TLS 1.0 vulnerability over 993 IMAPS
-
I recently ran some vulnerability tests via qualys against my cloudron setup and im showing a vulnerability with the 993 using tls 1.0. I thought 1.0 was disabled by cloudron? Is this a false alarm? IF not, is there an easy way to force tls 1.2 only?
-
I recently ran some vulnerability tests via qualys against my cloudron setup and im showing a vulnerability with the 993 using tls 1.0. I thought 1.0 was disabled by cloudron? Is this a false alarm? IF not, is there an easy way to force tls 1.2 only?
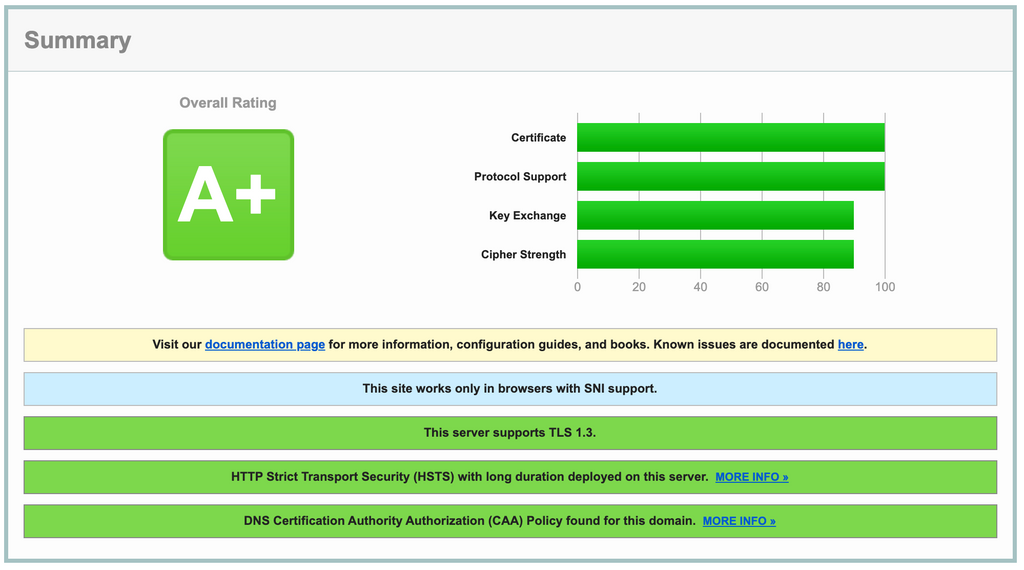
@mastadamus Curious, what URL did you use in the Qualsys test? I assume my.<domain>.<tld>? I just ran it on that URL for mine and got an A+.
-
@mastadamus Curious, what URL did you use in the Qualsys test? I assume my.<domain>.<tld>? I just ran it on that URL for mine and got an A+.

-
@d19dotca This tests the TLS of the HTTPS server. @Mastadamus is talking about the TLS of the IMAPS server.
-
I'm still not seeing anything about TLSv1.0 enabled on the mail domain either. @Mastadamus - are you able to explain how to reproduce this test so people can check out their own instances? So far I'm not able to reproduce.
-
I'm still not seeing anything about TLSv1.0 enabled on the mail domain either. @Mastadamus - are you able to explain how to reproduce this test so people can check out their own instances? So far I'm not able to reproduce.
@d19dotca I used the qualys vulnerability scanner community edition. You need to create an qualys account and use the actual vulnerability scanner. Also if you are running a firewall, you may have to unblock the qualys IP if it auto blocks it when it attempts various "scans' like checking for heartbleed etc. you can sign up for here https://www.qualys.com/community-edition/
-
I recently ran some vulnerability tests via qualys against my cloudron setup and im showing a vulnerability with the 993 using tls 1.0. I thought 1.0 was disabled by cloudron? Is this a false alarm? IF not, is there an easy way to force tls 1.2 only?
@mastadamus thanks for reporting! Initially, I thought this was a false alarm because tls1 connections don't work:
openssl s_client -connect my.example.com:993 -tls1 CONNECTED(00000003) 140461753824576:error:141E70BF:SSL routines:tls_construct_client_hello:no protocols available:../ssl/statem/statem_clnt.c:1112: --- no peer certificate available --- No client certificate CA names sent --- SSL handshake has read 0 bytes and written 7 bytes Verification: OK --- New, (NONE), Cipher is (NONE) Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE No ALPN negotiated Early data was not sent Verify return code: 0 (ok) ---Investigating further, I found that s_client can also fail if there is cipher match. And doing a "scan":
$ nmap --script ssl-enum-ciphers my.example.com -p 993 Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-20 09:50 PST Nmap scan report for my.example.com (45.55.2.141) Host is up (0.013s latency). PORT STATE SERVICE 993/tcp open imaps | ssl-enum-ciphers: | TLSv1.0: | ciphers: | TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_SEED_CBC_SHA (dh 1024) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp384r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp384r1) - A | TLS_RSA_WITH_AES_128_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_SEED_CBC_SHA (rsa 4096) - A | compressors: | NULL | cipher preference: client | warnings: | Key exchange (dh 1024) of lower strength than certificate key | TLSv1.1: | ciphers: | TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_SEED_CBC_SHA (dh 1024) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp384r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp384r1) - A | TLS_RSA_WITH_AES_128_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_SEED_CBC_SHA (rsa 4096) - A | compressors: | NULL | cipher preference: client | warnings: | Key exchange (dh 1024) of lower strength than certificate key | TLSv1.2: | ciphers: | TLS_DHE_RSA_WITH_AES_128_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 (dh 1024) - A | TLS_DHE_RSA_WITH_AES_128_CCM (dh 1024) - A | TLS_DHE_RSA_WITH_AES_128_CCM_8 (dh 1024) - A | TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (dh 1024) - A | TLS_DHE_RSA_WITH_AES_256_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 (dh 1024) - A | TLS_DHE_RSA_WITH_AES_256_CCM (dh 1024) - A | TLS_DHE_RSA_WITH_AES_256_CCM_8 (dh 1024) - A | TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (dh 1024) - A | TLS_DHE_RSA_WITH_ARIA_128_GCM_SHA256 (dh 1024) - A | TLS_DHE_RSA_WITH_ARIA_256_GCM_SHA384 (dh 1024) - A | TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA256 (dh 1024) - A | TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA (dh 1024) - A | TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA256 (dh 1024) - A | TLS_DHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (dh 1024) - A | TLS_DHE_RSA_WITH_SEED_CBC_SHA (dh 1024) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp384r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (secp384r1) - A | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp384r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp384r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (secp384r1) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp384r1) - A | TLS_ECDHE_RSA_WITH_ARIA_128_GCM_SHA256 (secp384r1) - A | TLS_ECDHE_RSA_WITH_ARIA_256_GCM_SHA384 (secp384r1) - A | TLS_ECDHE_RSA_WITH_CAMELLIA_128_CBC_SHA256 (secp384r1) - A | TLS_ECDHE_RSA_WITH_CAMELLIA_256_CBC_SHA384 (secp384r1) - A | TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (secp384r1) - A | TLS_RSA_WITH_AES_128_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 4096) - A | TLS_RSA_WITH_AES_128_CCM (rsa 4096) - A | TLS_RSA_WITH_AES_128_CCM_8 (rsa 4096) - A | TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 4096) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 4096) - A | TLS_RSA_WITH_AES_256_CCM (rsa 4096) - A | TLS_RSA_WITH_AES_256_CCM_8 (rsa 4096) - A | TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 4096) - A | TLS_RSA_WITH_ARIA_128_GCM_SHA256 (rsa 4096) - A | TLS_RSA_WITH_ARIA_256_GCM_SHA384 (rsa 4096) - A | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256 (rsa 4096) - A | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 4096) - A | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256 (rsa 4096) - A | TLS_RSA_WITH_SEED_CBC_SHA (rsa 4096) - A | compressors: | NULL | cipher preference: client | warnings: | Key exchange (dh 1024) of lower strength than certificate key |_ least strength: A Nmap done: 1 IP address (1 host up) scanned in 5.43 secondsSo, looks like something we have to disable in dovecot. We had disabled this in Haraka (the SMTP server) but not dovecot it seems. You can run nmap on port 587 to verify.
-
Ah nice, it seems the upgrade of the base image to bionic already fixed this since it comes with a newer dovecot.
$ nmap --script ssl-enum-ciphers my.example.com -p 993 Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-20 09:59 PST Nmap scan report for my.example.com (142.93.86.76) Host is up (0.014s latency). PORT STATE SERVICE 993/tcp open imaps | ssl-enum-ciphers: | TLSv1.2: | ciphers: | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_AES_128_CCM (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_AES_128_CCM_8 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CCM (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_AES_256_CCM_8 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_ARIA_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_ARIA_256_GCM_SHA384 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_CAMELLIA_128_CBC_SHA256 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_CAMELLIA_256_CBC_SHA384 (secp256r1) - A | TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (secp256r1) - A | compressors: | NULL | cipher preference: client | warnings: | Key exchange (secp256r1) of lower strength than certificate key |_ least strength: A -
Hey, glad I could be of service. Thanks for the quick replies and thankfully, its quickly remedied.
-
@girish sir
BTW, I apologize for not using your dedicated vulnerability reporting method.
- I just read up on it
- I really thought it was due to a settings misconfiguration part on my end and a false alarm as well. I was initially just looking for Guidance on fixing what I set up wrong. In the future if it's vulnerability concerned, I'll use your reporting mechanisms.
-
@girish sir
BTW, I apologize for not using your dedicated vulnerability reporting method.
- I just read up on it
- I really thought it was due to a settings misconfiguration part on my end and a false alarm as well. I was initially just looking for Guidance on fixing what I set up wrong. In the future if it's vulnerability concerned, I'll use your reporting mechanisms.
-
@mastadamus no problem! atleast, this is not a severe security issue and we have a fix coming already.
@girish agreed.
