Beszel is now available
-
@andreasdueren said in Beszel is now available:
Did anyone try setting it up to monitor the same or different cloudrons?
Good question, I tried but, no idea how to do that
@imc67 Well I did the unspeakable and unrecommended thing and installed it on a cloudron as a binary. Very much not recommended so I'm leaving the instructions here so you all can avoid it:
curl -sL https://get.beszel.dev -o /tmp/install-agent.sh && chmod +x /tmp/install-agent.sh && /tmp/install-agent.sh -p 45876 -k "KEY HERE"And opened up that port on cloudron with iptables:
sudo iptables -I INPUT 1 -p tcp --dport 45876 -j ACCEPT -m comment --comment "Cloudron: Allow TCP 45876 (Manual Addition for Beszel - DO NOT APPLY)"This is likely not going to be persistent and did I mention not recommended?
-
I have installed Beszel Hub on my Cloudron VPS and the agent on servers in my homelab. The agents seem unable to connect to the Beszel hub on the VPS, presumably because the default port 45876 is not open in the Cloudron firewall?
-
Forgive my ignorance of this particular app, but is there any ability to monitor Cloudron app containers itself with it? Or maybe related... does Cloudron plan on perhaps building this app into core so that we can get some souped-up monitoring capabilities for each container on the status page?
-
Forgive my ignorance of this particular app, but is there any ability to monitor Cloudron app containers itself with it? Or maybe related... does Cloudron plan on perhaps building this app into core so that we can get some souped-up monitoring capabilities for each container on the status page?
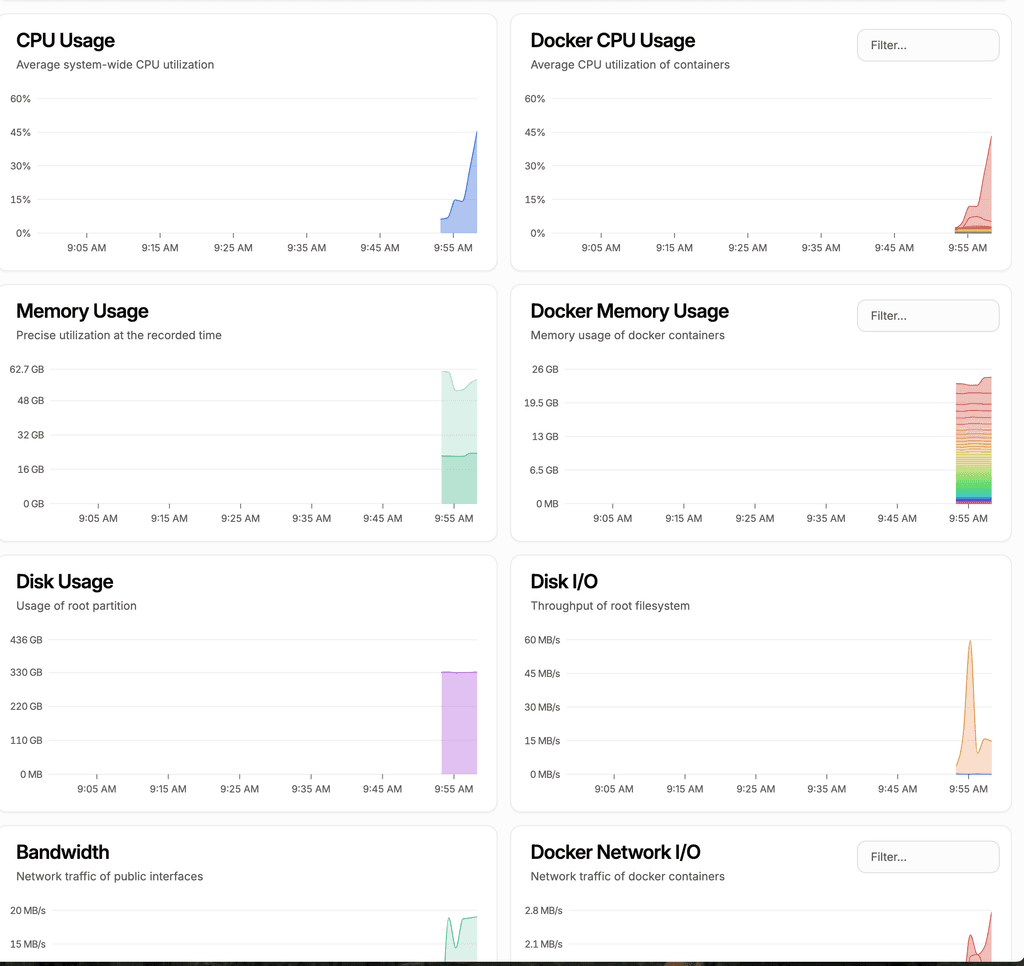
@d19dotca it’ll break down the memory usage per docker instance for example
-
@andreasdueren you can use https://docs.cloudron.io/networking/#whitelist-ports instead of the iptables rule to keep things persistent.
-
@imc67 Well I did the unspeakable and unrecommended thing and installed it on a cloudron as a binary. Very much not recommended so I'm leaving the instructions here so you all can avoid it:
curl -sL https://get.beszel.dev -o /tmp/install-agent.sh && chmod +x /tmp/install-agent.sh && /tmp/install-agent.sh -p 45876 -k "KEY HERE"And opened up that port on cloudron with iptables:
sudo iptables -I INPUT 1 -p tcp --dport 45876 -j ACCEPT -m comment --comment "Cloudron: Allow TCP 45876 (Manual Addition for Beszel - DO NOT APPLY)"This is likely not going to be persistent and did I mention not recommended?

@andreasdueren are those graphs clickable to drill down into each container/app or just high level?
Is there a dark mode? Custom dash?
-
@andreasdueren are those graphs clickable to drill down into each container/app or just high level?
Is there a dark mode? Custom dash?
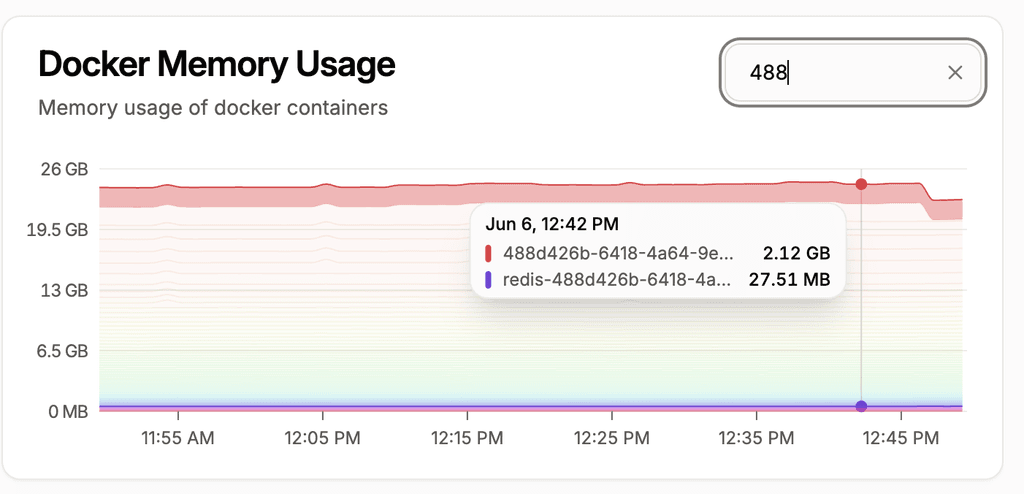
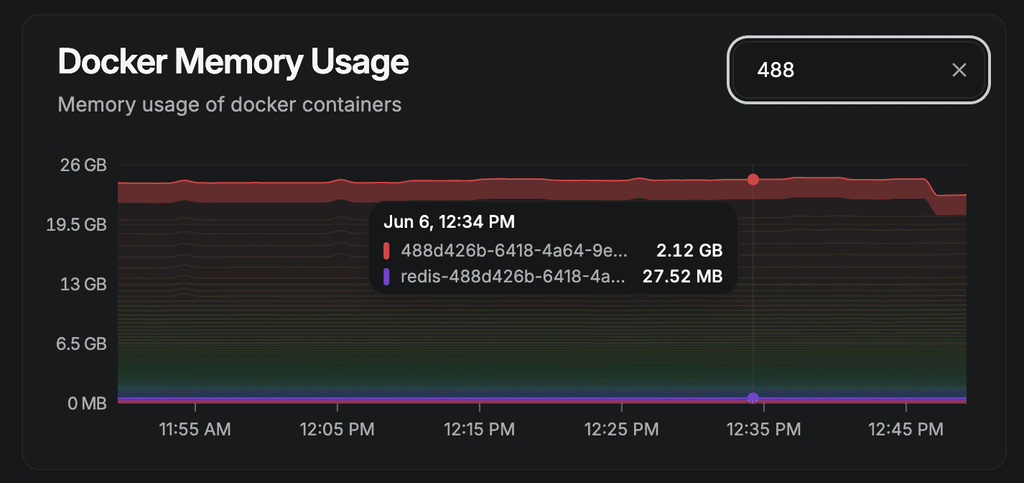
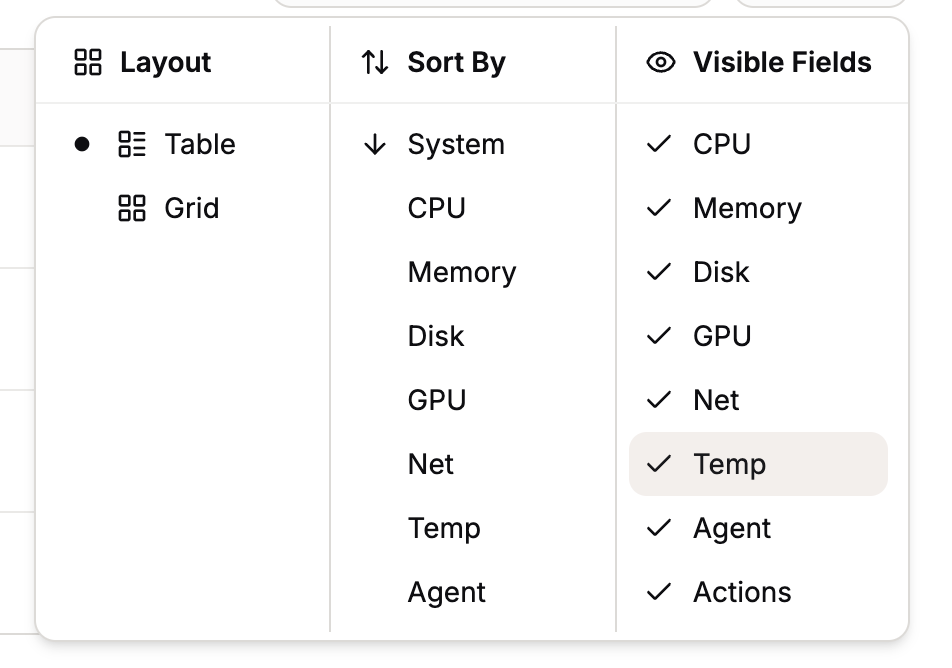
@robi Not clickable but filterable. Darkmode exists. You can rudimentarily change the layout but this is not designed to be hyper customized it seems.
-
@andreasdueren you can use https://docs.cloudron.io/networking/#whitelist-ports instead of the iptables rule to keep things persistent.
@joseph Oh nice!
-
@robi Not clickable but filterable. Darkmode exists. You can rudimentarily change the layout but this is not designed to be hyper customized it seems.



@andreasdueren Thank you.
Doesn't seem to help humans ID the Apps w/o further matching to names or domains or Cloudron renaming the container IDs like the redis one.
-
@andreasdueren Thank you.
Doesn't seem to help humans ID the Apps w/o further matching to names or domains or Cloudron renaming the container IDs like the redis one.
@robi Not optimal but still useful for my purposes.
-
 G girish forked this topic on
G girish forked this topic on
