Issues when using Cloudflare Proxy service for Cloudron
-
Recently I started using Cloudflare WAF service to protect my Cloudron instance. I had to proxy requests through Cloudflare for the WAF to work. After enabling Cloudflare proxy, I faced a few problems. I would like to share my setup as well as list out the problems.
My Setup
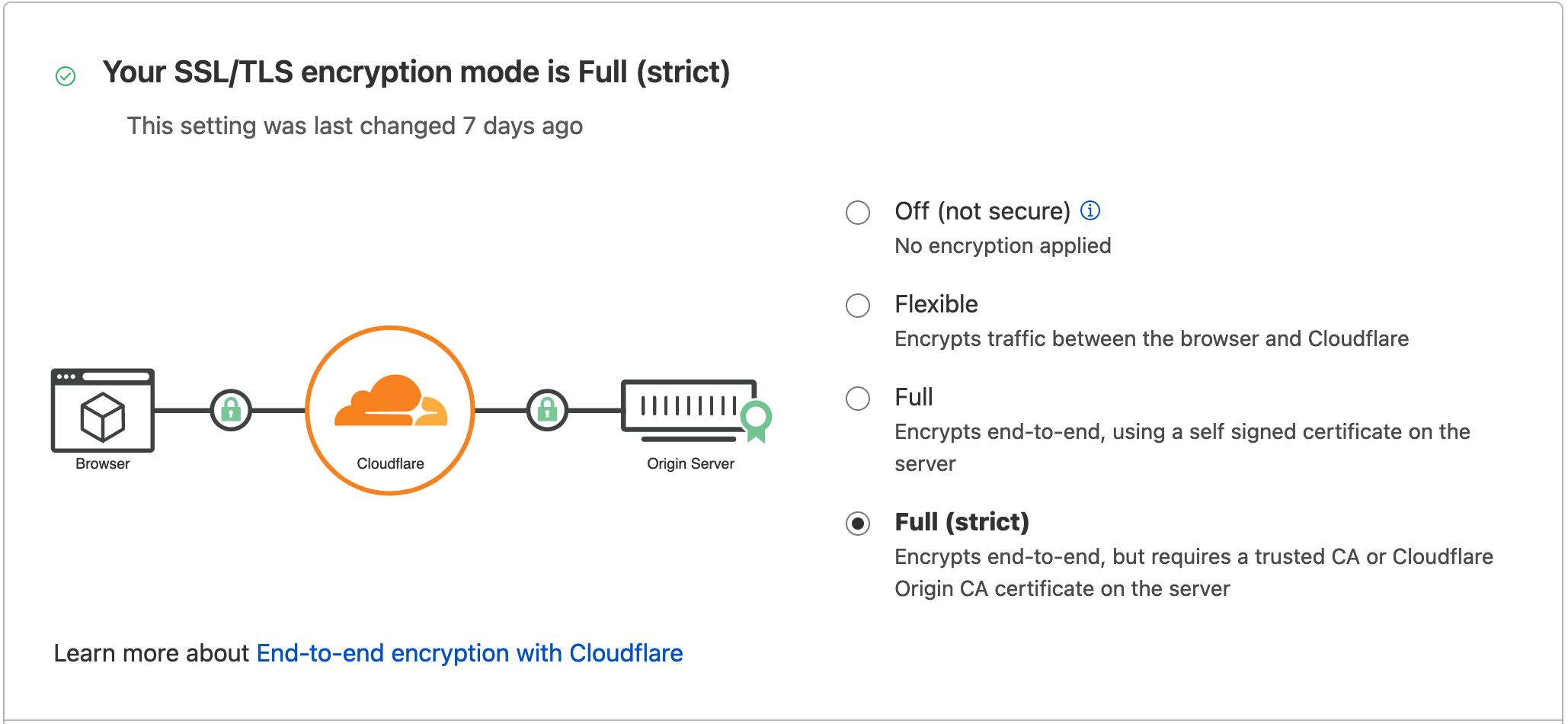
Cloudflare supports different options for SSL termination, among which Full Mode and Full (Strict) Modes are the two options. Since the origin server (Cloudron) forces all connections to be HTTPS, I used the Full(strict) mode. Also, Cloudflare does not support proxying
*.mydomain.org, but only individual subdomains likeapp1.mydomain.org,app2.mydomain.org.Cloudflare Dashboard
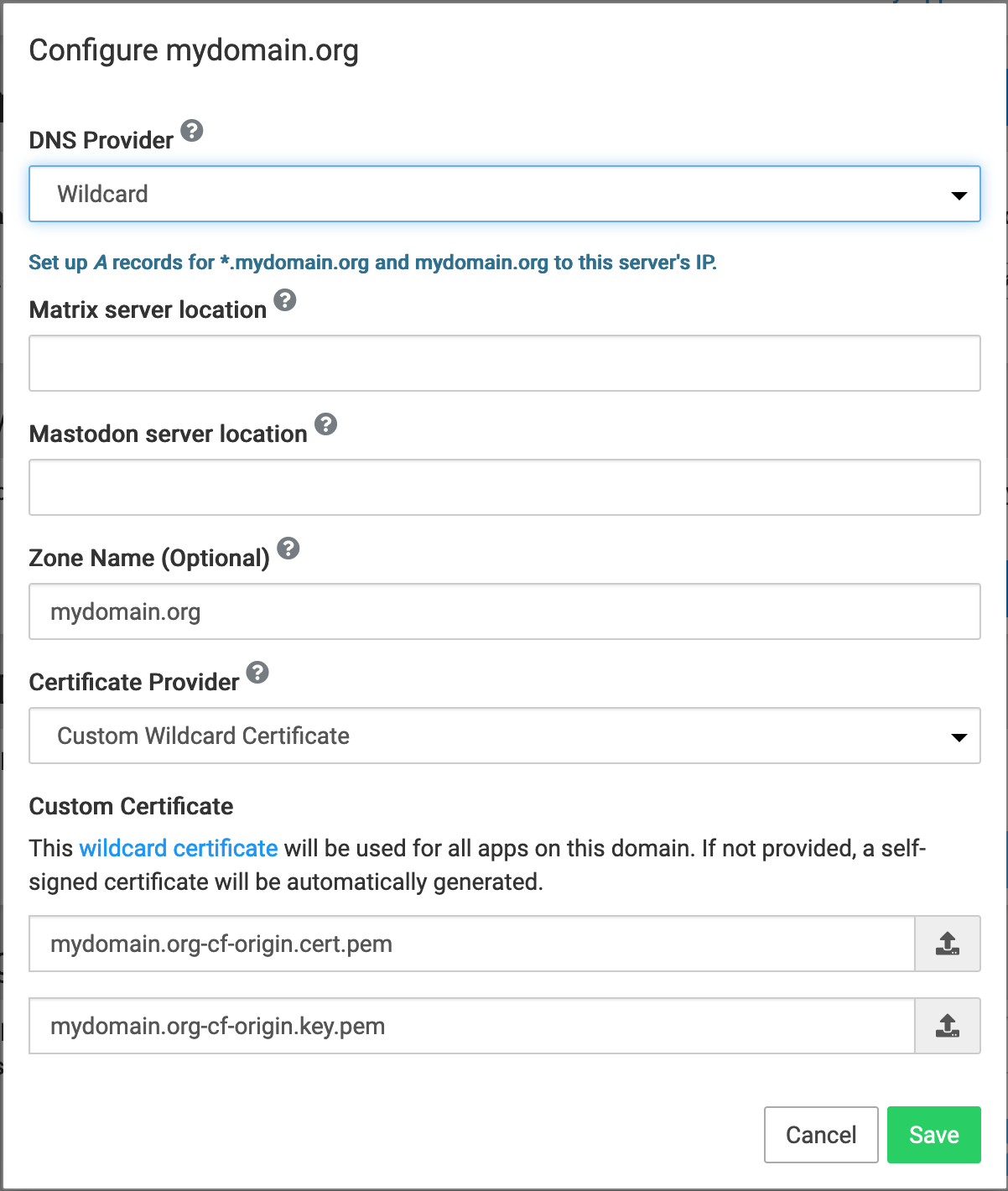
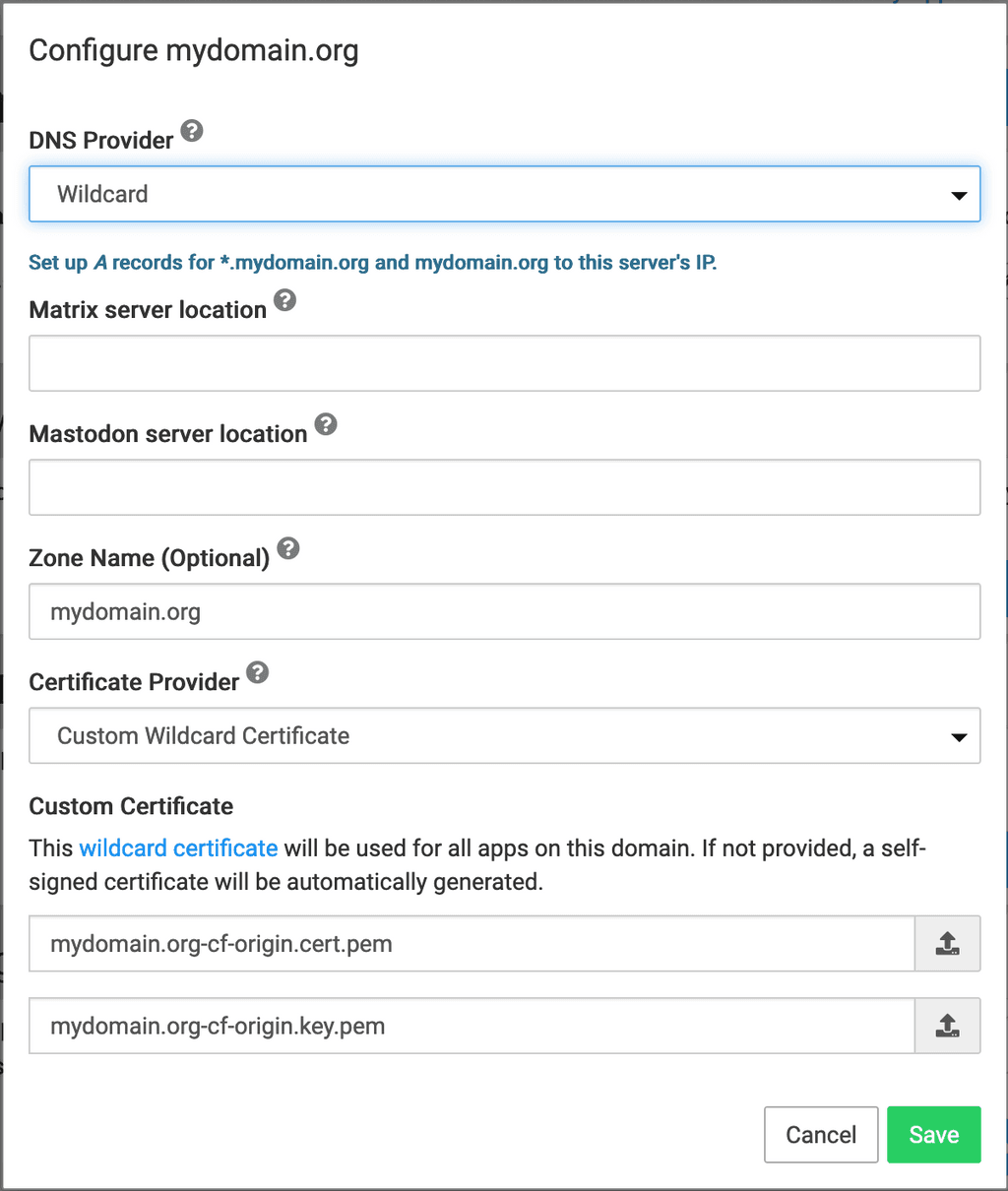
Cloudflare automatically provisions Edge Certificates for
mydomain.organd*.domain.organd then does SSL termination on their end. The origin server (Cloudron) must also have a valid certificate or Cloudflare Origin CA Certificates.Cloudron Domain Settings
I tested with both DNS Providers here - Cloudflare as well as Wildcard, with same results.
Many things are working as expected, but I noticed a few things got broken.
While installing new apps
-
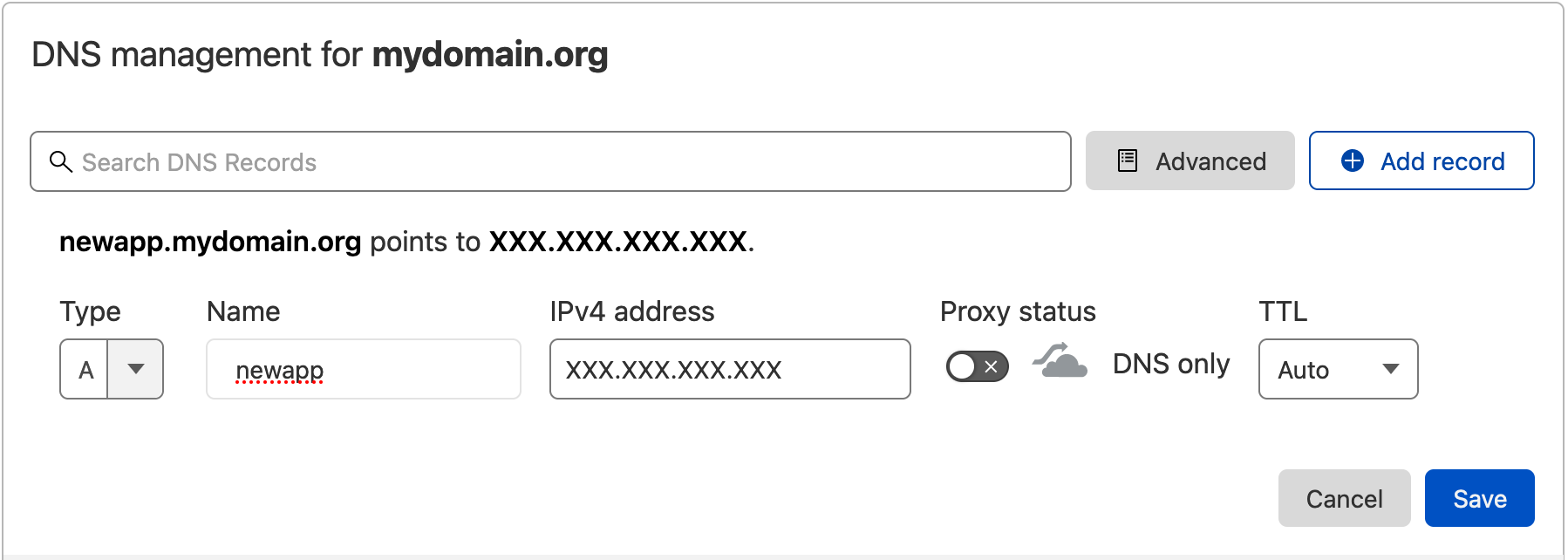
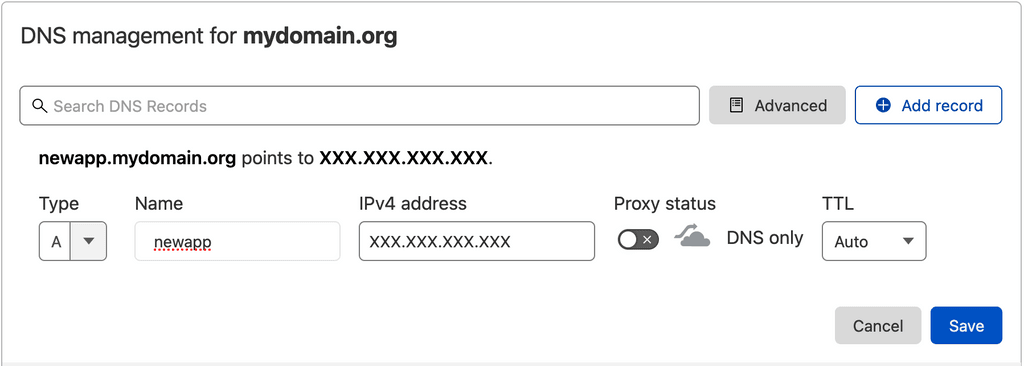
When I am using the Wildcard DNS provider or Cloudron, the app installs successfully but I see a certificate error when I open the newly installed app. That's because
newapp.mydomain.orgis only resolving because of the wildcard*.mydomain.orgentry, and it points directly to my Cloudron without proxying through Cloudflare. Since my Cloudflare is using Custom Certificates from Cloudflare Origin CA, web browsers don't trust it. I have to manually go to Cloudflare dashboard and add a new A-Record in proxy mode. Then the certificate errors resolve. -
Even if I'm using Cloudflare DNS Provider using API Token, Cloudron adds an A-Record but the certificate error still shows up because the A-Record is still in DNS-Only mode. If Cloudron gave an option to set the A-Record in Proxy Mode while installing the app, I didn't have to go to Cloudflare and change the record from DNS Only mode to Proxied Mode and wait for DNS to propagate.
Some Apps Report Wrong IP of Visitors (Cloudflare IPs)
When a website is proxied through Cloudflare, the visitors connect to the Cloudflare servers, and one of the Cloudflare IPs connects to the origin (Cloudron) server. Cloudron does forward the
X-Forwarded-Forheader to the apps, which works in most of the cases, but in this caseX-Forwarded-Forcontains the Cloudflare server's IP instead of the real visitor's IP! That's a bummer. See this online post on Cloudflare IPs where it discusses the ideas to detect the visitor's real IP address. If Cloudron could check forCF-Connecting-IPheader and pass that value as X-Forwarded-For, that would solve this issue entirely. Cloudflare publishes the list of IPs it uses to fetch origin content. The ipv4 addresses are here and ipv4 addresses are here.
That's all for now. I'll add more when I face other issues.
-
-
Recently I started using Cloudflare WAF service to protect my Cloudron instance. I had to proxy requests through Cloudflare for the WAF to work. After enabling Cloudflare proxy, I faced a few problems. I would like to share my setup as well as list out the problems.
My Setup
Cloudflare supports different options for SSL termination, among which Full Mode and Full (Strict) Modes are the two options. Since the origin server (Cloudron) forces all connections to be HTTPS, I used the Full(strict) mode. Also, Cloudflare does not support proxying
*.mydomain.org, but only individual subdomains likeapp1.mydomain.org,app2.mydomain.org.Cloudflare Dashboard

Cloudflare automatically provisions Edge Certificates for
mydomain.organd*.domain.organd then does SSL termination on their end. The origin server (Cloudron) must also have a valid certificate or Cloudflare Origin CA Certificates.Cloudron Domain Settings
I tested with both DNS Providers here - Cloudflare as well as Wildcard, with same results.

Many things are working as expected, but I noticed a few things got broken.
While installing new apps

-
When I am using the Wildcard DNS provider or Cloudron, the app installs successfully but I see a certificate error when I open the newly installed app. That's because
newapp.mydomain.orgis only resolving because of the wildcard*.mydomain.orgentry, and it points directly to my Cloudron without proxying through Cloudflare. Since my Cloudflare is using Custom Certificates from Cloudflare Origin CA, web browsers don't trust it. I have to manually go to Cloudflare dashboard and add a new A-Record in proxy mode. Then the certificate errors resolve. -
Even if I'm using Cloudflare DNS Provider using API Token, Cloudron adds an A-Record but the certificate error still shows up because the A-Record is still in DNS-Only mode. If Cloudron gave an option to set the A-Record in Proxy Mode while installing the app, I didn't have to go to Cloudflare and change the record from DNS Only mode to Proxied Mode and wait for DNS to propagate.
Some Apps Report Wrong IP of Visitors (Cloudflare IPs)
When a website is proxied through Cloudflare, the visitors connect to the Cloudflare servers, and one of the Cloudflare IPs connects to the origin (Cloudron) server. Cloudron does forward the
X-Forwarded-Forheader to the apps, which works in most of the cases, but in this caseX-Forwarded-Forcontains the Cloudflare server's IP instead of the real visitor's IP! That's a bummer. See this online post on Cloudflare IPs where it discusses the ideas to detect the visitor's real IP address. If Cloudron could check forCF-Connecting-IPheader and pass that value as X-Forwarded-For, that would solve this issue entirely. Cloudflare publishes the list of IPs it uses to fetch origin content. The ipv4 addresses are here and ipv4 addresses are here.
That's all for now. I'll add more when I face other issues.
@nj said in Issues when using Cloudflare Proxy service for Cloudron:
Even if I'm using Cloudflare DNS Provider using API Token, Cloudron adds an A-Record but the certificate error still shows up because the A-Record is still in DNS-Only mode. If Cloudron gave an option to set the A-Record in Proxy Mode while installing the app, I didn't have to go to Cloudflare and change the record from DNS Only mode to Proxied Mode and wait for DNS to propagate.
This is the best way to do it.
- Add the domain in Cloudron with Cloudflare DNS provider
- Cloudron will always add the A record in DNS Mode.
- Go to Cloudflare, and turn on proxying.
- For future DNS changes to this domain, Cloudron has code to "persist" the proxying flag. Just noting this down, since we have code explicitly for this use case.
I agree having a checkbox or something at app install time to enable proxying would be nice.
-
-
@nj said in Issues when using Cloudflare Proxy service for Cloudron:
Even if I'm using Cloudflare DNS Provider using API Token, Cloudron adds an A-Record but the certificate error still shows up because the A-Record is still in DNS-Only mode. If Cloudron gave an option to set the A-Record in Proxy Mode while installing the app, I didn't have to go to Cloudflare and change the record from DNS Only mode to Proxied Mode and wait for DNS to propagate.
This is the best way to do it.
- Add the domain in Cloudron with Cloudflare DNS provider
- Cloudron will always add the A record in DNS Mode.
- Go to Cloudflare, and turn on proxying.
- For future DNS changes to this domain, Cloudron has code to "persist" the proxying flag. Just noting this down, since we have code explicitly for this use case.
I agree having a checkbox or something at app install time to enable proxying would be nice.
@girish Sorry to revive an old topic and if there's a newer one I apologize, but I was just curious about this as I would prefer to have some sites protected by Cloudflare. I realize for certain subdomains, such as for SMTP server, that can't be proxied. But I think that's the only exception unless you're utilizing Cloudron as an LDAP source then you'd also leave "my.cloudroninstance.com" un-proxied (which isn't ideal as it leaves it vulnerable).
To give you some context, I'm asking because I have dedicated IP addresses and also use Tailscale. So, in Cloudflare I have a list of my dedicated IPs and Tailscale addresses and for some services I setup a WAF rule that simply blocks anyone from even attempting to access the site based on their IP address.
-
@girish Sorry to revive an old topic and if there's a newer one I apologize, but I was just curious about this as I would prefer to have some sites protected by Cloudflare. I realize for certain subdomains, such as for SMTP server, that can't be proxied. But I think that's the only exception unless you're utilizing Cloudron as an LDAP source then you'd also leave "my.cloudroninstance.com" un-proxied (which isn't ideal as it leaves it vulnerable).
To give you some context, I'm asking because I have dedicated IP addresses and also use Tailscale. So, in Cloudflare I have a list of my dedicated IPs and Tailscale addresses and for some services I setup a WAF rule that simply blocks anyone from even attempting to access the site based on their IP address.
@ajtatum correct, but that's not a cloudron limit, that's how cloudflare & DNS work
the MX can never be proxied hence, somewhat nullifying the whole idea ??in my usecase, the only solution I have found is for anyone that attempt to resolve my IP directly is sent to my.cloudron.domain (hence cloudflare proxied) but there is nothing you can do for the MX.
-
@girish Sorry to revive an old topic and if there's a newer one I apologize, but I was just curious about this as I would prefer to have some sites protected by Cloudflare. I realize for certain subdomains, such as for SMTP server, that can't be proxied. But I think that's the only exception unless you're utilizing Cloudron as an LDAP source then you'd also leave "my.cloudroninstance.com" un-proxied (which isn't ideal as it leaves it vulnerable).
To give you some context, I'm asking because I have dedicated IP addresses and also use Tailscale. So, in Cloudflare I have a list of my dedicated IPs and Tailscale addresses and for some services I setup a WAF rule that simply blocks anyone from even attempting to access the site based on their IP address.
-
 N nebulon marked this topic as a question on
N nebulon marked this topic as a question on
-
 N nebulon has marked this topic as solved on
N nebulon has marked this topic as solved on
-
Recently I started using Cloudflare WAF service to protect my Cloudron instance. I had to proxy requests through Cloudflare for the WAF to work. After enabling Cloudflare proxy, I faced a few problems. I would like to share my setup as well as list out the problems.
My Setup
Cloudflare supports different options for SSL termination, among which Full Mode and Full (Strict) Modes are the two options. Since the origin server (Cloudron) forces all connections to be HTTPS, I used the Full(strict) mode. Also, Cloudflare does not support proxying
*.mydomain.org, but only individual subdomains likeapp1.mydomain.org,app2.mydomain.org.Cloudflare Dashboard

Cloudflare automatically provisions Edge Certificates for
mydomain.organd*.domain.organd then does SSL termination on their end. The origin server (Cloudron) must also have a valid certificate or Cloudflare Origin CA Certificates.Cloudron Domain Settings
I tested with both DNS Providers here - Cloudflare as well as Wildcard, with same results.

Many things are working as expected, but I noticed a few things got broken.
While installing new apps

-
When I am using the Wildcard DNS provider or Cloudron, the app installs successfully but I see a certificate error when I open the newly installed app. That's because
newapp.mydomain.orgis only resolving because of the wildcard*.mydomain.orgentry, and it points directly to my Cloudron without proxying through Cloudflare. Since my Cloudflare is using Custom Certificates from Cloudflare Origin CA, web browsers don't trust it. I have to manually go to Cloudflare dashboard and add a new A-Record in proxy mode. Then the certificate errors resolve. -
Even if I'm using Cloudflare DNS Provider using API Token, Cloudron adds an A-Record but the certificate error still shows up because the A-Record is still in DNS-Only mode. If Cloudron gave an option to set the A-Record in Proxy Mode while installing the app, I didn't have to go to Cloudflare and change the record from DNS Only mode to Proxied Mode and wait for DNS to propagate.
Some Apps Report Wrong IP of Visitors (Cloudflare IPs)
When a website is proxied through Cloudflare, the visitors connect to the Cloudflare servers, and one of the Cloudflare IPs connects to the origin (Cloudron) server. Cloudron does forward the
X-Forwarded-Forheader to the apps, which works in most of the cases, but in this caseX-Forwarded-Forcontains the Cloudflare server's IP instead of the real visitor's IP! That's a bummer. See this online post on Cloudflare IPs where it discusses the ideas to detect the visitor's real IP address. If Cloudron could check forCF-Connecting-IPheader and pass that value as X-Forwarded-For, that would solve this issue entirely. Cloudflare publishes the list of IPs it uses to fetch origin content. The ipv4 addresses are here and ipv4 addresses are here.
That's all for now. I'll add more when I face other issues.
@nj said in Issues when using Cloudflare Proxy service for Cloudron:
Some Apps Report Wrong IP of Visitors (Cloudflare IPs)
When a website is proxied through Cloudflare, the visitors connect to the Cloudflare servers, and one of the Cloudflare IPs connects to the origin (Cloudron) server. Cloudron does forward the X-Forwarded-For header to the apps, which works in most of the cases, but in this case X-Forwarded-For contains the Cloudflare server's IP instead of the real visitor's IP! That's a bummer. See this online post on Cloudflare IPs where it discusses the ideas to detect the visitor's real IP address. If Cloudron could check for CF-Connecting-IP header and pass that value as X-Forwarded-For, that would solve this issue entirely. Cloudflare publishes the list of IPs it uses to fetch origin content. The ipv4 addresses are here and ipv4 addresses are here.@nj @girish Did the IP forwarding suggestion here ever get implemented?
-
-
-
@girish Nice, thank you. Have just added them manually.
Be double-nice if they were added automatically when Cloudflare is first used as a DNS Proxy, but I guess I understand that's both an additional feature to maintain, and maybe debatable if everyone would want it happening silently.