Use Cloudrons ldap in Authelia
-
Hi everybody,
Question...
I have Authelia installed at another location and i use it for applications that are running without 2fauth. I use Authelia here for the 2fauth in front.Now i want to offer my already existing users in Cloudron, to login with Authelia and use the other services at the other location.
I am following this guide:
https://docs.ibracorp.io/authelia/authelia/configuration
(Option 2 - Using an LDAP database) but not sure wich ldap section i have to follow for the Cloudrons Ldap integration..(?)- FreeIpa
- OpenLdap
- Active Directory
- LLDAP/Light Ldap
Another question is, that Cloudrons LDAP port:636 is exposed to the outside world, but restricted to only the IP adress of the other location in my firewall. And of course in the Cloudrons Ldap section, the IP address of the other location is in place there also.
Am i doing this the right way?
-
I have no clue about Authelia and what kind of LDAP flavor it supports, but probably OpenLDAP profile is compatible.
On your Cloudron side, you have to enable the user directory server. The settings and default values are mentioned in the docs at https://docs.cloudron.io/user-management/#directory-server
-
I have no clue about Authelia and what kind of LDAP flavor it supports, but probably OpenLDAP profile is compatible.
On your Cloudron side, you have to enable the user directory server. The settings and default values are mentioned in the docs at https://docs.cloudron.io/user-management/#directory-server
-
@nebulon Thanks a lot for the info. I'm going to try it out when I have some spare hours left this week.
I'll report back.....
@DanTheMan did you have success? Trying to do the same thing now. My approach will be:
- Set up a Container with Authelia (cloud also be a VM) in my private network alongside the Cloudron VM as in the same sub-net or vLAN
- Adapt Authelias Config accordingly, I want it to utilize a LDAP Backend and for starters integrating the one that Cloudron offers.
- Let Cloudron do the Cert-handling and expose Authelia via Cloudron-App-Proxy
- Adapt the Nginx-Config for the Cloudron Apps, I want to protect to require the SSO flow Authelia offers.
How did you approach the issue? Did you do things differently?
-
@DanTheMan did you have success? Trying to do the same thing now. My approach will be:
- Set up a Container with Authelia (cloud also be a VM) in my private network alongside the Cloudron VM as in the same sub-net or vLAN
- Adapt Authelias Config accordingly, I want it to utilize a LDAP Backend and for starters integrating the one that Cloudron offers.
- Let Cloudron do the Cert-handling and expose Authelia via Cloudron-App-Proxy
- Adapt the Nginx-Config for the Cloudron Apps, I want to protect to require the SSO flow Authelia offers.
How did you approach the issue? Did you do things differently?
@Jan-Macenka
So great to hear that someone wants to do the same thing as i had in mind
This is how I have set it up at the moment...
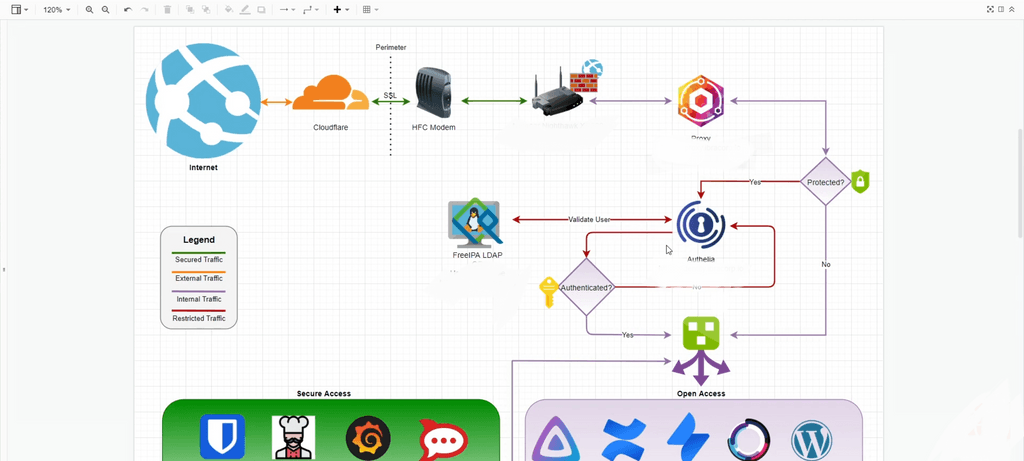
I am on holiday this week and coming home this weekend, so I will be here around that time to pick this up.
-
@DanTheMan did you have success? Trying to do the same thing now. My approach will be:
- Set up a Container with Authelia (cloud also be a VM) in my private network alongside the Cloudron VM as in the same sub-net or vLAN
- Adapt Authelias Config accordingly, I want it to utilize a LDAP Backend and for starters integrating the one that Cloudron offers.
- Let Cloudron do the Cert-handling and expose Authelia via Cloudron-App-Proxy
- Adapt the Nginx-Config for the Cloudron Apps, I want to protect to require the SSO flow Authelia offers.
How did you approach the issue? Did you do things differently?
So this is the update so far from my side;
-
Set up a Container with Authelia (cloud also be a VM) in my private network alongside the Cloudron VM as in the same sub-net or vLAN
Authelia is running in the same subnet as Cloudron now.
-
Let Cloudron do the Cert-handling and expose Authelia via Cloudron-App-Proxy
Authelia is running through the Cloudron-App-Proxy and handling certs for Authelia.
These are the one's that i'm struggling with at the moment;
-
Adapt Authelias Config accordingly, utilize LDAP Backend and integrating the one that Cloudron offers.

-
Adapt the Nginx-Config for the Cloudron Apps, protect to require the SSO flow Authelia offers.

-
Ok, so i found the following almost working, but i can't login Authelia with Cloudron's credentials (ldap)
This is the error i got from Authelia in the logs:

This is the config i have in Authelia,
authentication_backend:
password_reset:
disable: true
ldap:
implementation: custom
url: ldaps://cloudrons_ip:636
start_tls: false
tls:
server_name: my.cloudrons_domain
skip_verify: true
minimum_version: TLS1.2
base_dn: ou=users,dc=cloudron
username_attribute: uid
additional_users_dn: ou=users,dc=cloudron
users_filter: (&({username_attribute}={input})(objectClass=person))
additional_groups_dn: ou=groups,dc=cloudron
groups_filter: (&(member=uid={input},cn=users,cn=accounts,dc=cloudron)(objectclass=groupofnames))
group_name_attribute: cn
mail_attribute: mail
display_name_attribute: givenName
user: cn=admin,ou=system,dc=cloudron
password: "password for ldap in cloudron"Am i missing a step somewhere or maybe i have the "users_filter" or "groups_filter" setup in the wrong way?
Maybe someone can give me a pointer into the right direction.......
.I feel i'm so close to an almost working situation here.....

-
I think what you really want here is a custom Cloudron app package, running authelia and have the
ldapaddon enabled.If you connect to the internal ldap server, then it will auth only against per-app generated credentials (the app gets those via env variables) for the initial admin bind to allow searching.
Alternately you can enable exposed ldap and connect via the external route to then.
-
I think what you really want here is a custom Cloudron app package, running authelia and have the
ldapaddon enabled.If you connect to the internal ldap server, then it will auth only against per-app generated credentials (the app gets those via env variables) for the initial admin bind to allow searching.
Alternately you can enable exposed ldap and connect via the external route to then.
-
@nebulon
Thanks for the quick response.
I do have the alternately way exposed in this setup for now, but it's still the local way i want to connect...
do i have to connect it through domain? or is it still possible to do this via it's ip? locally? -
@DanTheMan you have to use the external ldap domain, as the server will check the source IP.
@nebulon
If i try to connect through it's Cloudrons external ldap domain, Authelia is not starting anymore, but if i reverse the action and connect through Cloudrons internal ip, Authelia is starting up and working again.Now for the test, if i remove Authelia's ip from the Restrict Access list in Cloudron, as suggested Authelia fails to start and Cloudron is doing it's job by refusing the not listed ip from Authelia. if i add Authelia's ip in the Restrict Access list in Cloudron again, Authelia starts up.
So i think it's possible to connect internally...... i guessA second question would be, if i have the Ldap part working, how could i Adapt the Nginx-Config for the Cloudron Apps, to protect the required SSO flow Authelia offers?
I think and feel that's going to be a lot harder to accomplish....
-
I don't quite know Authelia, so hard to say why it wouldn't startup in such a case. Just to be sure, have you enable the directory server in your Cloudron? This can be found at the bottom of the users view in your Cloudron dashboard.
But also as you correctly mention the required nginx changes to be persistent across Cloudron updates, it really makes so much more sense to bundle it as a Cloudron app.
-
 N nebulon marked this topic as a question on
N nebulon marked this topic as a question on
-
I don't quite know Authelia, so hard to say why it wouldn't startup in such a case. Just to be sure, have you enable the directory server in your Cloudron? This can be found at the bottom of the users view in your Cloudron dashboard.
But also as you correctly mention the required nginx changes to be persistent across Cloudron updates, it really makes so much more sense to bundle it as a Cloudron app.
@nebulon
I'm totally sure that I have enabled the directory server in Cloudron, not sure where it's stuck...Maybe I will try and give it a go to package Authelia as an app in Cloudron. Only thing is i have zero experience with that, so it's going to be a learning curve....
Maybe @Jan-Macenka can help/assist me with that?
-
 J james has marked this topic as solved on
J james has marked this topic as solved on
