DNS and VPN App
-
Ref. https://docs.cloudron.io/packages/adguard-home/#security
I'm struggling with this and like to only permit VPN clients to connect to adguard. Somehow I am messing this up.
Can somebody (you?) share their examples, please.

My current config is port 53 is open, no blocking of anything in adguard.
I can see one client connecting, which is the internal vpn server IP, and I cannot identify individual clients. I have two clients on the vpn for now.
I want to be able to identify these clients and permit them. I also want to be able to use the private dns option on android although that's not strictly required since I will be on the vpn or at home or office.
My concern is that since 53 is open, people may abuse the service.
I have tried setting the server's IP and the two VPN subnets to the allow list but I was unable to connect to the adguard for resolving dns queries from the vpn clients.
-
Ref. https://docs.cloudron.io/packages/adguard-home/#security
I'm struggling with this and like to only permit VPN clients to connect to adguard. Somehow I am messing this up.
Can somebody (you?) share their examples, please.

My current config is port 53 is open, no blocking of anything in adguard.
I can see one client connecting, which is the internal vpn server IP, and I cannot identify individual clients. I have two clients on the vpn for now.
I want to be able to identify these clients and permit them. I also want to be able to use the private dns option on android although that's not strictly required since I will be on the vpn or at home or office.
My concern is that since 53 is open, people may abuse the service.
I have tried setting the server's IP and the two VPN subnets to the allow list but I was unable to connect to the adguard for resolving dns queries from the vpn clients.
Hello @3246
@3246 said in DNS and VPN App:
My concern is that since 53 is open, people may abuse the service.
This is a valid concern and open DNS server are always used for DNS amplification attacks.
I am looking into it and will report back.
-
Hello @3246
Option 1 - Custom DNS no AdGuard DoT
DNS requests from the VPN Client will come over the
CLOUDRON_PROXY_IP=172.18.0.1
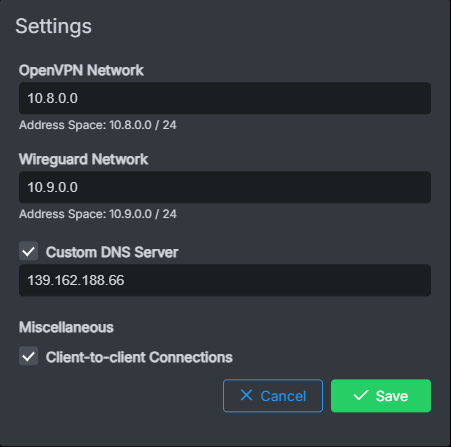
So if you whitelist172.18.0.1the requests should work when you use the IP address of your Cloudron Server as DNS IP.In the VPN Cloudron app you need to configure the custom DNS Server:
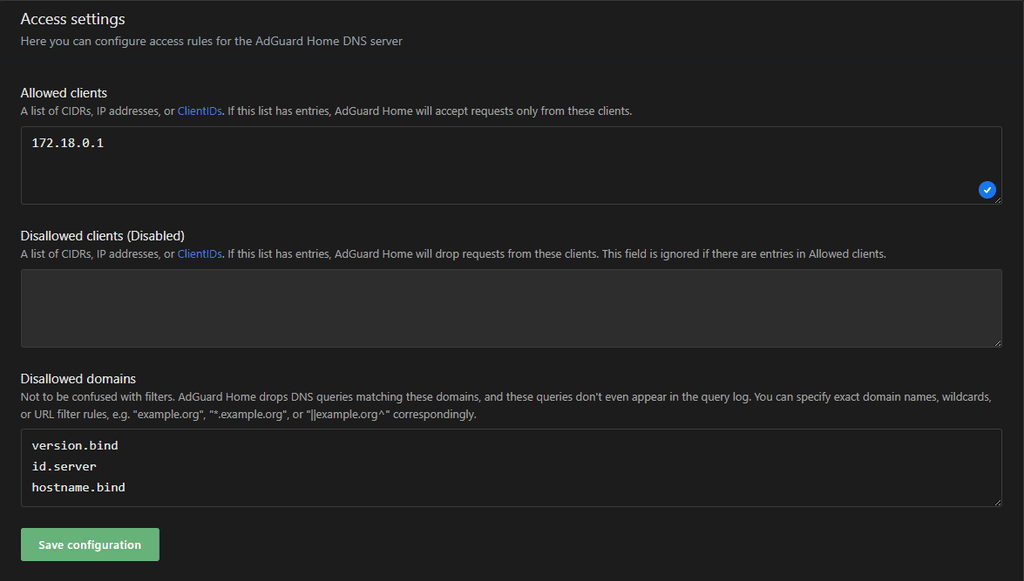
In AdGuard you need to whitelist the Cloudron Proxy IP:
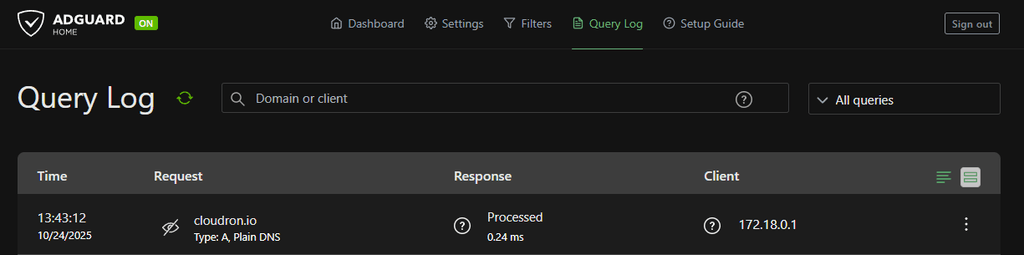
After saving the options and enabling (in my case) the Wireguard Client I can see the querrys in AdGuard:
Option 2 - Configure the VPN app to forward all to the AdGuard DNS Server no AdGuard DoT
From the Cloudron doc https://docs.cloudron.io/packages/vpn/#built-in-dns-server
Adding e.g.:
server=dns.cloudron.devAfter saving the file and restarting the app, all DNS queries are forwarded to
dns.cloudron.dev(The AdGuard App)
A custom DNS Server from Option 1 is not needed in the Client config.Possible side effect:
Doc:
This app has a built-in Dnsmasq DNS server which is pushed to clients. This DNS server allows resolution of connected clients using devicename.username.
This might not work when doing this.
Still the Cloudron Proxy IP needs to be whitelisted. See Option 1.
Using AdGuard DoT Clients and using them in the Whitelist
 Currently not possible in Cloudron 9 to use
Currently not possible in Cloudron 9 to use *.in domain aliases (fix coming)!It should be:
- configure your AdGuard app location to have the
*.dnsalias - add a client in AdGuard with the name
vpnc1(vpnc1is the name for the client, chose what ever you like) - whitelist the client
vpnc1in AdGuard under DNS Settings - configure the VPN Client use the
vpnc1.dns.cloudron.devdomain as the DNS Nameserver
But I did not get this working for a VPN Client.
This worked for e.g. Android Custom DNS Server.
But the VPN Client seems unable to resolve*.dns.cloudron.devordns.cloudron.dev.
Even when configuring this as a custom domain according to https://wiki.archlinux.org/title/Dnsmasq#Adding_a_custom_domainaddress=/dns.cloudron.dev/139.162.188.66 address=/*.dns.cloudron.dev/139.162.188.66Still not resolving.
I am currently looking deeper into this.
- configure your AdGuard app location to have the
-
 N nebulon has marked this topic as solved on
N nebulon has marked this topic as solved on
