Just had an Abuse Report against my Cloudron - What to do?
-
Linode support have just contacted me reporting the following:
We have received a report of Brute Force attempts originating from your Linode. This is most likely the result of a system compromise. If we have not heard from you in 24 hours, we may need to place network restrictions on your Linode to prevent further attacks.
Abuse Report
Extracted Details
ip 194.195.127.xxx
send_date 2023-07-17T04:57:51Z
received_date 2023-07-17T04:58:28Z
format fail2ban
This report was generated by AbusixI booted into Rescue Mode and run ClamAV and found no compromises. Any other ideas?
Thanks,
Shane. -
I had something similar, and uninstalled 2 recently installed/restored apps.
One was StirlingPDF (just because it was the last application installed : I do not believe this was the cause).
The other was a Wordpress Developer instance. I think this was the cause. I deleted it it without investigation.
It seemed to stop the problem.
Check which applications are running. Maybe stop them (instead of uninstalling) and see if this resolves the error reports.
My instance is on Hetzner and they provide a link to check the problem - don't know whether Linode do this.
Then I filed a statement, and after checking, Hetzner closed the incident. -
I had something similar, and uninstalled 2 recently installed/restored apps.
One was StirlingPDF (just because it was the last application installed : I do not believe this was the cause).
The other was a Wordpress Developer instance. I think this was the cause. I deleted it it without investigation.
It seemed to stop the problem.
Check which applications are running. Maybe stop them (instead of uninstalling) and see if this resolves the error reports.
My instance is on Hetzner and they provide a link to check the problem - don't know whether Linode do this.
Then I filed a statement, and after checking, Hetzner closed the incident.@timconsidine Thanks. The only app I had actively running but I haven't used or paid attention to for a while was LibreTranslate. I've deleted that app for now and just running Mastodon. Will see if that placates the Linode security team.
-
Out of interest, did you already have ClamAV installed or you installed it in response to this incident ?
Does it need to run while in rescue mode, or can it be run while VPS is running normally ? -
@shanelord01 Is there any other info on what kind of Brute Force is attempted?
Also, have you been with this IP and domain for a long enough time? I have seen these reports come very late after 6 months even. What is send_date and received_data in this context? The date of the report or the abuse?
-
Out of interest, did you already have ClamAV installed or you installed it in response to this incident ?
Does it need to run while in rescue mode, or can it be run while VPS is running normally ?@timconsidine They recommend using it in rescue mode. I had to install it (Linode provide an all-in-one script to update it and run the scan).
Minor issue with the GPG keys stopping apt from running that I had to fix (thanks ChatGPT for the assist).
Steps to fix
Here are the steps to fix the GPG error on Finnix Linux:-
Open a terminal or SSH into your Finnix Linux system.
-
Run the following command to retrieve the missing public keys:
gpg --keyserver keyserver.ubuntu.com --recv-keys 0E98404D386FA1D9 gpg --keyserver keyserver.ubuntu.com --recv-keys 6ED0E7B82643E131 -
Once the keys are imported, run the following command to export the keys to a file:
gpg --export 0E98404D386FA1D9 > pubkey1.asc gpg --export 6ED0E7B82643E131 > pubkey2.asc -
Once the keys are imported, create a new file in the trusted.gpg.d directory using the touch command. For example:
touch /etc/apt/trusted.gpg.d/debian-keys.gpg -
Now, move the exported key files to the
trusted.gpg.ddirectory:sudo mv pubkey1.asc /etc/apt/trusted.gpg.d/debian-keys.gpg sudo mv pubkey2.asc /etc/apt/trusted.gpg.d/debian-keys.gpg -
Update your package lists by running:
apt-get update
After following these modified steps, the missing GPG keys should be added to the
trusted.gpg.ddirectory, and you should be able to update and install packages without encountering the GPG error. -
-
@shanelord01 Is there any other info on what kind of Brute Force is attempted?
Also, have you been with this IP and domain for a long enough time? I have seen these reports come very late after 6 months even. What is send_date and received_data in this context? The date of the report or the abuse?
@girish I only have the info provided and the attached image.
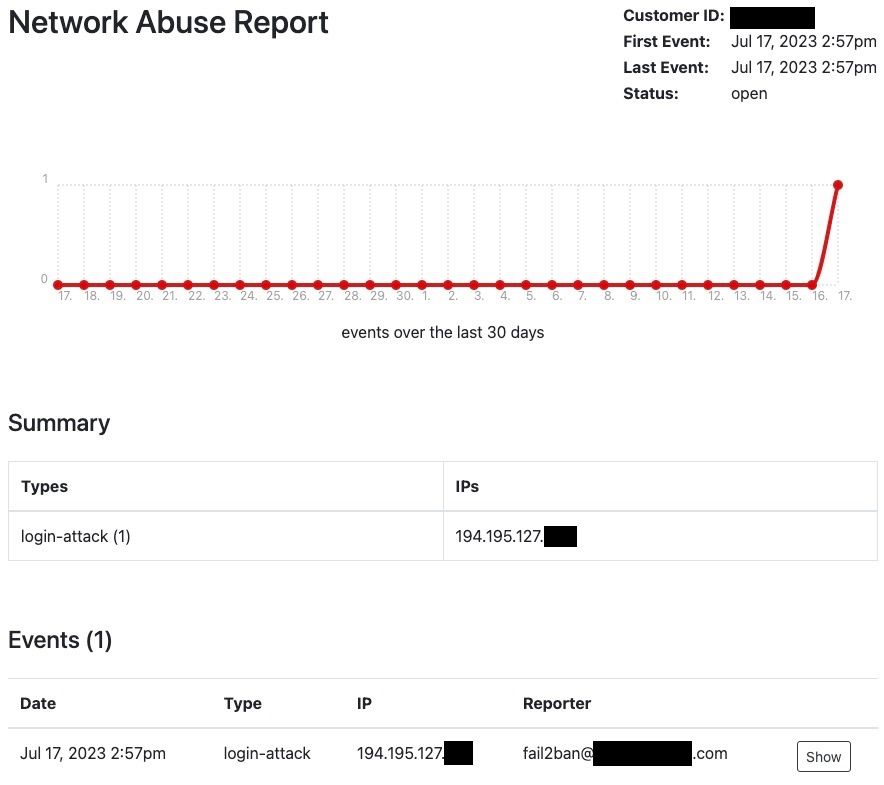
-
That is indeed quite abstract with no information on what is being attacked... Are you able to ask them what login attack means here? via SSH or HTTP ?
@girish I've asked and they have no more information. My scans and checks were enough for them to consider the case closed and no mitigation from them required.
-
@shanelord01 BTW, in case you run AdGuard, please be aware of this security issue - https://docs.cloudron.io/apps/adguard-home/#securing-installation
-
 G girish marked this topic as a question on
G girish marked this topic as a question on
-
 G girish has marked this topic as solved on
G girish has marked this topic as solved on
-
Hi, I've just had a report from digital ocean my hosting provider for my cloudron instance. How could I investigate, because I have several apps on my cloudron instance ?
