DoT support with client ID
-
According to Adguard wiki https://github.com/AdguardTeam/AdGuardHome/wiki/Clients#clientid, the users client ID can be set based on the url used for DoT.
I'm trying to connect to my adguard instance with clientID.adguard.example.com but there is a certificate mismatch because *.adguard.example.com certificates aren't being generated. See the error message below:
dog google.com --tls @clientid.adguard.example.com
Error [tls]: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:../ssl/statem/statem_clnt.c:1914: (Hostname mismatch)The main reason I want to do this is to limit DNS requests to certain clientIDs so I can use the private dns function on android. I can't use my cell IP address because it's dynamic, so that is the only way I see to have a locked down DNS server. I believe all that needs to be done is to issue certs for the adguard instance (as is already done) and then a wildcard cert for *.adguard.example.com.
-
From what I could make out from the AdGuard home config, only one TLS cert can be provided. This means that the cert for
*.adguard.example.comandadguard.example.comneed to be combined into one cert. We have to add support for such a cert in Cloudron since we don't request combined certs. -
 G girish marked this topic as a question on
G girish marked this topic as a question on
-
It could also be that in ClientID mode, DoH with
adguard.example.comis not supposed to work. Onlyclient.adguard.example.comis supposed to work.In any case, apart from the certs, we also need to set up wildcard DNS.
@girish Hi, I just had the same problem as "orangetech" and the same wish to use the client id as access restriction. What I don't understand:
I use my domain via netcup API and it was created for me by cloudron (probably) a wildcard certificate.
Why can't this wildcard certificate be used for the AdGuard app? When I check the certificate in the AdGuard web interface, it shows me that the certificate used is only valid for the main domain.
It would be nice if the client ID filtering option becomes possible. -
@girish Hi, I just had the same problem as "orangetech" and the same wish to use the client id as access restriction. What I don't understand:
I use my domain via netcup API and it was created for me by cloudron (probably) a wildcard certificate.
Why can't this wildcard certificate be used for the AdGuard app? When I check the certificate in the AdGuard web interface, it shows me that the certificate used is only valid for the main domain.
It would be nice if the client ID filtering option becomes possible.@7dowWilkes said in DoT support with client ID:
Why can't this wildcard certificate be used for the AdGuard app?
The wildcard cert does not cover the bare domain cert, because of the way certs work. AdGuard also only supports one cert at a time. This means that we have to get a cert which combines the bare domain (foo.com) and the wildcard (*.foo.com). Have to fix Cloudron's tls addon logic to support such an app. It's on my list.
-
@7dowWilkes said in DoT support with client ID:
Why can't this wildcard certificate be used for the AdGuard app?
The wildcard cert does not cover the bare domain cert, because of the way certs work. AdGuard also only supports one cert at a time. This means that we have to get a cert which combines the bare domain (foo.com) and the wildcard (*.foo.com). Have to fix Cloudron's tls addon logic to support such an app. It's on my list.
@girish
Is this supposed to work now?
I installed the latest AdGuard Home version with Cloudron and set a wildcard alias (*.thirdlevel).
But my Android phone is still unable to connect to device.thirdlevel.domain.comIs there still something that has to be implemented on Cloudron's side or am I missing something?
-
@girish
Is this supposed to work now?
I installed the latest AdGuard Home version with Cloudron and set a wildcard alias (*.thirdlevel).
But my Android phone is still unable to connect to device.thirdlevel.domain.comIs there still something that has to be implemented on Cloudron's side or am I missing something?
@nichu42 It will only work with next cloudron release - 7.4.
AdGuard supports ClientID in both DoH and DoT.
DoH client id works already right now. You can use this in firefox, for example, like this (in
about:config). Screenshot below is from desktop but maybe the mobile client supports it: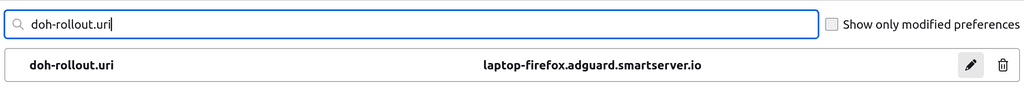
Android only supports DoT (the 'private DNS' feature). It requires a change in platform and thus will only work in next release.
-
@nichu42 It will only work with next cloudron release - 7.4.
AdGuard supports ClientID in both DoH and DoT.
DoH client id works already right now. You can use this in firefox, for example, like this (in
about:config). Screenshot below is from desktop but maybe the mobile client supports it:
Android only supports DoT (the 'private DNS' feature). It requires a change in platform and thus will only work in next release.
-
 G girish has marked this topic as solved on
G girish has marked this topic as solved on
-
@nichu42 It will only work with next cloudron release - 7.4.
AdGuard supports ClientID in both DoH and DoT.
DoH client id works already right now. You can use this in firefox, for example, like this (in
about:config). Screenshot below is from desktop but maybe the mobile client supports it:
Android only supports DoT (the 'private DNS' feature). It requires a change in platform and thus will only work in next release.
-
@nichu42 It will only work with next cloudron release - 7.4.
AdGuard supports ClientID in both DoH and DoT.
DoH client id works already right now. You can use this in firefox, for example, like this (in
about:config). Screenshot below is from desktop but maybe the mobile client supports it:
Android only supports DoT (the 'private DNS' feature). It requires a change in platform and thus will only work in next release.
@girish mh. is there anything to do if there is already a previous version of adguard & cloudron? The moment I updated both to the latest version and added an alias for the wildcard certificate, there is a mismatch between sub third and third level domain.dog cloudron.io --tls @phone.adg.example.org
Error [tls]: error:0A000086:SSL routines:tls_post_process_server_certificate:certificate verify failed:ssl/statem/statem_clnt.c:1889: (hostname mismatch)dog cloudron.io --tls @adg.example.org
A cloudron.io. 5m00s 165.227.67.76Forget about this question. I tested it with the wrong instance with v7.3
-
@girish
also a big thank you from my side - the solution of software-version and adguard works like a charm -
@nichu42 It will only work with next cloudron release - 7.4.
AdGuard supports ClientID in both DoH and DoT.
DoH client id works already right now. You can use this in firefox, for example, like this (in
about:config). Screenshot below is from desktop but maybe the mobile client supports it:
Android only supports DoT (the 'private DNS' feature). It requires a change in platform and thus will only work in next release.
-
@girish said in DoT support with client ID:
Android only supports DoT (the 'private DNS' feature). It requires a change in platform and thus will only work in next release.
is it already working? Trying to get it running but I have no success
@lukas said in DoT support with client ID:
is it already working? Trying to get it running but I have no success
Yes, it is. I have DoH and DoT enabled and restricted access to my clients. It's working great.
What have you tried so far? Which Cloudron version are you running? -
@lukas said in DoT support with client ID:
is it already working? Trying to get it running but I have no success
Yes, it is. I have DoH and DoT enabled and restricted access to my clients. It's working great.
What have you tried so far? Which Cloudron version are you running?@nichu42 said in DoT support with client ID:
What have you tried so far? Which Cloudron version are you running?
Added Client ID, like lukas-android to allow list, and added an alias lukas-android.agh.mydomain.tld to AdGuard Cloudron App. I'm running Cloudron 7.4
Regards,
Lukas -
@nichu42 said in DoT support with client ID:
What have you tried so far? Which Cloudron version are you running?
Added Client ID, like lukas-android to allow list, and added an alias lukas-android.agh.mydomain.tld to AdGuard Cloudron App. I'm running Cloudron 7.4
Regards,
Lukas -
 G girish locked this topic on
G girish locked this topic on
