Harden security features
-
In this thread https://forum.cloudron.io/topic/4723/what-s-coming-in-cloudron-6-3/4?_=1637136154239 long time ago a lot of suggestions where offered to harden the Cloudron security.
Still today IMHO we are still blind in for example failed logins, rate limiting, etc.
Is Cloudron audited? Is it an idea to gather ideas to harden Cloudron like mentioned in that thread?
-
There is no external audit happening at the moment.
Rate-limits on the login routes is implemented by now, for further recommendations I guess we should just handle those as separate feature requests here and have a discussion on the individual points.
-
In this thread https://forum.cloudron.io/topic/4723/what-s-coming-in-cloudron-6-3/4?_=1637136154239 long time ago a lot of suggestions where offered to harden the Cloudron security.
Still today IMHO we are still blind in for example failed logins, rate limiting, etc.
Is Cloudron audited? Is it an idea to gather ideas to harden Cloudron like mentioned in that thread?
@imc67 things like the FreeScout IP logs are just packaging bugs. If you report them separately, we can fix them. I pushed a new FreeScout package that fixes that, but you get the idea. Would be easier to discuss if the features/bug reports are broken down to separate topics.
-
In this thread https://forum.cloudron.io/topic/4723/what-s-coming-in-cloudron-6-3/4?_=1637136154239 long time ago a lot of suggestions where offered to harden the Cloudron security.
Still today IMHO we are still blind in for example failed logins, rate limiting, etc.
Is Cloudron audited? Is it an idea to gather ideas to harden Cloudron like mentioned in that thread?
@imc67 said in Harden security features:
Is Cloudron audited? Is it an idea to gather ideas to harden Cloudron like mentioned in that thread?
Not audited, but I looked at the code
As mentioned by nebulon; Cloudron have rate limit, which is great against bruteforce attack (bots and humans attack).But as they seem to forget, they also implement AppArmor, which contains the scope of action of each container and suggest you to change SSH port.
They also actively maintain their codes and do regular updates of all the apps and their stack (NGINX, ....), which might sound little but is, in reality, a big win in security.
So basically Cloudron is potentially vulnerable via OpenSSH, NGINX, Haraka, Container Evasion and weaken certificate (SSL/TLS,...).
- OpenSSH; as recommended in the doc, you should install Fail2Ban and change the port
- NGINX; NGINX team is pretty serious about security, so doing update and knowing the nginx rules are the key
- Haraka Mail; Hum I don't know this one
- Container Evasion (Docker): AppArmor is better than nothing, after that, I personally mount /var/lib/docker with
nodev, noexecbut I'm not even sure that help. - Weaken Certificate: you could scan your domains, but A+ at school was enough for me

Otherwise,
- you could close ports with a frontend firewall (at your host provider) you don't use, such as POP3, HTTP (80), ...
- enforcing the 2nd authentification
- and vote for implementation of applications such as CrowSec.
Also; be sure to deploy reputable applications and be active in these respective apps communities.
-
It is not directly related to Cloudron, but I just started to use Cloudflare Access to secure my Self Hosted server at home (not a cloudron). It is a ZeroTrust solution per subdomain (https://developers.cloudflare.com/cloudflare-one/).
My gateway only have HTTPS and SSH open and HTTPS is behind Cloudflare proxy; I know you have to trust Cloudflare as man in the middle...
And then to access any subdomain which pointed to that server, the person need to be part of my GitHub team and be authenticated by GitHub.So why I'm posting this here ?
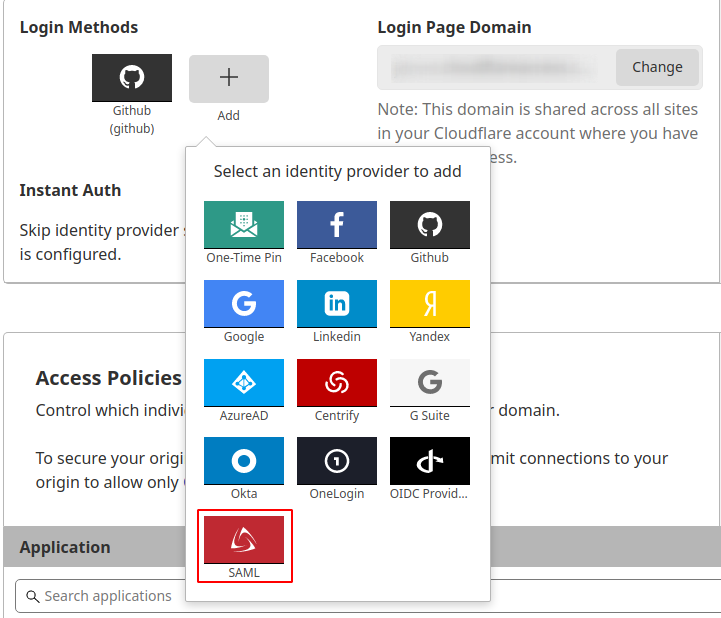
- it is easy to setup, while the One-Time Pin didn't work well for me
- maybe Cloudron would like to
2.1. implement it into their DNS option (but will look Cloudron is in favor to Cloudflare)
2.2. provide and identifiy authentification via SAML (if it is possible) - it is very easy to implement and make any apps/dns ultra secure.
- did I said it was very easy to setup ???

-
It is not directly related to Cloudron, but I just started to use Cloudflare Access to secure my Self Hosted server at home (not a cloudron). It is a ZeroTrust solution per subdomain (https://developers.cloudflare.com/cloudflare-one/).
My gateway only have HTTPS and SSH open and HTTPS is behind Cloudflare proxy; I know you have to trust Cloudflare as man in the middle...
And then to access any subdomain which pointed to that server, the person need to be part of my GitHub team and be authenticated by GitHub.So why I'm posting this here ?

- it is easy to setup, while the One-Time Pin didn't work well for me
- maybe Cloudron would like to
2.1. implement it into their DNS option (but will look Cloudron is in favor to Cloudflare)
2.2. provide and identifiy authentification via SAML (if it is possible) - it is very easy to implement and make any apps/dns ultra secure.
- did I said it was very easy to setup ???

@jodumont said in Harden security features:
provide and identifiy authentification via SAML (if it is possible)
SAML is an old and outdated protocol (that is also hard to work with), a more modern alternative is oidc (OpenID Connect, a standard based on Oauth 2.0), which is also offered in your screenshot.
