Update Documentation to warn of Cloudflare Proxy issues
-
Connecting Nextcloud to the Cloudron Collabora Online app doesn't work by default with Cloudflare Proxy enabled on the subdomain.
The fix is to add Cloudflare Trusted IPs to your Cloudron > Network > Configure Trusted IPs & Ranges, like so:
# Cloudflare IPv4 ranges 173.245.48.0/20 103.21.244.0/22 103.22.200.0/22 103.31.4.0/22 141.101.64.0/18 108.162.192.0/18 190.93.240.0/20 188.114.96.0/20 197.234.240.0/22 198.41.128.0/17 162.158.0.0/15 104.16.0.0/13 104.24.0.0/14 172.64.0.0/13 131.0.72.0/22 # Cloudflare IPv6 ranges 2400:cb00::/32 2606:4700::/32 2803:f800::/32 2405:b500::/32 2405:8100::/32 2a06:98c0::/29 2c0f:f248::/32Source: https://www.cloudflare.com/en-gb/ips/
@girish and @nebulon I wonder if these IPs should be pulled and updated from the Cloudflare API when anyone uses Cloudflare DNS settings in Cloudron?
Might save from much confusion potential and many support issues?
-
Hello @marcusquinn
That is interesting and might be worth considering when using Cloudflare as the DNS provider.
Questions I am asking myself are the following:- should this be done by default when Cloudflare is used
- should this only be done if Cloudflare is used with the
Enable proxying for new DNS recordssetting is enabled
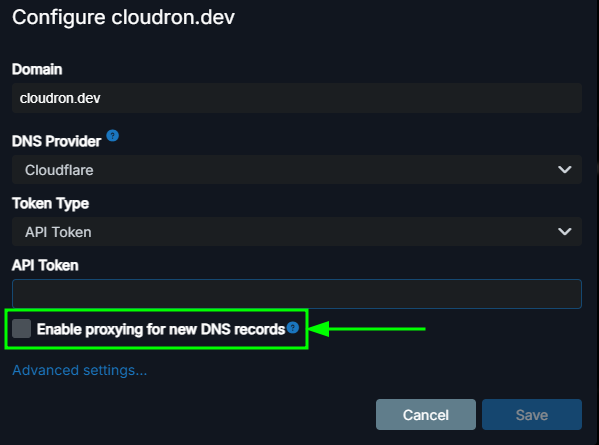
- how often should this list be checked for updates to prevent wrong IP addresses in the Trusted IPs setting
I like idea.
-
Hello @marcusquinn
That is interesting and might be worth considering when using Cloudflare as the DNS provider.
Questions I am asking myself are the following:- should this be done by default when Cloudflare is used
- should this only be done if Cloudflare is used with the
Enable proxying for new DNS recordssetting is enabled

- how often should this list be checked for updates to prevent wrong IP addresses in the Trusted IPs setting
I like idea.
@james said in Update Documentation to warn of Cloudflare Proxy issues:
should this be done by default when Cloudflare is used
Does this refer to the
Allow list for WOPI requestssetting in Nextcloud? Automatically allowing all requests that come from the Cloudflare infrastructure seems like a bad idea for me. -
Hello @fbartels
@marcusquinn said in Update Documentation to warn of Cloudflare Proxy issues:
The fix is to add Cloudflare Trusted IPs to your Cloudron > Network > Configure Trusted IPs & Ranges, like so:
As I understood it, it is about the https://docs.cloudron.io/networking/#trusted-ips configuration and not the app itself and not the WOPI setting of this specific app.
This post is also more a feature request with the example working on collabora. -
Hello @fbartels
@marcusquinn said in Update Documentation to warn of Cloudflare Proxy issues:
The fix is to add Cloudflare Trusted IPs to your Cloudron > Network > Configure Trusted IPs & Ranges, like so:
As I understood it, it is about the https://docs.cloudron.io/networking/#trusted-ips configuration and not the app itself and not the WOPI setting of this specific app.
This post is also more a feature request with the example working on collabora.@james @fbartels Correct, this is just for pre-populating and updating the values in Cloudron > Network > Configure Trusted IPs & Ranges, when "Enable proxying for new DNS records" is ticked on any app.
If you are using Cloudflare Proxying, you are implying you trust Cloudflare IPs to relay traffic.
The Nextcloud WOPI setting, although I think it could be pre-populated, is easier to do from following the documentation, if there's any concern why you wouldn't want that internal IP address pre-populated. Although, I can't think of why you would be concerned with an internal IP address being pre-populated in Nextcloud.
