Nextcloud Admin Settings > Security & setup warnings
-
Anyone else getting this here?
https://cloud.example.com/settings/admin/overviewSecurity & setup warnings
It's important for the security and performance of your instance that everything is configured correctly. To help you with that we are doing some automatic checks. Please see the linked documentation for more information.There are some warnings regarding your setup.
Your web server is not properly set up to resolve "/.well-known/webfinger". Further information can be found in the documentation .
.
Your web server is not properly set up to resolve "/.well-known/nodeinfo". Further information can be found in the documentation .
.
Please double check the installation guides , and check for any errors or warnings in the log.
, and check for any errors or warnings in the log.Check the security of your Nextcloud over our security scan
 .
. -
Anyone else getting this here?
https://cloud.example.com/settings/admin/overviewSecurity & setup warnings
It's important for the security and performance of your instance that everything is configured correctly. To help you with that we are doing some automatic checks. Please see the linked documentation for more information.There are some warnings regarding your setup.
Your web server is not properly set up to resolve "/.well-known/webfinger". Further information can be found in the documentation .
.
Your web server is not properly set up to resolve "/.well-known/nodeinfo". Further information can be found in the documentation .
.
Please double check the installation guides , and check for any errors or warnings in the log.
, and check for any errors or warnings in the log.Check the security of your Nextcloud over our security scan
 .
.@marcusquinn said in Nextcloud Admin Settings > Security & setup warnings:
Your web server is not properly set up to resolve "/.well-known/webfinger
That first one is because Nextcloud wants to be in the #fediverse world with Mastodon. Not at all required
The second one actually might be useful...but not sure how. @girish once upon a time we landed some well-knowns in Nextcloud I thought, did they drop off?
-
Anyone else getting this here?
https://cloud.example.com/settings/admin/overviewSecurity & setup warnings
It's important for the security and performance of your instance that everything is configured correctly. To help you with that we are doing some automatic checks. Please see the linked documentation for more information.There are some warnings regarding your setup.
Your web server is not properly set up to resolve "/.well-known/webfinger". Further information can be found in the documentation .
.
Your web server is not properly set up to resolve "/.well-known/nodeinfo". Further information can be found in the documentation .
.
Please double check the installation guides , and check for any errors or warnings in the log.
, and check for any errors or warnings in the log.Check the security of your Nextcloud over our security scan
 .
.@marcusquinn said in Nextcloud Admin Settings > Security & setup warnings:
Anyone else getting this here?
https://cloud.example.com/settings/admin/overview
Security & setup warnings
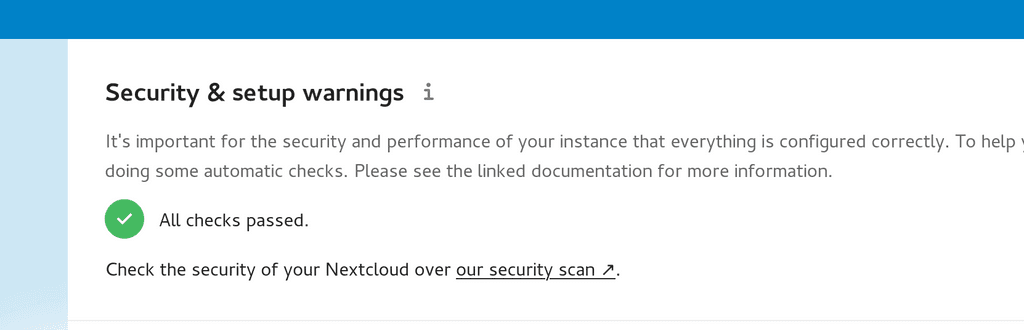
It's important for the security and performance of your instance that everything is configured correctly. To help you with that we are doing some automatic checks. Please see the linked documentation for more information.
There are some warnings regarding your setup.
Your web server is not properly set up to resolve "/.well-known/webfinger". Further information can be found in the documentation .
Your web server is not properly set up to resolve "/.well-known/nodeinfo". Further information can be found in the documentation .
Please double check the installation guides , and check for any errors or warnings in the log.
Check the security of your Nextcloud over our security scan .yep
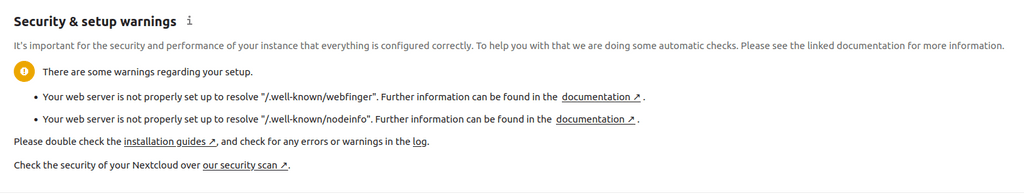
But clicking that last security scan link gives an A+
However, clicking on the first two documentation links take me to:
Which informs me that the .well-known stuff is also needed to get CardDAV and CalDAV to work properly, so does sound like this is something to look into...(although afaict my CardDAV and CalDAV are working fine, perhaps they wouldn't if I was trying to connect with different clients)
From the link above:
If you are running NGINX, make sure location = /.well-known/carddav { and location = /.well-known/caldav { are properly configured as described in NGINX configuration, adapt to use a subfolder if necessary.
Now change the URL in the client settings to just use:
instead of e.g.
https://example.com/nextcloud/remote.php/dav/principals/username.
Sounds like maybe this needs adding to the package?
# Make a regex exception for `/.well-known` so that clients can still # access it despite the existence of the regex rule # `location ~ /(\.|autotest|...)` which would otherwise handle requests # for `/.well-known`. location ^~ /.well-known { # The rules in this block are an adaptation of the rules # in `.htaccess` that concern `/.well-known`. location = /.well-known/carddav { return 301 /remote.php/dav/; } location = /.well-known/caldav { return 301 /remote.php/dav/; } location /.well-known/acme-challenge { try_files $uri $uri/ =404; } location /.well-known/pki-validation { try_files $uri $uri/ =404; } # Let Nextcloud's API for `/.well-known` URIs handle all other # requests by passing them to the front-end controller. return 301 /index.php$request_uri; } -
@marcusquinn said in Nextcloud Admin Settings > Security & setup warnings:
Anyone else getting this here?
https://cloud.example.com/settings/admin/overview
Security & setup warnings
It's important for the security and performance of your instance that everything is configured correctly. To help you with that we are doing some automatic checks. Please see the linked documentation for more information.
There are some warnings regarding your setup.
Your web server is not properly set up to resolve "/.well-known/webfinger". Further information can be found in the documentation .
Your web server is not properly set up to resolve "/.well-known/nodeinfo". Further information can be found in the documentation .
Please double check the installation guides , and check for any errors or warnings in the log.
Check the security of your Nextcloud over our security scan .yep

But clicking that last security scan link gives an A+

However, clicking on the first two documentation links take me to:
Which informs me that the .well-known stuff is also needed to get CardDAV and CalDAV to work properly, so does sound like this is something to look into...(although afaict my CardDAV and CalDAV are working fine, perhaps they wouldn't if I was trying to connect with different clients)
From the link above:
If you are running NGINX, make sure location = /.well-known/carddav { and location = /.well-known/caldav { are properly configured as described in NGINX configuration, adapt to use a subfolder if necessary.
Now change the URL in the client settings to just use:
instead of e.g.
https://example.com/nextcloud/remote.php/dav/principals/username.
Sounds like maybe this needs adding to the package?
# Make a regex exception for `/.well-known` so that clients can still # access it despite the existence of the regex rule # `location ~ /(\.|autotest|...)` which would otherwise handle requests # for `/.well-known`. location ^~ /.well-known { # The rules in this block are an adaptation of the rules # in `.htaccess` that concern `/.well-known`. location = /.well-known/carddav { return 301 /remote.php/dav/; } location = /.well-known/caldav { return 301 /remote.php/dav/; } location /.well-known/acme-challenge { try_files $uri $uri/ =404; } location /.well-known/pki-validation { try_files $uri $uri/ =404; } # Let Nextcloud's API for `/.well-known` URIs handle all other # requests by passing them to the front-end controller. return 301 /index.php$request_uri; } -
We sorted this issue by amending
/app/data/htaccess(/app/code/.htaccess) as follows:<IfModule mod_rewrite.c> RewriteEngine on RewriteCond %{HTTP_USER_AGENT} DavClnt RewriteRule ^$ /remote.php/webdav/ [L,R=302] RewriteRule .* - [env=HTTP_AUTHORIZATION:%{HTTP:Authorization}] RewriteRule ^\.well-known/host-meta /public.php?service=host-meta [QSA,L] RewriteRule ^\.well-known/host-meta\.json /public.php?service=host-meta-json [QSA,L] - RewriteRule ^\.well-known/webfinger /public.php?service=webfinger [QSA,L] - RewriteRule ^\.well-known/nodeinfo /public.php?service=nodeinfo [QSA,L] + RewriteRule ^/\.well-known/webfinger /index.php/.well-known/webfinger [R=301,L] + RewriteRule ^/\.well-known/nodeinfo /index.php/.well-known/nodeinfo [R=301,L] RewriteRule ^\.well-known/carddav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^\.well-known/caldav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^remote/(.*) remote.php [QSA,L] RewriteRule ^(?:build|tests|config|lib|3rdparty|templates)/.* - [R=404,L] RewriteCond %{REQUEST_URI} !^/\.well-known/(acme-challenge|pki-validation)/.* RewriteRule ^(?:\.|autotest|occ|issue|indie|db_|console).* - [R=404,L] </IfModule> -
@jdaviescoates have you tried to curl those paths? As far as I can tell, my Nextcloud instance does respond just fine on those regarding card/cal dav.
@nebulon said in Nextcloud Admin Settings > Security & setup warnings:
@jdaviescoates have you tried to curl those paths?
Nope.
But sounds like perhaps something like the .htaccess code @vladimir-d shared should be added to the package?
-
@nebulon said in Nextcloud Admin Settings > Security & setup warnings:
@jdaviescoates have you tried to curl those paths?
Nope.
But sounds like perhaps something like the .htaccess code @vladimir-d shared should be added to the package?
@jdaviescoates one issue with this is, that this file may have been changed by the user as well as it gets rewritten by nextcloud if needed, like from a plugin. So I am not sure what a solid migration path would be.
For a start though, I don't quite understand what the expected paths should be and if that is the correct place to patch those up. At least my instance as well as newly installed ones do not face the issue while not having those htaccess changes. So something is still missing in the puzzle.
-
My
/app/data/htaccessis a bit different:<IfModule mod_rewrite.c> RewriteEngine on RewriteCond %{HTTP_USER_AGENT} DavClnt RewriteRule ^$ /remote.php/webdav/ [L,R=302] RewriteRule .* - [env=HTTP_AUTHORIZATION:%{HTTP:Authorization}] RewriteRule ^\.well-known/host-meta /public.php?service=host-meta [QSA,L] RewriteRule ^\.well-known/host-meta\.json /public.php?service=host-meta-json [QSA,L] RewriteRule ^\.well-known/carddav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^\.well-known/caldav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^remote/(.*) remote.php [QSA,L] RewriteRule ^(?:build|tests|config|lib|3rdparty|templates)/.* - [R=404,L] RewriteCond %{REQUEST_URI} !^/.well-known/(acme-challenge|pki-validation)/.* RewriteRule ^(?:\.|autotest|occ|issue|indie|db_|console).* - [R=404,L] </IfModule> -
just a random guess, but perhaps you aren't using Nextcloud Talk @girish ?
I do and pretty sure @marcusquinn does too.
-
My
/app/data/htaccessis a bit different:<IfModule mod_rewrite.c> RewriteEngine on RewriteCond %{HTTP_USER_AGENT} DavClnt RewriteRule ^$ /remote.php/webdav/ [L,R=302] RewriteRule .* - [env=HTTP_AUTHORIZATION:%{HTTP:Authorization}] RewriteRule ^\.well-known/host-meta /public.php?service=host-meta [QSA,L] RewriteRule ^\.well-known/host-meta\.json /public.php?service=host-meta-json [QSA,L] RewriteRule ^\.well-known/carddav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^\.well-known/caldav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^remote/(.*) remote.php [QSA,L] RewriteRule ^(?:build|tests|config|lib|3rdparty|templates)/.* - [R=404,L] RewriteCond %{REQUEST_URI} !^/.well-known/(acme-challenge|pki-validation)/.* RewriteRule ^(?:\.|autotest|occ|issue|indie|db_|console).* - [R=404,L] </IfModule>@girish Looks like you done have those lines to edit, so maybe they are put there by an add-on:
- RewriteRule ^\.well-known/webfinger /public.php?service=webfinger [QSA,L] - RewriteRule ^\.well-known/nodeinfo /public.php?service=nodeinfo [QSA,L] -
just a random guess, but perhaps you aren't using Nextcloud Talk @girish ?
I do and pretty sure @marcusquinn does too.
@jdaviescoates We are. Recommend it too, much simpler and more integrated than Rocket.Chat. Call quality is great with it too.
-
just a random guess, but perhaps you aren't using Nextcloud Talk @girish ?
I do and pretty sure @marcusquinn does too.
@jdaviescoates said in Nextcloud Admin Settings > Security & setup warnings:
just a random guess, but perhaps you aren't using Nextcloud Talk @girish ?
Indeed, we don't. We use Jitsi
 So, maybe some migration within nextcloud is not patching htaccess correctly.
So, maybe some migration within nextcloud is not patching htaccess correctly. -
@jdaviescoates We are. Recommend it too, much simpler and more integrated than Rocket.Chat. Call quality is great with it too.
@marcusquinn said in Nextcloud Admin Settings > Security & setup warnings:
Call quality is great with it too.
Yeah generally fine with 2-3 people in my experience. Haven't really had the opportunity or need to try it with large groups yet.
But, out of interest, have you got the Talk High Performance Back End set-up too?
-
@marcusquinn said in Nextcloud Admin Settings > Security & setup warnings:
Call quality is great with it too.
Yeah generally fine with 2-3 people in my experience. Haven't really had the opportunity or need to try it with large groups yet.
But, out of interest, have you got the Talk High Performance Back End set-up too?
@jdaviescoates Yes, although we don't use it for large meetings, just 1-2-1 calls and chat. It needs a small patch for over 100 users to allow for status updates, but otherwise a very happy solution that users like for its just-works simplicity. It's really become a self-hosted alternative to Signal. Recommended!
-
We sorted this issue by amending
/app/data/htaccess(/app/code/.htaccess) as follows:<IfModule mod_rewrite.c> RewriteEngine on RewriteCond %{HTTP_USER_AGENT} DavClnt RewriteRule ^$ /remote.php/webdav/ [L,R=302] RewriteRule .* - [env=HTTP_AUTHORIZATION:%{HTTP:Authorization}] RewriteRule ^\.well-known/host-meta /public.php?service=host-meta [QSA,L] RewriteRule ^\.well-known/host-meta\.json /public.php?service=host-meta-json [QSA,L] - RewriteRule ^\.well-known/webfinger /public.php?service=webfinger [QSA,L] - RewriteRule ^\.well-known/nodeinfo /public.php?service=nodeinfo [QSA,L] + RewriteRule ^/\.well-known/webfinger /index.php/.well-known/webfinger [R=301,L] + RewriteRule ^/\.well-known/nodeinfo /index.php/.well-known/nodeinfo [R=301,L] RewriteRule ^\.well-known/carddav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^\.well-known/caldav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^remote/(.*) remote.php [QSA,L] RewriteRule ^(?:build|tests|config|lib|3rdparty|templates)/.* - [R=404,L] RewriteCond %{REQUEST_URI} !^/\.well-known/(acme-challenge|pki-validation)/.* RewriteRule ^(?:\.|autotest|occ|issue|indie|db_|console).* - [R=404,L] </IfModule>@vladimir-d said in Nextcloud Admin Settings > Security & setup warnings:
We sorted this issue by amending
/app/data/htaccess(/app/code/.htaccess) as follows:<IfModule mod_rewrite.c> RewriteEngine on RewriteCond %{HTTP_USER_AGENT} DavClnt RewriteRule ^$ /remote.php/webdav/ [L,R=302] RewriteRule .* - [env=HTTP_AUTHORIZATION:%{HTTP:Authorization}] RewriteRule ^\.well-known/host-meta /public.php?service=host-meta [QSA,L] RewriteRule ^\.well-known/host-meta\.json /public.php?service=host-meta-json [QSA,L] - RewriteRule ^\.well-known/webfinger /public.php?service=webfinger [QSA,L] - RewriteRule ^\.well-known/nodeinfo /public.php?service=nodeinfo [QSA,L] + RewriteRule ^/\.well-known/webfinger /index.php/.well-known/webfinger [R=301,L] + RewriteRule ^/\.well-known/nodeinfo /index.php/.well-known/nodeinfo [R=301,L] RewriteRule ^\.well-known/carddav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^\.well-known/caldav https://%{HTTP_HOST}/remote.php/dav/ [R=301,L] RewriteRule ^remote/(.*) remote.php [QSA,L] RewriteRule ^(?:build|tests|config|lib|3rdparty|templates)/.* - [R=404,L] RewriteCond %{REQUEST_URI} !^/\.well-known/(acme-challenge|pki-validation)/.* RewriteRule ^(?:\.|autotest|occ|issue|indie|db_|console).* - [R=404,L] </IfModule>That worked for me too.
I wonder what caused it though. I have another install of Nextcloud that also has Nextcloud Talk installed and that htaccess has no mention of webfinger, so it must be something else