Cloudron SPF record does not permit IP
-
@girish said in Cloudron SPF record does not permit IP:
I wonder how it can even have the IP of your home server.
It is not the IP of my server, this is the IP of my DSL at home.
@girish an news on this one?
-
@girish an news on this one?
@girish I do not want to bother you but any news on this?
-
@girish I do not want to bother you but any news on this?
@girish sorry but I have to ask: any update on this?
-
@girish sorry but I have to ask: any update on this?
@jaschaezra
I checked with myself. I confirm the problem with revealing the IP address of the home connection when sending emails from client mail -Thunderbird, K9 (Android), Gmail (iOS). It will probably be the same with other apps. When sending via webmail "Roundcube" the IP address of the home connection does not appear. -
@jaschaezra
I checked with myself. I confirm the problem with revealing the IP address of the home connection when sending emails from client mail -Thunderbird, K9 (Android), Gmail (iOS). It will probably be the same with other apps. When sending via webmail "Roundcube" the IP address of the home connection does not appear.@matix131997 this is correct as that is how the envelope is generated.
In some cases, very useful to use Snappy Mail or other client in Cloudron to avoid source IP issues.
-
@jaschaezra @matix131997 I could reproduce this one. Looks like Haraka outbound is adding that header. Note that this is not a problem for mail delivery as such, but it's not nice that the mail client IP is revealed for no reason. Looking into a fix.
-
@jaschaezra @matix131997 I could reproduce this one. Looks like Haraka outbound is adding that header. Note that this is not a problem for mail delivery as such, but it's not nice that the mail client IP is revealed for no reason. Looking into a fix.
-
@jaschaezra @matix131997 I could reproduce this one. Looks like Haraka outbound is adding that header. Note that this is not a problem for mail delivery as such, but it's not nice that the mail client IP is revealed for no reason. Looking into a fix.
@girish said in Cloudron SPF record does not permit IP:
@jaschaezra @matix131997 I could reproduce this one. Looks like Haraka outbound is adding that header. Note that this is not a problem for mail delivery as such, but it's not nice that the mail client IP is revealed for no reason. Looking into a fix.
And it gives a SPF-Soft-Fail which can at worst lead to being rejected.
-
@girish said in Cloudron SPF record does not permit IP:
@jaschaezra @matix131997 I could reproduce this one. Looks like Haraka outbound is adding that header. Note that this is not a problem for mail delivery as such, but it's not nice that the mail client IP is revealed for no reason. Looking into a fix.
And it gives a SPF-Soft-Fail which can at worst lead to being rejected.
@jaschaezra The receiving mailserver should be checking the the SPF record of the sending SMTP server, not the client, so you shouldn't get a (Soft)fail. Is the server IP not showing in the headers at all?
How often does the IP address of your home DSL connection change? Not a solution but at least a workaround would be to temporarily add that IP to the SPF record.
-
@jaschaezra The receiving mailserver should be checking the the SPF record of the sending SMTP server, not the client, so you shouldn't get a (Soft)fail. Is the server IP not showing in the headers at all?
How often does the IP address of your home DSL connection change? Not a solution but at least a workaround would be to temporarily add that IP to the SPF record.
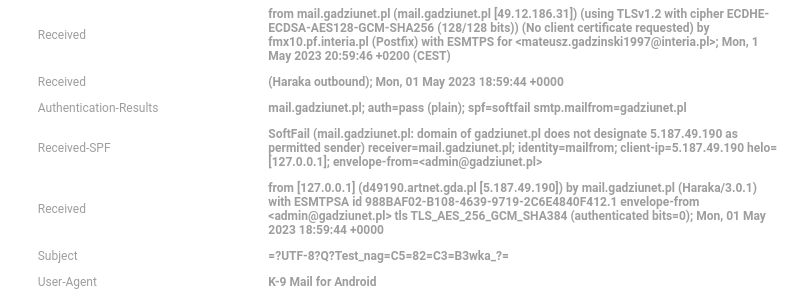
@ccfu
This is a strange case. As you can see from Haraka screen shot, when sending from client mail it assigns an address, just for the forum I included via VPN as the address "SMTP"
-
@girish said in Cloudron SPF record does not permit IP:
@jaschaezra @matix131997 I could reproduce this one. Looks like Haraka outbound is adding that header. Note that this is not a problem for mail delivery as such, but it's not nice that the mail client IP is revealed for no reason. Looking into a fix.
And it gives a SPF-Soft-Fail which can at worst lead to being rejected.
@jaschaezra It shouldn't affect mail delivery, afaik. As @ccfu said, the check is carried out by the receiving mail server and as such the added meta headers have no effect. But it's not desired to add the Client IP, that I agree. You can check this by sending mails to https://www.mail-tester.com/
-
@ccfu
This is a strange case. As you can see from Haraka screen shot, when sending from client mail it assigns an address, just for the forum I included via VPN as the address "SMTP"

@matix131997
Interesting. I still can't get my head around why the recipient mailserver is incorrectly evaluating the client IP and not the server IP in the SPF record though. The mail is not being sent to the recipient by the client but by the SMTP server. -
@jaschaezra It shouldn't affect mail delivery, afaik. As @ccfu said, the check is carried out by the receiving mail server and as such the added meta headers have no effect. But it's not desired to add the Client IP, that I agree. You can check this by sending mails to https://www.mail-tester.com/
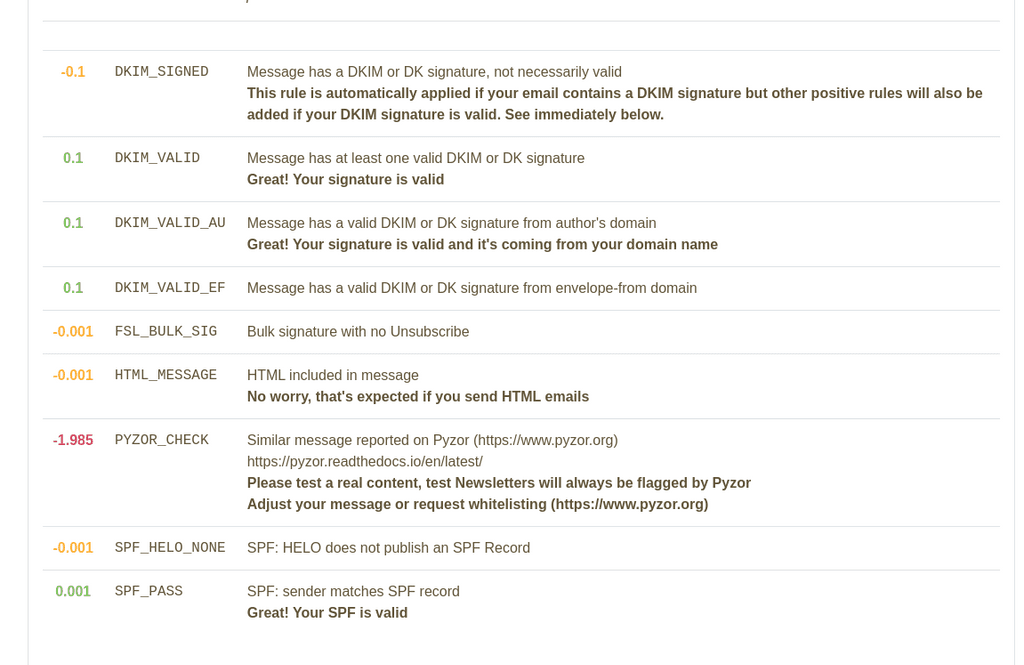
@girish This is the result:
-
@girish This is the result:

@matix131997 Yup, so the SPF is valid. The email header is only the results of Haraka/Cloudron mail server. This is not considered by the destination server.
-
 G girish marked this topic as a question on
G girish marked this topic as a question on
-
I have the exact same problem --- only since updating Cloudron to v7.4.1 from v7.3.6.
So, this has clearly been introduced by v7.4.x.SPF is more important than @staff are making out above.
Fundamentally, the point is that the SENDING Haraka/Cloudron is guilty of injecting the wrong header SPF details into OUTGOING emails.
This needs a rapid solution, as domain and server reputation is at stake!
-
I have the exact same problem --- only since updating Cloudron to v7.4.1 from v7.3.6.
So, this has clearly been introduced by v7.4.x.SPF is more important than @staff are making out above.
Fundamentally, the point is that the SENDING Haraka/Cloudron is guilty of injecting the wrong header SPF details into OUTGOING emails.
This needs a rapid solution, as domain and server reputation is at stake!
Nobody seems to be suggesting that SPF is not important but the SPF details are not injected by Cloudron or Haraka at all. These details are set in the domain's DNS records and can be checked by the receiving SMTP server when processing incoming email.
If a receiving mailserver is checking the wrong headers then it is misconfigured. Alternatively, the SPF record may be incorrect.
-
Nobody seems to be suggesting that SPF is not important but the SPF details are not injected by Cloudron or Haraka at all. These details are set in the domain's DNS records and can be checked by the receiving SMTP server when processing incoming email.
If a receiving mailserver is checking the wrong headers then it is misconfigured. Alternatively, the SPF record may be incorrect.
@ccfu said in Cloudron SPF record does not permit IP:
SPF details are not injected by Cloudron or Haraka at all
If so, then how come I can trace the origin of this problem to the Cloudron update to v7.4.1 from v7.3.6 ?
-
Yes, this is indeed some new information @RoundHouse1924 . What exactly has changed between 7.3.6 and 7.4.1 for you? Are mails getting reported as Spam now?
SPF is more important than @staff are making out above.
SPF is very important. I think you have misread the messages/posts. The "it" in many places is referring to the header in the email message. This header is not used for SPF validation.
-
Yes, this is indeed some new information @RoundHouse1924 . What exactly has changed between 7.3.6 and 7.4.1 for you? Are mails getting reported as Spam now?
SPF is more important than @staff are making out above.
SPF is very important. I think you have misread the messages/posts. The "it" in many places is referring to the header in the email message. This header is not used for SPF validation.
@girish
None of my outgoing mail is being rejected, but headers contain the following (first example sending from Thunderbird on Linux; second example sending from FairEmail on Android):-received-SPF: Fail (my.sharona.cloud: domain of groveland.place does not designate 138.199.6.239 as permitted sender) receiver=my.sharona.cloud; identity=mailfrom; client-ip=138.199.6.239 Authentication-Results: my.sharona.cloud; auth=pass (plain); spf=fail smtp.mailfrom=groveland.placeReceived-SPF: Fail (my.sharona.cloud: domain of citharas.org does not designate 86.15.69.112 as permitted sender) receiver=my.sharona.cloud; identity=mailfrom; client-ip=86.15.69.112 Authentication-Results: my.sharona.cloud; auth=pass (login); spf=fail smtp.mailfrom=citharas.orgIn both cases, the IP addresses belong to the sending mail client, not the server.
One of the 3 domains hosted uses an external relay, the other 2 use the internal SMTP.
Also, each domain's SPF record uses minus all, not tilde all --- so any rejection is not just a softfail:-
TXT v=spf1 a:my.sharona.cloud -allAlthough nothing is rejected by the receiving server, receiving clients show:-
FairEmail shows a waving flag, as per its FAQ:-
"...FairEmail can show a small red warning flag when DKIM, SPF or DMARC authentication failed on the receiving server. You can enable/disable authentication verification in the display settings"
https://github.com/M66B/FairEmail/blob/master/FAQ.mdThe DKIM Verifier Thunderbird extension shows "SPF: fail"
https://addons.thunderbird.net/en-GB/thunderbird/addon/dkim-verifier/So, the bottom line of all this is that the headers incorrectly show that the mail client is the authorised sender. Clearly, as the message passes through the Cloudron mail server (since v7.4.x), something is processed in a manner to cause this.
Hope all this makes sense!
