Please include ability to serve HTTP unencrypted over port 80 for network traffic inspection purposes
-
For those of us who wish to capture our network traffic for inspection, It makes more sense for us to put a LB/reverse proxy in front of our cloudron and then terminate SSL/TLS at the LB and pass un encrypted to our Cloudron. Obviously for certain traffic where E2E encryption is preferred we can proxy pass https. It would be nice if we had the ability to maybe select whether or not we want to also serve on port 80.
-
For those of us who wish to capture our network traffic for inspection, It makes more sense for us to put a LB/reverse proxy in front of our cloudron and then terminate SSL/TLS at the LB and pass un encrypted to our Cloudron. Obviously for certain traffic where E2E encryption is preferred we can proxy pass https. It would be nice if we had the ability to maybe select whether or not we want to also serve on port 80.
@Mastadamus Can you can also decrypt the traffic if you have the certs which you can get from
/home/yellowtent/platformdata/nginx/cert) ? Something like https://support.f5.com/csp/article/K19310681 or https://unit42.paloaltonetworks.com/wireshark-tutorial-decrypting-https-traffic/ -
@Mastadamus Can you can also decrypt the traffic if you have the certs which you can get from
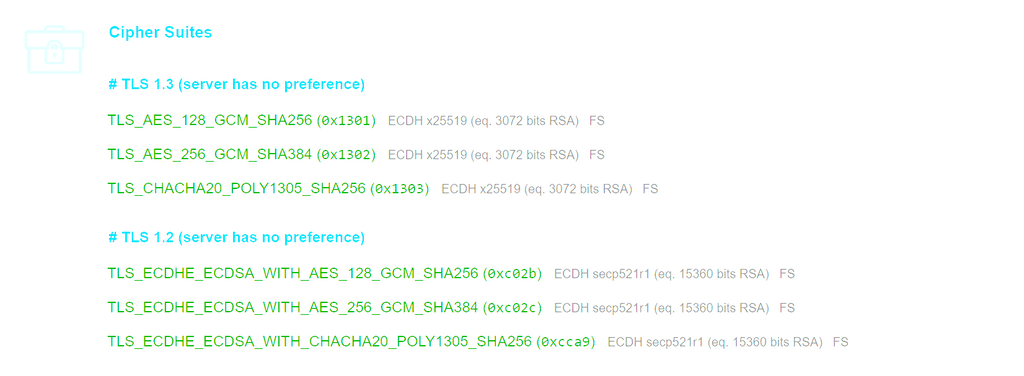
/home/yellowtent/platformdata/nginx/cert) ? Something like https://support.f5.com/csp/article/K19310681 or https://unit42.paloaltonetworks.com/wireshark-tutorial-decrypting-https-traffic/@girish Yeah thats what I do for my actual job, but it does introduce a ton of issues. 1. You can decrypt if you are using Diffie Helman. As far as I can determine currently the cloudron only accepts ECDH algorithms. This would prevent decryption since you can't MITM diffie hellman as far as I know.
-
@girish Yeah thats what I do for my actual job, but it does introduce a ton of issues. 1. You can decrypt if you are using Diffie Helman. As far as I can determine currently the cloudron only accepts ECDH algorithms. This would prevent decryption since you can't MITM diffie hellman as far as I know.

@Mastadamus said in Please include ability to serve HTTP unencrypted over port 80 for network traffic inspection purposes:
You can decrypt if you are using Diffie Helman. As far as I can determine currently the cloudron only accepts ECDH algorithms
Indeed, it cannot be decoded because PFS is a property of ECDH. See also Right, I guess this is because of PFS - https://serverfault.com/questions/869354/decoding-ssl-packets-with-cipher-tls-ecdhe-rsa-in-wireshark
I think having a way to support reverse proxies in front of cloudron would help the situation. It seems many people are hitting this limitation when they deploy at home.
-
@Mastadamus said in Please include ability to serve HTTP unencrypted over port 80 for network traffic inspection purposes:
You can decrypt if you are using Diffie Helman. As far as I can determine currently the cloudron only accepts ECDH algorithms
Indeed, it cannot be decoded because PFS is a property of ECDH. See also Right, I guess this is because of PFS - https://serverfault.com/questions/869354/decoding-ssl-packets-with-cipher-tls-ecdhe-rsa-in-wireshark
I think having a way to support reverse proxies in front of cloudron would help the situation. It seems many people are hitting this limitation when they deploy at home.
@girish do we have a way to do this yet? Support for reverse proxies in front of cloudron?
-
@girish do we have a way to do this yet? Support for reverse proxies in front of cloudron?
@Mastadamus why not do it behind?
-
@girish do we have a way to do this yet? Support for reverse proxies in front of cloudron?
