Cloudron and Apps Behind a Proxy
-
@doodlemania2 isn't that the typical home setup, where in this case the proxy is the home router?
-
@robi In a home setup, the home-router acts as a NAT, not a proxy. It's totally different, as it acts at level 3/4 of the network stack, not level 7
-
@doodlemania2 You can just proxy_pass (https), it should work fine. I think if you have the programmatic DNS then Cloudron can gets certs with DNS automation with no problem as well (otherwise, you will have to somehow auto-magically redirect .well-known stuff required for LE).
I recall this post - https://forum.cloudron.io/topic/2094/reverse-proxy-infront-of-cloudron-gives-me-to-many-redirects . Maybe @smilebasti has a config.
@girish That seems like a good idea. I was thinking of doing this:
Internet -> 1. NGinix Proxy Manager -> Cloudron
2. NGinix Proxy Manager -> Other thingWhere:
- Proxy host apps.mydomain.net (my cloudron) which has DNS set to public IP address.
- Proxy host blah.mydomain.net (my other thing) which has DNS set to public IP address.
Looks a bit like this:
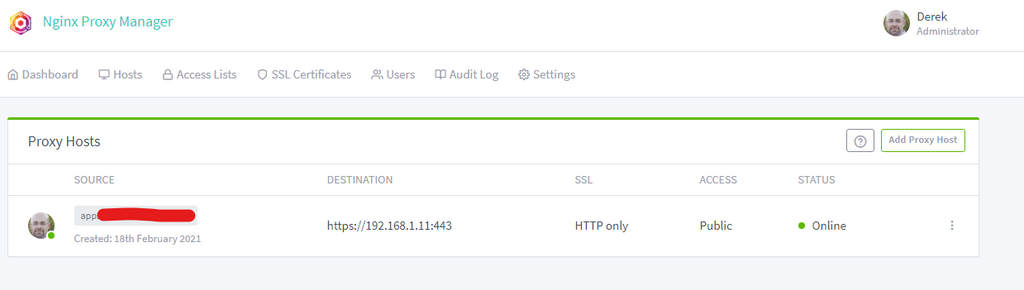
My Cloudron DNS is set up as Wildcard so that's happy. But I don't think I can have a cert in the proxy AND on the Cloudron resolving to same thing?
-
@girish That seems like a good idea. I was thinking of doing this:
Internet -> 1. NGinix Proxy Manager -> Cloudron
2. NGinix Proxy Manager -> Other thingWhere:
- Proxy host apps.mydomain.net (my cloudron) which has DNS set to public IP address.
- Proxy host blah.mydomain.net (my other thing) which has DNS set to public IP address.
Looks a bit like this:

My Cloudron DNS is set up as Wildcard so that's happy. But I don't think I can have a cert in the proxy AND on the Cloudron resolving to same thing?
@doodlemania2 may have to copy the cert over manually..
-
@girish That seems like a good idea. I was thinking of doing this:
Internet -> 1. NGinix Proxy Manager -> Cloudron
2. NGinix Proxy Manager -> Other thingWhere:
- Proxy host apps.mydomain.net (my cloudron) which has DNS set to public IP address.
- Proxy host blah.mydomain.net (my other thing) which has DNS set to public IP address.
Looks a bit like this:

My Cloudron DNS is set up as Wildcard so that's happy. But I don't think I can have a cert in the proxy AND on the Cloudron resolving to same thing?
@doodlemania2 said in Cloudron and Apps Behind a Proxy:
But I don't think I can have a cert in the proxy AND on the Cloudron resolving to same thing?
What do you mean by this? Cert doesn't resolve to anything (or did you mean DNS? even then I am not sure what you are asking...)
But you are on the right path! For Cloudron, choose https proxying.
-
@girish That seems like a good idea. I was thinking of doing this:
Internet -> 1. NGinix Proxy Manager -> Cloudron
2. NGinix Proxy Manager -> Other thingWhere:
- Proxy host apps.mydomain.net (my cloudron) which has DNS set to public IP address.
- Proxy host blah.mydomain.net (my other thing) which has DNS set to public IP address.
Looks a bit like this:

My Cloudron DNS is set up as Wildcard so that's happy. But I don't think I can have a cert in the proxy AND on the Cloudron resolving to same thing?
@doodlemania2 I think you should just use traefik (or another reverse-proxy that handles Let'sEncrypt stuff by itself), and just disable certs on Cloudron's side. You don't really care about the encryption between the Reverse-Proxy and cloudron, if there are self-signed certs, it shouldn't be an issue (as long as the reverse-proxy is configured to accept it)
-
@doodlemania2 I think you should just use traefik (or another reverse-proxy that handles Let'sEncrypt stuff by itself), and just disable certs on Cloudron's side. You don't really care about the encryption between the Reverse-Proxy and cloudron, if there are self-signed certs, it shouldn't be an issue (as long as the reverse-proxy is configured to accept it)
@mehdi this is kind of like that, just with a pretty GUI. https://github.com/jc21/nginx-proxy-manager?utm_source=nginx-proxy-manager
Haven't gotten it to work with CR yet, but I'm getting close!
-
@mehdi this is kind of like that, just with a pretty GUI. https://github.com/jc21/nginx-proxy-manager?utm_source=nginx-proxy-manager
Haven't gotten it to work with CR yet, but I'm getting close!
have tried pretty much everything i can think of but can't seem to get cloudron to NOT try to do SSL. it's not that big of a deal, just something I was trying to figure out for fun.
-
have tried pretty much everything i can think of but can't seem to get cloudron to NOT try to do SSL. it's not that big of a deal, just something I was trying to figure out for fun.
@doodlemania2 said in Cloudron and Apps Behind a Proxy:
but can't seem to get cloudron to NOT try to do SSL
Cloudron will always do TLS. Have your just tried configuring reverse proxy to do TLS? Atleast in nginx, this is doable. See https://docs.nginx.com/nginx/admin-guide/security-controls/securing-http-traffic-upstream/#complete-example
-
@doodlemania2 said in Cloudron and Apps Behind a Proxy:
but can't seem to get cloudron to NOT try to do SSL
Cloudron will always do TLS. Have your just tried configuring reverse proxy to do TLS? Atleast in nginx, this is doable. See https://docs.nginx.com/nginx/admin-guide/security-controls/securing-http-traffic-upstream/#complete-example
@girish this is likely just me not knowing how nginx works:
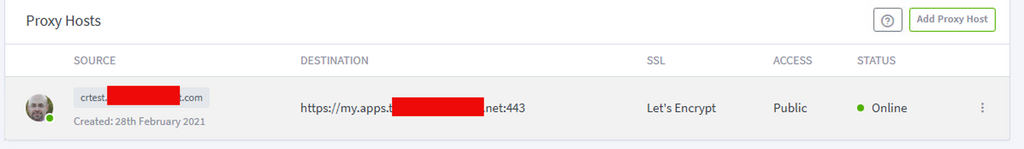
Was hoping crtest.altdomain would pass to existing my.apps.primarydomain and it would "just work" but I got the "You've found a cloudron in the wild"That was somewhat expected cause the CR doesn't know about crtest.altdomain. Was kind of hoping NGinx would have done that translation for me by keeping the destination as the 'URL' that I wanted.
I suppose I could create a crtest.altdomain in CR and things would magically just start working, but I'd have to assign the altdomain names to each of my apps, I think??
-
@girish this is likely just me not knowing how nginx works:

Was hoping crtest.altdomain would pass to existing my.apps.primarydomain and it would "just work" but I got the "You've found a cloudron in the wild"That was somewhat expected cause the CR doesn't know about crtest.altdomain. Was kind of hoping NGinx would have done that translation for me by keeping the destination as the 'URL' that I wanted.
I suppose I could create a crtest.altdomain in CR and things would magically just start working, but I'd have to assign the altdomain names to each of my apps, I think??
@doodlemania2 As a first step, you can try this to understand how it might work:
curl -k -H 'Host: app.domain.com' https://<cloudron-server-ip>To explain the above, first we try to reach the cloudron server by IP via https. In your case, (if I understood your setup), this IP will be the intranet cloudron server IP (and not the public one). Next, the
Hostheader helps (cloudron) nginx decide which vhost/app the request is meant for. Finally, the -k is needed because curl will not be able to match the server cert because we are accessing by IP but the cert will be whatever the host header was set to.If the above works, you just have to make it work in the above UI:
- Make sure destination is https://ip
- I am guessing the Host header is automatically set
- You have to accept the cert.
-
@doodlemania2 As a first step, you can try this to understand how it might work:
curl -k -H 'Host: app.domain.com' https://<cloudron-server-ip>To explain the above, first we try to reach the cloudron server by IP via https. In your case, (if I understood your setup), this IP will be the intranet cloudron server IP (and not the public one). Next, the
Hostheader helps (cloudron) nginx decide which vhost/app the request is meant for. Finally, the -k is needed because curl will not be able to match the server cert because we are accessing by IP but the cert will be whatever the host header was set to.If the above works, you just have to make it work in the above UI:
- Make sure destination is https://ip
- I am guessing the Host header is automatically set
- You have to accept the cert.
@girish Some success! This is wicked cool - and, by the way, I now have BBB server up and running for CR folks to use anytime they/yall need.
One question - when I go to my CR sites now, I am getting a cert error - you indicated that would likely happen I think. Any way to avoid that?
https://conference.cloudromdomain is nginx proxy to https://ip-address-of-cloudron.
-
@girish Some success! This is wicked cool - and, by the way, I now have BBB server up and running for CR folks to use anytime they/yall need.
One question - when I go to my CR sites now, I am getting a cert error - you indicated that would likely happen I think. Any way to avoid that?
https://conference.cloudromdomain is nginx proxy to https://ip-address-of-cloudron.
-
@doodlemania2 I think this is because nginx proxy manager does not have valid certs for the
conferencesubdomain. Does it say it has valid certs?@girish I think it's clean now - I tweaked the nginx. Should be able to see it at https://conference.apps.thedoodleproject.net huzzah!
-
@girish I think it's clean now - I tweaked the nginx. Should be able to see it at https://conference.apps.thedoodleproject.net huzzah!
-
@doodlemania2 Can confirm I can see it with proper certs

well, spoke almost too soon - now that I've got that up and running, I thought that I could force https, but Let's Encrypt doesn't like that because it needs to hit HTTP at a well known endpoint. So, am going to continue to tinker to see if I can pass both http and https
-
well, spoke almost too soon - now that I've got that up and running, I thought that I could force https, but Let's Encrypt doesn't like that because it needs to hit HTTP at a well known endpoint. So, am going to continue to tinker to see if I can pass both http and https
-
@doodlemania2 Cloudron does not require http for certs if you use the programmatic DNS backends (since it obtains certs by putting entries in DNS and not using http callbacks).
-
 G girish referenced this topic on
G girish referenced this topic on
-
@girish ahhh that's cool! Sad for me, using Azure DNS

I'm gonna try and figure out how to make my NGinx let both HTTP and HTTPS through on the same domain name - that would seem to be an obvious option hehe@doodlemania2 did you make any progress here?
My Use-Case:
I love CR for my own business and recommended it to one of my clients aswell. We want to operate it in their own infrastructure so in some private networks that are not fully exposed to the internet ans also I cant route 80/443 soley to CR since they are also operating other Web-Services which are not available in CR.What I am trying to achieve
Get cloudron to run on a private network behind a NginxProxyManager in parallel to other web-services.
SSL handling can be left to CR and Nginx should behave like a proxy server but only for sub-domains that are in conjunction with CR-Services. Ideally the forwarding rules would automatically get updated throughWhat I tried so far
Pretty much what you and others also tried. Setup is:
Internet => NignxProxyManager => Cloudron as VM on a lager ESXi in Parallel to other WebservicesDid you make any progress there or gave up eventually?
-
@doodlemania2 did you make any progress here?
My Use-Case:
I love CR for my own business and recommended it to one of my clients aswell. We want to operate it in their own infrastructure so in some private networks that are not fully exposed to the internet ans also I cant route 80/443 soley to CR since they are also operating other Web-Services which are not available in CR.What I am trying to achieve
Get cloudron to run on a private network behind a NginxProxyManager in parallel to other web-services.
SSL handling can be left to CR and Nginx should behave like a proxy server but only for sub-domains that are in conjunction with CR-Services. Ideally the forwarding rules would automatically get updated throughWhat I tried so far
Pretty much what you and others also tried. Setup is:
Internet => NignxProxyManager => Cloudron as VM on a lager ESXi in Parallel to other WebservicesDid you make any progress there or gave up eventually?
@Jan-Macenka I did! Here's my setup:
- Set up a wildcard cert with nginx proxy manager
- I forward *.domain bound for Cloudron to my cloudron server (in my instance located via a wireguard tunnel)
- I set DNS in Cloudron to NoOp
Easy peasy!
