How to configure LDAP in Discourse?
-
I see. I don't know where the plugin data is stored but I suppose the official package can be modified to include the LDAP addon, the plugin and its settings.
My personal incentive however, is to improve the experience for users (wrt the bullets above). Package automation can come later.
-
Gets a little technical about ruby and how discourse manages the plugins, but that all sort of goes hand-in-hand. Depending how the next day or two go, I'll see about doing something that we can use in order to keep the conversation moving and have a base to tackle some of those features from. Appreciate the context of your goals; I'll bear that in mind when the code starts flying

-
Gets a little technical about ruby and how discourse manages the plugins, but that all sort of goes hand-in-hand. Depending how the next day or two go, I'll see about doing something that we can use in order to keep the conversation moving and have a base to tackle some of those features from. Appreciate the context of your goals; I'll bear that in mind when the code starts flying

@jimcavoli Did any code start flying?

-
@jimcavoli Did any code start flying?

-
@girish It was not. As mentioned earlier I did some light digging into the issue but as you can see in this issue that is where it's at currently.
I figured there's no harm in enabling the Cloudron LDAP addon in the package but I realize that as maintainer you may have another view on that matter.
-
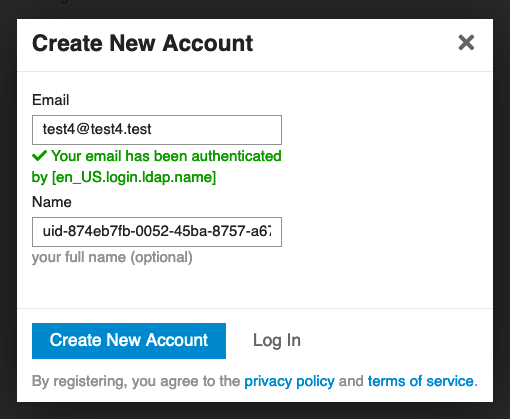
@yusf If I understand the current situation, if the LDAP plugin is enabled:
- User logs in.
- User sees a screen to 'create new account'. User has to just click through.
Is this the case? If so, that does not seem like a major issue.
-
@yusf To keep you updated, I looked into this a bit further. The issue is that when we add ldap as addon, Cloudron UI selects this as the default. For an app like discourse, using LDAP is uncommon since it's mostly a publicly forum use case.
I think before we add LDAP support to nodebb/discourse etc, we need to fix Cloudron to support "dynamic addons". This way one can toggle LDAP support on/off whenever they want. That's the best way to fix this. Otherwise, I suspect, people will blindly install Discourse with LDAP, then disable LDAP inside Discourse and this will only lead to problems (since in Cloudron packages currently we assume that LDAP support is never removed like that inside an app).
-
@yusf To keep you updated, I looked into this a bit further. The issue is that when we add ldap as addon, Cloudron UI selects this as the default. For an app like discourse, using LDAP is uncommon since it's mostly a publicly forum use case.
I think before we add LDAP support to nodebb/discourse etc, we need to fix Cloudron to support "dynamic addons". This way one can toggle LDAP support on/off whenever they want. That's the best way to fix this. Otherwise, I suspect, people will blindly install Discourse with LDAP, then disable LDAP inside Discourse and this will only lead to problems (since in Cloudron packages currently we assume that LDAP support is never removed like that inside an app).
@girish Seems like an apt solution to the problem. Thanks for looking into it.
For what it’s worth I’m often faced with the opposite use-case: some group need internal forum software, apart from other Cloudron services. So I’m interested in doing the same thing with NodeBB.
-
@yusf To keep you updated, I looked into this a bit further. The issue is that when we add ldap as addon, Cloudron UI selects this as the default. For an app like discourse, using LDAP is uncommon since it's mostly a publicly forum use case.
I think before we add LDAP support to nodebb/discourse etc, we need to fix Cloudron to support "dynamic addons". This way one can toggle LDAP support on/off whenever they want. That's the best way to fix this. Otherwise, I suspect, people will blindly install Discourse with LDAP, then disable LDAP inside Discourse and this will only lead to problems (since in Cloudron packages currently we assume that LDAP support is never removed like that inside an app).
@girish said in How to configure LDAP in Discourse?:
For an app like discourse, using LDAP is uncommon since it's mostly a publicly forum use case.
Even in those cases it'd still be nice to have LDAP, like we can in Rocket.Chat right now, i.e. Cloudron uses can use LDAP to login to Rocket.Chat using their Clourdon credentials, and non-Cloudron users can just register and login as normal too.
I'd like the same UX for Discourse too, best of both worlds!

-
@yusf To keep you updated, I looked into this a bit further. The issue is that when we add ldap as addon, Cloudron UI selects this as the default. For an app like discourse, using LDAP is uncommon since it's mostly a publicly forum use case.
I think before we add LDAP support to nodebb/discourse etc, we need to fix Cloudron to support "dynamic addons". This way one can toggle LDAP support on/off whenever they want. That's the best way to fix this. Otherwise, I suspect, people will blindly install Discourse with LDAP, then disable LDAP inside Discourse and this will only lead to problems (since in Cloudron packages currently we assume that LDAP support is never removed like that inside an app).
-
@yusf Yes, it should remain compatible. I haven't gotten time to updating the Dockerfile to have the LDAP plugin pre-installed and pre-configured. If you have the code for that, I can look into merging it.
@girish yet another reason for having the LDAP plugin for Discourse pre-installed and pre-configured on Cloudron would be so that we can start to try and reverse engineer the new Discourse Teams as much as possible (sadly it's not all open source, although as I understand it lots of the features are just using open source plugins)
More info about the difference between Discourse and Discourse Teams:
https://support.teams.discourse.com/docs?topic=85
https://meta.discourse.org/t/comparing-discourse-for-teams-with-discourse/168423/7Edit: and following my prompts they've now added the list of open source plugins they use in Teams to that support link, i.e.
Ships with the following official plugins: akismet, assign, cakeday, calendar, chat-integration, checklist, code-review, docs, encrypt, footnote, github, graphviz, math, openid-connect, policy, rss-polling, solved, spoiler-alert
-
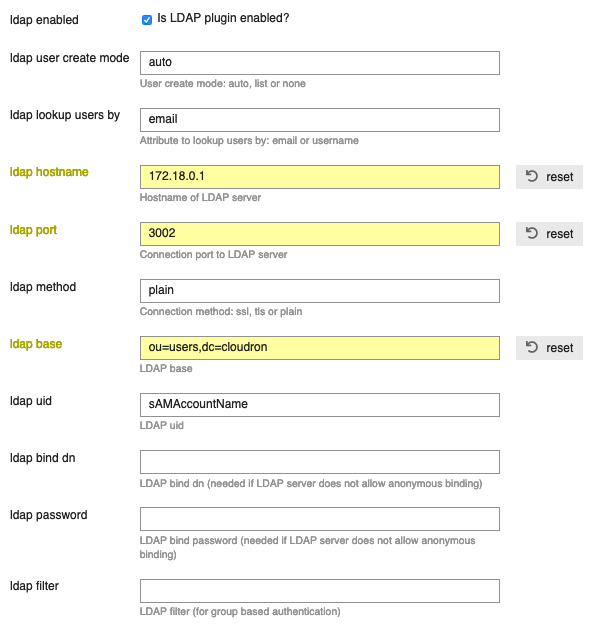
Sorry. Got to the party too late. Today I installed the LDAP plugin from here https://github.com/jonmbake/discourse-ldap-auth and took some ldap creds from my wekan app.
Short info: both user managements lives together in harmony
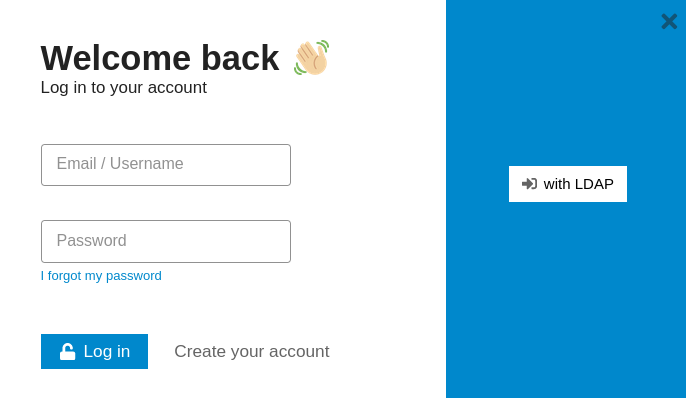
In my understanding the sign-up process goes to discourse user management. LDAP is only for the sign-in process (makes sense).
The only glitch at the moment:

Disabling LDAP in the Plugin settings doesn't change anything.My 2 cents for the moment: please add the LDAP addon to this app, because of the plugin and some use cases, where LDAP makes sense.
-
Sorry. Got to the party too late. Today I installed the LDAP plugin from here https://github.com/jonmbake/discourse-ldap-auth and took some ldap creds from my wekan app.
Short info: both user managements lives together in harmony

In my understanding the sign-up process goes to discourse user management. LDAP is only for the sign-in process (makes sense).
The only glitch at the moment:

Disabling LDAP in the Plugin settings doesn't change anything.My 2 cents for the moment: please add the LDAP addon to this app, because of the plugin and some use cases, where LDAP makes sense.
-
@luckow said in How to configure LDAP in Discourse?:
Disabling LDAP in the Plugin settings doesn't change anything.
Probably have to restart discourse?
-
Sorry. Got to the party too late. Today I installed the LDAP plugin from here https://github.com/jonmbake/discourse-ldap-auth and took some ldap creds from my wekan app.
Short info: both user managements lives together in harmony

In my understanding the sign-up process goes to discourse user management. LDAP is only for the sign-in process (makes sense).
The only glitch at the moment:

Disabling LDAP in the Plugin settings doesn't change anything.My 2 cents for the moment: please add the LDAP addon to this app, because of the plugin and some use cases, where LDAP makes sense.
@luckow said in How to configure LDAP in Discourse?:
My 2 cents for the moment: please add the LDAP addon to this app, because of the plugin and some use cases, where LDAP makes sense.
+1000000
-
 J james marked this topic as a regular topic on
J james marked this topic as a regular topic on