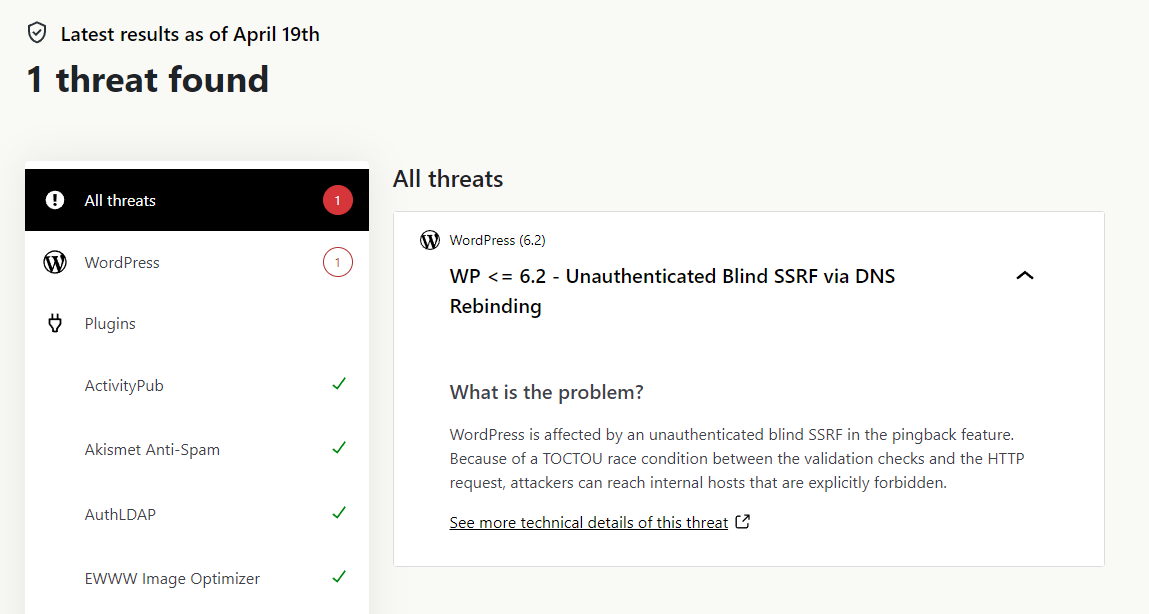
Jetpack alerting on security vuln
-
That's quite an abstract threat message
 Can't say I understand it. @ianhyzy Can you post the link in the screenshot? (The technical details link)
Can't say I understand it. @ianhyzy Can you post the link in the screenshot? (The technical details link) -
-
@ianhyzy I think that link is saying that there is no known fix. https://www.sonarsource.com/blog/wordpress-core-unauthenticated-blind-ssrf/ says similar. Looks like quite a recent report.
@girish said in Jetpack alerting on security vuln:
@ianhyzy I think that link is saying that there is no known fix. https://www.sonarsource.com/blog/wordpress-core-unauthenticated-blind-ssrf/ says similar. Looks like quite a recent report.
also seems to say this issue by itself isn't much to worry about
We couldn't generically identify ways to leverage this behavior to take over vulnerable instances without relying on other vulnerable services.
and
We've audited the code in the hope of finding parser differential bugs that would allow reaching unintended ports or performing POST requests without success: the initial URL validation steps are restrictive enough to prevent their exploitation. As mentioned earlier, attackers would have to chain this behavior with another vulnerability to impact the targeted organization's security significantly.