Miniflux: Many feeds not fetching with „dial tcp: lookup # on 127.0.0.11:53: server misbehaving“
-
Many (not all) feeds that I know exist are not fetched with this error:
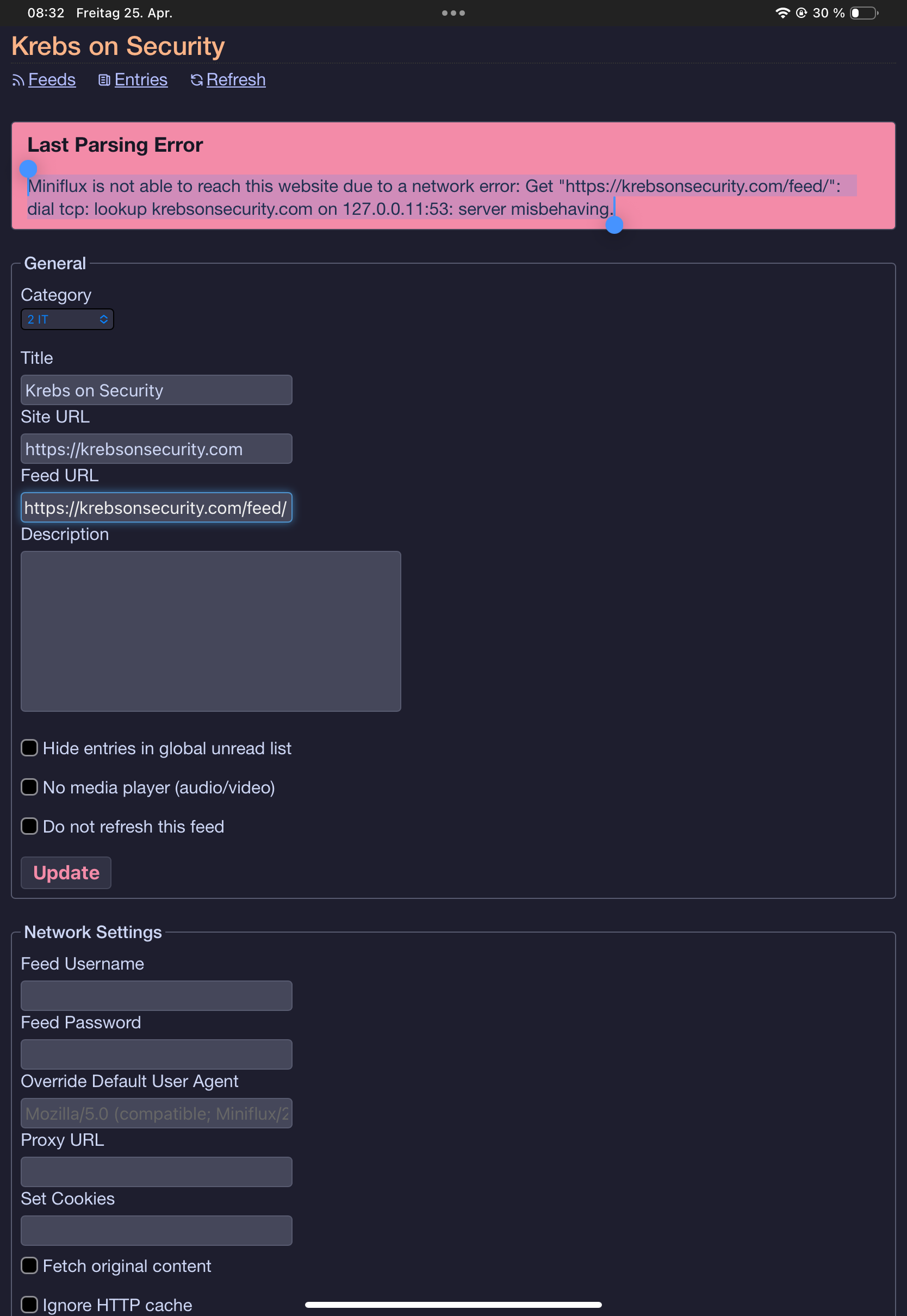
Miniflux is not able to reach this website due to a network error: Get "https://krebsonsecurity.com/feed/": dial tcp: lookup krebsonsecurity.com on 127.0.0.11:53: server misbehaving.Googling this error led to nothing.
The config looks fine:
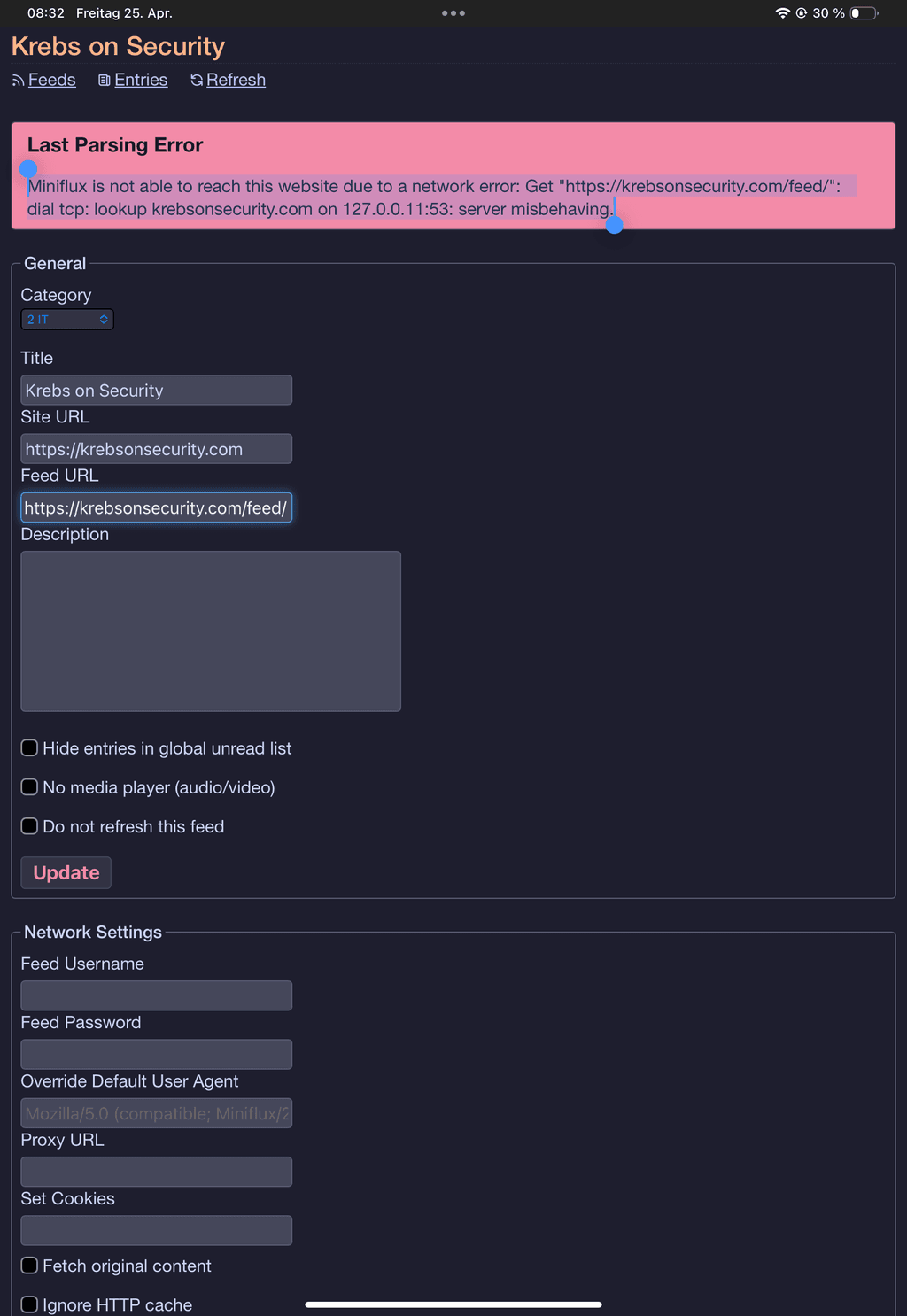
Basic data:
sudo cloudron-support --troubleshoot [sudo] password for ##: Vendor: AZW Product: EQ Linux: 6.8.0-58-generic Ubuntu: noble 24.04 Processor: Intel(R) N100 BIOS Intel(R) N100 To Be Filled By O.E.M. CPU @ 2.8GHz x 4 RAM: 16144264KB Disk: /dev/mapper/ubuntu--vg-ubuntu--lv 355G [OK]node version is correct [OK]IPv6 is enabled and public IPv6 address is working [OK]docker is running [OK]docker version is correct [OK]MySQL is running [OK]nginx is running [OK]dashboard cert is valid [OK]dashboard is reachable via loopback [OK]box v8.3.1 is running [OK]netplan is good [OK]DNS is resolving via systemd-resolved [OK]Dashboard is reachable via domain name [OK]Domain ## is valid and has not expired [OK]unbound is running -
I have restarted the server for good measure.
E.g.
host https://www.heise.de/rss/heise-atom.xmlresults in
Host https://www.heise.de/rss/heise-atom.xml not found: 3(NXDOMAIN)but I can open it in my browser for example.
Also:
host -a heise.de Trying "heise.de" Host heise.de not found: 4(NOTIMP) Received 26 bytes from 127.0.0.11#53 in 6 ms -
For a start
hostwants the domain not the URL, so that explains the first NXDOMAIN. But I don't think this is related to the issue. So if you runhost heise.deon your laptop, the Cloudron host system and within the app container, do you get different results? -
I can reach heise.de on the host system,
host heise.de heise.de has address 193.99.144.80 heise.de has IPv6 address 2a02:2e0:3fe:1001:302:: heise.de mail is handled by 30 mx03.hornetsecurity.com. heise.de mail is handled by 40 mx04.hornetsecurity.com. heise.de mail is handled by 10 mx01.hornetsecurity.com. heise.de mail is handled by 20 mx02.hornetsecurity.com.also on my local laptop. Just not from within the app container.
-
Errr, tried again from the webterminal, now I get:
host heise.de heise.de has address 193.99.144.80 heise.de has IPv6 address 2a02:2e0:3fe:1001:302:: heise.de mail is handled by 10 mx01.hornetsecurity.com. heise.de mail is handled by 20 mx02.hornetsecurity.com. heise.de mail is handled by 30 mx03.hornetsecurity.com. heise.de mail is handled by 40 mx04.hornetsecurity.com.Is it possible that it works only from time to time?
-
So the container uses the host system resolver these days, so
systemd-resolvewhich runs on port 53. Next time this happens, check ifsystemd-resolveis actually working on the host.Additionally have you setup any custom iptables rules, which may interefere here and maybe rate-limit any requests coming from the docker network?
-
Thanks!
My system-resolve seems running fine
resolvectl status Global Protocols: -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported resolv.conf mode: stub Link 2 (enp1s0) Current Scopes: DNS Protocols: +DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Current DNS Server: fdff:f1da:f5a:0:464e:6dff:feac:46ff DNS Servers: 192.168.1.1 fdff:f1da:f5a:0:464e:6dff:feac:46ff 2003:ee:4f1f:e500:464e:6dff:feac:46ff DNS Domain: fritz.box Link 3 (enp2s0) Current Scopes: none Protocols: -DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Link 4 (virbr0) Current Scopes: none Protocols: -DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Link 5 (br-0ff7871073ab) Current Scopes: none Protocols: -DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Link 6 (br-17a44d2d96f4) Current Scopes: none Protocols: -DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Link 7 (docker0) Current Scopes: none Protocols: -DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Link 13 (veth2e6cf90) Current Scopes: none Protocols: -DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Link 15 (veth45f4e5a) Current Scopes: none Protocols: -DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Link 17 (veth0b5b238) Current Scopes: none Protocols: -DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Link 19 (vethe61bf0a) Current Scopes: none Protocols: -DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Link 21 (vethb53dfde) Current Scopes: noneMy iptables have one addition from the default for a docker container running Xubuntu and Firefox that I needed accessible via Guacamole in Cloudron:
ACCEPT 6 -- 172.30.0.0/16 172.18.0.0/16 tcp spt:3389 ACCEPT 6 -- 172.18.0.0/16 172.30.0.0/16 tcp dpt:3389In context:
Chain INPUT (policy ACCEPT) target prot opt source destination CLOUDRON_RATELIMIT 0 -- 0.0.0.0/0 0.0.0.0/0 CLOUDRON 0 -- 0.0.0.0/0 0.0.0.0/0 LIBVIRT_INP 0 -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT) target prot opt source destination CLOUDRON_RATELIMIT 0 -- 0.0.0.0/0 0.0.0.0/0 DOCKER-USER 0 -- 0.0.0.0/0 0.0.0.0/0 DOCKER-ISOLATION-STAGE-1 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED DOCKER 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED DOCKER 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED DOCKER 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 LIBVIRT_FWX 0 -- 0.0.0.0/0 0.0.0.0/0 LIBVIRT_FWI 0 -- 0.0.0.0/0 0.0.0.0/0 LIBVIRT_FWO 0 -- 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT) target prot opt source destination LIBVIRT_OUT 0 -- 0.0.0.0/0 0.0.0.0/0 Chain CLOUDRON (1 references) target prot opt source destination DROP 0 -- 0.0.0.0/0 0.0.0.0/0 match-set cloudron_blocklist src ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp multiport dports 22,80,202,443 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:3389 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:32400 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:32500 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 multiport dports 3478,5349 ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 multiport dports 3478,5349 ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 multiport dports 50000:51000 ACCEPT 1 -- 0.0.0.0/0 0.0.0.0/0 icmptype 8 ACCEPT 1 -- 0.0.0.0/0 0.0.0.0/0 icmptype 0 ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 udp spt:53 ACCEPT 6 -- 172.18.0.0/16 172.18.0.1 multiport dports 3002,3003 ACCEPT 17 -- 172.18.0.0/16 0.0.0.0/0 udp dpt:53 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 LOG 0 -- 0.0.0.0/0 0.0.0.0/0 limit: avg 2/min burst 5 LOG flags 0 level 7 prefix "Packet dropped: " DROP 0 -- 0.0.0.0/0 0.0.0.0/0 Chain CLOUDRON_RATELIMIT (2 references) target prot opt source destination CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443 flags:0x17/0x02 #conn src/32 > 5000 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 state NEW recent: SET name: public-22 side: source mask: 255.255.255.255 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 state NEW recent: UPDATE seconds: 10 hit_count: 5 name: public-22 side: source mask: 255.255.255.255 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:202 state NEW recent: SET name: public-202 side: source mask: 255.255.255.255 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:202 state NEW recent: UPDATE seconds: 10 hit_count: 5 name: public-202 side: source mask: 255.255.255.255 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:222 state NEW recent: SET name: public-222 side: source mask: 255.255.255.255 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:222 state NEW recent: UPDATE seconds: 10 hit_count: 5 name: public-222 side: source mask: 255.255.255.255 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:636 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:3004 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- !172.18.0.0/16 172.18.0.0/16 tcp dpt:2525 flags:0x17/0x02 #conn src/32 > 50 CLOUDRON_RATELIMIT_LOG 6 -- !172.18.0.0/16 172.18.0.0/16 tcp dpt:4190 flags:0x17/0x02 #conn src/32 > 50 CLOUDRON_RATELIMIT_LOG 6 -- !172.18.0.0/16 172.18.0.0/16 tcp dpt:9993 flags:0x17/0x02 #conn src/32 > 50 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:2525 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:3002 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:4190 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:9993 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:9995 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:3306 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:5432 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:6379 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:27017 flags:0x17/0x02 #conn src/32 > 5000 Chain CLOUDRON_RATELIMIT_LOG (19 references) target prot opt source destination LOG 0 -- 0.0.0.0/0 0.0.0.0/0 limit: avg 2/min burst 5 LOG flags 0 level 7 prefix "IPTables RateLimit: " DROP 0 -- 0.0.0.0/0 0.0.0.0/0 Chain DOCKER (3 references) target prot opt source destination ACCEPT 6 -- 0.0.0.0/0 172.18.0.2 tcp dpt:22 ACCEPT 6 -- 0.0.0.0/0 172.18.0.3 tcp dpt:2003 ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:2465 ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:2587 ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:4190 ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:9993 ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:9995 ACCEPT 6 -- 0.0.0.0/0 172.18.18.225 tcp dpt:53 ACCEPT 17 -- 0.0.0.0/0 172.18.18.225 udp dpt:53 ACCEPT 6 -- 0.0.0.0/0 172.18.18.225 tcp dpt:853 Chain DOCKER-ISOLATION-STAGE-1 (1 references) target prot opt source destination DOCKER-ISOLATION-STAGE-2 0 -- 0.0.0.0/0 0.0.0.0/0 DOCKER-ISOLATION-STAGE-2 0 -- 0.0.0.0/0 0.0.0.0/0 DOCKER-ISOLATION-STAGE-2 0 -- 0.0.0.0/0 0.0.0.0/0 RETURN 0 -- 0.0.0.0/0 0.0.0.0/0 Chain DOCKER-ISOLATION-STAGE-2 (3 references) target prot opt source destination DROP 0 -- 0.0.0.0/0 0.0.0.0/0 DROP 0 -- 0.0.0.0/0 0.0.0.0/0 DROP 0 -- 0.0.0.0/0 0.0.0.0/0 RETURN 0 -- 0.0.0.0/0 0.0.0.0/0 Chain DOCKER-USER (1 references) target prot opt source destination DROP 0 -- 0.0.0.0/0 0.0.0.0/0 match-set cloudron_blocklist src ACCEPT 6 -- 172.30.0.0/16 172.18.0.0/16 tcp spt:3389 ACCEPT 6 -- 172.18.0.0/16 172.30.0.0/16 tcp dpt:3389 RETURN 0 -- 0.0.0.0/0 0.0.0.0/0 Chain LIBVIRT_FWI (1 references) target prot opt source destination ACCEPT 0 -- 0.0.0.0/0 192.168.122.0/24 ctstate RELATED,ESTABLISHED REJECT 0 -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable Chain LIBVIRT_FWO (1 references) target prot opt source destination ACCEPT 0 -- 192.168.122.0/24 0.0.0.0/0 REJECT 0 -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable Chain LIBVIRT_FWX (1 references) target prot opt source destination ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 Chain LIBVIRT_INP (1 references) target prot opt source destination ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 udp dpt:53 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:53 ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 udp dpt:67 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:67 Chain LIBVIRT_OUT (1 references) target prot opt source destination ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 udp dpt:53 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:53 ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 udp dpt:68 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:68 -
Thanks for the hint! It reminded me that I had tried something with qemu-kvm a while ago. After removing those rules, everything seems to be working!
-
N necrevistonnezr marked this topic as a question on
-
N necrevistonnezr has marked this topic as solved on
-
No, the errors came back. Is it at all possible it‘s connected to Adguard Home running on the same Cloudron (which uses port 53, IIRC)?
My
/etc/resolv.conflooks like this btwnameserver 127.0.0.53 options edns0 trust-ad search fritz.boxMy iptables look fine now…
Chain INPUT (policy ACCEPT) target prot opt source destination CLOUDRON_RATELIMIT 0 -- 0.0.0.0/0 0.0.0.0/0 CLOUDRON 0 -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy DROP) target prot opt source destination CLOUDRON_RATELIMIT 0 -- 0.0.0.0/0 0.0.0.0/0 DOCKER-USER 0 -- 0.0.0.0/0 0.0.0.0/0 DOCKER-ISOLATION-STAGE-1 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED DOCKER 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED DOCKER 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED DOCKER 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT) target prot opt source destination Chain CLOUDRON (1 references) target prot opt source destination DROP 0 -- 0.0.0.0/0 0.0.0.0/0 match-set cloudron_blocklist src ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp multiport dports 22,80,202,443 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:3389 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:32400 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:32500 ACCEPT 6 -- 0.0.0.0/0 0.0.0.0/0 multiport dports 3478,5349 ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 multiport dports 3478,5349 ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 multiport dports 50000:51000 ACCEPT 1 -- 0.0.0.0/0 0.0.0.0/0 icmptype 8 ACCEPT 1 -- 0.0.0.0/0 0.0.0.0/0 icmptype 0 ACCEPT 17 -- 0.0.0.0/0 0.0.0.0/0 udp spt:53 ACCEPT 6 -- 172.18.0.0/16 172.18.0.1 multiport dports 3002,3003 ACCEPT 17 -- 172.18.0.0/16 0.0.0.0/0 udp dpt:53 ACCEPT 0 -- 0.0.0.0/0 0.0.0.0/0 LOG 0 -- 0.0.0.0/0 0.0.0.0/0 limit: avg 2/min burst 5 LOG flags 0 level 7 prefix "Packet dropped: " DROP 0 -- 0.0.0.0/0 0.0.0.0/0 Chain CLOUDRON_RATELIMIT (2 references) target prot opt source destination CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:443 flags:0x17/0x02 #conn src/32 > 5000 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 state NEW recent: SET name: public-22 side: source mask: 255.255.255.255 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 state NEW recent: UPDATE seconds: 10 hit_count: 5 name: public-22 side: source mask: 255.255.255.255 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:202 state NEW recent: SET name: public-202 side: source mask: 255.255.255.255 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:202 state NEW recent: UPDATE seconds: 10 hit_count: 5 name: public-202 side: source mask: 255.255.255.255 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:222 state NEW recent: SET name: public-222 side: source mask: 255.255.255.255 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:222 state NEW recent: UPDATE seconds: 10 hit_count: 5 name: public-222 side: source mask: 255.255.255.255 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:636 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:3004 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- !172.18.0.0/16 172.18.0.0/16 tcp dpt:2525 flags:0x17/0x02 #conn src/32 > 50 CLOUDRON_RATELIMIT_LOG 6 -- !172.18.0.0/16 172.18.0.0/16 tcp dpt:4190 flags:0x17/0x02 #conn src/32 > 50 CLOUDRON_RATELIMIT_LOG 6 -- !172.18.0.0/16 172.18.0.0/16 tcp dpt:9993 flags:0x17/0x02 #conn src/32 > 50 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:2525 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:3002 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:4190 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:9993 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:9995 flags:0x17/0x02 #conn src/32 > 500 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:3306 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:5432 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:6379 flags:0x17/0x02 #conn src/32 > 5000 CLOUDRON_RATELIMIT_LOG 6 -- 172.18.0.0/16 172.18.0.0/16 tcp dpt:27017 flags:0x17/0x02 #conn src/32 > 5000 Chain CLOUDRON_RATELIMIT_LOG (19 references) target prot opt source destination LOG 0 -- 0.0.0.0/0 0.0.0.0/0 limit: avg 2/min burst 5 LOG flags 0 level 7 prefix "IPTables RateLimit: " DROP 0 -- 0.0.0.0/0 0.0.0.0/0 Chain DOCKER (3 references) target prot opt source destination ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:2465 ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:2587 ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:4190 ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:9993 ACCEPT 6 -- 0.0.0.0/0 172.18.30.4 tcp dpt:9995 ACCEPT 6 -- 0.0.0.0/0 172.18.0.2 tcp dpt:2003 ACCEPT 6 -- 0.0.0.0/0 172.18.18.225 tcp dpt:53 ACCEPT 17 -- 0.0.0.0/0 172.18.18.225 udp dpt:53 ACCEPT 6 -- 0.0.0.0/0 172.18.18.225 tcp dpt:853 ACCEPT 6 -- 0.0.0.0/0 172.18.0.3 tcp dpt:22 Chain DOCKER-ISOLATION-STAGE-1 (1 references) target prot opt source destination DOCKER-ISOLATION-STAGE-2 0 -- 0.0.0.0/0 0.0.0.0/0 DOCKER-ISOLATION-STAGE-2 0 -- 0.0.0.0/0 0.0.0.0/0 DOCKER-ISOLATION-STAGE-2 0 -- 0.0.0.0/0 0.0.0.0/0 RETURN 0 -- 0.0.0.0/0 0.0.0.0/0 Chain DOCKER-ISOLATION-STAGE-2 (3 references) target prot opt source destination DROP 0 -- 0.0.0.0/0 0.0.0.0/0 DROP 0 -- 0.0.0.0/0 0.0.0.0/0 DROP 0 -- 0.0.0.0/0 0.0.0.0/0 RETURN 0 -- 0.0.0.0/0 0.0.0.0/0 Chain DOCKER-USER (1 references) target prot opt source destination DROP 0 -- 0.0.0.0/0 0.0.0.0/0 match-set cloudron_blocklist src ACCEPT 6 -- 172.30.0.0/16 172.18.0.0/16 tcp spt:3389 ACCEPT 6 -- 172.18.0.0/16 172.30.0.0/16 tcp dpt:3389 RETURN 0 -- 0.0.0.0/0 0.0.0.0/0