Cannot login anymore after switch to OIDC in latest update
-
Your issue seems to be related to networking actually. With OpenID the apps have to be able to reach the OpenID provider, which is running on the dashboard domain.
Can you maybe check from a webterminal inside the app if the following works (after the rollback):curl -v https://my.<your cloudron domain>/.well-known/openid-configuration@nebulon said in Cannot login anymore after switch to OIDC in latest update:
curl -v https://my.<your cloudron domain>/.well-known/openid-configuration
I cannot reach this URL. Not from bookstack and not from any other sytem.
Do I have to configure something under Domain & Certs before?

-
With OpenID the apps backends have to be able to reach the OpenID provider, which on Cloudron is running on the dashboard domain. So any app with OpenID will fail if your system can't call the Cloudron APIs from within its app containers.
For a start, can you resolve the dashboard domain from the webterminal of an app?
host my.domain.comIf this is a system hosted behind a router (like a homesetup) make sure hairpinning is supported.
-
With OpenID the apps backends have to be able to reach the OpenID provider, which on Cloudron is running on the dashboard domain. So any app with OpenID will fail if your system can't call the Cloudron APIs from within its app containers.
For a start, can you resolve the dashboard domain from the webterminal of an app?
host my.domain.comIf this is a system hosted behind a router (like a homesetup) make sure hairpinning is supported.
@nebulon It returns the public IP address. The system is behind a reverse proxy. The webinterface is reachable over the internet. Should I be able to open https://my.<your cloudron domain>/.well-known/openid-configuration from a browser?
I only get a server error.
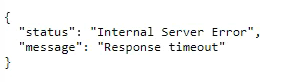
-
Yes that should be publicly reachable. Can you check the server side logs at
/home/yellowtent/platformdata/logs/box.logabout any errors? -
If the local systems can resolve the public IP then this seems fine.
What kind of reverse proxy setup is this, maybe it interferes with the requests? Can you maybe disable that and expose the system directly just to see if it works as expected then? -
 N nebulon has marked this topic as solved on
N nebulon has marked this topic as solved on
-
Hello,
Now, I have the same problem at a customer. Cloudron and bookstack are not accessible from the internet. It is used only internal. I created a custom.conf for the unbound dns. But it is still not working. How do I have to configure the dns setting that OpenID Connect is working? We use a wildcard certificate.
-
Hello,
Now, I have the same problem at a customer. Cloudron and bookstack are not accessible from the internet. It is used only internal. I created a custom.conf for the unbound dns. But it is still not working. How do I have to configure the dns setting that OpenID Connect is working? We use a wildcard certificate.
@buesching said in Cannot login anymore after switch to OIDC in latest update:
But it is still not working
Can you tell us what is not working?
a) Can users reach the cloudron dashboard?
b) Is the app not able to reach the cloudron oidc api? Like maybe nothing appears after you click oidc button in browser?
c) Is that wildcard certificate self signed?If c) is the issue then fixing unbound won't help here. Most apps do not accept self signed certs for oidc. I recommend simply using a proper wildcard cert. You can either switch to one of the Cloudron supported DNS providers OR purchase a wildcard cert (it's only 45usd at https://www.garrisonhost.com/ssl-certificates/alphassl). In either case, you can keep your setup completely private as now.
-
@buesching said in Cannot login anymore after switch to OIDC in latest update:
But it is still not working
Can you tell us what is not working?
a) Can users reach the cloudron dashboard?
b) Is the app not able to reach the cloudron oidc api? Like maybe nothing appears after you click oidc button in browser?
c) Is that wildcard certificate self signed?If c) is the issue then fixing unbound won't help here. Most apps do not accept self signed certs for oidc. I recommend simply using a proper wildcard cert. You can either switch to one of the Cloudron supported DNS providers OR purchase a wildcard cert (it's only 45usd at https://www.garrisonhost.com/ssl-certificates/alphassl). In either case, you can keep your setup completely private as now.
@girish
a) yes
b) same error as in the 4th post. See above.
c) it is not self signed. Its from geotrust.We had the same problem in our environment. It was an misconfiguration of our reverse proxy (from the firewall).
In the environment of the customer the dashboards are note accessible from the internet. In that case the traffic does not run over the reverse proxy. The connection is established locally. -
If you are looking for some DNS solution to avoid the reverse proxy, you have to add something like this to unbound custom config:
server: local-zone: example.com typetransparent local-data: "my.example.com A 172.18.0.1"example.com is your dashboard domain . 172.18.0.1 is the internal oidc server for the app can reach.
-
@buesching Ah, all right. So, your issue looks like bookstack cannot contact cloudron dashboard because of the reverseproxy not looping back http requests. Is this sorted out now? Or are you still looking for assistance?

