Use Cloudron Logins for host protected settings
-
That file overwrites the upstream
config.jsin https://git.cloudron.io/cloudron/mirotalksfu-app/-/blob/main/Dockerfile?ref_type=heads#L13 and then loads the one in/app/data/config.jsand then patches up the process internal config object. Only very specific config options are copied over though. For auth it is only those three essentially https://git.cloudron.io/cloudron/mirotalksfu-app/-/blob/main/config.js?ref_type=heads#L20But maybe to take a step back, whatever is specified regarding oidc in the
/app/data/config.jswill get overwritten during runtime. So that is probably not the root cause of the issue you are facing. -
You are right I misread the Dockerfile, thanks for pointing this out!
Maybe it would it be easier to have an example of a
config.jsfile in the documentation.
I guess I'm not the only one failing to configure it
Do I need to create anOpenID Connect Providerin my Cloudron user directory? -
@cvachery I'm confused by this thread.
You shouldn't need to configue anything.
Just select the relevant User management settings when installing and Cloudron sets it all up, no?

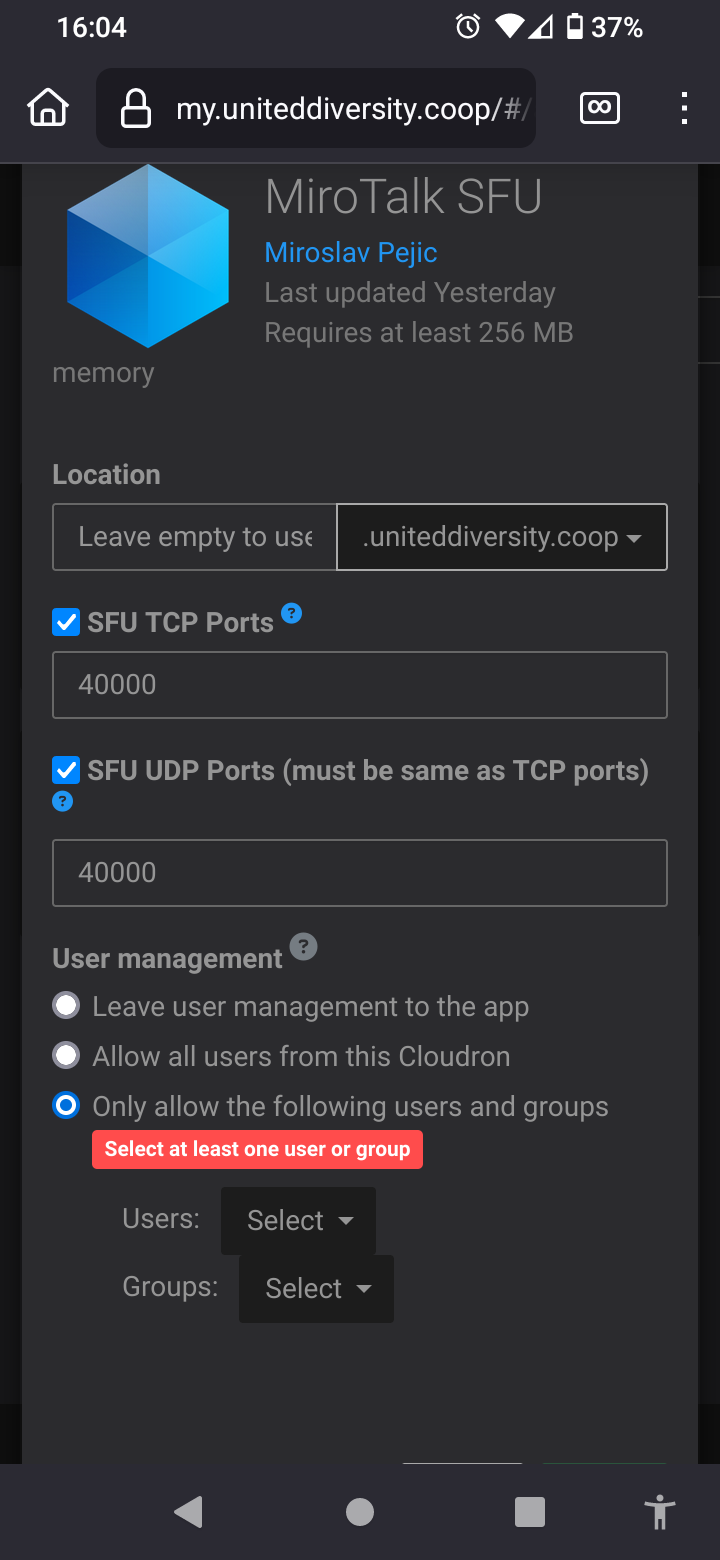
-
I did the same but ticked
Allow all users from this Cloudron
Thing is @jdaviescoates by default anyone can create/join a room. But I want to restrict room creation to logged in users and anyone can join with the link.
And when activating those parameters is when problems arise. -
I did the same but ticked
Allow all users from this Cloudron
Thing is @jdaviescoates by default anyone can create/join a room. But I want to restrict room creation to logged in users and anyone can join with the link.
And when activating those parameters is when problems arise.This post is deleted! -
I did the same but ticked
Allow all users from this Cloudron
Thing is @jdaviescoates by default anyone can create/join a room. But I want to restrict room creation to logged in users and anyone can join with the link.
And when activating those parameters is when problems arise.@cvachery said in Use Cloudron Logins for host protected settings:
Thing is @jdaviescoates by default anyone can create/join a room. But I want to restrict room creation to logged in users and anyone can join with the link.
Ah, right. That ought to be default when choosing Cloudron user management, but I guess it isn't.
-
@avatar1024 said in Use Cloudron Logins for host protected settings:
Otherwise, while guest cannot enter the app base domain without a login, they can still create rooms freely by creating a url: mirotalkappprefix.mydomain.com/join/roomname
@MiroTalk is that behaviour intended?
Not a behaviour intended! I'm considering a refinement where guests are only allowed to join specified rooms that have already been created by authenticated users. This approach might offer better control and security. Will be released in the next version.
Thanks to @MiroTalk in the latest version it works and the config is nearly perfect
Only issue is still one identified erlier that anonymous users can create room if they go to the specific URL@MiroTalk said in Use Cloudron Logins for host protected settings:
@avatar1024 said in Use Cloudron Logins for host protected settings:
Otherwise, while guest cannot enter the app base domain without a login, they can still create rooms freely by creating a url: mirotalkappprefix.mydomain.com/join/roomname
@MiroTalk is that behaviour intended?
Not a behaviour intended! I'm considering a refinement where guests are only allowed to join specified rooms that have already been created by authenticated users. This approach might offer better control and security. Will be released in the next version.
-
Thanks to @MiroTalk in the latest version it works and the config is nearly perfect
Only issue is still one identified erlier that anonymous users can create room if they go to the specific URL@MiroTalk said in Use Cloudron Logins for host protected settings:
@avatar1024 said in Use Cloudron Logins for host protected settings:
Otherwise, while guest cannot enter the app base domain without a login, they can still create rooms freely by creating a url: mirotalkappprefix.mydomain.com/join/roomname
@MiroTalk is that behaviour intended?
Not a behaviour intended! I'm considering a refinement where guests are only allowed to join specified rooms that have already been created by authenticated users. This approach might offer better control and security. Will be released in the next version.
@cvachery said in Use Cloudron Logins for host protected settings:
Thanks to @MiroTalk in the latest version it works and the config is nearly perfect
Only issue is still one identified erlier that anonymous users can create room if they go to the specificShould be fixed in both
MiroTalk P2P v.1.3.79&MiroTalk SFU v.1.5.80. Cheers. -
@cvachery said in Use Cloudron Logins for host protected settings:
Thanks to @MiroTalk in the latest version it works and the config is nearly perfect
Only issue is still one identified erlier that anonymous users can create room if they go to the specificShould be fixed in both
MiroTalk P2P v.1.3.79&MiroTalk SFU v.1.5.80. Cheers.@MiroTalk said in Use Cloudron Logins for host protected settings:
@cvachery said in Use Cloudron Logins for host protected settings:
Thanks to @MiroTalk in the latest version it works and the config is nearly perfect
Only issue is still one identified erlier that anonymous users can create room if they go to the specificShould be fixed in both
MiroTalk P2P v.1.3.79&MiroTalk SFU v.1.5.80. Cheers.Yeah I am still having issue with this / cannot figure out the correct settings to prevent anonymous user room creation.
Basically, I am trying to limit room creation to registered Cloudron User, but still keep the possibility for anonymous users to join a room once created.
At the moment, my MiroTalk SFU app has its cloudron setting access control set to "Only allow the following users and groups".
I do have a custom config.js with the following:
host: { /* Host Protection (default: false) To enhance host security, enable host protection - user auth and provide valid usernames and passwords in the users array. */ protected: true, user_auth: false, users: [ /* { username: 'username', password: 'password', }, { username: 'username2', password: 'password2', }, ... */ ] },Yet room creation is still allowed for anonymous users.
I could set
user_authtotrueand provider "provide valid usernames and passwords in the users array." as mentioned in the config.js comment, but my understanding is that this will void/conflict with the cloudron OIDC integration.Of course, I am likely missing something so I am wondering if anyone got this working properly and if/when so, what are the proper settings for preventing room creation by anonymous users.
Many thanks,
-
@MiroTalk said in Use Cloudron Logins for host protected settings:
@cvachery said in Use Cloudron Logins for host protected settings:
Thanks to @MiroTalk in the latest version it works and the config is nearly perfect
Only issue is still one identified erlier that anonymous users can create room if they go to the specificShould be fixed in both
MiroTalk P2P v.1.3.79&MiroTalk SFU v.1.5.80. Cheers.Yeah I am still having issue with this / cannot figure out the correct settings to prevent anonymous user room creation.
Basically, I am trying to limit room creation to registered Cloudron User, but still keep the possibility for anonymous users to join a room once created.
At the moment, my MiroTalk SFU app has its cloudron setting access control set to "Only allow the following users and groups".
I do have a custom config.js with the following:
host: { /* Host Protection (default: false) To enhance host security, enable host protection - user auth and provide valid usernames and passwords in the users array. */ protected: true, user_auth: false, users: [ /* { username: 'username', password: 'password', }, { username: 'username2', password: 'password2', }, ... */ ] },Yet room creation is still allowed for anonymous users.
I could set
user_authtotrueand provider "provide valid usernames and passwords in the users array." as mentioned in the config.js comment, but my understanding is that this will void/conflict with the cloudron OIDC integration.Of course, I am likely missing something so I am wondering if anyone got this working properly and if/when so, what are the proper settings for preventing room creation by anonymous users.
Many thanks,
@Neiluj If you have OIDC enabled, you can safely remove the entire
host: { ... }section from your configuration. Simply rely on OIDC for authentication, and let me know if everything works as expected. Thank you! -
@Neiluj I just tried this here also with MiroTalk SFU and without changing the app configs manually, just install the app with Cloudron usermanagement enabled and then only authenticated users can create meetings, while everyone can join them with the share link.
-
@Neiluj I just tried this here also with MiroTalk SFU and without changing the app configs manually, just install the app with Cloudron usermanagement enabled and then only authenticated users can create meetings, while everyone can join them with the share link.
@nebulon said in Use Cloudron Logins for host protected settings:
@Neiluj I just tried this here also with MiroTalk SFU and without changing the app configs manually, just install the app with Cloudron usermanagement enabled and then only authenticated users can create meetings, while everyone can join them with the share link.
cant login when i follow your direction
-
I think a direct link is like a public link share unless the room is protected, so that might be expected on how the app is currently written
@nebulon said in Use Cloudron Logins for host protected settings:
I think a direct link is like a public link share unless the room is protected, so that might be expected on how the app is currently written
even if i enable protection still cant use couldron account
-
@nebulon said in Use Cloudron Logins for host protected settings:
I think a direct link is like a public link share unless the room is protected, so that might be expected on how the app is currently written
even if i enable protection still cant use couldron account
@mdc773 I think perhaps you're missing something here.
If you're already logged into your Cloudron dashboard in the same browser you visit your MiroTalk app URL, it doesn't prompt for auth - it just magically checks if you're logged in and if you are just automatically logs you in.
But if you visit the same URL in a private tab you should indeed get prompted to login to Cloudron.
At least that's what happens for me.
I am logged into my Cloudron dashboard, so when I visit my MiroTalk URL I arrive here:
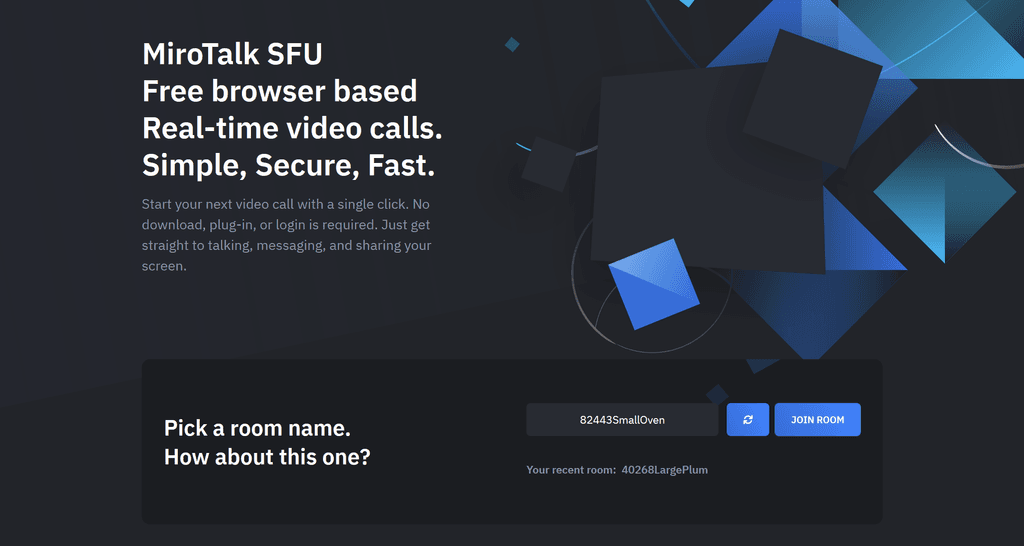
But if I visit the same URL in a private tab I get this:
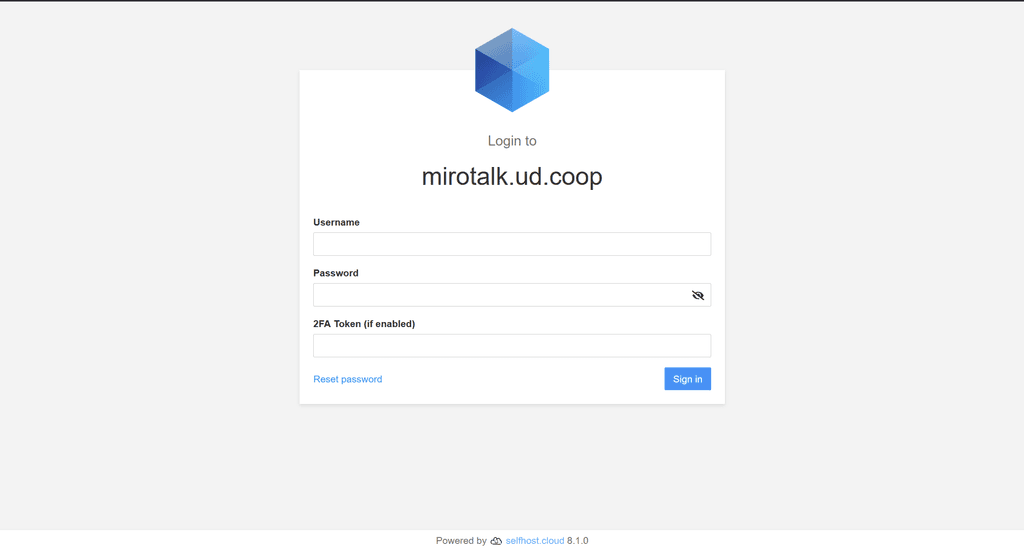
I also just double checked and if you try to visit a join URL of a meeting after the logged in person has left the meeting, it no longer works and you are presented with the login screen again.
