Reduce visibility to spam bots via KnockD
-
Certain services, like ssh get a lot of attention from bots if the port is open.
It would be nice to remove being the attention of such scans by closing those affected ports.
Since we still need to use them, they can be enabled for us specifically via port knocking.
Combined with temporary IP whitelisting, keeping related connections open in IPtables, and cleaning up the white list/port after IP change/inactivity, that would keep things nicely automated, and reduce the amount of logging and CPU necessary.
It could also be nicely adapted to the remote Cloudron support process.
-
Certain services, like ssh get a lot of attention from bots if the port is open.
It would be nice to remove being the attention of such scans by closing those affected ports.
Since we still need to use them, they can be enabled for us specifically via port knocking.
Combined with temporary IP whitelisting, keeping related connections open in IPtables, and cleaning up the white list/port after IP change/inactivity, that would keep things nicely automated, and reduce the amount of logging and CPU necessary.
It could also be nicely adapted to the remote Cloudron support process.
@robi Wow Robi, this is a great feature request!!! Just yesterday one of my Cloudron instances got a lot of traffic to email for a bruteforce attack.
@girish I think this feature have to put on the top of the list to improve safety but also to reduce workload of instances and network traffic...
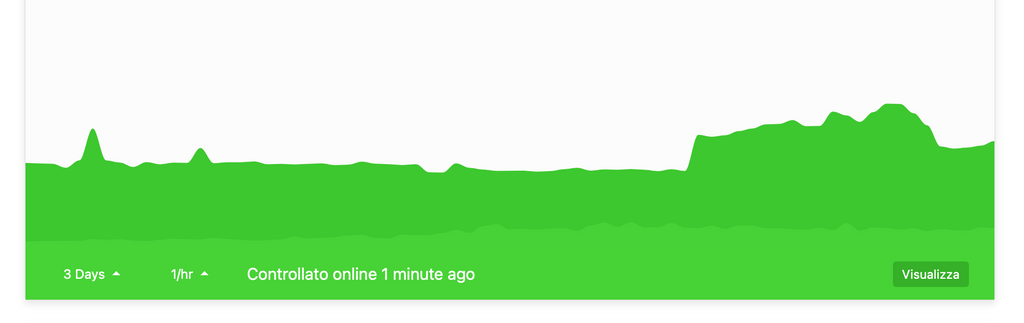
This is a statping how network performances was impacted before and later bruteforce.
Also, need a robust alert system - email or other - to let us know that something is happens.
