Nextcloud OIDC integration
-
@whitespace said in Nextcloud OIDC integration:
Cloudron accounts should be able to login with their Cloudron credentials without the need of "Login with Cloudron" just by typing their Cloudron credentials into Nextcloud's login form.
This one is not possible. Cloudron accounts have to use the 'Login with Cloudron' button to login . At a platform level, we have standardized on OIDC and where possible the package has been switched to use this.
But apart from that, I suggest just installing a test instance of nextcloud or a clone of your current nextcloud and check out what happens on the upgrade path.
@joseph We are already up-to-date on a live Nextcloud. Thankfully problem 1. only affaects 5 accounts so far. We will manually transfer those to Cloudron.
A nice option would be to customize the text of the "Login with Cloudron" button and the info text shown above. Or, even better, a redirect to Cloudron's login form without a need of the button to begin with.
-
@joseph said in Nextcloud OIDC integration:
This one is not possible. Cloudron accounts have to use the 'Login with Cloudron' button to login . At a platform level, we have standardized on OIDC and where possible the package has been switched to use this.
It kinda make sense that this is not possible, and while it may be confusing for existing users to now have to login in a different way, it makes login in more convenient overall.
However, it would still be great to have some sort of mapping from OIDC credentials to user credential in Nextcloud, as beyond just logging in, OIDC currently makes it rather awkward to connect to other part of Nextcloud. For example, according to this guide, syncing calendars via CalDAV requires you set-up a separate app login, which pretty much defeats the point of a SSO/OIDC set-up. Frankly, for anyone doing anything else than login into Nextcloud from the web interface (syncing calendars, syncing joplin notes, or using any other app that connect to nextcloud via username and password), the new OIDC set-up is more awkward and complicated than LDAP.
Is such a mapping be possible at all, like it is with LDAP??
@avatar1024 the auth situation is not ideal, agreed. But are you comfortable having a setup where users are storing their raw password in all these devices, mobile apps (whichever app your users install) and laptops?
Can't/not my place to make security choices for you
 , but I think if you want the old setup, I think you have to setup nextcloud without Cloudron user management and create users inside nextcloud itself . For us (platform point of view), we want to guide users to what we consider better/more secure. A leaked raw password of the platform has very big implications (compromises all apps)
, but I think if you want the old setup, I think you have to setup nextcloud without Cloudron user management and create users inside nextcloud itself . For us (platform point of view), we want to guide users to what we consider better/more secure. A leaked raw password of the platform has very big implications (compromises all apps) -
@joseph We are already up-to-date on a live Nextcloud. Thankfully problem 1. only affaects 5 accounts so far. We will manually transfer those to Cloudron.
A nice option would be to customize the text of the "Login with Cloudron" button and the info text shown above. Or, even better, a redirect to Cloudron's login form without a need of the button to begin with.
@whitespace said in Nextcloud OIDC integration:
A nice option would be to customize the text of the "Login with Cloudron" button and the info text shown above. Or, even better, a redirect to Cloudron's login form without a need of the button to begin with.
Cloudron already supports this but wasn't supported in the nextcloud plugin. But good news, this was just implemented upstream - https://github.com/nextcloud/user_oidc/issues/859 . It's still not released yet.
edit: looks like this is released, will try to update package
-
@avatar1024 the auth situation is not ideal, agreed. But are you comfortable having a setup where users are storing their raw password in all these devices, mobile apps (whichever app your users install) and laptops?
Can't/not my place to make security choices for you
 , but I think if you want the old setup, I think you have to setup nextcloud without Cloudron user management and create users inside nextcloud itself . For us (platform point of view), we want to guide users to what we consider better/more secure. A leaked raw password of the platform has very big implications (compromises all apps)
, but I think if you want the old setup, I think you have to setup nextcloud without Cloudron user management and create users inside nextcloud itself . For us (platform point of view), we want to guide users to what we consider better/more secure. A leaked raw password of the platform has very big implications (compromises all apps)@girish said in Nextcloud OIDC integration:
A leaked raw password of the platform has very big implications (compromises all apps)
Very much agreed with that and overall I take your point about wanted to prioritise more secured routes. This approach does increase security but I would say only marginally, and with that reasoning we could make cloudron and various apps even more secured but at the further expense of convenience, which I don't think anymore would be up for.
Security is about a range of practices which have somewhat a hierarchy. Things like encrypting your device hard drive being probably the overarching security measure when it comes to password protection, along with using apps that transmit login details securely between device and server (though storing securely is less of a problem if device is encrypted) and using an proper password token / manager. Otherwise if someone get physical access to your device, it is likely they will get access to the platform password by some other means, for example from the web browser where, unless told otherwise, casual users will keep their platform password stored for convenience.
Sure no one is saying we should make the task easy for anyone attempting an attack like keeping all your passwords in a plain text file on your desktop, but wanting to protect the platform password by making usability much worst, where in fact the main security culprit is elsewhere (in people devices encryption and password practices) I'm not sure makes much sense. That's just my opinion, I'm happy to be told wrong and it is also not my place to tell you about security choices :).
-
Basically yes. Here is the scenario in chronological order.
- Fresh Nextcloud is installed on Cloudron instance pre-OIDC, user management being set to Cloudron, not Nextcloud
- Accounts are created via Cloudron user management
- Users start using Nextcloud
- Users create more accounts within Nextcloud
- Accounts created within Nextcloud do not sync back to Cloudron user directory. This was not seen as a problem since these local users were able to login into Nextcloud which is all they needed.
- Nextcloud gets updated to OIDC version.
- Accounts that were LDAP Cloudron accounts can not login via Nextcloud login form anymore. They have to "Login with Cloudron".
- Accounts that were created within Nextcloud and did not reflect into Cloudron user directory can not log in anymore.
This is where we are now. The two problems summarized being:
- Nextcloud accounts that do not exist in the Cloudron directory can not login into Nextcloud anymore.
- Cloudron accounts that used to login with their Cloudron credentials into Nextcloud's login form, can not login directly. They have to "Login with Cloudron", get redirected to Cloudron's app specific login screen and only after that they are logged in into Nextcloud.
Expected behaviour:
- Nextcloud accounts that do not exist in Cloudron user directory should be able to log in via Nextcloud login form.
- Cloudron accounts should be able to login with their Cloudron credentials without the need of "Login with Cloudron" just by typing their Cloudron credentials into Nextcloud's login form.
@whitespace said in Nextcloud OIDC integration:
Nextcloud accounts that do not exist in Cloudron user directory should be able to log in via Nextcloud login form.
This seems to be working as expected. Some users in one of my Nextcloud instance are not Cloudron users and after the update enabling OIDC they haven't been logged out and their credentials seem to be working as usual.
-
@jdaviescoates I have published a new package with groups disabled. Can you please check?
@avatar1024 OIDC Group Sync has to be configured by the package installer just like LDAP Group Sync. Cloudron only exposes groups but does not provision the app (it's not possible for Cloudron to know what group should be what).
@firmansi we can't support both LDAP and OIDC in the long run. But on platform level, we already decided to switch to OIDC for all apps. This is more secure and auditable. I think you can probably wait for the upgrade anyway till all the issues are ironed out. Most of the apps that support OIDC have already been switched to OIDC from LDAP.
@girish said in Nextcloud OIDC integration:
OIDC Group Sync has to be configured by the package installer just like LDAP Group Sync.
Hi @girish
So is there a solution to add users in the Nextcloud admin group with OIDC group mapping activated?
Group mapping works well but when I add users to the admin group from the Nextcloud user interface it doesn't work (as noted by @jdaviescoates earlier in this thread).
-
@girish said in Nextcloud OIDC integration:
OIDC Group Sync has to be configured by the package installer just like LDAP Group Sync.
Hi @girish
So is there a solution to add users in the Nextcloud admin group with OIDC group mapping activated?
Group mapping works well but when I add users to the admin group from the Nextcloud user interface it doesn't work (as noted by @jdaviescoates earlier in this thread).
@avatar1024 it's working for me. But you can only edit/ update users that have logged in post updating to OIDC - it's like all the previous users don't really exist anymore.
-
@avatar1024 it's working for me. But you can only edit/ update users that have logged in post updating to OIDC - it's like all the previous users don't really exist anymore.
@jdaviescoates Thanks! Have you activated group mapping / syncing though? For me it's not working. I cannot add myself to the admin group (and I have definitely logged in - in fact that's how I know I'm not an admin
 ). I can login with the "admin" user via the Nextcloud form but cannot add anyone else to the admin group, including myself.
). I can login with the "admin" user via the Nextcloud form but cannot add anyone else to the admin group, including myself. -
@jdaviescoates Thanks! Have you activated group mapping / syncing though? For me it's not working. I cannot add myself to the admin group (and I have definitely logged in - in fact that's how I know I'm not an admin
 ). I can login with the "admin" user via the Nextcloud form but cannot add anyone else to the admin group, including myself.
). I can login with the "admin" user via the Nextcloud form but cannot add anyone else to the admin group, including myself.@avatar1024 said in Nextcloud OIDC integration:
Have you activated group mapping / syncing though?
No.
-
@avatar1024 said in Nextcloud OIDC integration:
Have you activated group mapping / syncing though?
No.
@jdaviescoates Yeah so it also works for me if I don't activate group mapping / syncing but I was asking if there is a solution to add admins users with that enabled.
On one instance we used LDAP groups syncing and so switching to OIDC we need to also sync groups...but then we also needs admins

Anyone got a clue?
PS: I've tried with my user who is a cloudron superadmin and with another user who is a Cloudron admin. None of them appear in the NC admin group or can be added to it.
-
@avatar1024 can nextcloud admin group have an arbitrary name or should it be admin(s) ? Since group sync is turned on, you have to create a such a group on Cloudron. The admins group is reserved in Cloudron, but this can be changed I think.
-
@avatar1024 can nextcloud admin group have an arbitrary name or should it be admin(s) ? Since group sync is turned on, you have to create a such a group on Cloudron. The admins group is reserved in Cloudron, but this can be changed I think.
@joseph said in Nextcloud OIDC integration:
can nextcloud admin group have an arbitrary name or should it be admin(s) ?
In NC the group name for Admins is "admin". You can't change that and you can't create another group with admin rights. And in Cloudron one cannot create a group called "admin" (as you say the name is reserved). It feels like either:
- Cloudron admins and Super admins should be mapped with the NC admin group
- OIDC group syncing should exclude syncing the NC admin group
-
@avatar1024 there is a "Group whitelist regex" field in the OIDC UI. Have you tried setting it to only the groups you care about? It says it supports regexp, but not sure if it supports lookahead regexps (ask chatgpt) . i.e match all groups that are not admin.
-
@avatar1024 there is a "Group whitelist regex" field in the OIDC UI. Have you tried setting it to only the groups you care about? It says it supports regexp, but not sure if it supports lookahead regexps (ask chatgpt) . i.e match all groups that are not admin.
@joseph Thanks, that worked!
So far I haven't been able to allow all groups but exclude "admin", but when I only allow only a specific group then the admin group is not provisioned and works as expected.
-
Ok this regex to whitelist all groups except "admin" seems to work well
 : ^(?!admin$).+$
: ^(?!admin$).+$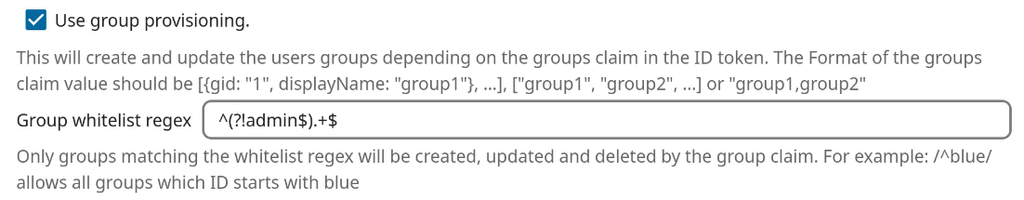
-
J joseph referenced this topic on
-
Is there a way to lead logged-in Nextcloud OICD users from Logout back to the Cloudron login form in logged-out state?
Expected behaviour
- User is logged-in in Nextcloud
- User presses "Logout" in Nextcloud.
- User is logged out of the Nextcloud and from Cloudron.
- User sees the Cloudron login form.
What happens with ˋallow_user_multiple_backendsˋ set to value=0:
- User presses "Logout" in Nextcloud
- User is invisibly getting redirected to Cloudron login form that reports to the Nextcloud instance that user is logged-in.
- User ends up logged-in in Nextcloud.
This would be useful for instances where Nextcloud is the primarily hosted app. We have a server with Nextcloud and Collabora Office backend. There is usually no necessity for users to ever see the dashboard other than editing their profile.
-
I guess Nextcloud initiates the OpenID login redirection automatically in that case then. Since the user still has a login session with the OpenID provider (the Cloudron) it will auto-login.
Since the logout of Nextcloud itself is from the Nextcloud session, the OpenID provider has no clue about a logout event, so I don't think this is currently possible.
-
Is this known that the encryption keys are not initialized anymore after login in with OIDC? I am currently unable to access any of my files via web after the login and the message "Encryption app is enabled, but your keys are not initialized. Please log-out and log-in again." appears but logging out and in again does not help
-
Is this known that the encryption keys are not initialized anymore after login in with OIDC? I am currently unable to access any of my files via web after the login and the message "Encryption app is enabled, but your keys are not initialized. Please log-out and log-in again." appears but logging out and in again does not help
@RaV001 said in Nextcloud OIDC integration:
Is this known that the encryption keys are not initialized anymore after login in with OIDC? I am currently unable to access any of my files via web after the login and the message "Encryption app is enabled, but your keys are not initialized. Please log-out and log-in again." appears but logging out and in again does not help
Okay I updated to the latest version of Nextcloud in Cloudron and now this has changed to telling me that "Invalid private key for encryption app. Please update your private key password in your personal settings to recover access to your encrypted files" but not sure what the old password should be as I am still using the same account but now logged in via OIDC. No files are readable currently
-
@RaV001 said in Nextcloud OIDC integration:
Is this known that the encryption keys are not initialized anymore after login in with OIDC? I am currently unable to access any of my files via web after the login and the message "Encryption app is enabled, but your keys are not initialized. Please log-out and log-in again." appears but logging out and in again does not help
Okay I updated to the latest version of Nextcloud in Cloudron and now this has changed to telling me that "Invalid private key for encryption app. Please update your private key password in your personal settings to recover access to your encrypted files" but not sure what the old password should be as I am still using the same account but now logged in via OIDC. No files are readable currently
@RaV001 said in Nextcloud OIDC integration:
not sure what the old password should be
I'm not sure as I don't use this, but presumably it'll be whatever "your private key password" (not your Cloudron pw) was before whenever you set it up.
Hopefully you made a note of it or remember it?!
If not you could well be stuck.
As an "doesn't help you right now" aside, this is precisely why I personally don't use encryption much myself - I figure the risk of me somehow losing access to my own files by something going wrong or me losing or forgetting my keys is actually quite a lot higher (in that it's actually happened before) than someone nefarious gaining access to my files (which as far as I know has never actually happened)
