Matrix Federation not working - curl works but Federation Tester doesn't
-
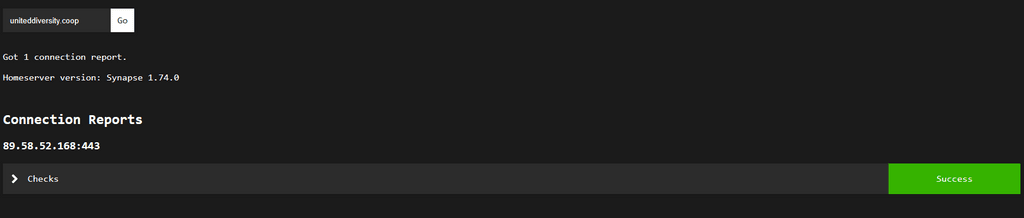
Curl -L is returning the correct response to :433 but the Federation Tester returns:
Get "https://[serveripaddress]:8448/_matrix/key/v2/server": context deadline exceeded (Client.Timeout exceeded while awaiting headers)External rooms are "not accessible at this time"
The matrix server locaiton is set in cloudron with :443 set explicity
there is an app (wordpress install) on the bare domain name. -
had never checked previously, but same:
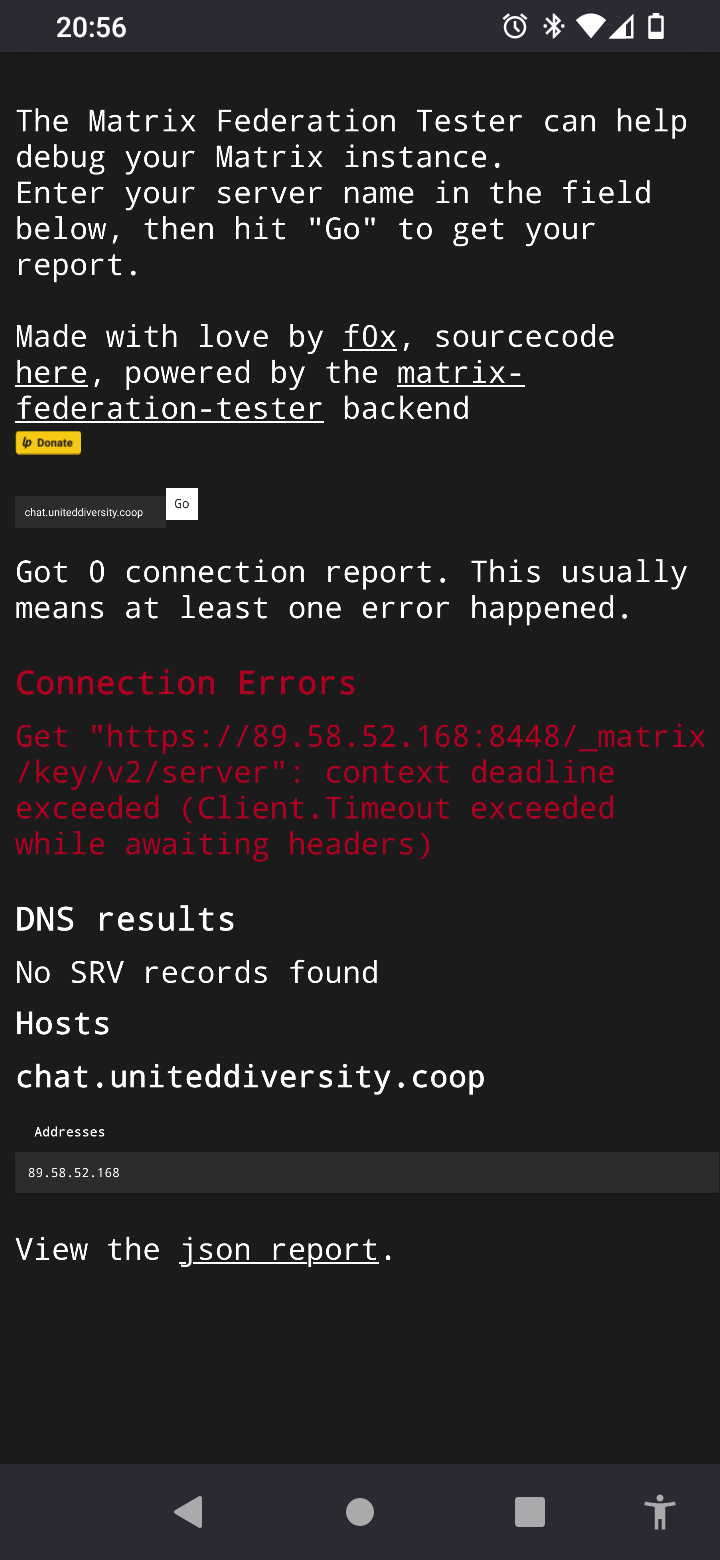
Looks like perhaps we need to add some DNS records that it isn't finding
Here is the json report
{ "WellKnownResult": { "m.server": "", "result": "No .well-known found", "CacheExpiresAt": 0 }, "DNSResult": { "SRVSkipped": false, "SRVCName": "", "SRVRecords": null, "SRVError": { "Message": "lookup _matrix._tcp.chat.uniteddiversity.coop on 8.8.8.8:53: no such host" }, "Hosts": { "chat.uniteddiversity.coop": { "CName": "chat.uniteddiversity.coop.", "Addrs": [ "89.58.52.168" ], "Error": null } }, "Addrs": [ "89.58.52.168:8448" ] }, "ConnectionReports": {}, "ConnectionErrors": { "89.58.52.168:8448": { "Message": "Get \"https://89.58.52.168:8448/_matrix/key/v2/server\": context deadline exceeded (Client.Timeout exceeded while awaiting headers)" } }, "Version": { "error": "Get \"matrix://chat.uniteddiversity.coop/_matrix/federation/v1/version\": dial tcp 89.58.52.168:8448: i/o timeout" }, "FederationOK": false }I'm on my phone but I think that gives some clues as to what needs adding.
Hopefully @staff can update the package to automate adding the necessary entries needed to make this work.
-
had never checked previously, but same:

Looks like perhaps we need to add some DNS records that it isn't finding
Here is the json report
{ "WellKnownResult": { "m.server": "", "result": "No .well-known found", "CacheExpiresAt": 0 }, "DNSResult": { "SRVSkipped": false, "SRVCName": "", "SRVRecords": null, "SRVError": { "Message": "lookup _matrix._tcp.chat.uniteddiversity.coop on 8.8.8.8:53: no such host" }, "Hosts": { "chat.uniteddiversity.coop": { "CName": "chat.uniteddiversity.coop.", "Addrs": [ "89.58.52.168" ], "Error": null } }, "Addrs": [ "89.58.52.168:8448" ] }, "ConnectionReports": {}, "ConnectionErrors": { "89.58.52.168:8448": { "Message": "Get \"https://89.58.52.168:8448/_matrix/key/v2/server\": context deadline exceeded (Client.Timeout exceeded while awaiting headers)" } }, "Version": { "error": "Get \"matrix://chat.uniteddiversity.coop/_matrix/federation/v1/version\": dial tcp 89.58.52.168:8448: i/o timeout" }, "FederationOK": false }I'm on my phone but I think that gives some clues as to what needs adding.
Hopefully @staff can update the package to automate adding the necessary entries needed to make this work.
This is what I get when testing matrix.org
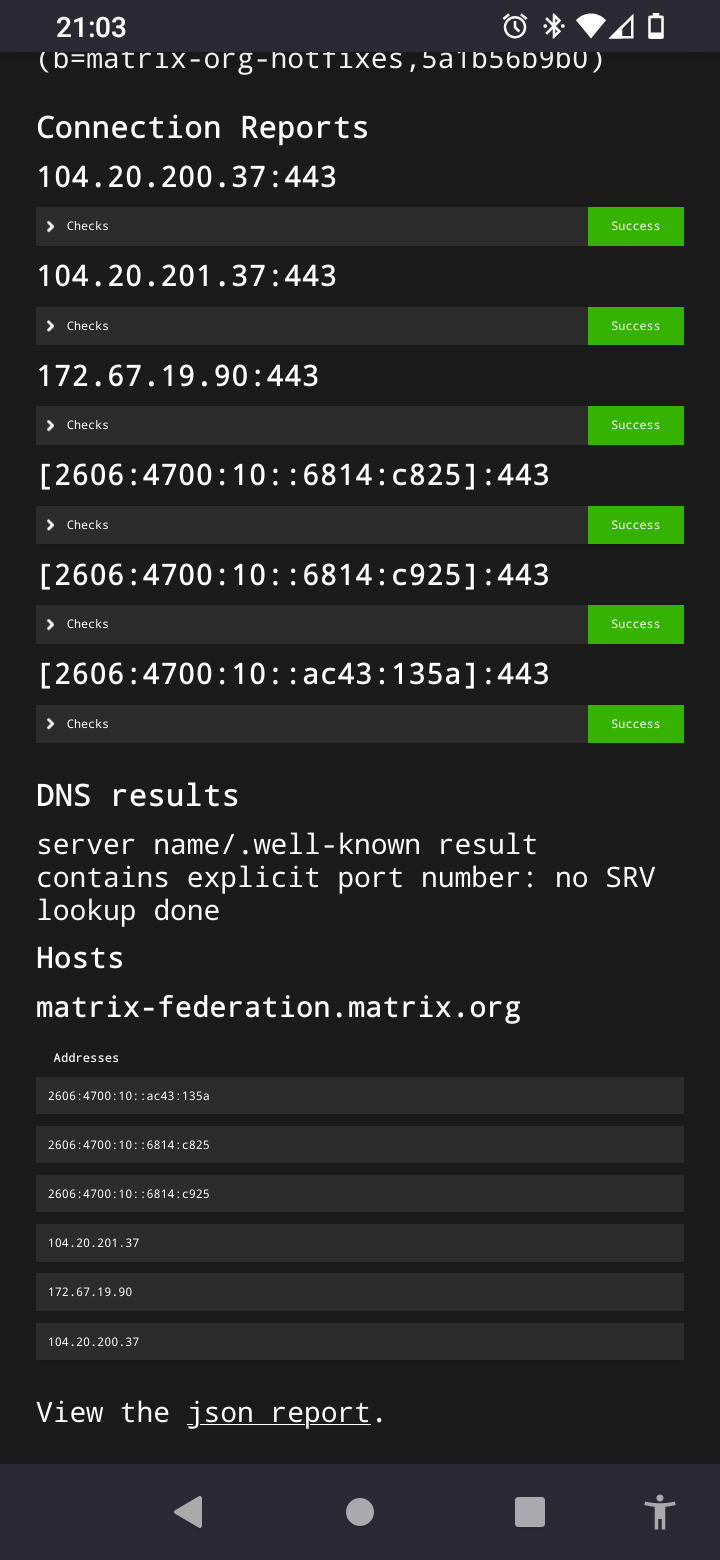
{ "WellKnownResult": { "m.server": "matrix-federation.matrix.org:443", "CacheExpiresAt": 1672707841 }, "DNSResult": { "SRVSkipped": true, "SRVCName": "", "SRVRecords": null, "SRVError": null, "Hosts": { "matrix-federation.matrix.org": { "CName": "matrix-federation.matrix.org.", "Addrs": [ "2606:4700:10::ac43:135a", "2606:4700:10::6814:c825", "2606:4700:10::6814:c925", "104.20.200.37", "172.67.19.90", "104.20.201.37" ], "Error": null } }, "Addrs": [ "[2606:4700:10::ac43:135a]:443", "[2606:4700:10::6814:c825]:443", "[2606:4700:10::6814:c925]:443", "104.20.200.37:443", "172.67.19.90:443", "104.20.201.37:443" ] }, "ConnectionReports": { "104.20.200.37:443": { "Certificates": [ { "SubjectCommonName": "sni.cloudflaressl.com", "IssuerCommonName": "Cloudflare Inc ECC CA-3", "SHA256Fingerprint": "kBX1oyhKwmIT6Tm+cwaR+UvttEmkpHypQcUTPHWrJqU", "DNSNames": [ "matrix.org", "*.matrix.org", "sni.cloudflaressl.com" ] }, { "SubjectCommonName": "Cloudflare Inc ECC CA-3", "IssuerCommonName": "Baltimore CyberTrust Root", "SHA256Fingerprint": "OrvmPa91bFAWtrhfUgFf2Oisvid8UIexJ6YFY6hB7Yo", "DNSNames": null } ], "Cipher": { "Version": "TLS 1.3", "CipherSuite": "TLS_AES_128_GCM_SHA256" }, "Checks": { "AllChecksOK": true, "MatchingServerName": true, "FutureValidUntilTS": true, "HasEd25519Key": true, "AllEd25519ChecksOK": true, "Ed25519Checks": { "ed25519:a_RXGa": { "ValidEd25519": true, "MatchingSignature": true } }, "ValidCertificates": true }, "Errors": [], "Ed25519VerifyKeys": { "ed25519:a_RXGa": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" }, "Info": {}, "Keys": { "old_verify_keys": { "ed25519:auto": { "expired_ts": 1576767829750, "key": "Noi6WqcDj0QmPxCNQqgezwTlBKrfqehY1u2FyWP9uYw" } }, "server_name": "matrix.org", "signatures": { "matrix.org": { "ed25519:a_RXGa": "+/oYcZdYctgxcZCCrP4wx5S3rc1+2pbdpv3sJkKBpqn/uhJd+7+NPd9hUb3HBw+CVjjGugNSznM3RUgri4kQAQ" } }, "valid_until_ts": 1672751664505, "verify_keys": { "ed25519:a_RXGa": { "key": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" } } } }, "104.20.201.37:443": { "Certificates": [ { "SubjectCommonName": "sni.cloudflaressl.com", "IssuerCommonName": "Cloudflare Inc ECC CA-3", "SHA256Fingerprint": "kBX1oyhKwmIT6Tm+cwaR+UvttEmkpHypQcUTPHWrJqU", "DNSNames": [ "matrix.org", "*.matrix.org", "sni.cloudflaressl.com" ] }, { "SubjectCommonName": "Cloudflare Inc ECC CA-3", "IssuerCommonName": "Baltimore CyberTrust Root", "SHA256Fingerprint": "OrvmPa91bFAWtrhfUgFf2Oisvid8UIexJ6YFY6hB7Yo", "DNSNames": null } ], "Cipher": { "Version": "TLS 1.3", "CipherSuite": "TLS_AES_128_GCM_SHA256" }, "Checks": { "AllChecksOK": true, "MatchingServerName": true, "FutureValidUntilTS": true, "HasEd25519Key": true, "AllEd25519ChecksOK": true, "Ed25519Checks": { "ed25519:a_RXGa": { "ValidEd25519": true, "MatchingSignature": true } }, "ValidCertificates": true }, "Errors": [], "Ed25519VerifyKeys": { "ed25519:a_RXGa": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" }, "Info": {}, "Keys": { "old_verify_keys": { "ed25519:auto": { "expired_ts": 1576767829750, "key": "Noi6WqcDj0QmPxCNQqgezwTlBKrfqehY1u2FyWP9uYw" } }, "server_name": "matrix.org", "signatures": { "matrix.org": { "ed25519:a_RXGa": "+/oYcZdYctgxcZCCrP4wx5S3rc1+2pbdpv3sJkKBpqn/uhJd+7+NPd9hUb3HBw+CVjjGugNSznM3RUgri4kQAQ" } }, "valid_until_ts": 1672751664505, "verify_keys": { "ed25519:a_RXGa": { "key": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" } } } }, "172.67.19.90:443": { "Certificates": [ { "SubjectCommonName": "sni.cloudflaressl.com", "IssuerCommonName": "Cloudflare Inc ECC CA-3", "SHA256Fingerprint": "kBX1oyhKwmIT6Tm+cwaR+UvttEmkpHypQcUTPHWrJqU", "DNSNames": [ "matrix.org", "*.matrix.org", "sni.cloudflaressl.com" ] }, { "SubjectCommonName": "Cloudflare Inc ECC CA-3", "IssuerCommonName": "Baltimore CyberTrust Root", "SHA256Fingerprint": "OrvmPa91bFAWtrhfUgFf2Oisvid8UIexJ6YFY6hB7Yo", "DNSNames": null } ], "Cipher": { "Version": "TLS 1.3", "CipherSuite": "TLS_AES_128_GCM_SHA256" }, "Checks": { "AllChecksOK": true, "MatchingServerName": true, "FutureValidUntilTS": true, "HasEd25519Key": true, "AllEd25519ChecksOK": true, "Ed25519Checks": { "ed25519:a_RXGa": { "ValidEd25519": true, "MatchingSignature": true } }, "ValidCertificates": true }, "Errors": [], "Ed25519VerifyKeys": { "ed25519:a_RXGa": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" }, "Info": {}, "Keys": { "old_verify_keys": { "ed25519:auto": { "expired_ts": 1576767829750, "key": "Noi6WqcDj0QmPxCNQqgezwTlBKrfqehY1u2FyWP9uYw" } }, "server_name": "matrix.org", "signatures": { "matrix.org": { "ed25519:a_RXGa": "+/oYcZdYctgxcZCCrP4wx5S3rc1+2pbdpv3sJkKBpqn/uhJd+7+NPd9hUb3HBw+CVjjGugNSznM3RUgri4kQAQ" } }, "valid_until_ts": 1672751664505, "verify_keys": { "ed25519:a_RXGa": { "key": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" } } } }, "[2606:4700:10::6814:c825]:443": { "Certificates": [ { "SubjectCommonName": "sni.cloudflaressl.com", "IssuerCommonName": "Cloudflare Inc ECC CA-3", "SHA256Fingerprint": "kBX1oyhKwmIT6Tm+cwaR+UvttEmkpHypQcUTPHWrJqU", "DNSNames": [ "matrix.org", "*.matrix.org", "sni.cloudflaressl.com" ] }, { "SubjectCommonName": "Cloudflare Inc ECC CA-3", "IssuerCommonName": "Baltimore CyberTrust Root", "SHA256Fingerprint": "OrvmPa91bFAWtrhfUgFf2Oisvid8UIexJ6YFY6hB7Yo", "DNSNames": null } ], "Cipher": { "Version": "TLS 1.3", "CipherSuite": "TLS_AES_128_GCM_SHA256" }, "Checks": { "AllChecksOK": true, "MatchingServerName": true, "FutureValidUntilTS": true, "HasEd25519Key": true, "AllEd25519ChecksOK": true, "Ed25519Checks": { "ed25519:a_RXGa": { "ValidEd25519": true, "MatchingSignature": true } }, "ValidCertificates": true }, "Errors": [], "Ed25519VerifyKeys": { "ed25519:a_RXGa": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" }, "Info": {}, "Keys": { "old_verify_keys": { "ed25519:auto": { "expired_ts": 1576767829750, "key": "Noi6WqcDj0QmPxCNQqgezwTlBKrfqehY1u2FyWP9uYw" } }, "server_name": "matrix.org", "signatures": { "matrix.org": { "ed25519:a_RXGa": "+/oYcZdYctgxcZCCrP4wx5S3rc1+2pbdpv3sJkKBpqn/uhJd+7+NPd9hUb3HBw+CVjjGugNSznM3RUgri4kQAQ" } }, "valid_until_ts": 1672751664505, "verify_keys": { "ed25519:a_RXGa": { "key": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" } } } }, "[2606:4700:10::6814:c925]:443": { "Certificates": [ { "SubjectCommonName": "sni.cloudflaressl.com", "IssuerCommonName": "Cloudflare Inc ECC CA-3", "SHA256Fingerprint": "kBX1oyhKwmIT6Tm+cwaR+UvttEmkpHypQcUTPHWrJqU", "DNSNames": [ "matrix.org", "*.matrix.org", "sni.cloudflaressl.com" ] }, { "SubjectCommonName": "Cloudflare Inc ECC CA-3", "IssuerCommonName": "Baltimore CyberTrust Root", "SHA256Fingerprint": "OrvmPa91bFAWtrhfUgFf2Oisvid8UIexJ6YFY6hB7Yo", "DNSNames": null } ], "Cipher": { "Version": "TLS 1.3", "CipherSuite": "TLS_AES_128_GCM_SHA256" }, "Checks": { "AllChecksOK": true, "MatchingServerName": true, "FutureValidUntilTS": true, "HasEd25519Key": true, "AllEd25519ChecksOK": true, "Ed25519Checks": { "ed25519:a_RXGa": { "ValidEd25519": true, "MatchingSignature": true } }, "ValidCertificates": true }, "Errors": [], "Ed25519VerifyKeys": { "ed25519:a_RXGa": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" }, "Info": {}, "Keys": { "old_verify_keys": { "ed25519:auto": { "expired_ts": 1576767829750, "key": "Noi6WqcDj0QmPxCNQqgezwTlBKrfqehY1u2FyWP9uYw" } }, "server_name": "matrix.org", "signatures": { "matrix.org": { "ed25519:a_RXGa": "+/oYcZdYctgxcZCCrP4wx5S3rc1+2pbdpv3sJkKBpqn/uhJd+7+NPd9hUb3HBw+CVjjGugNSznM3RUgri4kQAQ" } }, "valid_until_ts": 1672751664505, "verify_keys": { "ed25519:a_RXGa": { "key": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" } } } }, "[2606:4700:10::ac43:135a]:443": { "Certificates": [ { "SubjectCommonName": "sni.cloudflaressl.com", "IssuerCommonName": "Cloudflare Inc ECC CA-3", "SHA256Fingerprint": "kBX1oyhKwmIT6Tm+cwaR+UvttEmkpHypQcUTPHWrJqU", "DNSNames": [ "matrix.org", "*.matrix.org", "sni.cloudflaressl.com" ] }, { "SubjectCommonName": "Cloudflare Inc ECC CA-3", "IssuerCommonName": "Baltimore CyberTrust Root", "SHA256Fingerprint": "OrvmPa91bFAWtrhfUgFf2Oisvid8UIexJ6YFY6hB7Yo", "DNSNames": null } ], "Cipher": { "Version": "TLS 1.3", "CipherSuite": "TLS_AES_128_GCM_SHA256" }, "Checks": { "AllChecksOK": true, "MatchingServerName": true, "FutureValidUntilTS": true, "HasEd25519Key": true, "AllEd25519ChecksOK": true, "Ed25519Checks": { "ed25519:a_RXGa": { "ValidEd25519": true, "MatchingSignature": true } }, "ValidCertificates": true }, "Errors": [], "Ed25519VerifyKeys": { "ed25519:a_RXGa": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" }, "Info": {}, "Keys": { "old_verify_keys": { "ed25519:auto": { "expired_ts": 1576767829750, "key": "Noi6WqcDj0QmPxCNQqgezwTlBKrfqehY1u2FyWP9uYw" } }, "server_name": "matrix.org", "signatures": { "matrix.org": { "ed25519:a_RXGa": "+/oYcZdYctgxcZCCrP4wx5S3rc1+2pbdpv3sJkKBpqn/uhJd+7+NPd9hUb3HBw+CVjjGugNSznM3RUgri4kQAQ" } }, "valid_until_ts": 1672751664505, "verify_keys": { "ed25519:a_RXGa": { "key": "l8Hft5qXKn1vfHrg3p4+W8gELQVo8N13JkluMfmn2sQ" } } } } }, "ConnectionErrors": {}, "Version": { "name": "Synapse", "version": "1.74.0 (b=matrix-org-hotfixes,5a1b56b9b0)" }, "FederationOK": true } -
Seems for some reason on Cloudron it's not picking up the well known and port. Odd
-
Curl -L is returning the correct response to :433 but the Federation Tester returns:
Get "https://[serveripaddress]:8448/_matrix/key/v2/server": context deadline exceeded (Client.Timeout exceeded while awaiting headers)External rooms are "not accessible at this time"
The matrix server locaiton is set in cloudron with :443 set explicity
there is an app (wordpress install) on the bare domain name.@Supaiku You have to use the matrix federated domain NOT the app domain (unless these are both the same, by default on cloudron they are NOT)
Example, my matrix server is
matrix.urgero.orgwithurgero.orgbeing the user's domain for federation.Testing
matrix.urgero.orgactually fails with that tool - buturgero.orgdoes not.Hope this helps.
Edit: @jdaviescoates
-
had never checked previously, but same:

Looks like perhaps we need to add some DNS records that it isn't finding
Here is the json report
{ "WellKnownResult": { "m.server": "", "result": "No .well-known found", "CacheExpiresAt": 0 }, "DNSResult": { "SRVSkipped": false, "SRVCName": "", "SRVRecords": null, "SRVError": { "Message": "lookup _matrix._tcp.chat.uniteddiversity.coop on 8.8.8.8:53: no such host" }, "Hosts": { "chat.uniteddiversity.coop": { "CName": "chat.uniteddiversity.coop.", "Addrs": [ "89.58.52.168" ], "Error": null } }, "Addrs": [ "89.58.52.168:8448" ] }, "ConnectionReports": {}, "ConnectionErrors": { "89.58.52.168:8448": { "Message": "Get \"https://89.58.52.168:8448/_matrix/key/v2/server\": context deadline exceeded (Client.Timeout exceeded while awaiting headers)" } }, "Version": { "error": "Get \"matrix://chat.uniteddiversity.coop/_matrix/federation/v1/version\": dial tcp 89.58.52.168:8448: i/o timeout" }, "FederationOK": false }I'm on my phone but I think that gives some clues as to what needs adding.
Hopefully @staff can update the package to automate adding the necessary entries needed to make this work.
-
@murgero thanks!

So looks like everything is actually working fine


-
@murgero thanks!

So looks like everything is actually working fine


-
@jdaviescoates The tool says your matrix install is working perfectly lol
-
-
@Supaiku You have to use the matrix federated domain NOT the app domain (unless these are both the same, by default on cloudron they are NOT)
Example, my matrix server is
matrix.urgero.orgwithurgero.orgbeing the user's domain for federation.Testing
matrix.urgero.orgactually fails with that tool - buturgero.orgdoes not.Hope this helps.
Edit: @jdaviescoates
@murgero ah yes... this does seem to be the trick.
I just found the line in the docs that says:
Step 3. Federation Federation setup is automatic. Use the Federation Tester to verify that everything is setup properly. Note you must enter the server_name (like example.com) in the form field in the website and NOT the location of your home server (despite what the form says). -
 N nebulon marked this topic as a question on
N nebulon marked this topic as a question on
-
 N nebulon has marked this topic as solved on
N nebulon has marked this topic as solved on