Abuse report received
-
So now Hetzner are saying there is evidence of a netscan :
Netscan detected from host 88.99.xxx.xxx
Tue Jul 4 15:44:19 2023 TCP 88.99.xxx.xxx 54602 => 1.2.3.4 80
Tue Jul 4 15:44:32 2023 TCP 88.99.xxx.xxx 54602 => 1.2.3.4 80
Tue Jul 4 15:43:30 2023 TCP 88.99.xxx.xxx 58742 => 6.6.6.6 80
Tue Jul 4 15:45:04 2023 TCP 88.99.xxx.xxx 60244 => 10.0.0.10 80
Tue Jul 4 15:43:29 2023 TCP 88.99.xxx.xxx 56196 => 10.0.0.23 80
Tue Jul 4 15:43:33 2023 TCP 88.99.xxx.xxx 56196 => 10.0.0.23 80
etc.I have no knowledge of what this might be.
Other than installing a couple of apps this morning from the app store, I cannot think of any change on the server.Confused.
@timconsidine said in Abuse report received:
So now Hetzner are saying there is evidence of a netscan :
Netscan detected from host 88.99.xx.xx
Tue Jul 4 15:44:19 2023 TCP 88.99.xx.xx 54602 => 1.2.3.4 80
Tue Jul 4 15:44:32 2023 TCP 88.99.xx.xx 54602 => 1.2.3.4 80
Tue Jul 4 15:43:30 2023 TCP 88.99.xx.xx 58742 => 6.6.6.6 80
Tue Jul 4 15:45:04 2023 TCP 88.99.xx.xx 60244 => 10.0.0.10 80
Tue Jul 4 15:43:29 2023 TCP 88.99.xx.xx 56196 => 10.0.0.23 80
Tue Jul 4 15:43:33 2023 TCP 88.99.xx.xx 56196 => 10.0.0.23 80I have no knowledge of what this might be.
Other than installing a couple of apps this morning from the app store, I cannot think of any change on the server.Confused.
Just for clarification: Are the IP addresses after "=>" the ones that were the targets according to Hetzner? If so these IP addresses sound weird to me. Btw maybe you forgot to redact your IP on the left side if it's your server IP.
-
@timconsidine said in Abuse report received:
So now Hetzner are saying there is evidence of a netscan :
Netscan detected from host 88.99.xx.xx
Tue Jul 4 15:44:19 2023 TCP 88.99.xx.xx 54602 => 1.2.3.4 80
Tue Jul 4 15:44:32 2023 TCP 88.99.xx.xx 54602 => 1.2.3.4 80
Tue Jul 4 15:43:30 2023 TCP 88.99.xx.xx 58742 => 6.6.6.6 80
Tue Jul 4 15:45:04 2023 TCP 88.99.xx.xx 60244 => 10.0.0.10 80
Tue Jul 4 15:43:29 2023 TCP 88.99.xx.xx 56196 => 10.0.0.23 80
Tue Jul 4 15:43:33 2023 TCP 88.99.xx.xx 56196 => 10.0.0.23 80I have no knowledge of what this might be.
Other than installing a couple of apps this morning from the app store, I cannot think of any change on the server.Confused.
Just for clarification: Are the IP addresses after "=>" the ones that were the targets according to Hetzner? If so these IP addresses sound weird to me. Btw maybe you forgot to redact your IP on the left side if it's your server IP.
@warg yes it is the right hand ones after
=>which are the targets
and yes, I had problems copy/pasting log entries to be on separate lines, and forgot to redact my address.
Thanks for the alert.
And now done.There is one line (near beginning) in your quoted message where it is unredacted, but I can't edit your post. Can you do that? I'd be very grateful.
I think the weirdness of the target addresses is an aspect of whatever was doing a netscan. But I'm no expert on this.
-
@warg yes it is the right hand ones after
=>which are the targets
and yes, I had problems copy/pasting log entries to be on separate lines, and forgot to redact my address.
Thanks for the alert.
And now done.There is one line (near beginning) in your quoted message where it is unredacted, but I can't edit your post. Can you do that? I'd be very grateful.
I think the weirdness of the target addresses is an aspect of whatever was doing a netscan. But I'm no expert on this.
@timconsidine said in Abuse report received:
There is one line (near beginning) in your quoted message where it is unredacted, but I can't edit your post. Can you do that? I'd be very grateful.
Sorry, I didn't see that when I redacted them . . . fixed! (A bit pitty that you can see previous revisions of a post as a non-admin in this forum software, I think).
@timconsidine said in Abuse report received:
I think the weirdness of the target addresses is an aspect of whatever was doing a netscan. But I'm no expert on this.
I could imagine some docker or Cloudron voodoo does have some broken checks that check on local network IPs by accident and thus triggering it by accident? Not sure.
-
Update : Hetzner now say issue closed.
Thanks to responders for their advice and patience.
I did 2 things :
- uninstalled an instance of StirlingPDF (simply because it was the last installed)
- uninstalled an instance of Wordpress Developer which has been stopped for months, but was re-started today because a user wanted to update it to latest version before using it.
My suspicion :
- user installed something in Wordpress
- Wordpress is dodgy without tons of maintenance.
I know some people love it, but I hate Wordpress almost as much as I hate <insert favourite satan>.
Anyway, it's gone now.
Awaiting Hetzner confirmation that all cool.But @staff : should there not be something in Cloudron to be able to do effective server malware scanning ?
Or some kind of tripwire-type utility ? -
@timconsidine said in Abuse report received:
There is one line (near beginning) in your quoted message where it is unredacted, but I can't edit your post. Can you do that? I'd be very grateful.
Sorry, I didn't see that when I redacted them . . . fixed! (A bit pitty that you can see previous revisions of a post as a non-admin in this forum software, I think).
@timconsidine said in Abuse report received:
I think the weirdness of the target addresses is an aspect of whatever was doing a netscan. But I'm no expert on this.
I could imagine some docker or Cloudron voodoo does have some broken checks that check on local network IPs by accident and thus triggering it by accident? Not sure.
@warg said in Abuse report received:
(A bit pitty that you can see previous revisions of a post as a non-admin in this forum software, I think).
Yep !
@warg said in Abuse report received:
I could imagine some docker or Cloudron voodoo does have some broken checks that check on local network IPs by accident and thus triggering it by accident? Not sure.
Maybe.
Certainly interested in what platform (server) checks can be implemented to prevent this, or detect it. -
Update : Hetzner now say issue closed.
Thanks to responders for their advice and patience.
I did 2 things :
- uninstalled an instance of StirlingPDF (simply because it was the last installed)
- uninstalled an instance of Wordpress Developer which has been stopped for months, but was re-started today because a user wanted to update it to latest version before using it.
My suspicion :
- user installed something in Wordpress
- Wordpress is dodgy without tons of maintenance.
I know some people love it, but I hate Wordpress almost as much as I hate <insert favourite satan>.
Anyway, it's gone now.
Awaiting Hetzner confirmation that all cool.But @staff : should there not be something in Cloudron to be able to do effective server malware scanning ?
Or some kind of tripwire-type utility ?@timconsidine said in Abuse report received:
I know some people love it, but I hate Wordpress almost as much as I hate <insert favourite satan>.
I wouldn't be surprised if a WordPress instance caused it. WordPress is a security nightmare and if it's unmaintained, it's even more. Sadly popularity of a software doesn't requires a proper software quality . . .
I'm curious as well. If Cloudron is deciding about the whole environment it runs on, it must provide proper tools. Furthermore it also needs ways to include security or monitoring tools that are common but not supported officially. Otherwise we have in general some kind of compliance or security issue in general someday.
-
@timconsidine I'm glad the issue is resolved, or should I say, isn't a threat to the continuity of your VPS. Time for diagnosis!
@warg You're right, we do need some tools to help with situations like these. BTW, here's a copy of the letter that I received, I excluded the top portion for privacy reasons (name, address, account number, etc.). Spectrum (formerly known as Time Warner) is a huge ISP here in the US.
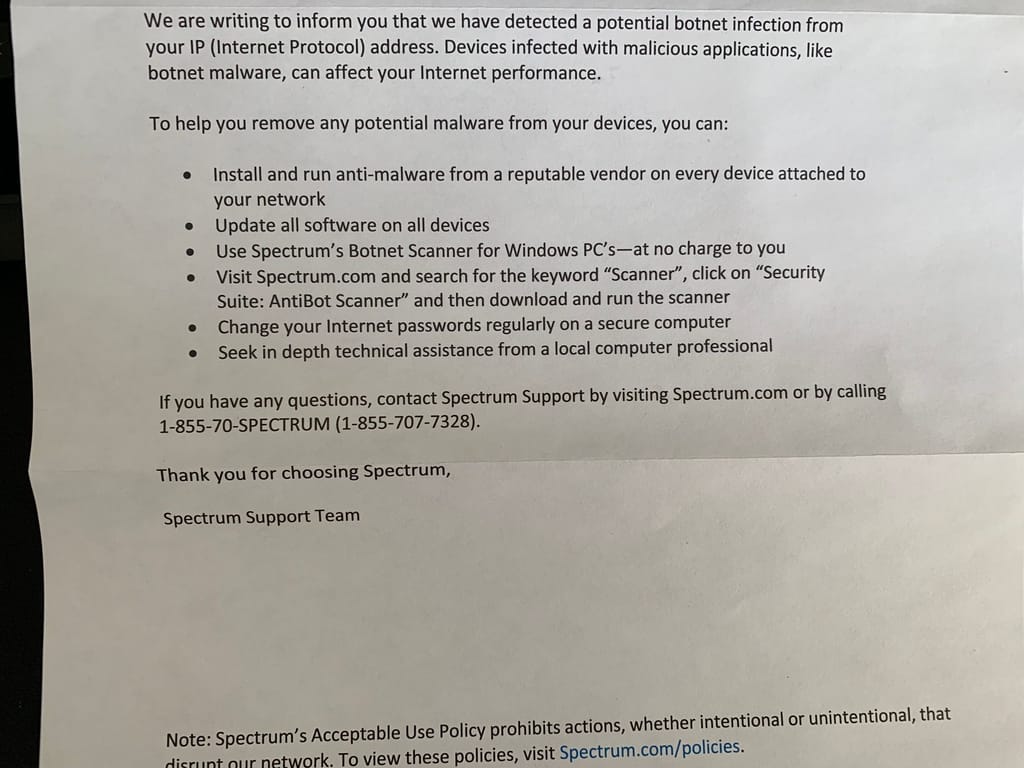
There are multiple posts about receiving this letter and according to the web pages I did read, none were able to find any actual proof that their devices were infected with malware.
https://duckduckgo.com/?q=reddit+spectrum+botnet+infection+letter&t=ffab&ia=web
-
@timconsidine I'm glad the issue is resolved, or should I say, isn't a threat to the continuity of your VPS. Time for diagnosis!
@warg You're right, we do need some tools to help with situations like these. BTW, here's a copy of the letter that I received, I excluded the top portion for privacy reasons (name, address, account number, etc.). Spectrum (formerly known as Time Warner) is a huge ISP here in the US.

There are multiple posts about receiving this letter and according to the web pages I did read, none were able to find any actual proof that their devices were infected with malware.
https://duckduckgo.com/?q=reddit+spectrum+botnet+infection+letter&t=ffab&ia=web
@humptydumpty sure looks like a "sales letter" for their services rather than a technical letter.
-
 G girish has marked this topic as solved on
G girish has marked this topic as solved on
-
@timconsidine I found very similar reports in other server forums (all with this
mach3builders.nlsignature):- https://forum.virtualmin.com/t/under-attack-or-attacking-other-servers/115101/13
- https://community.freepbx.org/t/freepbx-server-compromised/69797
- https://www.3cx.com/community/threads/abuse-from.82124/
- https://gathering.tweakers.net/forum/list_messages/2033082
I am not sure what to make out of this since it seem to happen even without WP and even on a freepbx installation.
-
@timconsidine I found very similar reports in other server forums (all with this
mach3builders.nlsignature):- https://forum.virtualmin.com/t/under-attack-or-attacking-other-servers/115101/13
- https://community.freepbx.org/t/freepbx-server-compromised/69797
- https://www.3cx.com/community/threads/abuse-from.82124/
- https://gathering.tweakers.net/forum/list_messages/2033082
I am not sure what to make out of this since it seem to happen even without WP and even on a freepbx installation.
@girish said in Abuse report received:
I found very similar reports in other server forums
interesting, thank you
also not sure what to make of it !
