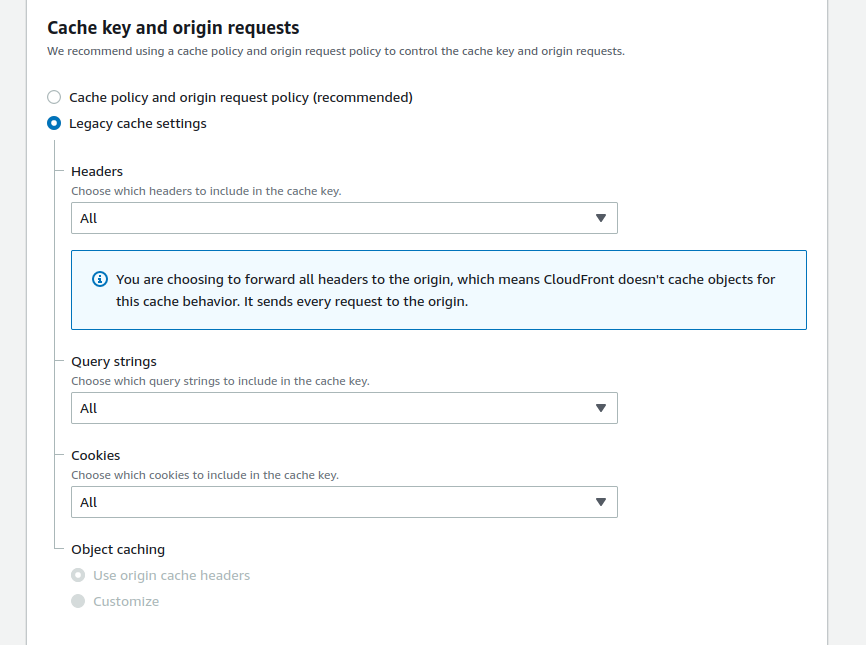
@girish I don't think I understand the problem here. There is no "cloudron domain" that could be leaked. I create a CloudFront distribution, say example.cloudfront.net (or whatever custom domain I configure in CloudFront). This distribution forwards requests with this host to my Cloudron box (over plain HTTP). And there I have a custom nginx config that connects example.cloudfront.net to the Matomo container. There is no other domain involved.
I think the way Cloudron works I still need at least one domain like matomo.cloudron.example.com connected to the app (what you called the "cloudron domain"). Because Cloudron wouldn't know that my custom nginx config already handles connection of the domain. But I don't use it and Matomo doesn't know it exists. Matomo also doesn't know about CloudFront. To Matomo it is indistinguishable from the original setup. Because Matomo is not behind CloudFront, Matomo is behind Cloudron's nginx. How could it leak?
The only thing I need to take care of is that if someone finds the Cloudron Domain (which I don't need, but Cloudron does), they cannot correlate it to the same Matomo that is served through CloudFront. I think the way I'll do this is by using a domain specifically for Cloudron (e.g. not cloudron.my-company.com but my-cloudron.com), so that it cannot be found by enumeration of our subdomains (not sure how well you can protect DNS). And if the custom nginx config takes precedence over Cloudron's own, then I think I can also disable the custom domain and return a 400 instead of forwarding requests to Matomo? So someone "discovering" the domain would still not know it's actually the same Matomo instance served via CloudFront (CloudFront doesn't leak the origin).
Is there something I'm misunderstanding?