Email Spoofing Issue
-
+1 for virus on desktop. Windows?
-
This is what I found as a queued email:
{
"ts": 1756359482397,
"type": "queued",
"direction": "outbound",
"uuid": "1332F07B-0C99-419E-A058-C1C88C5B8A94.1",
"messageId": "<8cdb5704f0341e15369841ea1ed2d8d2ec82cb3e@w*****.in>",
"mailFrom": "<dikshant@w*****.in>",
"spamStatus": null,
"mailbox": null,
"quotaPercent": null,
"rcptTo": [
"blinbernard@sfr.fr",
"cfcappa@hotmail.com",
"saqrhani@gmail.com",
"60saladino@gmail.com",
"johnbagby@yahoo.com"
],
"remote": {
"ip": "118.151.221.26",
"port": 41442,
"host": "NXDOMAIN",
"info": "NXDOMAIN",
"closed": false,
"is_private": false,
"is_local": false
},
"authUser": "dikshant@w******.in",
"message": "Message Queued (1332F07B-0C99-419E-A058-C1C88C5B8A94.1)"
}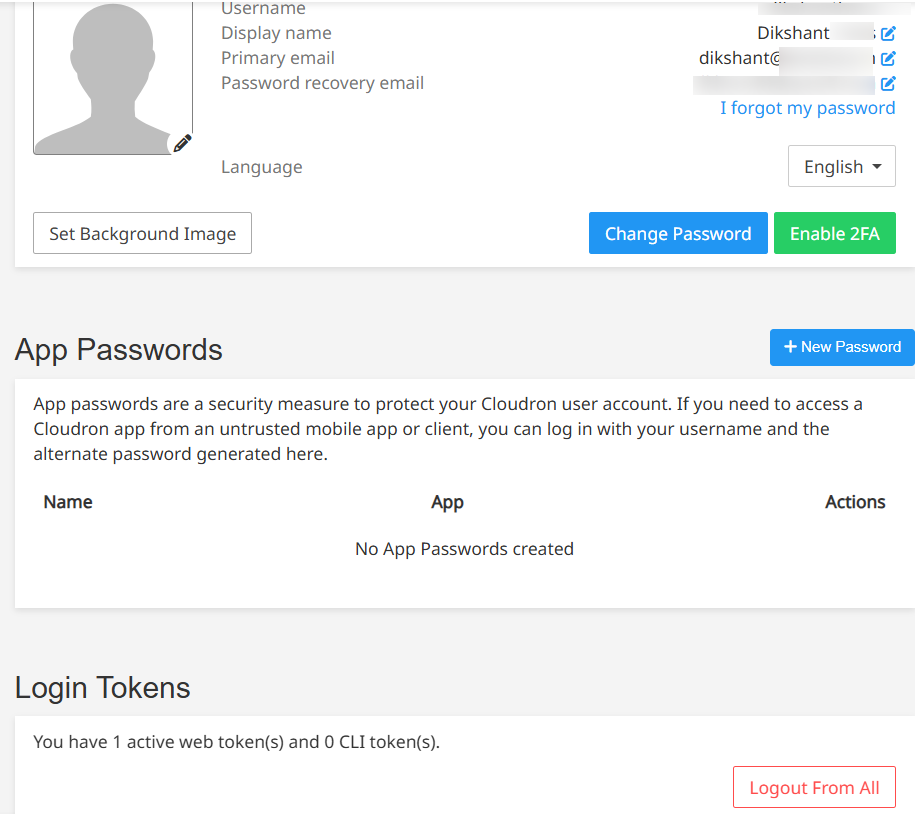
No app passwords as well.
Also, I'm sure there is no virus as well in the system.
-
The log entry shows that the email originated from an IP in Indonesia which does not have the best reputation (the ISP is PT Centrin Online Prima) and was sent whilst logged in as dikshant@... Does this information help you to identify the connections?
If you do not recognise the connections, check some of the other log entries. Are the mails all being sent from the same IP? If so, you could block it in the network settings. If not, do you see a pattern?
-
@robi Yes, I did that already, but if not don,e then even if changing the password for the email won't log them out on its own?
@webliska logins are session based.
You can change the password all you like, as long as the session is active, it doesn't prevent access.
The logs may be misleading in printing the user logged in, when it's really just checking for an active session.
Hence the button exists.
-
@webliska logins are session based.
You can change the password all you like, as long as the session is active, it doesn't prevent access.
The logs may be misleading in printing the user logged in, when it's really just checking for an active session.
Hence the button exists.
@robi said in Email Spoofing Issue:
logins are session based.
You can change the password all you like, as long as the session is active, it doesn't prevent access.
This was the other thing I was wondering, together with a virus laden local machine somewhere, i.e. an active session on a dodgy machine.
-
Regarding infected PC's, I recommend installing Malwarebytes (free) and doing an advanced scan. I caught a crypto miner that Windows Security (Defender) didn't. It was so stubborn to remove that I had to scan/quarantine it twice. CPU/GPU usage would spike when idle, but it would hide when in use or if I opened task manager. PC is used for gaming only so that's definitely how it came in and the top culprits are: Epic games, GTA 5, or Microsoft Flight Sim (mods related).
To summarize the key recommendations for OP:
- scan PC for malware/virus
- delete app passwords found in user's profile section
- reset passwords
- use the log out button to end all active sessions
- restart server for good measure
- report back
-
 J james referenced this topic on
J james referenced this topic on
-
 J james has marked this topic as solved on
J james has marked this topic as solved on
