Setting ['login_rate_limit'] to prevent brute force login attacks in Roundcube
-
I realized recently that there's a setting in Roundcube that can help prevent brute force login attacks.
I went to see if this was set in the Roundcube package to figure if it was adequate or if I should add it into the customization file.
I didn't find anything in the Cloudron Roundcube App config template which contains
$config['login_rate_limit'] = 3;(which is the default in Roundcube apparently, according to their repo on GitHub).So I am just wondering two things...
-
Is this setting actually enabled in the Roundcube package and I just missed it?
-
Is the brute-force attack limited by other Cloudron security settings perhaps which means it's not necessary in the app itself?
-
If it's not set, should it be perhaps considered in the app package?
I'll set it manually in the custom config file if needed, but wanted to check on this first with just what I found from some quick research.
-
-
I realized recently that there's a setting in Roundcube that can help prevent brute force login attacks.
I went to see if this was set in the Roundcube package to figure if it was adequate or if I should add it into the customization file.
I didn't find anything in the Cloudron Roundcube App config template which contains
$config['login_rate_limit'] = 3;(which is the default in Roundcube apparently, according to their repo on GitHub).So I am just wondering two things...
-
Is this setting actually enabled in the Roundcube package and I just missed it?
-
Is the brute-force attack limited by other Cloudron security settings perhaps which means it's not necessary in the app itself?
-
If it's not set, should it be perhaps considered in the app package?
I'll set it manually in the custom config file if needed, but wanted to check on this first with just what I found from some quick research.
-
-
@d19dotca I don't use this in my roundcube but wouldn't setting a rate limit in LDAP (obviously only apps that support LDAP login would work here) be a better option?
-
@murgero I agree, however it doesn’t seem that Cloudron’s built-in rate limiting helps cover this use-case.
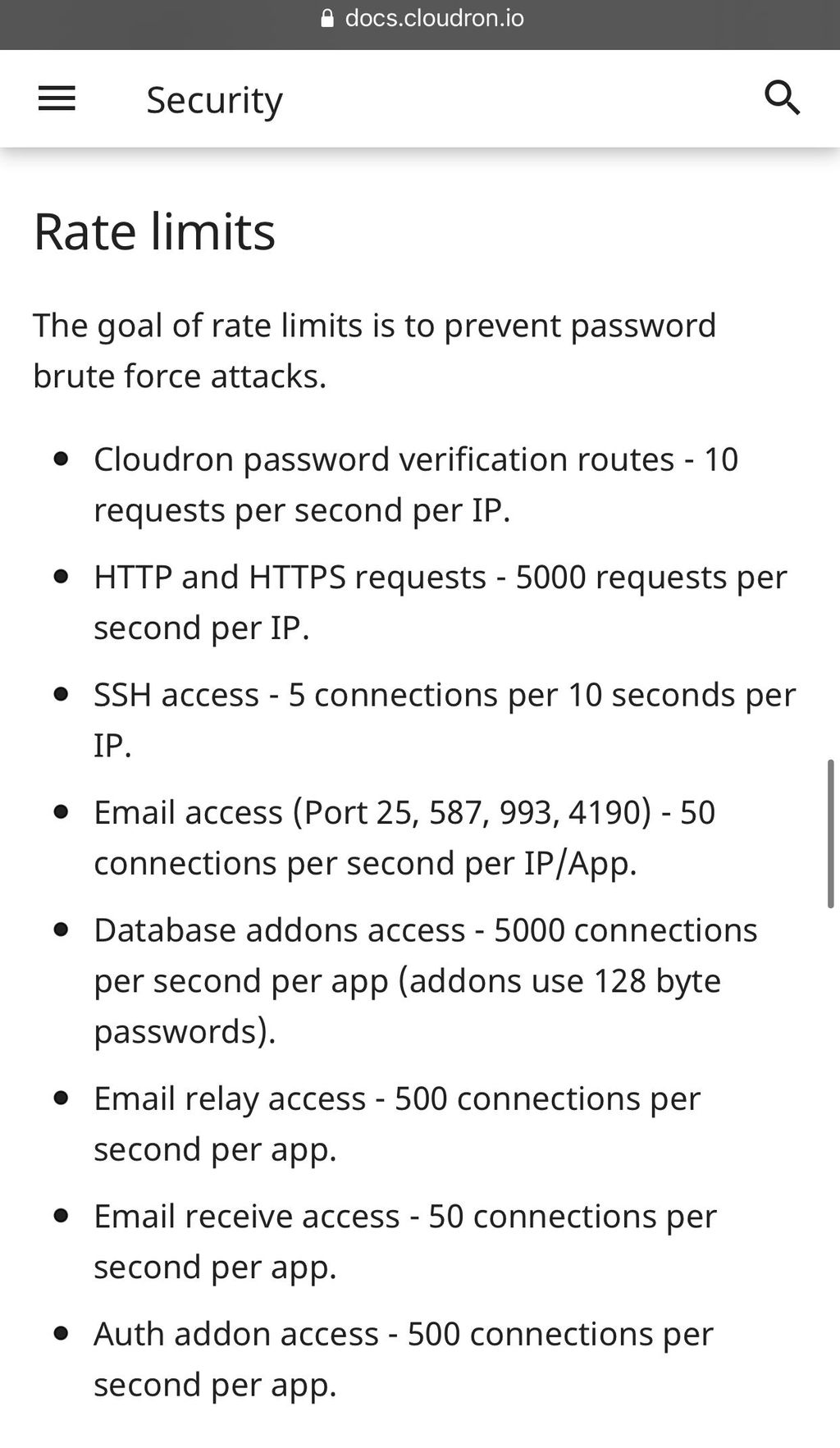
Am I maybe missing a configuration that covers that?
-
@murgero Ah okay. If true, that seems way too low of a rate limit to really be effective at all. Because that’d mean that one user could try to login 10 times per second? I’d think it should be at least 10 times per minute especially since it’s per IP. If almost prefer it to be more like 5 a minute tops, personally.
-
@murgero Ah okay. If true, that seems way too low of a rate limit to really be effective at all. Because that’d mean that one user could try to login 10 times per second? I’d think it should be at least 10 times per minute especially since it’s per IP. If almost prefer it to be more like 5 a minute tops, personally.
@d19dotca said in Setting ['login_rate_limit'] to prevent brute force login attacks in Roundcube:
If almost prefer it to be more like 5 a minute tops, personally
That’s why I suggested in this post https://forum.cloudron.io/topic/4723/what-s-coming-in-cloudron-6-3/4 to make all the rate limiting configurable

-
@d19dotca said in Setting ['login_rate_limit'] to prevent brute force login attacks in Roundcube:
If almost prefer it to be more like 5 a minute tops, personally
That’s why I suggested in this post https://forum.cloudron.io/topic/4723/what-s-coming-in-cloudron-6-3/4 to make all the rate limiting configurable

@imc67 Ah okay, that’s actually what got me looking into Roundcube in particular and led me down this path. Haha. I agree, the rate limiting needs to be customizable. I just thought maybe I can do it at the app level (which seems like I can for Roundcube at least but not sure if this is overwritten by the system settings). Maybe I’ll just wait until it’s baked into Cloudron to configure properly down the road.

