Cloudron Password Hash Algorithm
-
Oh my, oh my, the world is coming to an end!
Please stop spreading panic. PBKDF2-SHA1 is not the same as SHA1. SHA1 has collisions - big deal.
@mehdi and I nicely explained to you in chat why this is not the issue and why there's no need for immediate action AT ALL.
Please stop scaring the users for no real reason without understanding the underlying problem. Thanks!
-
Oh my, oh my, the world is coming to an end!
Please stop spreading panic. PBKDF2-SHA1 is not the same as SHA1. SHA1 has collisions - big deal.
@mehdi and I nicely explained to you in chat why this is not the issue and why there's no need for immediate action AT ALL.
Please stop scaring the users for no real reason without understanding the underlying problem. Thanks!
@mario said in Critical: Cloudron Password Hash Algorithm Must Be Updated Immediately:
PKBDF2-SHA1 is not the same as SHA1
PBKDF...
https://en.wikipedia.org/wiki/PBKDF2 -
@mario said in Critical: Cloudron Password Hash Algorithm Must Be Updated Immediately:
PKBDF2-SHA1 is not the same as SHA1
PBKDF...
https://en.wikipedia.org/wiki/PBKDF2 -
@Hillside502 why are you linking me to a wikipedia article?
Edit: Ah, I see - because of a typo I made, corrected.
@mario
just to indicate the source of my correction -
@mario
just to indicate the source of my correction -
For transparency reasons and so you can understand why there's no real danger here, here's what @mehdi and me wrote:
me:
" you are aware that HMAC/SHA1 (used by PBKDF) is just fine for password storage and not really broken as you say?
even MD5 would be just fine
afaik
so the urgency is non-warranted
"@mehdi explains it in greater detail:
"
To be clear, pbkdf2-sha1 is not sha1. Using just sha1 or md5 would be extremely
bad, using just any hash fonction would be very very bad, as they are litteraly built to be as fast as possible, whereas for storing passwords we deliberatly want it to be slow. PBKDF2 uses a hash function in a much more complicated scheme, to make them suitable for storing passwords and/or creating symetric keys from a password.
So pbkdf2 is not broken, even if the sha1 it uses is broken
"(I need to look how quoting works with this forum software, so sorry about that)
-
Exactly what Mario just said. Your data is not at risk. This is not a security flaw.
To explain a bit more, I posted this in the chat:
To explain a bit more, hash functions should have 2 main caracteristics : non-reversibility (given the output, you cannot know the input), and minimal collisions (2 inputs should not have the same output). For SHA1, the collisions part was completely broken, but for passords we mainly care about the non-reversibility part.
But PBKDF2 is definitely not state-of-the-art either... I would recommend moving to scrypt (which has my personal preference), or argon2, yeah. There is, however, no urgency whatsoever. And the migration may be a bit tricky.
-
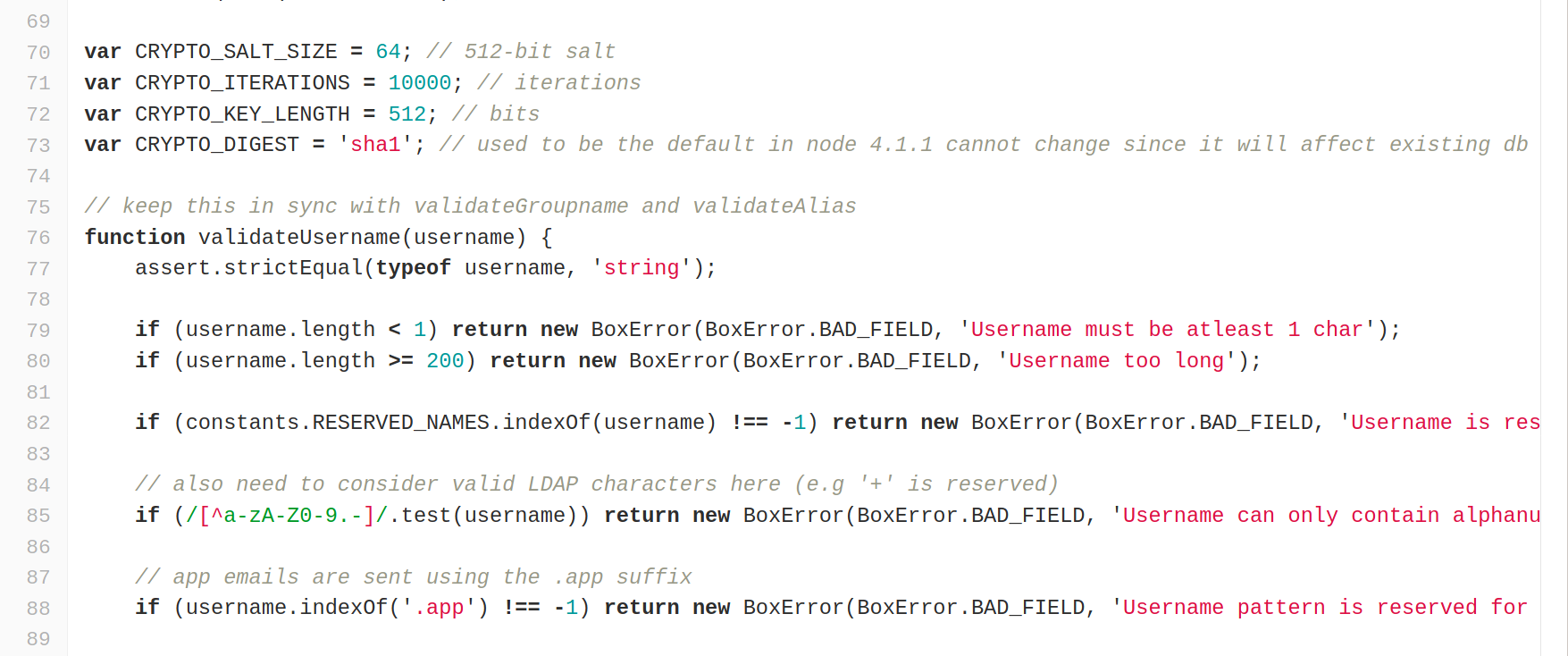
As others pointed, Cloudron uses PBKDF2-HMAC-SHA1 with a per-user salt. This is totally different from just using SHA1.
As we are not cryptographers ourselves, the best approach is to not try to re-implement crypto ourselves and just follow NIST guidelines - NIST 800-63 Specs.
It recommends PBKDF2 and atleast 10k iterations. We also follow most of it's other password guidelines including following including 8 character minimum, support at least 64 characters maximum length, all ASCII characters (including space) should be supported, no password hints/expiry, non-SMS 2FA etc.
There is a good article summarizing the NIST guidelines at the Sophos website and also an article how to store passwords safely.
-
As others pointed, Cloudron uses PBKDF2-HMAC-SHA1 with a per-user salt. This is totally different from just using SHA1.
As we are not cryptographers ourselves, the best approach is to not try to re-implement crypto ourselves and just follow NIST guidelines - NIST 800-63 Specs.
It recommends PBKDF2 and atleast 10k iterations. We also follow most of it's other password guidelines including following including 8 character minimum, support at least 64 characters maximum length, all ASCII characters (including space) should be supported, no password hints/expiry, non-SMS 2FA etc.
There is a good article summarizing the NIST guidelines at the Sophos website and also an article how to store passwords safely.
@girish
Good to know that max password length is >=64, as at one time Cloudron's was 30 -
@girish
Good to know that max password length is >=64, as at one time Cloudron's was 30