Referrer-Policy header is overwritten
-
It looks like Cloudron hides apps’ Referrer-Policy HTTP header (in this line), replacing it with the rather lax value “no-referrer-when-downgrade”, which can result in private URLs leaking to third parties.
Example case that led to this discovery: We run HedgeDoc (which adds a “same-origin” policy); and just this week we found that, without us having published our pad’s URL anywhere, somebody had edited the pad after finding the URL in their server logs.
I am not sure what the ideal solution would be. Perhaps you may want to add your referrer policy only if the application did not already specify one?
-
It looks like Cloudron hides apps’ Referrer-Policy HTTP header (in this line), replacing it with the rather lax value “no-referrer-when-downgrade”, which can result in private URLs leaking to third parties.
Example case that led to this discovery: We run HedgeDoc (which adds a “same-origin” policy); and just this week we found that, without us having published our pad’s URL anywhere, somebody had edited the pad after finding the URL in their server logs.
I am not sure what the ideal solution would be. Perhaps you may want to add your referrer policy only if the application did not already specify one?
@gerben thanks for reporting, I have fixed the default policy to
same-originnow.That said, I think we have to report this as a security issue upstream in HedgeDoc. I see that a locked mode doc should not be editable by guests but it is. A private mode doc should not be editable by other logged in users but it is. I will report this upstream and put a link here, but looks pretty serious. -
I seem to have imagined things, the permissions work perfectly.
@gerben Can you clarify how an anonymous user ended up editing a doc based on a link? Was it a "freely" permission ? BTW, you can disable anonymous entirely by editing
/app/data/config.jsonand settingallowAnonymousto false.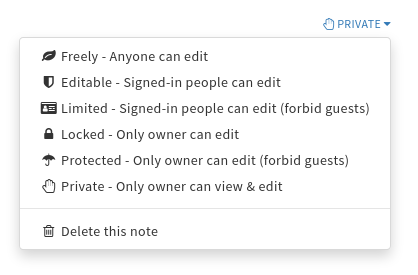
-
I seem to have imagined things, the permissions work perfectly.
@gerben Can you clarify how an anonymous user ended up editing a doc based on a link? Was it a "freely" permission ? BTW, you can disable anonymous entirely by editing
/app/data/config.jsonand settingallowAnonymousto false.
-
 G girish referenced this topic on
G girish referenced this topic on
