Implement Crowdsec, a docker and sever level crowd sourced security guard
-
@mastadamus I'd like to give an update. I installed the NGINX bouncer and it took down cloudron's NGINX service. During the install it prompted me if i wanted to change several config files or leave the current file in place and I left my current config file in place yet it still crashed and refused to come back up. More investigation is necessary to make this work.
@mastadamus The IP TABLE bouncer seems to be working fine. Also I installed the metabase Docker container running on 8181 with success.
-
@teamcrw are you installing an nginx bouncer with it?
@mastadamus no didn't install nginx bouncer with it. i didn't encounter any problems since i installed it with default settings.
-
 J JOduMonT referenced this topic on
J JOduMonT referenced this topic on
-
 J JOduMonT referenced this topic on
J JOduMonT referenced this topic on
-
@mastadamus no didn't install nginx bouncer with it. i didn't encounter any problems since i installed it with default settings.
@teamcrw I realized crowdsec isn't succesfully parsing the NGINX logs generated by cloudron because Cloudron uses a non standard /non default log format for NGINX. Working on that now.
-
I would like to suggest implemententing Crowdsec as a built-in feature to a cloudron install. Assuming most of our installs (speaking on the community behalf) are internet facing, something like this, could become very powerful and beneficial as a security feature.
Hi!
Just to let you good people know: I am head of community at CrowdSec and I think it's a great idea if Cloudron has build-in support for CrowdSec.
I would be happy to help anyone here out in installing it - and of course to facilitate Cloudron the help they would need to implement it.
Just DM me or write me at klaus (at) crowdsec (dot) net.
-
@teamcrw I realized crowdsec isn't succesfully parsing the NGINX logs generated by cloudron because Cloudron uses a non standard /non default log format for NGINX. Working on that now.
@mastadamus I've since got the logs to be parsed by taking out the custom "combined2" log format for nginx.conf. If this is to be shipped with cloudron it would either require to have custom parsers written OR the nginx.conf for cloudron would need to use default combined log format.
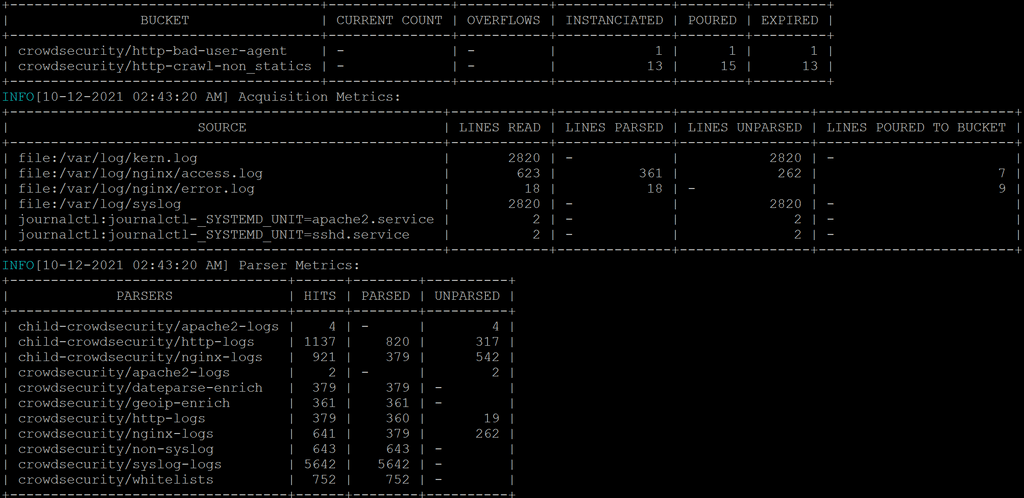
I am using an iptable bouncer and i'm not sure if it will perform block actions on the iptables based of something triggerd by nginx. I will dig further into that. That being said, it is fullfulling the role fail2ban would normally play and is working appropriately.
-
@mastadamus I've since got the logs to be parsed by taking out the custom "combined2" log format for nginx.conf. If this is to be shipped with cloudron it would either require to have custom parsers written OR the nginx.conf for cloudron would need to use default combined log format.

I am using an iptable bouncer and i'm not sure if it will perform block actions on the iptables based of something triggerd by nginx. I will dig further into that. That being said, it is fullfulling the role fail2ban would normally play and is working appropriately.
@mastadamus said in Implement Crowdsec, a docker and sever level crowd sourced security guard:
@mastadamus I've since got the logs to be parsed by taking out the custom "combined2" log format for nginx.conf. If this is to be shipped with cloudron it would either require to have custom parsers written OR the nginx.conf for cloudron would need to use default combined log format.

I am using an iptable bouncer and i'm not sure if it will perform block actions on the iptables based of something triggerd by nginx. I will dig further into that. That being said, it is fullfulling the role fail2ban would normally play and is working appropriately.
@klausagnoletti is this something that could be done by your team?
-
@mastadamus said in Implement Crowdsec, a docker and sever level crowd sourced security guard:
@mastadamus I've since got the logs to be parsed by taking out the custom "combined2" log format for nginx.conf. If this is to be shipped with cloudron it would either require to have custom parsers written OR the nginx.conf for cloudron would need to use default combined log format.

I am using an iptable bouncer and i'm not sure if it will perform block actions on the iptables based of something triggerd by nginx. I will dig further into that. That being said, it is fullfulling the role fail2ban would normally play and is working appropriately.
@klausagnoletti is this something that could be done by your team?
@privsec The other thing to consider is, when i installed the nginx bouncer, even though i left configs default, it crashed the nginx service and i couldn't restart it. Even after I uninstalled the bouncer, I couldn't get nginx back so i had reverted to a snapshot. The iptable bouncer works decent though. Will have to do further testing to figure out why installing the nginx bouncer crashes nginx for cloudron.
-
@mastadamus said in Implement Crowdsec, a docker and sever level crowd sourced security guard:
@mastadamus I've since got the logs to be parsed by taking out the custom "combined2" log format for nginx.conf. If this is to be shipped with cloudron it would either require to have custom parsers written OR the nginx.conf for cloudron would need to use default combined log format.

I am using an iptable bouncer and i'm not sure if it will perform block actions on the iptables based of something triggerd by nginx. I will dig further into that. That being said, it is fullfulling the role fail2ban would normally play and is working appropriately.
@klausagnoletti is this something that could be done by your team?
@klausagnoletti is this something that could be done by your team?
Sorry but which part? Parsers?
-
@klausagnoletti is this something that could be done by your team?
Sorry but which part? Parsers?
@klausagnoletti yup
-
@klausagnoletti yup
@privsec Yes of course. If you post a question about it in our Discourse https://discourse.crowdsec.net I am sure someone on the team is able to help.
-
@privsec The other thing to consider is, when i installed the nginx bouncer, even though i left configs default, it crashed the nginx service and i couldn't restart it. Even after I uninstalled the bouncer, I couldn't get nginx back so i had reverted to a snapshot. The iptable bouncer works decent though. Will have to do further testing to figure out why installing the nginx bouncer crashes nginx for cloudron.
@mastadamus Confirmed. This happened to me today, when I tried to install Crowdsec with Nginx bouncer onto my Cloudron VM.
Thank heavens for a good backup strategy. Digital Ocean snapshots to the rescue.
To have Crowdsec working with my Cloudron install would be a massive value add.
I am not even sure why Nginx failed to start afterwards. I did however note that the install modified or wiped a lot of the Nginx configs which were already in place and perhaps modified by Cloudron. But I haven't tried to dive any deeper.
-
@mastadamus Confirmed. This happened to me today, when I tried to install Crowdsec with Nginx bouncer onto my Cloudron VM.
Thank heavens for a good backup strategy. Digital Ocean snapshots to the rescue.
To have Crowdsec working with my Cloudron install would be a massive value add.
I am not even sure why Nginx failed to start afterwards. I did however note that the install modified or wiped a lot of the Nginx configs which were already in place and perhaps modified by Cloudron. But I haven't tried to dive any deeper.
@makemrproper yeah I tried it twice and first time told it to keep original config and second time allowed modifications.. both times nginx refused to start and I couldn't figure out why.
-
@mastadamus Confirmed. This happened to me today, when I tried to install Crowdsec with Nginx bouncer onto my Cloudron VM.
Thank heavens for a good backup strategy. Digital Ocean snapshots to the rescue.
To have Crowdsec working with my Cloudron install would be a massive value add.
I am not even sure why Nginx failed to start afterwards. I did however note that the install modified or wiped a lot of the Nginx configs which were already in place and perhaps modified by Cloudron. But I haven't tried to dive any deeper.
@makemrproper my strategy now is to use iptables bouncer with nginx parser.
See my feature request for nginx log method though.. you have to revert cloudron nginx logs back to nginx default and not combined2 as they are normally or crowdsec parser won't work..
-
Hey, since I was here last time we have created a Discord server and that would be a good place to influence CrowdSec devs to implement CrowdSec into Cloudron

-
Hey, since I was here last time we have created a Discord server and that would be a good place to influence CrowdSec devs to implement CrowdSec into Cloudron

In my experience, DO not install the nginx bouncer, it's useless if you install the firewall-bouncer anyway. (the firewall bouncer catch attacks, probs etc..even before they reach the nginx server)
There is another post on this forum another user and me share their steps by steps to get it running.
