Restricting app access to logged-in Cloudron users
-
Assume a Cloudron instance at example.com running two apps at:
Does Cloudron's security / authentication model allow for allowing public internet access to (1) while restricting access to (2) to signed-in Cloudron users?
The use case is that the blog at (1) would be intended for public consumption while the wiki would be an organization-internal resource that no one outside the org should be able to access at all.
I have looked through the SSO docs, and at the per-app Access Control / User Management settings, e.g. to "Allow all users from this Cloudron" or to "Allow the following users or groups", but these options configure who may log in to the app, not who may see the app at all. The app at (2) (Wiki.js) does not appear to have an option to restrict access to logged in users (everything is public by default), so I'm looking for a way to lock it down at the Cloudron / nginx level.
-
Assume a Cloudron instance at example.com running two apps at:
Does Cloudron's security / authentication model allow for allowing public internet access to (1) while restricting access to (2) to signed-in Cloudron users?
The use case is that the blog at (1) would be intended for public consumption while the wiki would be an organization-internal resource that no one outside the org should be able to access at all.
I have looked through the SSO docs, and at the per-app Access Control / User Management settings, e.g. to "Allow all users from this Cloudron" or to "Allow the following users or groups", but these options configure who may log in to the app, not who may see the app at all. The app at (2) (Wiki.js) does not appear to have an option to restrict access to logged in users (everything is public by default), so I'm looking for a way to lock it down at the Cloudron / nginx level.
@cbeams Short answer is yes.
To give the bigger picture: Cloudron is essentially deploying apps on the server. Then there is a centralized user directory. When possible, apps are pre-integrated to use this centralized user directory as authentication mechanism.
"When possible" means that app has to support LDAP. When it doesn't support LDAP, the app will have it's own authentication directory. "authentication mechanism" means that only username and password are matched. Any roles/permissions (i.e authorization) are configured inside the app itself.
Finally, apps on Cloudron are deployed to be internet facing i.e anyone can visit the app. The app itself might choose not show any public content though. As in, it requires auth for users to see anything.
To take your specific case:
-
Ghost does not have LDAP integration. Cloudron will deploy it as public facing. So, this is what you want already.
-
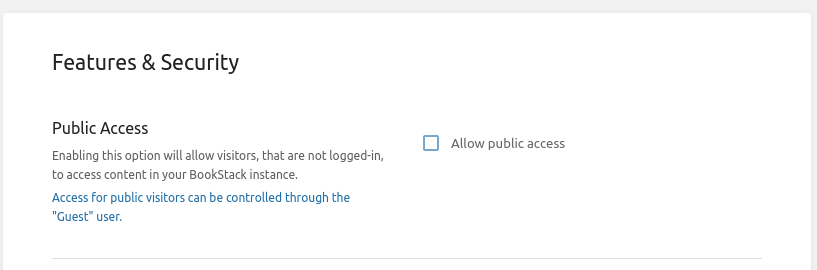
wikijs does support LDAP integration. Cloudron will deploy it as public facing. What you want is then to check if wikijs can restrict content access only to authenticated users. Which it does. Under
Settingslook forPublic Access.
On a side note, if you did want to make Ghost also private, Ghost also has a feature under "Labs" in the settings to password protect the site.
-
-
@cbeams Short answer is yes.
To give the bigger picture: Cloudron is essentially deploying apps on the server. Then there is a centralized user directory. When possible, apps are pre-integrated to use this centralized user directory as authentication mechanism.
"When possible" means that app has to support LDAP. When it doesn't support LDAP, the app will have it's own authentication directory. "authentication mechanism" means that only username and password are matched. Any roles/permissions (i.e authorization) are configured inside the app itself.
Finally, apps on Cloudron are deployed to be internet facing i.e anyone can visit the app. The app itself might choose not show any public content though. As in, it requires auth for users to see anything.
To take your specific case:
-
Ghost does not have LDAP integration. Cloudron will deploy it as public facing. So, this is what you want already.
-
wikijs does support LDAP integration. Cloudron will deploy it as public facing. What you want is then to check if wikijs can restrict content access only to authenticated users. Which it does. Under
Settingslook forPublic Access.

On a side note, if you did want to make Ghost also private, Ghost also has a feature under "Labs" in the settings to password protect the site.
@girish thanks for the response, makes sense. By the way, it looks like you pasted a screenshot from Bookstack's settings screen, as opposed to wiki.js. So far as I can tell, Wiki.js does not have equivalent "make this instance private to logged in users" functionality.
Also note that it looks like CloudFlare's "Access" feature could be a way to lock down whole subdomains/apps to logged in Cloudron users, regardless of whether the app explicitly supports doing so. https://www.cloudflare.com/teams/access/
-
-
@cbeams indeed, I took a quick look at wikijs and all I could find was some setting on a page level to publish or not publish pages. This apparently makes pages only visible for users logged into wikijs. But I am not sure if this is what you really want, since the wikijs UI then to edit pages and all is also visible on those pages.
-
@girish thanks for the response, makes sense. By the way, it looks like you pasted a screenshot from Bookstack's settings screen, as opposed to wiki.js. So far as I can tell, Wiki.js does not have equivalent "make this instance private to logged in users" functionality.
Also note that it looks like CloudFlare's "Access" feature could be a way to lock down whole subdomains/apps to logged in Cloudron users, regardless of whether the app explicitly supports doing so. https://www.cloudflare.com/teams/access/
