @potemkin_ai has an old install?@necrevistonnezr my installation is quite old - that's correct. Thanks for checking in!
@girish , thank you for the doc's reference! Guess it might make sense to stress that during the installation, as well as an offer to increase KDF up to 2 mln (as per Bitwarden docs as well).
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login