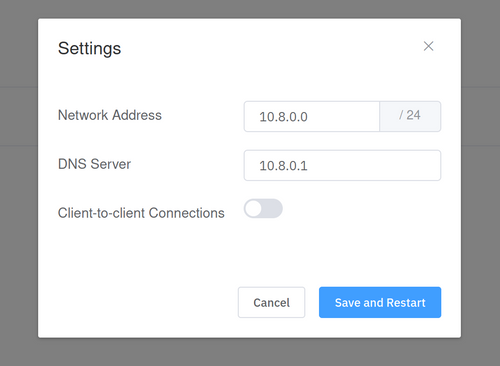
OpenVPN Admin UI
-
@nebulon has added an initial admin interface to the openvpn app. The app is not published with his changes yet, so don't go looking for it yet.
Next step, we will try to make a UI that lets one set a custom internal DNS server. Another idea depending on how easy/hard it is , is to set a custom block list. Something like https://github.com/notracking/hosts-blocklists . There is also a mega block list here - https://gist.github.com/OnlyInAmerica/75e200886e02e7562fa1.
Just putting this here, in case someone had ideas/suggestions.
-
A very very good blocklist:
https://oisd.nl, specifically https://dbl.oisd.nl
Comments and reviews: https://www.reddit.com/r/oisd_blocklist/comments/gjn972/abpoisdnl_internets_1_domain_blocklist/
-
-
@mehdi said in OpenVPN Admin UI:
I would love to take a look at this admin interface, a screenshot maybe ?
I haven't seen it myself
 I will post a screenshot when I am looking to add this DNS blocklist feature.
I will post a screenshot when I am looking to add this DNS blocklist feature.@mehdi Since you wrote the original app, do you have any opinion on how we should integrate this feature? It looks like we can take two approaches:
- Either integrate an ad blocker into the VPN app itself. I guess we can have some cron job periodically pull down the block list and update the dnsmasq host entries
OR
- Just allow a way to set a external DNS server. That external DNS server can possibly be another app on Cloudron or some pi-hole or something else.
-
@mehdi said in OpenVPN Admin UI:
I would love to take a look at this admin interface, a screenshot maybe ?
I haven't seen it myself
 I will post a screenshot when I am looking to add this DNS blocklist feature.
I will post a screenshot when I am looking to add this DNS blocklist feature.@mehdi Since you wrote the original app, do you have any opinion on how we should integrate this feature? It looks like we can take two approaches:
- Either integrate an ad blocker into the VPN app itself. I guess we can have some cron job periodically pull down the block list and update the dnsmasq host entries
OR
- Just allow a way to set a external DNS server. That external DNS server can possibly be another app on Cloudron or some pi-hole or something else.
Either integrate an ad blocker into the VPN app itself. I guess we can have some cron job periodically pull down the block list and update the dnsmasq host entries
The problem with this approach is that for, I believe, most users of Cloudron's OpenVPN, it would be completely overkill
 I think most users just want a VPN, and an interface to configure DNS stuff would just be confusing, like off-topic.
I think most users just want a VPN, and an interface to configure DNS stuff would just be confusing, like off-topic.Just allow a way to set a external DNS server. That external DNS server can possibly be another app on Cloudron or some pi-hole or something else.
That would be OK. I think a configuration field to allow to chose the DNS server that OpenVPN sets on clients (or more precisely the upstream DNS server of dnsmasq, so we can keep the local hostnames) makes total sense.
However, using this to achieve the desired functionality would not be trivial, as hosting the Pi-hole on the same Cloudron would not really be doable: Pi-hole docs explicitly discourages exposing the DNS port on public networks, and I don't really see a way to expose it from a hypothetical Pi-hole app to OpenVPN, but not to the rest of the world

Long story short, I think that there is no clean and easy way to implement this at the moment. What I suggest would be:
- on the short term, allow more configurability of dnsmasq, so users who are willing to get their hands dirty can install their own Pi-hole or something else, or even manually add blocklists to dnsmasq if they can tweak the config files
- on the long term, allow apps to define default firewalling rules in their manifest. For example, a Pi-hole app could expose its DNS port but only to local clients, not to the global internet. And I believe a few other apps (or potential apps) could definitely benefit from such a feature
-
While the specific DNS option would be good for VPN, the Admin UI could include other services such as:
- wireguard-RS,
- v2ray
and perhaps even some proxy options like - shadowsocksX.
As an all in one solution, a rebrand to CloudronVPN wouldn't be out of the question.
Services such as Outline have their own management app to setup up servers and manage usage and clients that ease the connection process. Fork it.
-
Another remark here is to think about how to design this UI so that it is easily portable to other apps that don't necessarily have a UI, but would need one for being ported into a Cloudron App.
Then include it in the build/tool chain as an option when making new Apps.