TLS Cert exporter to enable up-front Firewall deep-packet-inspection
-
Hello Cloudron-Team,
It would be great to have a feature that allows for the export of the Lets!Encrypt Certificates, sounds strange but below is why this would be great.
Feature Description:
Have an API-Endpoint or Workflow that can trigger a Webhook or direct export of the Let’s Encrypt/Certbot Certificates to remote Systems especially Firewalls.Use Case:
When using Cloudron in networks of industrial clients they usually want to secure ALL traffic through a central firewall. To allow for the deep-packet-inspection capabilities and the corresponding protection level the firewall needs to have access to the certificates used for the TLS-channels, else it can only see that there is encrypted traffic happening. Since Let's Encrypt/Certbot is cyclically renewing the certificates an automated way/workflow of "informing" upstream systems of new certificates would reduce manual efforts.Expected Behavior:
When a certificate is initially issued OR when it is renewed by Certbot as a post-processing step there should be the possibility to configure a Webhook that recieves this certificate along some meta-data on the application for use in upstream systems, mainly Firewalls.Is there some way to achieve this at this point already or would this be a new feature?
Best regards and keep up the good work Cloudron and the Comunity are really great,
Jan Macenka -
Hello Cloudron-Team,
It would be great to have a feature that allows for the export of the Lets!Encrypt Certificates, sounds strange but below is why this would be great.
Feature Description:
Have an API-Endpoint or Workflow that can trigger a Webhook or direct export of the Let’s Encrypt/Certbot Certificates to remote Systems especially Firewalls.Use Case:
When using Cloudron in networks of industrial clients they usually want to secure ALL traffic through a central firewall. To allow for the deep-packet-inspection capabilities and the corresponding protection level the firewall needs to have access to the certificates used for the TLS-channels, else it can only see that there is encrypted traffic happening. Since Let's Encrypt/Certbot is cyclically renewing the certificates an automated way/workflow of "informing" upstream systems of new certificates would reduce manual efforts.Expected Behavior:
When a certificate is initially issued OR when it is renewed by Certbot as a post-processing step there should be the possibility to configure a Webhook that recieves this certificate along some meta-data on the application for use in upstream systems, mainly Firewalls.Is there some way to achieve this at this point already or would this be a new feature?
Best regards and keep up the good work Cloudron and the Comunity are really great,
Jan Macenka@Jan-Macenka said in TLS Cert exporter to enable up-front Firewall deep-packet-inspection:
Is there some way to achieve this at this point already or would this be a new feature?
There is no feature like that right now.
You can always provide Cloudron with a custom certificate which then can also be used by the firewall:
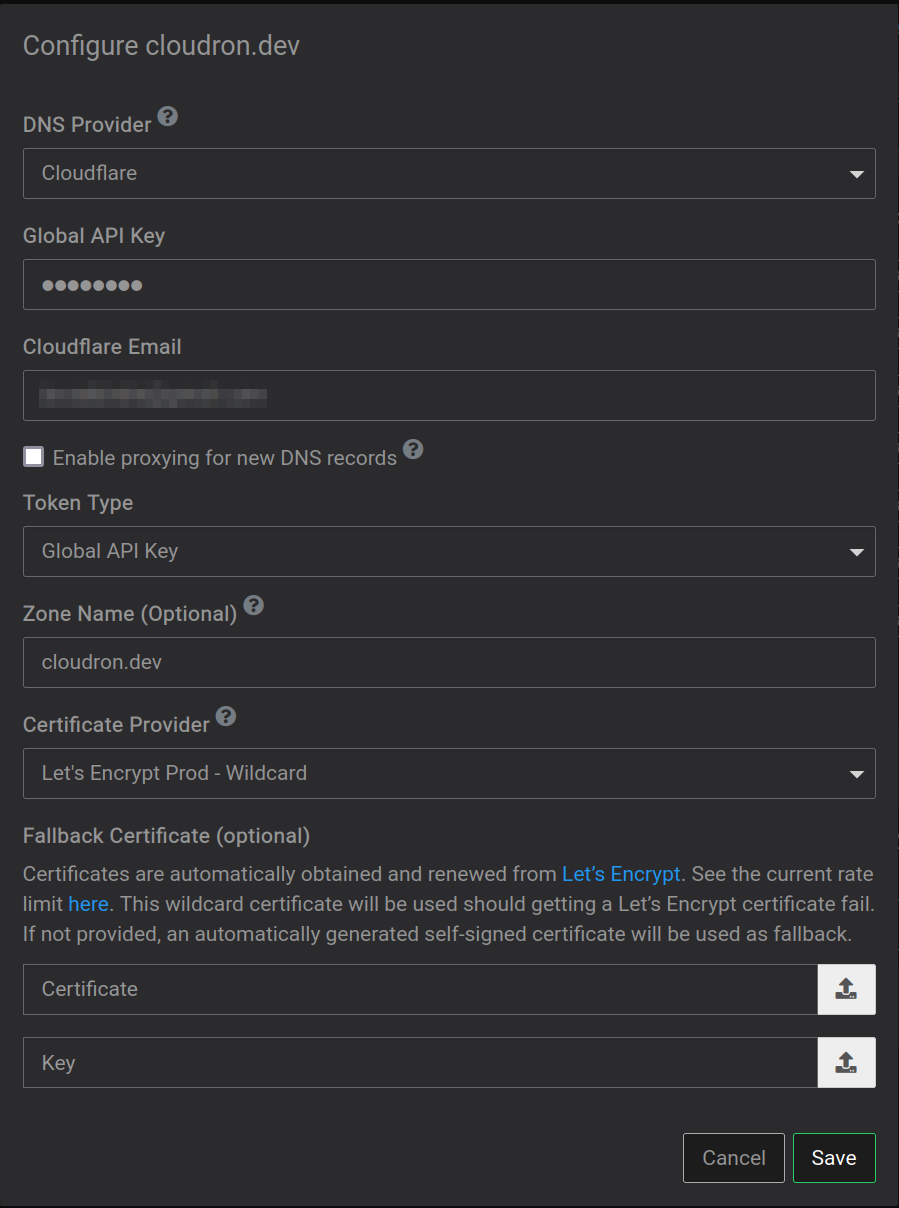
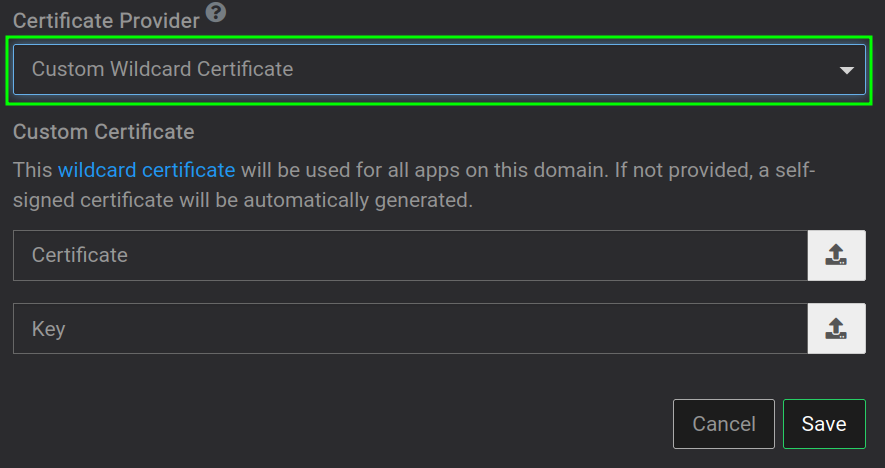
Also all certificates can be accessed freely under
/home/yellowtent/platformdata/nginx/cert/ -
@Jan-Macenka said in TLS Cert exporter to enable up-front Firewall deep-packet-inspection:
Is there some way to achieve this at this point already or would this be a new feature?
There is no feature like that right now.
You can always provide Cloudron with a custom certificate which then can also be used by the firewall:


Also all certificates can be accessed freely under
/home/yellowtent/platformdata/nginx/cert/@BrutalBirdie said in TLS Cert exporter to enable up-front Firewall deep-packet-inspection:
Also all certificates can be accessed freely under /home/yellowtent/platformdata/nginx/cert/
As a heads up, those certs change every 2 months (LE certs have only 3 month validity).
-
@BrutalBirdie said in TLS Cert exporter to enable up-front Firewall deep-packet-inspection:
Also all certificates can be accessed freely under /home/yellowtent/platformdata/nginx/cert/
As a heads up, those certs change every 2 months (LE certs have only 3 month validity).
@BrutalBirdie thanks for bringing this up. I know about this but actually in my Threat model a compromized or leaked certificate plays an important role. Hence the rather short TTL of only 2 month is a benefit or actually a required feature (at least for me).
@girish thats exactly the point, these change and I need to notify "other systems" of the current certificates.
To be honest, I am looking for something that matches the role of cert-manager in a Kubernetes-Cluster with the intention to integrate it with HashiCorp Vault (which you already have enabled as a cloudron-app)

One solution could be: Creating the certificates though another tool and uploading it to the cloudron-instance and other systems. If I uploaded a new cert to
/home/yellowtent/platformdata/nginx/cert/do I need to trigger any "regeneration" of sub-domain certs e.g. though the API or will all Nginx-instances just use this cert "as-is" for all apps? -
@BrutalBirdie thanks for bringing this up. I know about this but actually in my Threat model a compromized or leaked certificate plays an important role. Hence the rather short TTL of only 2 month is a benefit or actually a required feature (at least for me).
@girish thats exactly the point, these change and I need to notify "other systems" of the current certificates.
To be honest, I am looking for something that matches the role of cert-manager in a Kubernetes-Cluster with the intention to integrate it with HashiCorp Vault (which you already have enabled as a cloudron-app)

One solution could be: Creating the certificates though another tool and uploading it to the cloudron-instance and other systems. If I uploaded a new cert to
/home/yellowtent/platformdata/nginx/cert/do I need to trigger any "regeneration" of sub-domain certs e.g. though the API or will all Nginx-instances just use this cert "as-is" for all apps?@Jan-Macenka The easiest approach is actually to just purchase a wildcard cert. I have used https://www.garrisonhost.com/ssl-certificates/alphassl in the past a lot. It's under 50 bucks. But you can get it from 2 years even . And then set the cert in the Domains view and you are set.
-
@Jan-Macenka The easiest approach is actually to just purchase a wildcard cert. I have used https://www.garrisonhost.com/ssl-certificates/alphassl in the past a lot. It's under 50 bucks. But you can get it from 2 years even . And then set the cert in the Domains view and you are set.
@girish thanks for the suggestion. I know about this approach but my goals are:
- Have short-lived certificates with a well established and protected renewal-mechanism in order to minimize potential damage (exposure time) from leaked certificates (threat model)
- Have a way to bring automation into the stack to comply with some corporate policies so certificates can be "made known" to other systems such as firewalls (need for automation to reduce manual efforts)
For now I'll try to generate the certs in an external Certbot-workflow and distribute them to Cloudron just like other endpoints. This will outsource the renewal process from these systems.
-
@girish thanks for the suggestion. I know about this approach but my goals are:
- Have short-lived certificates with a well established and protected renewal-mechanism in order to minimize potential damage (exposure time) from leaked certificates (threat model)
- Have a way to bring automation into the stack to comply with some corporate policies so certificates can be "made known" to other systems such as firewalls (need for automation to reduce manual efforts)
For now I'll try to generate the certs in an external Certbot-workflow and distribute them to Cloudron just like other endpoints. This will outsource the renewal process from these systems.
@Jan-Macenka you can have a single host or docker container running, for example, acme.sh with DNS challenge to always renew the cert or certs for multiple domains and then sync it automatically to other instances.
I am still in the progress of switching all my servers from certbot to acme.sh since certbot is only supported via snap and the apt version is not getting updated.
The apt version cant even request ed25519 certs. -
@Jan-Macenka you can have a single host or docker container running, for example, acme.sh with DNS challenge to always renew the cert or certs for multiple domains and then sync it automatically to other instances.
I am still in the progress of switching all my servers from certbot to acme.sh since certbot is only supported via snap and the apt version is not getting updated.
The apt version cant even request ed25519 certs.@BrutalBirdie said in TLS Cert exporter to enable up-front Firewall deep-packet-inspection:
Thanks for the hint. There is an ansible-module for this which is exactly how I will try to approach this.
If I found a workable solution, I'll come back to the forum and give you an update. Should I forget and someone else is interested, feel free to prompt me
Thanks for your quick responses and
 cudos
cudos  to the great Coudron forum and staff, its really a joy to see how good your support is!
to the great Coudron forum and staff, its really a joy to see how good your support is! -
@BrutalBirdie said in TLS Cert exporter to enable up-front Firewall deep-packet-inspection:
Thanks for the hint. There is an ansible-module for this which is exactly how I will try to approach this.
If I found a workable solution, I'll come back to the forum and give you an update. Should I forget and someone else is interested, feel free to prompt me
Thanks for your quick responses and
 cudos
cudos  to the great Coudron forum and staff, its really a joy to see how good your support is!
to the great Coudron forum and staff, its really a joy to see how good your support is!@Jan-Macenka
Ohhhh! Thanks for sharing! I also use Ansible and was not aware of an existing Ansible Module for acme!
I will have to take a look at that! -
@BrutalBirdie said in TLS Cert exporter to enable up-front Firewall deep-packet-inspection:
Thanks for the hint. There is an ansible-module for this which is exactly how I will try to approach this.
If I found a workable solution, I'll come back to the forum and give you an update. Should I forget and someone else is interested, feel free to prompt me
Thanks for your quick responses and
 cudos
cudos  to the great Coudron forum and staff, its really a joy to see how good your support is!
to the great Coudron forum and staff, its really a joy to see how good your support is!@Jan-Macenka as a follow up.
This module is for the acme protocol: https://datatracker.ietf.org/doc/html/rfc8555And if I understand this module and everything correctly this will not auto renew on the system it self.
So you will have to run the ansible deployment again to renew the certs.For the BigBlueButton Role I maintain I've written a task for installing acme.sh to manage the cert of the deployment.
I also turned this into a standalone Role for my company but not published it since its such a little role/task.
Maybe this can help you even further.
ps: big thanks for the beer
 @Jan-Macenka
@Jan-Macenka -
 B BrutalBirdie referenced this topic on
B BrutalBirdie referenced this topic on
