Improve security and ciphers
-
Hello,
Regarding to :
- https://securityheaders.io
- https://observatory.mozilla.org/analyze/
- https://tls.imirhil.fr/smtp/
- https://tls.imirhil.fr/https/
There is a way to improve security (ciphers, like Content-Security-Policy in https headers by example).
Also, I've notice that each application have his own score which means that reverse-proxy configuration is not iso for each app ? Is it normal ? -
@saglagla It should be the same for all apps since Cloudron uses a reverse proxy internally.
I checked my.cloudron.io (cloudron), git.cloudron.io (gitlab), chat.cloudron.io (rocketchat) and forum.cloudron.io (nodebb), files.cloudron.io (nextcloud). I get
Afor all the domains. The CSP headers have to be ideally set by the upstream app, most of them do not set it (but nextcloud does). -
@saglagla It should be the same for all apps since Cloudron uses a reverse proxy internally.
I checked my.cloudron.io (cloudron), git.cloudron.io (gitlab), chat.cloudron.io (rocketchat) and forum.cloudron.io (nodebb), files.cloudron.io (nextcloud). I get
Afor all the domains. The CSP headers have to be ideally set by the upstream app, most of them do not set it (but nextcloud does).@girish said in Improve security and ciphers:
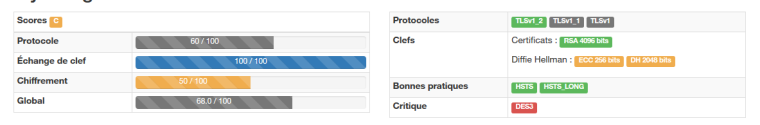
If you check on the mozilla observatory https://observatory.mozilla.org/analyze/my.cloudron.io get a B due to CSP.
Also, if you're using :https://tls.imirhil.fr/ with http test, you'll get a C
-
-
Okay, okay.
Ans, So, each app get his OWN web server ? Okay so it's complicated to uniform the security policy easily...
Also, by example why allowing 3DES ? like DES-CBC3-SHA in all TLS version ?EDIT : I think every app need to be at a A or A+ grade in order to be validated for cloudron.
Paperwork / Wallabag allow unsecure cookies by exemple :
Session cookie set without the Secure flag, but transmission over HTTP prevented by HSTSEDIT 2 : Sorry for the twin-post
Also, I'm just trying to follow up all the public recommandation from the french IT Sec agency -
I have updated the ciphers now according to mozilla's config generator. The commit is https://git.cloudron.io/cloudron/box/commit/ddaa52163bf3844b36d6c29fdffb5db3e0b3f5d0
For the CSP settings, this indeed cannot properly be done on a platform level, as apps require differently strict settings there and have to provide this on their own, so this should ideally be fixed in each app upstream.
