That fixed the problem. Thank you.
CaeruleusAqua
Posts
-
Backup failed -
Hacker AttackHello everyone,
Today we received an email stating that someone was able to log into our server and apparently also take over accounts in the Cloudron API.
The email came from https://secureforge.io/ and looked legitimate at first glance, but upon closer inspection, you can see that the site is fake.
I was able to see in the logs that users had logged into various email accounts and that our website had been deleted from the “Surfer App.”
Almost all accounts have two-factor authentication. However, my account was also visible in the logs, and it definitely has two-factor authentication enabled.
I have now taken the server completely offline for the time being.
I am asking for help here on how to solve the problem.
-
Documenso does not come up after update to 1.6.0==> Create / Migrate db Jul 28 21:46:07 ==> Setting up OIDC Jul 28 21:46:07 => Update site config Jul 28 21:46:09 2025-07-28T19:46:09Z Jul 28 21:46:09 2025-07-28T19:46:09Z Jul 28 21:46:09 2025-07-28T19:46:09Z Jul 28 21:46:09 2025-07-28T19:46:09Z Jul 28 21:46:09 \ Jul 28 21:46:09 \Prisma schema loaded from packages/prisma/schema.prisma Jul 28 21:46:09 Error: P3009 Jul 28 21:46:09 Datasource "db": PostgreSQL database "db831ce9e36aaa4dsab586a1c87917sa89", schema "public" at "postgresql:5432" Jul 28 21:46:09 Jul 28 21:46:09 migrate found failed migrations in the target database, new migrations will not be applied. Read more about how to resolve migration issues in a production database: https://pris.ly/d/migrate-resolve Jul 28 21:46:09 132 migrations found in prisma/migrations Jul 28 21:46:09 The `20250522054050_add_organisations` migration started at 2025-07-28 19:45:58.163673 UTC failed Jul 28 21:46:11 ==> Create / Migrate db Jul 28 21:46:11 ==> Setting up OIDC Jul 28 21:46:11 => Update site config Jul 28 21:46:13 => Healtheck error: Error: connect ECONNREFUSED 172.18.16.133:3000 -
Email receiving issueHello everyone,
I currently have the problem that we cannot receive various emails from exchange servers.
The problem seems to be that exchange cannot find a compatible cipher.
I have already tried to activate more ciphers in Haraka itself, but I still only get the ECDHE from nmap although RSA is definitely activated.
Could this have something to do with the reverse proxy?
nmap --script ssl-enum-ciphers -p 25 mail.byte-robotics.com Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-04-03 11:03 CEST Nmap scan report for mail.byte-robotics.com (37.221.195.213) Host is up (0.017s latency). Other addresses for mail.byte-robotics.com (not scanned): 2a03:4000:8:173:444e:10ff:fec8:1ac5 PORT STATE SERVICE 25/tcp open smtp | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_128_CCM (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_128_CCM_8 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CCM (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CCM_8 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_ARIA_128_GCM_SHA256 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_ARIA_256_GCM_SHA384 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_CAMELLIA_128_CBC_SHA256 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_CAMELLIA_256_CBC_SHA384 (ecdh_x25519) - A | TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A | compressors: | NULL | cipher preference: server | cipher preference error: Network error | TLSv1.3: | ciphers: | TLS_AKE_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A | TLS_AKE_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A | TLS_AKE_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A | cipher preference: server |_ least strength: A -
Email receiving issueUnfortunately I don't have much:
only the error from the mail itself, in the Cloudron logs was unfortunately nothing to see.Remote Server at byte-robotics.com (2a03:4000:8:173:444e:10ff:fec8:1ac5) returned '400 4.4.7 Message delayed'
31.03.2025 12:32:06 - Remote Server at byte-robotics.com (2a03:4000:8:173:444e:10ff:fec8:1ac5) returned '451 4.4.0 Primary target IP address responded with: "421 4.4.1 Connection timed out." Attempted failover to alternate host, but that did not succeed. Either there are no alternate hosts, or delivery failed to all alternate hosts. The last endpoint attempted was 2a03:4000:8:173:444e:10ff:fec8:1ac5:25'The other side said:
It caused the problem while negotiating the encryption. Your server did not initially accept any encryption from the cipher suite offered by our mail server. This was easy to see with WireShark and in a packet trace on our firewall.
I then disabled encryption to your mail server on our side, after which there was an unencrypted connection and the mail was delivered to you.
In the next step, I configured an SMTP proxy outgoing on our firewall that replaces the ciphers generated by the Exchange server with more up-to-date ones. This also resulted in an encrypted connection.
His trace from yesterday:
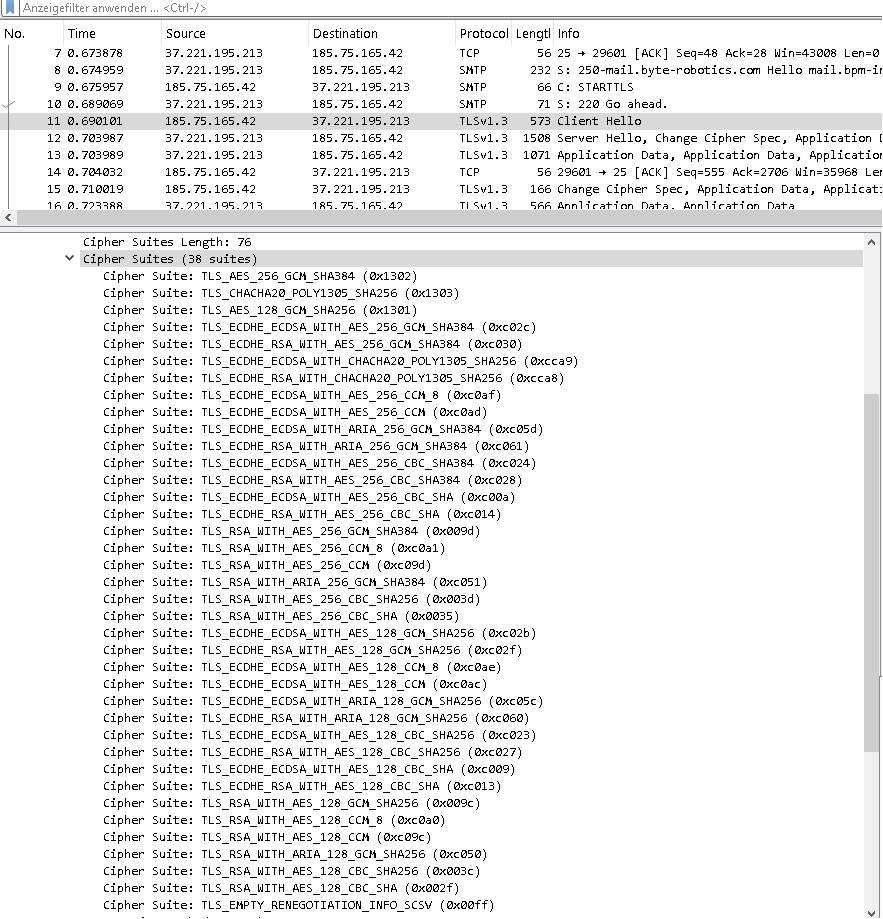
And what now is used (after modifying the firewall)
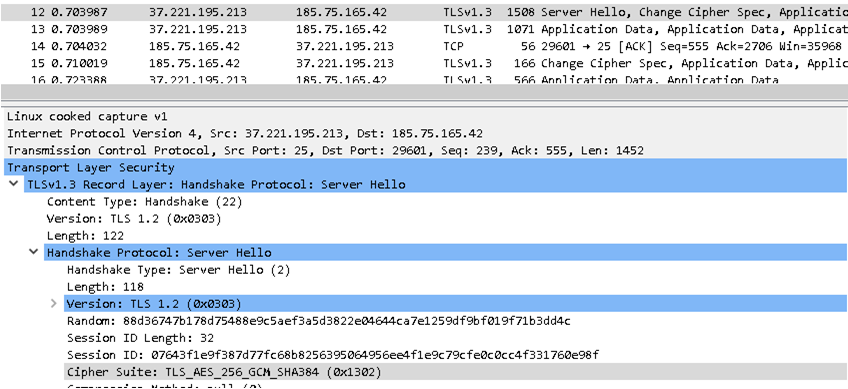
-
Backup failedMy Cloudron backups have been failing for some time now.
I use rsync for backups. Approximately 180 GB, of which approximately 145 GB is for Nextcloud.
At first, I got the following error:
Aug 29 04:34:05 box:tasks update 5586: {"percent":80.99999999999999,"message":"Copying +ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/+ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/uYbVX3iQfX9ZX3oi2MrYO+OXMcKUXMqPbEwUm2cEBTNEFKqHHl8s6HafSSU+bTUz/tkVG1KBPdeNa1nbZ66NCIIX3SkMFhT5lXOtJLWcg7Ps/TS2Uj0cyUXTWKt1+2U04XWBM0wrFxvkHTb5WCpgkU9w/JOyEKB54wsfiC8Ur0lRqnqAe9xpWM1fltgRvYlxcUZE/xKBO1jw7Yly60K3n4+wK4UGVol6qNC43rUIjLHHKQ+w/hND+OXzdXNZMUrd8FWx3N7F766WpNFbviBzGQkuL2Z0/GiI2Wgr5sD9j+h+6Z1lh6gp0Y2ECkzNT2e6-gW5xU0c/Ckc-OtdAyuVQ9W60xUXCpA2UXpg7r5T51MJjM60i9cE/S97H90ysHhQ4nXUOyMMHuEJA-UvEFS+27lB35T4sqcc/zwTOKFpZViYWCmrp2KiDklEhdpD26JQsCUiKPG43i5M/xod4paQs7-r+TZKYECcDmp8kVn9Ed8ssOOp0YL0fXhA"} Aug 29 04:34:05 box:tasks update 5586: {"percent":80.99999999999999,"message":"Copying +ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/+ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/uYbVX3iQfX9ZX3oi2MrYO+OXMcKUXMqPbEwUm2cEBTNEFKqHHl8s6HafSSU+bTUz/tkVG1KBPdeNa1nbZ66NCIIX3SkMFhT5lXOtJLWcg7Ps/TS2Uj0cyUXTWKt1+2U04XWBM0wrFxvkHTb5WCpgkU9w/JOyEKB54wsfiC8Ur0lRqnqAe9xpWM1fltgRvYlxcUZE/zg9uigbEhW0XJuMA4wmH5T6Yra2tgoieJw8lROEB6+Q/Ckc-OtdAyuVQ9W60xUXCpA2UXpg7r5T51MJjM60i9cE/S97H90ysHhQ4nXUOyMMHuEJA-UvEFS+27lB35T4sqcc/ZB7X5ucjnMRQYKClPU-VZPiI0r16vmmtVFjcxLKNlxo/wpF57b8mwK7mjJVLE13y73hRqU5OLj7s2rxoCVy2fTI/wjieJyQM44Ul8KspUoYpqbZu2NkR2kJfQvvV9+GXLEw/5MMoNG03PDeAt9nC-2e3Hp3q3+oPzs9thQTuZnQtuu0"} Aug 29 04:34:05 4:05.151Z box:tasks update 5586: {"percent":80.99999999999999,"message":"Copying +ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/+ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/uYbVX3iQfX9ZX3oi2MrYO+OXMcKUXMqPbEwUm2cEBTNEFKqHHl8s6HafSSU+bTUz/tkVG1KBPdeNa1nbZ66NCIIX3SkMFhT5lXOtJLWcg7Ps/TS2Uj0cyUXTWKt1+2U04XWBM0wrFxvkHTb5WCpgkU9w/JOyEKB54wsfiC8Ur0lRqnqAe9xpWM1fltgRvYlxcUZE/zg9uigbEhW0XJuMA4wmH5T6Yra2tgoieJw8lROEB6+Q/Ckc-OtdAyuVQ9W60xUXCpA2UXpg7r5T51MJjM60i9cE/S97H90ysHhQ4nXUOyMMHuEJA-UvEFS+27lB35T4sqcc/ZB7X5ucjnMRQYKClPU-VZPiI0r16vmmtVFjcxLKNlxo/wpF57b8mwK7mjJVLE13y73hRqU5OLj7s2rxoCVy2fTI/wjieJyQM44Ul8KspUoYpqbZu2NkR2kJfQvvV9+GXLEw/GwaF-tDFzuXbKEqImz3bXS09XdPv3f7qRgr5wKY1f18"} Aug 29 12:34:05 box:database Connection 287 error: Packets out of order. Got: 0 Expected: 2 PROTOCOL_PACKETS_OUT_OF_ORDER Aug 29 12:34:05 box:database Connection 269 error: Packets out of order. Got: 0 Expected: 2 PROTOCOL_PACKETS_OUT_OF_ORDER Aug 29 12:34:05 box:database Connection 268 error: Packets out of order. Got: 0 Expected: 2 PROTOCOL_PACKETS_OUT_OF_ORDER Aug 29 12:34:05 box:database Connection 286 error: Packets out of order. Got: 0 Expected: 2 PROTOCOL_PACKETS_OUT_OF_ORDER Aug 29 12:34:05 box:database Connection 285 error: Packets out of order. Got: 0 Expected: 2 PROTOCOL_PACKETS_OUT_OF_ORDERI then did some research and increased the memory of the Postgree and MySQL services. Since then, I have been getting the following error:
30 04:55:51 box:storage/s3 Upload progress: {"loaded":157286400,"part":17,"key":"backup/snapshot/app_da39dd94-29b5-4049-9aa5-76864ebc4608/PxfpEb7+wUmcI4HqtZyk3+S3X74-uOlD48PJw6USsRw"} Aug 30 04:55:51 box:tasks update 5599: {"percent":80.99999999999999,"message":"Uploading /home/yellowtent/appsdata/da39dd94-29b5-4049-9aa5-76864ebc4608/postgresqldump: 186M@11MBps (cloud.sdsf.de)"} Aug 30 04:55:52 box:storage/s3 Upload finished. {"ETag":"\"33160dc4ed64115c025804e2f7ee85bf\"","Location":"https://dsfsdjuh.s3.eu-central-3.ionoscloud.com/backup/snapshot/app_da39dd94-29b5-4049-9aa5-76864ebc4608/%2Bym30OeTAZmJJGSygsdvvo%2BQA-R6uI783QOB%2B9CR6-4/%2Bym30OeTAZmJJGSygsdvvo%2BQA-R6uI783QOB%2B9CR6-4/73cf3LW0lq8Gl9z%2B%2Buno9UZMcBYCsnUXKrSje95Irh8/DTXDa93HoxW4QTyb1SX%2Bv3o2u8y1K9OPHusDt43HE3E/Uml0E1jL5nx4k7awALYeoxUHGsDDj086JffucaV5Sx0/f1C3F5NR01z3YGzFF4xVmSa53CQ7YDYdoOLQhCFRZ2cXymhPiaFjrCPXeHVLWw3v/wyBpuP046dw9sW5eBM1TBBajKwevVv18UKfYc69FRow/VtjMWbuZ48jDDkj4SsNX782j8svZKhd4tIoPwc-vL9Z0QvmHRW5K0xf5twQ1eCuUXCj6nBytX86Dh6Jd81Mx0A/jL5sTQaH9cvpujCsHeY8Fwedtw%2BFYycO0KPLqEfiAZl5OuJn-TPt0zVLoreyZZhv%2B6R5uVKd1iLrngqLoanF9DbHExuqVGyMYEt65JFvA3o7Hf%2B0Kf7alzkiAlUiEWdSR-5dL84xxMSomfYCrm0EvA","key":"backup/snapshot/app_da39dd94-29b5-4049-9aa5-76864ebc4608/+ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/+ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/73cf3LW0lq8Gl9z++uno9UZMcBYCsnUXKrSje95Irh8/DTXDa93HoxW4QTyb1SX+v3o2u8y1K9OPHusDt43HE3E/Uml0E1jL5nx4k7awALYeoxUHGsDDj086JffucaV5Sx0/f1C3F5NR01z3YGzFF4xVmSa53CQ7YDYdoOLQhCFRZ2cXymhPiaFjrCPXeHVLWw3v/wyBpuP046dw9sW5eBM1TBBajKwevVv18UKfYc69FRow/VtjMWbuZ48jDDkj4SsNX782j8svZKhd4tIoPwc-vL9Z0QvmHRW5K0xf5twQ1eCuUXCj6nBytX86Dh6Jd81Mx0A/jL5sTQaH9cvpujCsHeY8Fwedtw+FYycO0KPLqEfiAZl5OuJn-TPt0zVLoreyZZhv+6R5uVKd1iLrngqLoanF9DbHExuqVGyMYEt65JFvA3o7Hf+0Kf7alzkiAlUiEWdSR-5dL84xxMSomfYCrm0EvA","Key":"backup/snapshot/app_da39dd94-29b5-4049-9aa5-76864ebc4608/+ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/+ym30OeTAZmJJGSygsdvvo+QA-R6uI783QOB+9CR6-4/73cf3LW0lq8Gl9z++uno9UZMcBYCsnUXKrSje95Irh8/DTXDa93HoxW4QTyb1SX+v3o2u8y1K9OPHusDt43HE3E/Uml0E1jL5nx4k7awALYeoxUHGsDDj086JffucaV5Sx0/f1C3F5NR01z3YGzFF4xVmSa53CQ7YDYdoOLQhCFRZ2cXymhPiaFjrCPXeHVLWw3v/wyBpuP046dw9sW5eBM1TBBajKwevVv18UKfYc69FRow/VtjMWbuZ48jDDkj4SsNX782j8svZKhd4tIoPwc-vL9Z0QvmHRW5K0xf5twQ1eCuUXCj6nBytX86Dh6Jd81Mx0A/jL5sTQaH9cvpujCsHeY8Fwedtw+FYycO0KPLqEfiAZl5OuJn-TPt0zVLoreyZZhv+6R5uVKd1iLrngqLoanF9DbHExuqVGyMYEt65JFvA3o7Hf+0Kf7alzkiAlUiEWdSR-5dL84xxMSomfYCrm0EvA","Bucket":"dsfsdjuh"} Aug 30 04:55:52 /home/yellowtent/box/node_modules/aws-sdk/lib/services/s3.js:712 Aug 30 04:55:52 resp.error = AWS.util.error(new Error(), { Aug 30 04:55:52 ^ Aug 30 04:55:52 Aug 30 04:55:52 400: null Aug 30 04:55:52 at Request.extractError (/home/yellowtent/box/node_modules/aws-sdk/lib/services/s3.js:712:35) Aug 30 04:55:52 at Request.callListeners (/home/yellowtent/box/node_modules/aws-sdk/lib/sequential_executor.js:106:20) Aug 30 04:55:52 at Request.emit (/home/yellowtent/box/node_modules/aws-sdk/lib/sequential_executor.js:78:10) Aug 30 04:55:52 at Request.emit (/home/yellowtent/box/node_modules/aws-sdk/lib/request.js:686:14) Aug 30 04:55:52 at Request.transition (/home/yellowtent/box/node_modules/aws-sdk/lib/request.js:22:10) Aug 30 04:55:52 at AcceptorStateMachine.runTo (/home/yellowtent/box/node_modules/aws-sdk/lib/state_machine.js:14:12) Aug 30 04:55:52 at /home/yellowtent/box/node_modules/aws-sdk/lib/state_machine.js:26:10 Aug 30 04:55:52 at Request.<anonymous> (/home/yellowtent/box/node_modules/aws-sdk/lib/request.js:38:9) Aug 30 04:55:52 at Request.<anonymous> (/home/yellowtent/box/node_modules/aws-sdk/lib/request.js:688:12) Aug 30 04:55:52 at Request.callListeners (/home/yellowtent/box/node_modules/aws-sdk/lib/sequential_executor.js:116:18) { Aug 30 04:55:52 code: 400, Aug 30 04:55:52 region: null, Aug 30 04:55:52 time: 2025-08-30T02:55:53.849Z, Aug 30 04:55:52 requestId: null, Aug 30 04:55:52 extendedRequestId: undefined, Aug 30 04:55:52 cfId: undefined, Aug 30 04:55:52 statusCode: 400, Aug 30 04:55:52 retryable: false, Aug 30 04:55:52 retryDelay: 20000 Aug 30 04:55:52 } Aug 30 04:55:52 Aug 30 04:55:52 Node.js v20.18.0 Aug 30 04:55:53 box:shell backuptask: /usr/bin/sudo -S -E --close-from=4 /home/yellowtent/box/src/scripts/backupupload.js snapshot/app_da39dd94-29b5-4049-9aa5-76864ebc4608 rsync {"localRoot":"/home/yellowtent/appsdata/da39dd94-29b5-4049-9aa5-76864ebc4608","layout":[]} errored BoxError: backuptask exited with code 1 signal null Aug 30 04:55:53 at ChildProcess.<anonymous> (/home/yellowtent/box/src/shell.js:137:19) Aug 30 04:55:53 at ChildProcess.emit (node:events:519:28) Aug 30 04:55:53 at ChildProcess.emit (node:domain:488:12) Aug 30 04:55:53 at ChildProcess._handle.onexit (node:internal/child_process:294:12) { Aug 30 04:55:53 reason: 'Shell Error', Aug 30 04:55:53 details: {}, Aug 30 04:55:53 code: 1, Aug 30 04:55:53 signal: null Aug 30 04:55:53 } Aug 30 04:55:53 box:backuptask runBackupUpload: backuptask crashed BoxError: backuptask exited with code 1 signal null Aug 30 04:55:53 at ChildProcess.<anonymous> (/home/yellowtent/box/src/shell.js:137:19) Aug 30 04:55:53 at ChildProcess.emit (node:events:519:28) Aug 30 04:55:53 at ChildProcess.emit (node:domain:488:12) Aug 30 04:55:53 at ChildProcess._handle.onexit (node:internal/child_process:294:12) { Aug 30 04:55:53 reason: 'Shell Error', Aug 30 04:55:53 details: {}, Aug 30 04:55:53 code: 1, Aug 30 04:55:53 signal: null Aug 30 04:55:53 } Aug 30 04:55:53 box:backuptask fullBackup: app cloud.sdsf.de backup finished. Took 8402.405 seconds Aug 30 04:55:53 box:locks write: current locks: {"backup_task":null} Aug 30 04:55:53 box:locks release: app_da39dd94-29b5-4049-9aa5-76864ebc4608 Aug 30 04:55:53 box:taskworker Task took 14153.117 seconds Aug 30 04:55:53 box:tasks setCompleted - 5599: {"result":null,"error":{"stack":"BoxError: Backuptask crashed\n at runBackupUpload (/home/yellowtent/box/src/backuptask.js:170:15)\n at process.processTicksAndRejections (node:internal/process/task_queues:95:5)\n at async uploadAppSnapshot (/home/yellowtent/box/src/backuptask.js:369:5)\n at async backupAppWithTag (/home/yellowtent/box/src/backuptask.js:391:5)","name":"BoxError","reason":"Internal Error","details":{},"message":"Backuptask crashed"}} Aug 30 04:55:53 box:tasks update 5599: {"percent":100,"result":null,"error":{"stack":"BoxError: Backuptask crashed\n at runBackupUpload (/home/yellowtent/box/src/backuptask.js:170:15)\n at process.processTicksAndRejections (node:internal/process/task_queues:95:5)\n at async uploadAppSnapshot (/home/yellowtent/box/src/backuptask.js:369:5)\n at async backupAppWithTag (/home/yellowtent/box/src/backuptask.js:391:5)","name":"BoxError","reason":"Internal Error","details":{},"message":"Backuptask crashed"}} Aug 30 04:55:53 BoxError: Backuptask crashed Aug 30 04:55:53 at runBackupUpload (/home/yellowtent/box/src/backuptask.js:170:15) Aug 30 04:55:53 at process.processTicksAndRejections (node:internal/process/task_queues:95:5) Aug 30 04:55:53 at async uploadAppSnapshot (/home/yellowtent/box/src/backuptask.js:369:5) Aug 30 04:55:53 at async backupAppWithTag (/home/yellowtent/box/src/backuptask.js:391:5) -
Hacker AttackI can't do much more right now. I have reported the whole thing to the insurance company and their service provider is now investigating it.
-
Hacker AttackSorry Wrong Mail:
Return-Path: <010001990f0e42e0-62660a78-1ce2-4634-8ffc-9bf6a8298fcc-000000@amazonses.com> Delivered-To: changedtosomething@softdata.com Received: from mail.softdata.com ([127.0.0.1]) (using TLSv1.3 with cipher TLS_AES_256_GCM_SHA384 (256/256 bits)) by mail.softdata.com with LMTPS id ADgZHQ8UuGjJEAAAhyJ/EA (envelope-from <010001990f0e42e0-62660a78-1ce2-4634-8ffc-9bf6a8298fcc-000000@amazonses.com>) for <changedtosomething@softdata.com>; Wed, 03 Sep 2025 10:10:23 +0000 Received: (Haraka outbound); Wed, 03 Sep 2025 10:10:23 +0000 Authentication-Results: mail.softdata.com; spf=pass smtp.mailfrom=amazonses.com Received-SPF: Pass (mail.softdata.com: domain of amazonses.com designates 54.240.48.99 as permitted sender) receiver=mail.softdata.com; identity=mailfrom; client-ip=54.240.48.99 helo=a48-99.smtp-out.amazonses.com; envelope-from=<010001990f0e42e0-62660a78-1ce2-4634-8ffc-9bf6a8298fcc-000000@amazonses.com> Received-SPF: None (mail.softdata.com: domain of a48-99.smtp-out.amazonses.com does not designate 54.240.48.99 as permitted sender) receiver=mail.softdata.com; identity=helo; client-ip=54.240.48.99 helo=a48-99.smtp-out.amazonses.com; envelope-from=<010001990f0e42e0-62660a78-1ce2-4634-8ffc-9bf6a8298fcc-000000@amazonses.com> X-Envelope-To: changedtosomething@softdata.com Received: from a48-99.smtp-out.amazonses.com (a48-99.smtp-out.amazonses.com [54.240.48.99]) by mail.softdata.com (Haraka) with ESMTPS id 18F6A514-7F45-48C1-A61F-FC6CF89B4ED4.1 envelope-from <010001990f0e42e0-62660a78-1ce2-4634-8ffc-9bf6a8298fcc-000000@amazonses.com> tls TLS_AES_256_GCM_SHA384; Wed, 03 Sep 2025 10:10:19 +0000 DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/simple; s=u5yoimczihtcw4zjts7o5kzmsmlfq6au; d=secureforge.io; t=1756894217; h=Content-Type:MIME-Version:From:To:Subject:Date:Message-ID:Reply-To; bh=i4RKBlI36Eh1jCg4OHgr2zEj3kldd0g0/rwYs6Frg20=; b=iuImrBoooXebgjTBsMNc21l8o1y3yxscEEhAJsu+o3HfmLN/DCGXfE3CjOkfxVEO D+ux2sgcNSyVVhskA0TXV7gmWGVpXtS1BQZEMR1KyXTZb68RT+oVcEROZ1iHTtxKnHy yPYNAS0NwSTcIM/7w+YLa7SJkzx3KJipChg7+6XI5saT/FyyUdzHOgxqMG4CA5jThAp Heas82IFkuDr3laFZhPiX/rDJCMWv0XkUJohBLc/8pCsjZlE2HNwrDlpxyGnSYlVK5D r1fTR4ScHjU5eJsbIMBMpxuukinwSWKYSvsFDLxTqcaqAnWA4aBqB9SA3pc5YVJAEBO HsBPS+1l5Q== DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/simple; s=6gbrjpgwjskckoa6a5zn6fwqkn67xbtw; d=amazonses.com; t=1756894217; h=Content-Type:MIME-Version:From:To:Subject:Date:Message-ID:Reply-To:Feedback-ID; bh=i4RKBlI36Eh1jCg4OHgr2zEj3kldd0g0/rwYs6Frg20=; b=DNOPGmBqjUGeq2/2caQDulWjgRsT7BSV7HbOXeQjVUqrN+w58x1XpYY8Jbpk25yw DTzSypnFOyL+tdowBA51KPtTMN0CJ6XTE3Qh3roIaAsNL/TvlDfJ9NhLFPZ5xnM9gQY G47vGUpVNbGHnv21NdPHHDs5mIyWY0ln9iZjySIg= Content-Type: multipart/alternative; boundary="===============6338578617582795644==" MIME-Version: 1.0 From: Sean Whitaker <sean@secureforge.io> To: changedtosomething@softdata.com Subject: Full account takeover on byteRobotics API Date: Wed, 3 Sep 2025 10:10:16 +0000 Message-ID: <010001990f0e42e0-62660a78-1ce2-4634-8ffc-9bf6a8298fcc-000000@email.amazonses.com> Reply-To: sean@secureforge.io Feedback-ID: ::1.us-east-1.39BSdkv6G4z3E8aSaLuVz+9W8p+wYTmQZCv5YQp0+aw=:AmazonSES X-SES-Outgoing: 2025.09.03-54.240.48.99 X-Spam-Checker-Version: SpamAssassin 4.0.0 (2022-12-13) on b29685ce0917 X-Spam-Status: No, score=0.8 required=5.0 tests=DKIM_SIGNED,DKIM_VALID, DKIM_VALID_AU,DKIM_VALID_EF,HEADER_FROM_DIFFERENT_DOMAINS,HTML_MESSAGE, RCVD_IN_DNSWL_NONE,RCVD_IN_MSPIKE_H4,RCVD_IN_MSPIKE_WL,SPF_HELO_NONE, SPF_PASS autolearn=no autolearn_force=no version=4.0.0 X-Spam-Report: * -0.0 RCVD_IN_MSPIKE_H4 RBL: Very Good reputation (+4) * [54.240.48.99 listed in wl.mailspike.net] * -0.0 RCVD_IN_DNSWL_NONE RBL: Sender listed at https://www.dnswl.org/, no * trust * [54.240.48.99 listed in list.dnswl.org] * -0.0 SPF_PASS SPF: sender matches SPF record * 0.0 SPF_HELO_NONE SPF: HELO does not publish an SPF Record * -0.1 DKIM_VALID_AU Message has a valid DKIM or DK signature from author's * domain * -0.1 DKIM_VALID Message has at least one valid DKIM or DK signature * -0.1 DKIM_VALID_EF Message has a valid DKIM or DK signature from * envelope-from domain * 0.1 DKIM_SIGNED Message has a DKIM or DK signature, not necessarily * valid * -0.0 RCVD_IN_MSPIKE_WL Mailspike good senders * 1.0 HEADER_FROM_DIFFERENT_DOMAINS From and EnvelopeFrom 2nd level mail * domains are different * 0.0 HTML_MESSAGE BODY: HTML included in message -
Hacker AttackReturn-Path: <sean@secureforge.io> Delivered-To: changedtosomething@softdata.com Received: from mail.softdata.com ([127.0.0.1]) (using TLSv1.3 with cipher TLS_AES_256_GCM_SHA384 (256/256 bits)) by mail.softdata.com with LMTPS id J0AtGAcguGi+EgAAhyJ/EA (envelope-from <sean@secureforge.io>) for <changedtosomething@softdata.com>; Wed, 03 Sep 2025 11:01:27 +0000 Received: (Haraka outbound); Wed, 03 Sep 2025 11:01:27 +0000 Authentication-Results: mail.softdata.com; spf=pass smtp.mailfrom=secureforge.io Received-SPF: Pass (mail.softdata.com: domain of secureforge.io designates 2607:f8b0:4864:20::535 as permitted sender) receiver=mail.softdata.com; identity=mailfrom; client-ip=2607:f8b0:4864:20::535 helo=mail-pg1-x535.google.com; envelope-from=<sean@secureforge.io> Received-SPF: None (mail.softdata.com: domain of mail-pg1-x535.google.com does not designate 2607:f8b0:4864:20::535 as permitted sender) receiver=mail.softdata.com; identity=helo; client-ip=2607:f8b0:4864:20::535 helo=mail-pg1-x535.google.com; envelope-from=<sean@secureforge.io> X-Envelope-To: changedtosomething@softdata.com Received: from mail-pg1-x535.google.com (mail-pg1-x535.google.com [2607:f8b0:4864:20::535]) by mail.softdata.com (Haraka) with ESMTPS id F167E284-C87C-48F6-84E6-BB725B512079.1 envelope-from <sean@secureforge.io> tls TLS_AES_256_GCM_SHA384; Wed, 03 Sep 2025 11:01:23 +0000 Received: by mail-pg1-x535.google.com with SMTP id 41be03b00d2f7-b49cf21320aso6824905a12.1 for <changedtosomething@softdata.com>; Wed, 03 Sep 2025 04:01:22 -0700 (PDT) DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=secureforge.io; s=google; t=1756897279; x=1757502079; darn=softdata.com; h=to:subject:message-id:date:from:mime-version:references:in-reply-to :from:to:cc:subject:date:message-id:reply-to; bh=gCCeFn2TSijhXXXnfhXDF9SsCOo5SiSyBBS7VOg+UdQ=; b=KKvsRpdQUDOhxikSSfhvOPPJSQ81ZWfzrpywFtrDGHi1+YKcaah5QECKKdjnNkA3Of Dr5f6S02lRcM/ufRIcbzm8vZZA5U647VeRvC+WQ9Pwwn6t9zgXZAAJ6DzJOrYfAL0UEv NsORzeW9whYvCCzRTDitY48//qdNcWyQ+cXfJubQY/qhy8bBmlhFIclHDXKONbNb2/LL G5hVSMROT+4jIcN7vQxYkY5KfSN8hjxoiACPM9nYrBCICxYH+Lx1f0Ut8FgWM9AFhQjU 33xruBEXHszQi67DHgtchbdMef6rUC7lWkxm2ciEfTWHVIhhbjQhLTkkajIszA459k+T g9Qw== X-Google-DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=1e100.net; s=20230601; t=1756897279; x=1757502079; h=to:subject:message-id:date:from:mime-version:references:in-reply-to :x-gm-message-state:from:to:cc:subject:date:message-id:reply-to; bh=gCCeFn2TSijhXXXnfhXDF9SsCOo5SiSyBBS7VOg+UdQ=; b=hERQ0lcyKZwZyTNOu6D8XR6M3U7sszJqa+alvVOfqiG4OEaSWVUlBSSq9Jd/RUsXWw lgzE9WlyLgk+IBXekVxvykR+FlHyQrOHRIO8iqZ0xKAwtk+LzPrX8r8h0yvUFSR4Fje9 R4BdPfNEeSWbZxG3eHQYaYDaXgRTLgzB1H5MxQqgtF0ZHvMQTeTBpA6/AVnP1RtGz4iv ryPRYpp8KuwCEyYY8aEbv1UuGndfX/+bsEpLxwA2Vk63qOPowHKZF23LXBh0/O66RMYN RpHba58G0FEIiM1AdW3cfWguTsQhy+VPH+mFeG42K25z2ePALU96OS3f/ugEzmFvFaN+ 2UsQ== X-Gm-Message-State: AOJu0Yxq4mMqhkDAG8ecs6wG3fSdEI5X3BmkgoXm32xCSx5GRTfUC3N6 TSZpVdept9RVJS2n62db5x26QCMnV6KubmpTUGpwu3e2cf2I5XsrNNoxN8lqwtyBszU5PdsSCt6 BIFYTJbRqUJeATa96DQVsBFDivQWrp0MY4SJBu+DOSUuXpBO5PYYitpo= X-Gm-Gg: ASbGncsi/munX5KOTa6BU3UNmdhaK2ZekTcXafj3nMcOUUNtB/5YE1ba8omaW4hhHKf 467Yb7eIG0b0AX0+J4klJYXjcMxcplzFhX9X9sXBKwgyoEdlPjtu9G/wMl4V9tBabKlNsT5Agef 8N/ysfwsnTNUcru9BS24kqGAH8OfnQ80FtBIeYiF7KgeLuTXFELudn1ZuaY62x2ByGMZ73XP5rR VEfr2EvFVZGBheOjtOzocfEnkCr1rFXCGs4 X-Google-Smtp-Source: AGHT+IE2uTk2zt//sQSgg1yt7S12v3oOUESatehax8RSykQAxopFTCKEdVQxZ+mn+2nu+9cojVBfKgxI5Q5hc2bqQq4= X-Received: by 2002:a17:90b:48c3:b0:327:7334:403d with SMTP id 98e67ed59e1d1-328156de6b3mr21560976a91.26.1756897278858; Wed, 03 Sep 2025 04:01:18 -0700 (PDT) Received: from 498586711441 named unknown by gmailapi.google.com with HTTPREST; Wed, 3 Sep 2025 11:01:18 +0000 Received: from 498586711441 named unknown by gmailapi.google.com with HTTPREST; Wed, 3 Sep 2025 11:01:18 +0000 In-Reply-To: <016601dc1cc1$5563ec30$002bc490$@softdata.com> References: <016601dc1cc1$5563ec30$002bc490$@softdata.com> MIME-Version: 1.0 From: sean@secureforge.io Date: Wed, 3 Sep 2025 11:01:18 +0000 X-Gm-Features: Ac12FXxry76BDyT7JH0lL-ZT5F7SYF2lZsBkK-9Kuq_zjvMGxRrg8G6Pp9gtzjU Message-ID: <CAAEQtJ7MYqVjcB2NN659eYXiPnTH9dFKWCDKNYLvd6jvnRCmcQ@mail.gmail.com> Subject: AW: Full account takeover on byteRobotics API To: changedtosomething@softdata.com Content-Type: multipart/alternative; boundary="00000000000036a82d063de38655" X-Spam-Checker-Version: SpamAssassin 4.0.0 (2022-12-13) on b29685ce0917 X-Spam-Status: No, score=-0.2 required=5.0 tests=DKIM_SIGNED,DKIM_VALID, DKIM_VALID_AU,DKIM_VALID_EF,HTML_MESSAGE,RCVD_IN_DNSWL_NONE, SPF_HELO_NONE,SPF_PASS autolearn=ham autolearn_force=no version=4.0.0 X-Spam-Report: * -0.0 SPF_PASS SPF: sender matches SPF record * 0.0 SPF_HELO_NONE SPF: HELO does not publish an SPF Record * -0.1 DKIM_VALID_AU Message has a valid DKIM or DK signature from author's * domain * -0.1 DKIM_VALID Message has at least one valid DKIM or DK signature * -0.1 DKIM_VALID_EF Message has a valid DKIM or DK signature from * envelope-from domain * 0.1 DKIM_SIGNED Message has a DKIM or DK signature, not necessarily * valid * 0.0 HTML_MESSAGE BODY: HTML included in message * -0.0 RCVD_IN_DNSWL_NONE RBL: Sender listed at https://www.dnswl.org/, no * trust * [2607:f8b0:4864:20:0:0:0:535 listed in] [list.dnswl.org] -
Error 400 in backup process with Ionos S3 Object StorageI've had the same problem since a week ago. The strange thing is that everything had been running flawlessly for a year. However, we recently set up a second Cloudron. The backup is stored on a different bucket and also has its own key. The problem occurs on both servers. Unfortunately, it's not deterministic.
03:00:33 box:storage/s3 Upload progress: {"loaded":95400493056,"part":920,"key":"backup/snapshot/app_da39dd94-29b5-4049-9aa5-76864ebc4608.tar.gz.enc"} Oct 16 03:00:33 /home/yellowtent/box/node_modules/aws-sdk/lib/services/s3.js:712 Oct 16 03:00:33 resp.error = AWS.util.error(new Error(), { Oct 16 03:00:33 ^ Oct 16 03:00:33 Oct 16 03:00:33 400: null Oct 16 03:00:33 at Request.extractError (/home/yellowtent/box/node_modules/aws-sdk/lib/services/s3.js:712:35) Oct 16 03:00:33 at Request.callListeners (/home/yellowtent/box/node_modules/aws-sdk/lib/sequential_executor.js:106:20) Oct 16 03:00:33 at Request.emit (/home/yellowtent/box/node_modules/aws-sdk/lib/sequential_executor.js:78:10) Oct 16 03:00:33 at Request.emit (/home/yellowtent/box/node_modules/aws-sdk/lib/request.js:686:14) Oct 16 03:00:33 at Request.transition (/home/yellowtent/box/node_modules/aws-sdk/lib/request.js:22:10) Oct 16 03:00:33 at AcceptorStateMachine.runTo (/home/yellowtent/box/node_modules/aws-sdk/lib/state_machine.js:14:12) Oct 16 03:00:33 at /home/yellowtent/box/node_modules/aws-sdk/lib/state_machine.js:26:10 Oct 16 03:00:33 at Request.<anonymous> (/home/yellowtent/box/node_modules/aws-sdk/lib/request.js:38:9) Oct 16 03:00:33 at Request.<anonymous> (/home/yellowtent/box/node_modules/aws-sdk/lib/request.js:688:12) Oct 16 03:00:33 at Request.callListeners (/home/yellowtent/box/node_modules/aws-sdk/lib/sequential_executor.js:116:18) { Oct 16 03:00:33 code: 400, Oct 16 03:00:33 region: null, Oct 16 03:00:33 time: 2025-10-16T01:00:34.559Z, Oct 16 03:00:33 requestId: null, Oct 16 03:00:33 extendedRequestId: undefined, Oct 16 03:00:33 cfId: undefined, Oct 16 03:00:33 statusCode: 400, Oct 16 03:00:33 retryable: false, Oct 16 03:00:33 retryDelay: 20000 Oct 16 03:00:33 } Oct 16 03:00:33 Oct 16 03:00:33 Node.js v20.18.0 Oct 16 03:00:34 box:shell backuptask: /usr/bin/sudo -S -E --close-from=4 /home/yellowtent/box/src/scripts/backupupload.js snapshot/app_da39dd94-29b5-4049-9aa5-76864ebc4608 tgz {"localRoot":"/home/yellowtent/appsdata/da39dd94-29b5-4049-9aa5-76864ebc4608","layout":[]} errored BoxError: backuptask exited with code 1 signal null Oct 16 03:00:34 at ChildProcess.<anonymous> (/home/yellowtent/box/src/shell.js:137:19) Oct 16 03:00:34 at ChildProcess.emit (node:events:519:28) Oct 16 03:00:34 at ChildProcess.emit (node:domain:488:12) Oct 16 03:00:34 at ChildProcess._handle.onexit (node:internal/child_process:294:12) { Oct 16 03:00:34 reason: 'Shell Error', Oct 16 03:00:34 details: {}, Oct 16 03:00:34 code: 1, Oct 16 03:00:34 signal: null Oct 16 03:00:34 } Oct 16 03:00:34 box:backuptask runBackupUpload: backuptask crashed BoxError: backuptask exited with code 1 signal null Oct 16 03:00:34 at ChildProcess.<anonymous> (/home/yellowtent/box/src/shell.js:137:19) Oct 16 03:00:34 at ChildProcess.emit (node:events:519:28) Oct 16 03:00:34 at ChildProcess.emit (node:domain:488:12) Oct 16 03:00:34 at ChildProcess._handle.onexit (node:internal/child_process:294:12) { Oct 16 03:00:34 reason: 'Shell Error', Oct 16 03:00:34 details: {}, Oct 16 03:00:34 code: 1, Oct 16 03:00:34 signal: null Oct 16 03:00:34 }
