HSTS Preload
-
It would be nice to have a way to modify the default nginx headers of WordPress Apps.
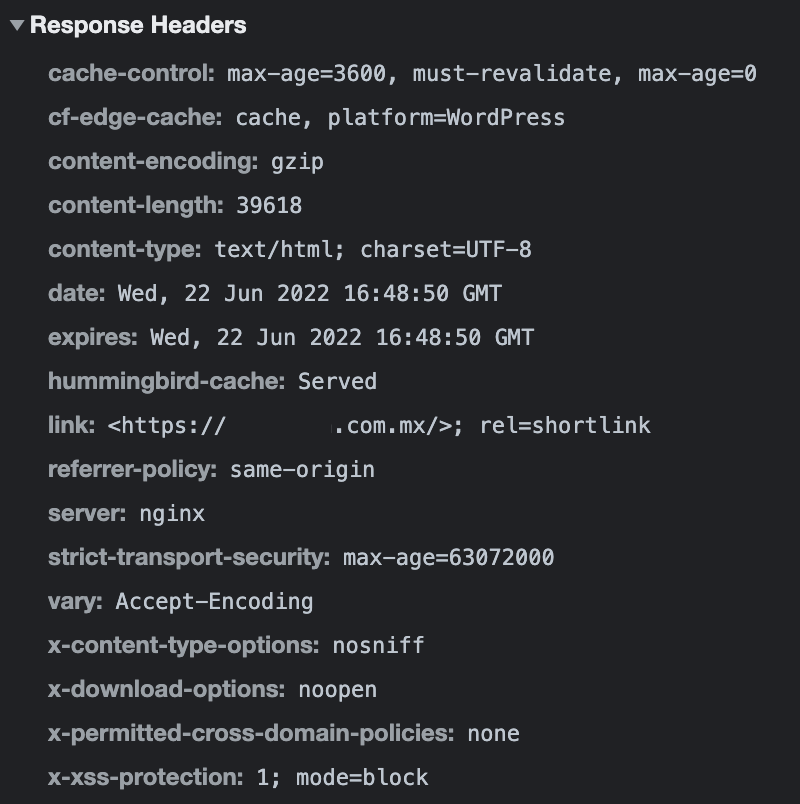
By default, WordPress Apps in Cloudron have the header "strict-transport-security: max-age=63072000". You can find a screenshot below and the reference in here: https://git.cloudron.io/cloudron/box/-/blob/master/src/nginxconfig.ejs#L98
This feature request would be useful in several ways; one of them is because there are simple requirements to submit a domain to the HSTS Preload List. The requirements are adding the "strict-transport-security" header with:
- The max-age must be at least 31536000 seconds (1 year).
- The includeSubDomains directive must be specified.
- The preload directive must be specified.
Using a WordPress plugin I added the required header, but then I would have 2 "strict-transport-security" headers that would result in an "ineligibility" status by submitting the HSTS Preload form.
Please comment if you think I missed something or want to add something to this request. Thanks for reading!
This is a screenshot of our website's headers using Chrome Tools:
-
The requirements are here https://hstspreload.org/ .
I think instead of making something generic, we can possible just add a checkbox say "Enable HSTS Preload" or something.
-
@girish any news on this? As in Europe we currently have this ongoing war between Ukrain and Russia with a hight amount of cyber-attacks in circulation, it would be great to bump up the available security measures as much as possible

If you would be going to create a tunable security-setting here, it would also be really great if you could give the option to select which TLS-Versions should be supported and maybe set a sensible default to support 1.1, 1.2 and 1.3.
Also, do you know if Cloudron uses a Version of NGINX that already supports QUIC protocol rather than TCP to transport HTTP?
Would also be glad to lend a hand if you need support with getting this to work.
-
This is implemented now. Will be available in 7.4.
-
 G girish marked this topic as a question on
G girish marked this topic as a question on
-
 G girish has marked this topic as solved on
G girish has marked this topic as solved on
-
@girish said in HSTS Preload:
This is implemented now. Will be available in 7.4.
I have just upgraded to 7.4, enabled HSTS for my Mastodon instance on blueplanet.social and tried to submitted the address to hstspreload.org, but it reports:
Error: Multiple HSTS headers Response error: Multiple HSTS headers (number of HSTS headers: 3). -
-
The header is coming from somewhere else. Only the last line is generate by Cloudron. We don't have any code to generate other two lines. So maybe this comes mastodon itself.
< strict-transport-security: max-age=63072000; includeSubDomains < x-cached: MISS < strict-transport-security: max-age=31536000 < strict-transport-security: max-age=63072000; includeSubDomains; preload -
@nichu42 ah, this is the same as https://github.com/mastodon/mastodon/issues/17083
-
@girish said in HSTS Preload:
@nichu42 ah, this is the same as https://github.com/mastodon/mastodon/issues/17083
Ah, thanks. So we have Mastodon + Ruby + Cloudron. Is there a way to get rid off the others and thus only have Cloudron set the header?
-
-
