Tutanota - Secure email for everybody
-
This looks like a good option for those concerned with encryption.
I'm mostly just adding this as imho every single open source webmail client in existence leaves a LOT to be desired

And so the more options we get to play with to find the best fit for our needs, the better:
-
See this for access to Tutanota mails by court order, linking a newspaper article and including a response by the Tutanota team: https://www.reddit.com/r/privacytoolsIO/comments/dv9hh0/tutanota_seems_to_be_forced_to_provide_access_to/
ProtonMail might be subject to something similar without being able to say so (gag order); see the multitude of court orders at https://protonmail.com/blog/transparency-report/
The problem is: Either both sender and receiver use encryption or it’s not worth much during transport.
Email is just not secure / private. Trying to do so is just a waste of time IMHO. If you need security / privacy, use a secure messenger protocol.
-
See this for access to Tutanota mails by court order, linking a newspaper article and including a response by the Tutanota team: https://www.reddit.com/r/privacytoolsIO/comments/dv9hh0/tutanota_seems_to_be_forced_to_provide_access_to/
ProtonMail might be subject to something similar without being able to say so (gag order); see the multitude of court orders at https://protonmail.com/blog/transparency-report/
The problem is: Either both sender and receiver use encryption or it’s not worth much during transport.
Email is just not secure / private. Trying to do so is just a waste of time IMHO. If you need security / privacy, use a secure messenger protocol.
- The court order thing for Tutanota only concerns their hosting, not when the app is self hosted.
- About ProtonMail, they are based in Switzerland and there is no concept of gag orders in switzerland.
However, you are right, trying to build a secure email platform is a fool's errand. If you need privacy and security, use a secure messenger protocol, totally
-
@mehdi said in Tutanota - Secure email for everybody:
secure email platform is a fool's errand
We removed SSLv3 in 5.2 and we already got a couple of bug reports that orange is rejecting mails

@girish
SSL 3 was (correctly) removed way back from Cloudron --- I am on v5.1.5
The orange problem could be related to cipher suites recently removed --- there is currently just one weak suite.
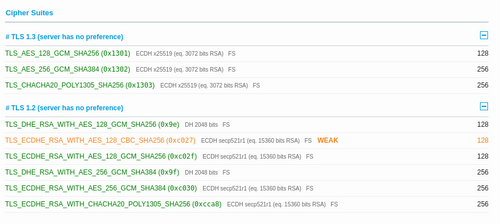
Suggest @mehdi was referring to weak message encryption and unencrypted metadata (subject lines, etc) rather than transport security.
-
@Hillside502 Sorry, I meant that SSL3 was removed for the email server in 5.2. You are correct that 5.1.x already removed it for HTTPS server.
Sadly, it seem orange only offers SSLv3 (!). In fact, one has to go out of their way to even get these old protocols with recent node versions.
root@localhost:~# openssl s_client -starttls smtp -tls1_2 -crlf -connect smtp-in.orange.fr:25 CONNECTED(00000005) 140519366549952:error:1425F102:SSL routines:ssl_choose_client_version:unsupported protocol:../ssl/statem/statem_lib.c:1907: --- no peer certificate available --- No client certificate CA names sent --- SSL handshake has read 303 bytes and written 260 bytes Verification: OK --- New, (NONE), Cipher is (NONE) Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : 0000 Session-ID: Session-ID-ctx: Master-Key: PSK identity: None PSK identity hint: None SRP username: None Start Time: 1590362274 Timeout : 7200 (sec) Verify return code: 0 (ok) Extended master secret: no ---
Hello! It looks like you're interested in this conversation, but you don't have an account yet.
Getting fed up of having to scroll through the same posts each visit? When you register for an account, you'll always come back to exactly where you were before, and choose to be notified of new replies (either via email, or push notification). You'll also be able to save bookmarks and upvote posts to show your appreciation to other community members.
With your input, this post could be even better 💗
Register Login