Incoming mail server listed on Spamhaus, but seems to still pass to mailing list?
-
I've noticed a recurring spam message coming through to a mailing list recipient - and unfortunately since mailing lists forward on messages even when identified as spam - I am trying to block the mail server from connecting. The mail server linked to sending a lot of spam on to one of my clients is
mail.fultonmta.comand when I did a quick blocklist check on it it's shown in Spamhaus and many others. So I'm curious... why is this message still coming through? Does the mailing list not reject messages even if on Spamhaus, only for mailboxes perhaps?https://mxtoolbox.com/SuperTool.aspx?action=blacklist%3Amail.fultonmta.com
{ "ts": 1615745498759, "type": "queued", "direction": "inbound", "uuid": "6580A6F8-8514-44F7-9817-5D9BE7EACD5B.1", "remote": { "ip": "104.206.50.251", "port": 59258, "host": "mail.fultonmta.com", "info": "mail.fultonmta.com", "closed": false, "is_private": false, "is_local": false }, "authUser": null, "mailFrom": "<SRS0=07d1=IN=lithiumlode.com=warby.parker.ad-<clientUsername>=<clientDomain>@<clientDomain>>", "rcptTo": [ "<<clientEmailAddressOnCloudronWhichForwardsToGmailLater>>" ], "details": { "spamStatus": "No, score=4.6 required=5.0 tests=AC_FROM_MANY_DOTS,ADMITS_SPAM, \tDKIM_SIGNED,DKIM_VALID,DKIM_VALID_AU,DKIM_VALID_EF,FSL_THIS_IS_ADV, \tHTML_IMAGE_RATIO_02,HTML_MESSAGE,PLING_QUERY,SPF_HELO_NONE,SPF_PASS, \tURIBL_BLACK autolearn=no autolearn_force=no version=3.4.4", "message": "Message Queued (6580A6F8-8514-44F7-9817-5D9BE7EACD5B.1) (6580A6F8-8514-44F7-9817-5D9BE7EACD5B.1)" } }Unfortunately I can't tell when the IP or hostname was added to the Spamhaus network, so it's possible it's only just recently added and not all this time before, but I doubt it given the amount of times it's been sending and given how many other lists it's on.
So I guess my question really is... when a connecting mail server / IP is on Spamhaus but the message is to a mailing list, does that still get checked and blocked since it's on Spamhaus like it does for normal mailboxes? Trying to figure out if something is broken or if it's actually working as designed. Also trying to see how I can block this server, ultimately.
One thing I noticed though too is the mail server hostname
mail.fultonmta.com(which is the mail server for the spammy domain) resolves to about a dozen IP addresses, so I suppose it's possible it came from an IP which isn't yet on it, though I'm not sure. -
I've noticed a recurring spam message coming through to a mailing list recipient - and unfortunately since mailing lists forward on messages even when identified as spam - I am trying to block the mail server from connecting. The mail server linked to sending a lot of spam on to one of my clients is
mail.fultonmta.comand when I did a quick blocklist check on it it's shown in Spamhaus and many others. So I'm curious... why is this message still coming through? Does the mailing list not reject messages even if on Spamhaus, only for mailboxes perhaps?https://mxtoolbox.com/SuperTool.aspx?action=blacklist%3Amail.fultonmta.com
{ "ts": 1615745498759, "type": "queued", "direction": "inbound", "uuid": "6580A6F8-8514-44F7-9817-5D9BE7EACD5B.1", "remote": { "ip": "104.206.50.251", "port": 59258, "host": "mail.fultonmta.com", "info": "mail.fultonmta.com", "closed": false, "is_private": false, "is_local": false }, "authUser": null, "mailFrom": "<SRS0=07d1=IN=lithiumlode.com=warby.parker.ad-<clientUsername>=<clientDomain>@<clientDomain>>", "rcptTo": [ "<<clientEmailAddressOnCloudronWhichForwardsToGmailLater>>" ], "details": { "spamStatus": "No, score=4.6 required=5.0 tests=AC_FROM_MANY_DOTS,ADMITS_SPAM, \tDKIM_SIGNED,DKIM_VALID,DKIM_VALID_AU,DKIM_VALID_EF,FSL_THIS_IS_ADV, \tHTML_IMAGE_RATIO_02,HTML_MESSAGE,PLING_QUERY,SPF_HELO_NONE,SPF_PASS, \tURIBL_BLACK autolearn=no autolearn_force=no version=3.4.4", "message": "Message Queued (6580A6F8-8514-44F7-9817-5D9BE7EACD5B.1) (6580A6F8-8514-44F7-9817-5D9BE7EACD5B.1)" } }Unfortunately I can't tell when the IP or hostname was added to the Spamhaus network, so it's possible it's only just recently added and not all this time before, but I doubt it given the amount of times it's been sending and given how many other lists it's on.
So I guess my question really is... when a connecting mail server / IP is on Spamhaus but the message is to a mailing list, does that still get checked and blocked since it's on Spamhaus like it does for normal mailboxes? Trying to figure out if something is broken or if it's actually working as designed. Also trying to see how I can block this server, ultimately.
One thing I noticed though too is the mail server hostname
mail.fultonmta.com(which is the mail server for the spammy domain) resolves to about a dozen IP addresses, so I suppose it's possible it came from an IP which isn't yet on it, though I'm not sure.@d19dotca It seems the IP is on the zen spamhaus. So, it must have been caught by the DNSBL and the mail won't even be accepted. It could be that it's on the spamlist now but not during the time you created the post.
root@my:~# host 251.50.206.104.zen.spamhaus.org 251.50.206.104.zen.spamhaus.org has address 127.0.0.3 -
@d19dotca It seems the IP is on the zen spamhaus. So, it must have been caught by the DNSBL and the mail won't even be accepted. It could be that it's on the spamlist now but not during the time you created the post.
root@my:~# host 251.50.206.104.zen.spamhaus.org 251.50.206.104.zen.spamhaus.org has address 127.0.0.3@girish I noticed a clearly-spam message getting past still though. It arrived just 11 minutes ago and when I checked the IP it was listed on 9 blacklists including 3 of the 4 I have enabled for denying connections too, but yet it got through. It's technically possible it just wasn't listed at that moment and was listed inside of the last 11 minutes, but I find this hard to believe when I've had multiple experiences like this now.
I realize blacklists tend to be pretty "realtime" so change frequently but what are the odds that around 10 blacklists have it listed, three of the four I have enabled too, and it still passed through as if it wasn't on any of those lists just 11 minutes prior? I'm not 100% convinced this is working every time. This could still be coincidental, but every time this happens where I can see the IP listed in a number of blacklists just minutes after it was received yet never got denied... so I feel less trusting of that explanation that it just wasn't listed earlier. This was also for a forwarded address again too. Here's the latest log entry of this example:
{ "ts": 1615911038010, "type": "queued", "direction": "inbound", "uuid": "754E0225-803C-4DE7-B854-630BF768D010.1", "remote": { "ip": "173.232.62.180", "port": 59517, "host": "mail.gryphonmta.com", "info": "mail.gryphonmta.com", "closed": false, "is_private": false, "is_local": false }, "authUser": null, "mailFrom": "<SRS0=7798=IP=classifieds113.com=betterbutterspreadercom_help-<clientUsername>=<clientDomain>@<clientDomain>>", "rcptTo": [ "<<clientEmail>>" ], "details": { "spamStatus": "No, score=1.5 required=5.0 tests=DKIM_SIGNED,DKIM_VALID, \tDKIM_VALID_AU,DKIM_VALID_EF,HTML_IMAGE_RATIO_02,HTML_MESSAGE, \tSPF_HELO_NONE,SPF_PASS,URIBL_BLACK autolearn=no autolearn_force=no \tversion=3.4.4", "message": "Message Queued (754E0225-803C-4DE7-B854-630BF768D010.1) (754E0225-803C-4DE7-B854-630BF768D010.1)" } }11 minutes after it arrived, I checked the MXToolbox (https://mxtoolbox.com/SuperTool.aspx?action=blacklist%3A173.232.62.180&run=toolpage) and it was on 9 different lists at that moment.
PS - The two examples in this thread so far are showing off what seem to be the worst-offender here, the
mail.fultonmta.comandmail.gryphonmta.comIPs. I'm going to send them abuse emails soon so they can try to stop it if they care about it themselves too. haha. -
This just happened again, new IP but same hostname. This time I caught it 18 minutes later. Here's the state as of 18 minutes past when it was received:
Log:
{ "ts": 1615918296442, "type": "queued", "direction": "inbound", "uuid": "653AD85F-4A99-4F90-8AF5-C921B71F3FDD.1", "remote": { "ip": "173.232.62.176", "port": 48492, "host": "mail.gryphonmta.com", "info": "mail.gryphonmta.com", "closed": false, "is_private": false, "is_local": false }, "authUser": null, "mailFrom": "<SRS0=42fa=IP=sunsetpetals.com=easycanvasprintsdeals.offer-<clientUsername>=<clientDomain>@<clientDomain>>", "rcptTo": [ "<<clientEmail>>" ], "details": { "spamStatus": "Yes, score=5.1 required=5.0 tests=ADMITS_SPAM,DKIM_SIGNED, \tDKIM_VALID,DKIM_VALID_AU,DKIM_VALID_EF,FSL_THIS_IS_ADV, \tHTML_IMAGE_ONLY_24,HTML_MESSAGE,HTML_SHORT_LINK_IMG_3,SPF_HELO_NONE, \tSPF_PASS,URIBL_BLACK autolearn=no autolearn_force=no version=3.4.4", "message": "Message Queued (653AD85F-4A99-4F90-8AF5-C921B71F3FDD.1) (653AD85F-4A99-4F90-8AF5-C921B71F3FDD.1)" } }Listed on...
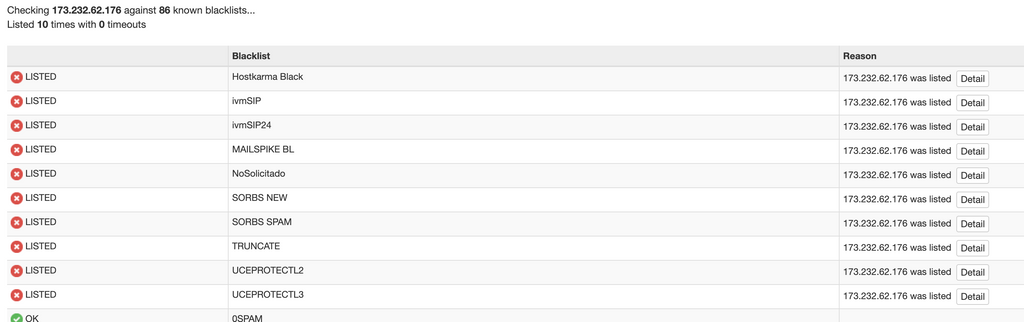
Of the blacklists above, I have MAILSPIKE BL added in my mail server but it doesn't seem to be denying anything in it, despite it appearing to be already on a number of blacklists including the one I have enabled.
This behaviour seems consistent to one particular recipient and much of the spam comes from the
mail.gryphonmta.comandmail.fultonmta.commail servers, because the Mailspike BL seems to be working fine for other connections to my mail server still.I'm pretty convinced at this point these IPs have been listed for a while now in the various blacklists given that the image above is basically what I see every time I check the IP from these two mail servers, so I'm pretty confident this isn't working properly 100% of the time and the theory of it not being listed earlier I suspect is not valid in this case. It's happening far too often for this to be not listed in the blacklists it's set to check.
-
Okay... I may be on the side of this working properly again. lol. Maybe I've been wrong this whole time in thinking it wasn't working correctly.
So coincidentally I was checking the mail server logs and saw another example of the same message go through to the same recipient from the same mail server, it was listed in the logs as "just now" so I quickly checked mxtoolbox and found that only 4 at that time had been listed, none of which were ones I was using.
Here is how it looked at the very moment I checked when it was "just now" in the logs:
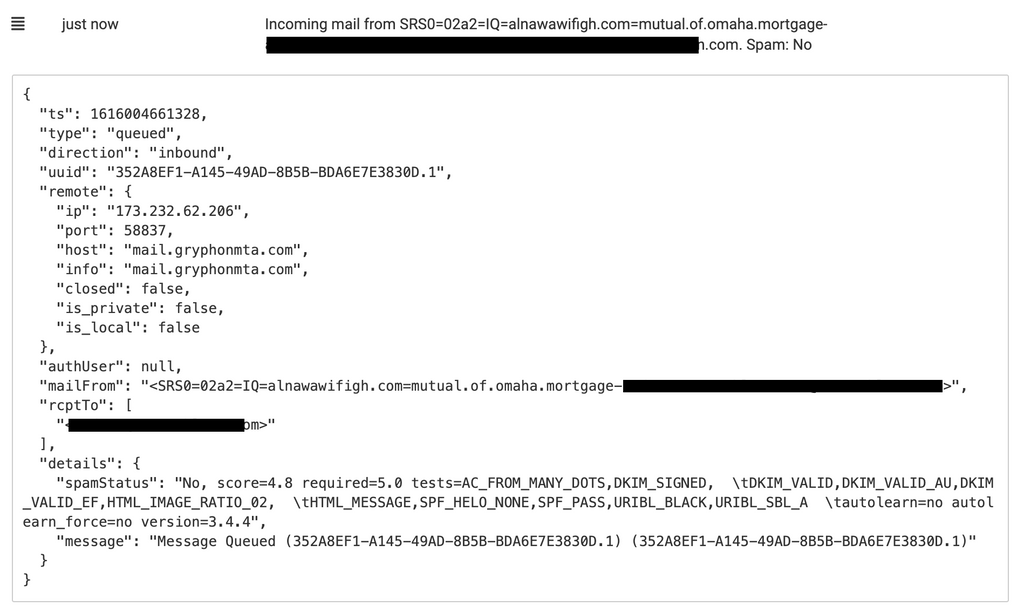
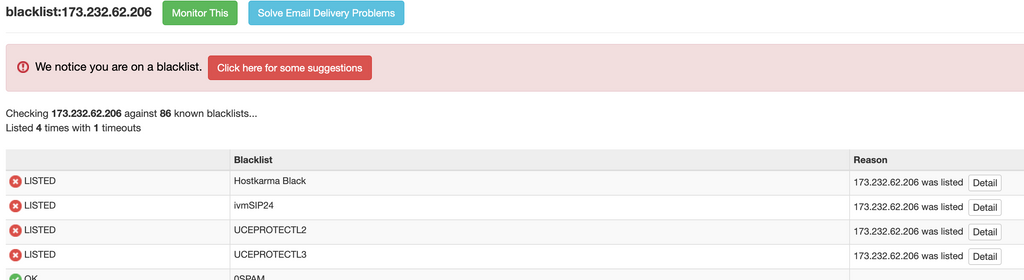
Edit: Checking about 6 minutes later, I see the blocklists have aleady been updated for more (Spamhaus Zen in this case would have caught it if it were about 5 minutes earlier):
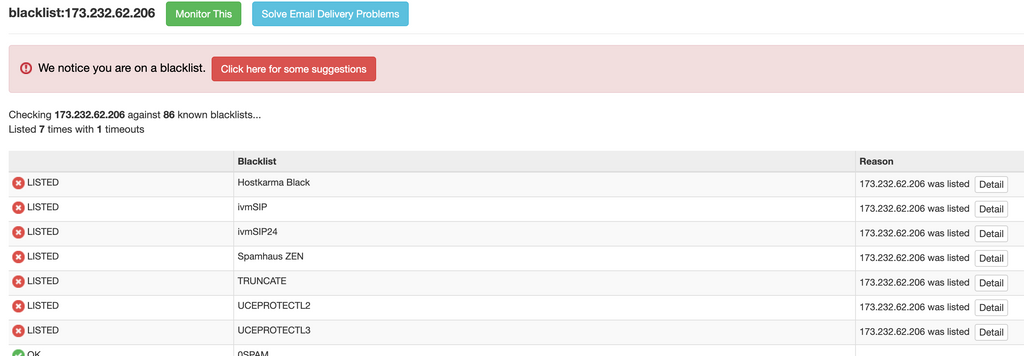
So I guess we can probably mark this as resolved, as I now see conclusive evidence that the various blocklists used just didn't have it listed until a few minutes after the message was received. I guess in order for it to adapt so quickly this spam attack on one of my users from those mail servers must be right at the beginning of a spam wave. Kind of neat actually to see how real-time these lists are. haha.
