Vaultwarden on Cloudron initial setup
-
https://docs.cloudron.io/apps/vaultwarden/
The instructions on the support page are difficult to follow / don't work:
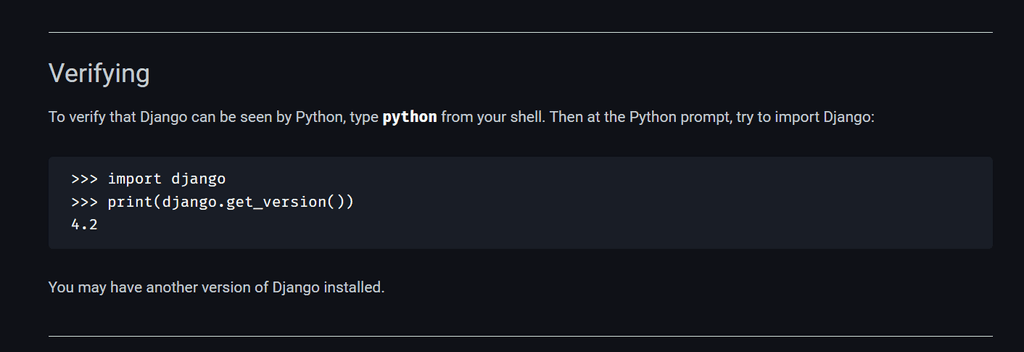
If you type the following, nothing happens:
app/code/vaultwarden hashsame with the following:
vaultwardenand this:
vaultwarden hashand also this:
Generate an Argon2id PHC string using the 'bitwarden' preset:What do we actually need to do? Also, could we include a quick animated gif for each application demonstrating the setup procedure?
-
L LoudLemur marked this topic as a question on
-
L LoudLemur has marked this topic as solved on
-
@robi said in Vaultwarden on Cloudron initial setup:
@staff please do a doc fix on the above
There is actually already a pull request from @necrevistonnezr that fixes this:
(after I had similar issues https://forum.cloudron.io/post/66377 )
-
Maybe I forgot to create a merge request? I just created (a new?) one.
I somehow don't understand Gitlab - well, I'm not really a programmer.
-
Is it ok like this: https://paste.cloudron.io/ahotevaboc.md (Patch via your hastebin)?
-
For some reason that diff does not really match the latest docs version, but I pushed a change to fix the
./vaultwarden hashcommand as you also have in the diff. Not sure if this was really all in the end. -
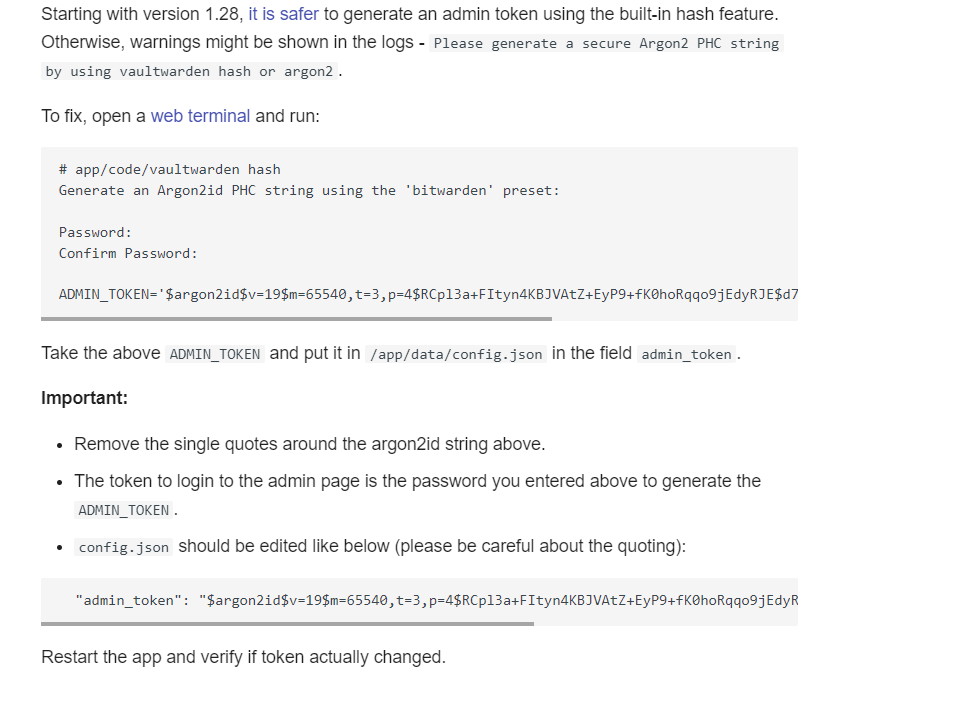
@nebulon the docs are still not right, as what's in the docs (img below) is not what a user will see when they open the web terminal.
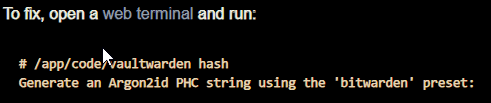
should be more like:
root@abc:/app/code# ./vaultwarden hash -
Users may not understand that they either have to copy & past the whole
/app/code/vaultwarden hashinto the command line OR just./vaultwarden hash -
Users may not understand that they either have to copy & past the whole
/app/code/vaultwarden hashinto the command line OR just./vaultwarden hash@necrevistonnezr said in Vaultwarden on Cloudron initial setup:
Users may not understand that they either have to copy & past the whole
/app/code/vaultwarden hashinto the command line OR just./vaultwarden hashTrying this didn't work:
/app/code/vaultwarden hashAs @robi said, using the following command does:
./vaultwarden hashI think part of the problem in this case is not having a clear policy about how to represent commands in the documentation.
-
@necrevistonnezr said in Vaultwarden on Cloudron initial setup:
Users may not understand that they either have to copy & past the whole
/app/code/vaultwarden hashinto the command line OR just./vaultwarden hashTrying this didn't work:
/app/code/vaultwarden hashAs @robi said, using the following command does:
./vaultwarden hashI think part of the problem in this case is not having a clear policy about how to represent commands in the documentation.
@LoudLemur Weird. If I open up the Web Terminal for Vaultwarden and copy & past
/app/code/vaultwarden hash(the whole thing!), it works for me: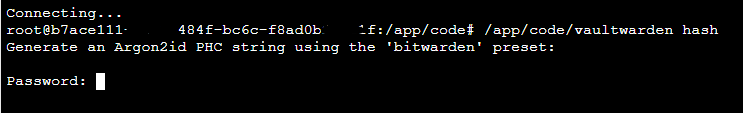
-
I just double checked this. It works fine even when run from
/tmpas current directory.root@bb442c5d-ba11-4a7f-b4ff-663720abdc2f:/tmp# /app/code/vaultwarden hash Generate an Argon2id PHC string using the 'bitwarden' preset: Password: Confirm Password: ADMIN_TOKEN='$argon2id$v=19$m=65540,t=3,p=4$vIlWyi0mBy4yIEnMZB54VWRjZN+sbamxAvvVy+ORGf0$IfU/tB2ULY97ccACP0444mSmm6rCORIWraTApg4E5uA' Generation of the Argon2id PHC string took: 268.843761ms -
I just double checked this. It works fine even when run from
/tmpas current directory.root@bb442c5d-ba11-4a7f-b4ff-663720abdc2f:/tmp# /app/code/vaultwarden hash Generate an Argon2id PHC string using the 'bitwarden' preset: Password: Confirm Password: ADMIN_TOKEN='$argon2id$v=19$m=65540,t=3,p=4$vIlWyi0mBy4yIEnMZB54VWRjZN+sbamxAvvVy+ORGf0$IfU/tB2ULY97ccACP0444mSmm6rCORIWraTApg4E5uA' Generation of the Argon2id PHC string took: 268.843761ms@girish while you may know how to make it work from any directory, the average user perspective is a very point-and-click one with direct comparison to what they see in their terminal and your docs.
So all the variations you give are just adding confusion, as it doesn't match what they see once they click the web terminal button and the new tab opens.
Hence the docs need instructions as compared to the default experience users see.
Is that clearer?
-
@girish while you may know how to make it work from any directory, the average user perspective is a very point-and-click one with direct comparison to what they see in their terminal and your docs.
So all the variations you give are just adding confusion, as it doesn't match what they see once they click the web terminal button and the new tab opens.
Hence the docs need instructions as compared to the default experience users see.
Is that clearer?
-
I just double checked this. It works fine even when run from
/tmpas current directory.root@bb442c5d-ba11-4a7f-b4ff-663720abdc2f:/tmp# /app/code/vaultwarden hash Generate an Argon2id PHC string using the 'bitwarden' preset: Password: Confirm Password: ADMIN_TOKEN='$argon2id$v=19$m=65540,t=3,p=4$vIlWyi0mBy4yIEnMZB54VWRjZN+sbamxAvvVy+ORGf0$IfU/tB2ULY97ccACP0444mSmm6rCORIWraTApg4E5uA' Generation of the Argon2id PHC string took: 268.843761msI think the documentation should present the necessary command in isolation.
This should then be accompanied by an sort of screenshot image of what the user can expect to see when they attempt it, the context and perhaps the results after successfully using the command.
Currently, what Cloudron documentation shows is only the last part, what one might see in the terminal.
The markdown used to create this could be more clear. Different use of colour could be used to indicate:
- the commands to be typed into the terminal
- the prompt/path
- the results from using the command
I will have a look around for some better custom markdown. Somebody might know some good stuff already.
root@bb442c5d-ba11-4a7f-b4ff-663720abdc2f:/tmp# /app/code/vaultwarden hash Generate an Argon2id PHC string using the 'bitwarden' preset: Password: Confirm Password: ADMIN_TOKEN='$argon2id$v=19$m=65540,t=3,p=4$vIlWyi0mBy4yIEnMZB54VWRjZN+sbamxAvvVy+ORGf0$IfU/tB2ULY97ccACP0444mSmm6rCORIWraTApg4E5uA' Generation of the Argon2id PHC string took: 268.843761msIf the documentation presents the information like this, the user has to know that there is a:
- distinction between the current path being indicated and the command itself
- how to extract the command from the other information.
If users trying to follow the documentation don't realize this, then they may attempt to follow the instructions by trying to copy/paste like this into the terminal:
root@bb442c5d-ba11-4a7f-b4ff-663720abdc2f:/tmp# /app/code/vaultwarden hashor they might even try and copy paste this:
root@bb442c5d-ba11-4a7f-b4ff-663720abdc2f:/tmp# /app/code/vaultwarden hash Generate an Argon2id PHC string using the 'bitwarden' preset:or this:
Generate an Argon2id PHC string using the 'bitwarden' preset:
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login