Securing SSH: disable password authentication
-
The docs don't match what I see in my sshd_config file.
https://docs.cloudron.io/security/
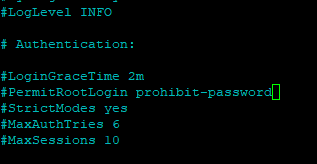
Should I uncomment
PermitRootLogin prohibit-password? -
Follow-up questions/notes:
- I need to uncomment (remove #) from each line I want to "activate", right?
- I tried with without sudo but
systemctl restart sshdreturned something like "ssh_config not found" so I restarted the server instead.
What I did was remove # from the beginning of the SSH port line and changed 22 to 202. It looks like it's working as I couldn't connect thru port 22 anymore. I'm not sure how to secure the rest. VPS installed Ubuntu images come installed with root by default. For my home servers, I set up my own username/password so the process isn't the same. It would be great if a guide/steps could be mentioned in the docs for us noobs.
-
I see you've added another post about it

If you want good security then set up as below. This is the way I use on all servers and where possible on the provider's external firewall I restrict the port on the VPN IP.
PermitRootLogin prohibit-password PubkeyAuthentication yes PasswordAuthentication no KbdInteractiveAuthentication no UsePAM yesprohibit-password - This they started using from version 22.04 as a new security method.
KbdInteractiveAuthentication is the newer line that replaces "ChallengeResponseAuthentication"
Changing port 22 to 202 doesn't make the attack more secure, hackers have started scanning all ports that send back a header that SSH is running on that port.
You have to uncomment the line to make it work.
-
I see you've added another post about it

If you want good security then set up as below. This is the way I use on all servers and where possible on the provider's external firewall I restrict the port on the VPN IP.
PermitRootLogin prohibit-password PubkeyAuthentication yes PasswordAuthentication no KbdInteractiveAuthentication no UsePAM yesprohibit-password - This they started using from version 22.04 as a new security method.
KbdInteractiveAuthentication is the newer line that replaces "ChallengeResponseAuthentication"
Changing port 22 to 202 doesn't make the attack more secure, hackers have started scanning all ports that send back a header that SSH is running on that port.
You have to uncomment the line to make it work.
@matix131997 the exact post I'm looking for! Thank you!
-
In Ubuntu 24.04 the restart does not work with "systemctl restart sshd", but only with "systemctl restart ssh.service".
-
 N nebulon marked this topic as a question on
N nebulon marked this topic as a question on
-
 N nebulon has marked this topic as solved on
N nebulon has marked this topic as solved on
-
 H humptydumpty referenced this topic on
H humptydumpty referenced this topic on
