SFTPGo
-
@PhilipInt said in SFTP solution:
I don't understand how a simple sftp server app is not available on cloudron yet ?
Cloudron is designed for hosting web applications i.e apps that have a frontend that can be accessed using a browser. Running server programs (daemons) has not been the focus and currently out of scope.
sftpgo does seems to be more than a simple daemon, it's a web application . It fits in Cloudron.
I just want a place where I can set up a ftp server, add users and permissions on folders, that's it !
If you are not attached to the ftp server aspect, we have various apps like Nextcloud, Cubby, maybe even Surfer which does exactly this.
If you are not attached to the ftp server aspect, we have various apps like Nextcloud, Cubby, maybe even Surfer which does exactly this.
Where Nextcloud is just too heavy and Cubby a tad too minimalistic SFTPGO could fill a gap (+exended other features both of the available solutions are lacking) as well as Filestash.
Also referencing @nebulon's post: https://forum.cloudron.io/topic/7019/sftpgo
-
C ctrl referenced this topic on
-
C ctrl referenced this topic on
-
Started working on it.
First working state here: https://git.cloudron.io/BrutalBirdie/sftpgo-cloudron-app/-/tree/0.0.8?ref_type=tagsDefinition of working:
- SFTP working - tested with FileZilla
- FTP working
- WebUI Working with features
- TODO | OIDC not configured correctly, want to help?https://docs.sftpgo.com/latest/oidc/?h=redirect
Quick test for "techy" users:
wget https://git.cloudron.io/BrutalBirdie/sftpgo-cloudron-app/-/raw/0.0.8/CloudronManifest.json cloudron install --location sftpgo --image brutalbirdie/sftpgo.cloudron.app:0.0.8 -
While on the topic.
FTP is somewhat working because it needs the passive_port_range and yes I could add the Manifest - tcpports - portCount to do this, but I dislike it.I would be fine with SFTP only and no FTP.
But need input from the community. -
Update: FTP and ftpes now working.
Use Version 0.0.9 -
WebDav also working.
Tested with curl.
e.g:wget https://git.cloudron.io/BrutalBirdie/sftpgo-cloudron-app/-/raw/0.0.8/CloudronManifest.json curl -T CloudronManifest.json -u REDACTED:REDACTED https://sftpgo.cloudron.dev:8888 CreatedBuuuuuut this
8888is rather ugly imho.
I would opt for an extra subdomain via. https://docs.cloudron.io/packaging/manifest/#httpports so you don't need the8888
Will test it. -
OIDC stills needs work and I struggle to figure out what is wrong.
Testing all features including all the support for gcs, azure blob and S3 support for users I did not do yet.
Tests also missing for the app and needs to be done.Imo, could be published as unstable (when OIDC is working
 ), so people can start testing to give feedback.
), so people can start testing to give feedback. 
-
WIP - Docker Image 0.0.10
Okay so after some tinkering and reading SFTPGo Code a bit I figures out this seems the correct redirect uris for the manifest.
"oidc": { "loginRedirectUri": "/web/oidc/redirect, /web/admin/oidclogin, /web/client/oidclogin", "logoutRedirectUri": "/", "tokenSignatureAlgorithm": "RS256" }But now I see this:
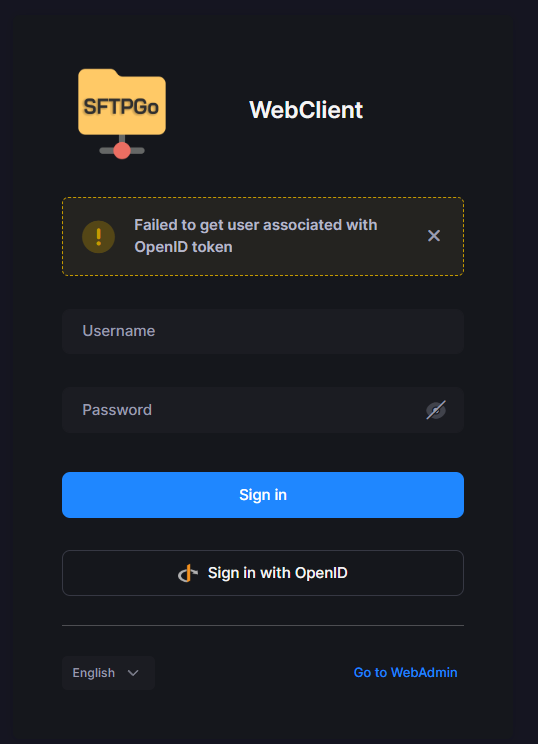
Hmmmmmm yea.... create a user? Please? Pretty please?
Ugh.....
https://docs.sftpgo.com/2.6/dynamic-user-mod/Did I understand this doc right? I need to write a small script which I then need to package with Cloudron?
UUUGGGGHHHHHHHHH OKKKKAAAAYYYY FINE!
-
I've done it. . . . OIDC is now working.
Use Version 0.0.11 but now the login via FileZilla with the Cloudron password is not working
. . .
Hmmm this happend now with a FileZilla
sftp://connection:Jan 26 01:51:04 {"level":"debug","time":"2025-01-26T00:56:30.125","sender":"dataprovider_postgresql","message":"pre-login hook completed, elapsed: 47.318602ms"} Jan 26 01:51:04 {"level":"debug","time":"2025-01-26T00:56:30.132","sender":"dataprovider_postgresql","message":"user \"elias.hackradt\" added/updated from pre-login hook response, id: 1"} Jan 26 01:51:04 {"level":"debug","time":"2025-01-26T00:56:30.157","sender":"connection_failed","client_ip":"2a02:8109:ab82:c600:200b:7676:a14b:4ae1","username":"elias.hackradt","login_type":"keyboard-interactive","protocol":"SSH","error":"credentials cannot be null or empty"} Jan 26 01:51:04 {"level":"debug","time":"2025-01-26T00:56:30.162","sender":"defender","client_ip":"2a02:8109:ab82:c600:200b:7676:a14b:4ae1","protocol":"SSH","event":"LoginFailed","increase_score_by":1,"score":9} Jan 26 01:51:04 {"level":"debug","time":"2025-01-26T00:56:31.223","sender":"dataprovider_postgresql","message":"pre-login hook completed, elapsed: 35.230284ms"} Jan 26 01:51:04 {"level":"debug","time":"2025-01-26T00:56:31.226","sender":"dataprovider_postgresql","message":"user \"elias.hackradt\" added/updated from pre-login hook response, id: 1"} Jan 26 01:51:04 {"level":"debug","time":"2025-01-26T00:56:31.250","sender":"connection_failed","client_ip":"2a02:8109:ab82:c600:200b:7676:a14b:4ae1","username":"elias.hackradt","login_type":"keyboard-interactive","protocol":"SSH","error":"read tcp [fd00:c107:d509::23]:2022->[2a02:8109:ab82:c600:200b:7676:a14b:4ae1]:4271: read: connection reset by peer"} Jan 26 01:51:04 {"level":"debug","time":"2025-01-26T00:56:31.253","sender":"defender","client_ip":"2a02:8109:ab82:c600:200b:7676:a14b:4ae1","protocol":"SSH","event":"LoginFailed","increase_score_by":1,"score":10}I mean leaking the password via. maybe even an unsecured
ftpconnection is bad.
sftpis a secure connection so the password could be transmitted for theOIDClogin? I mean the log statesJan 26 01:51:04 {"level":"debug","time":"2025-01-26T00:56:30.132","sender":"dataprovider_postgresql","message":"user "elias.hackradt" added/updated from pre-login hook response, id: 1"}
soooo login was OK I guess but the forward back to the sftp client is somehow faulty.
What IS working, adding a ssh-pub key to my profile:
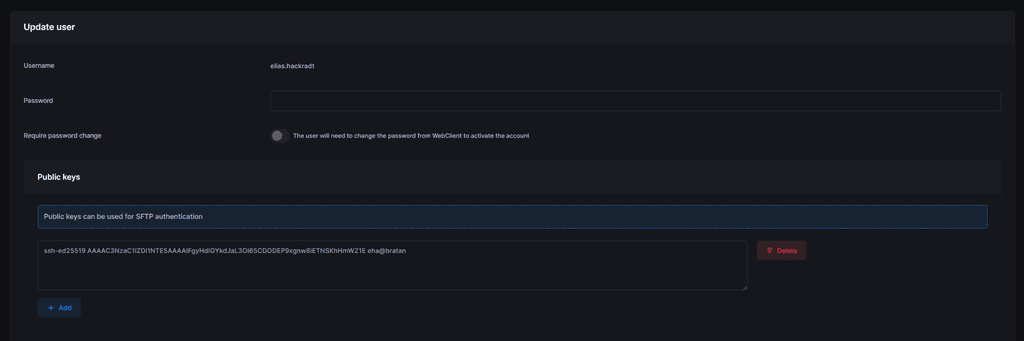
and using that key in filezilla to connect:
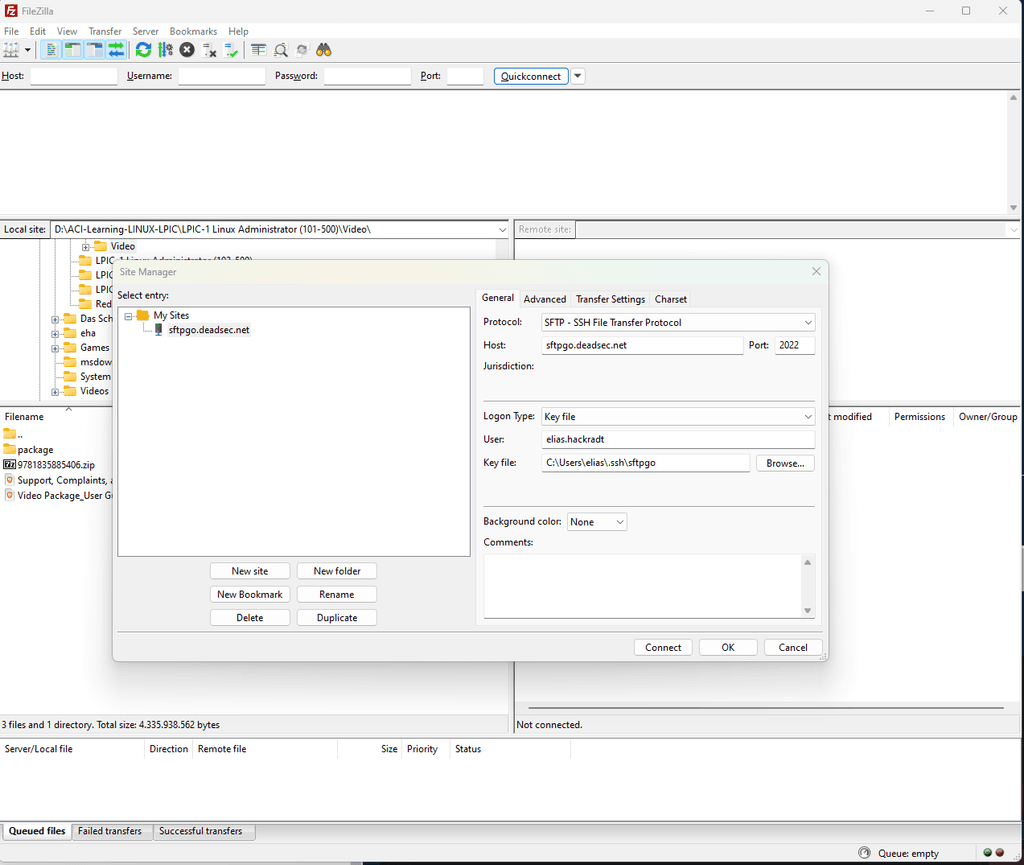
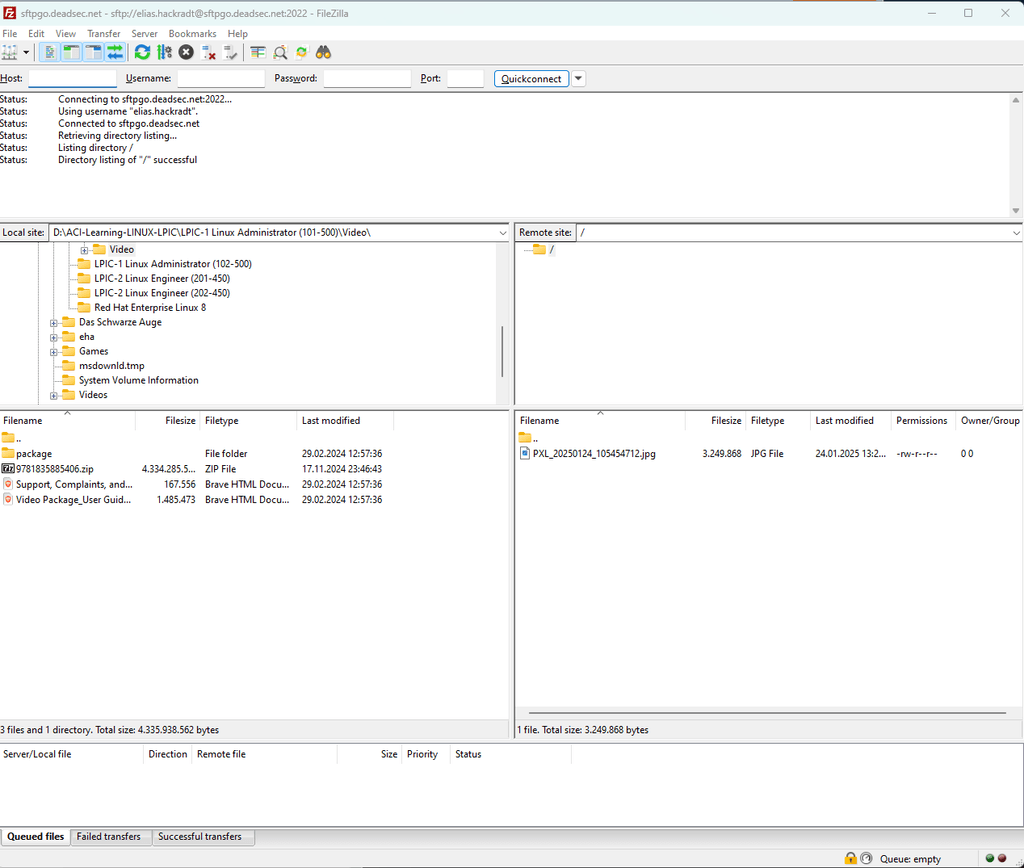
This could be a way to use OIDC with SFTPGo.
Scraping my head how it would be best.
-
HAH even worse! With my current solution, you can send a random username. via. ftp and it will be created

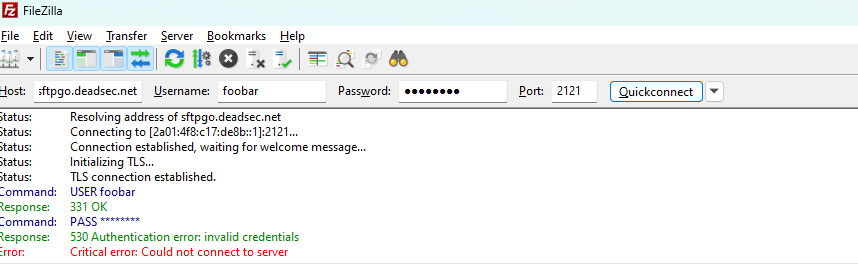
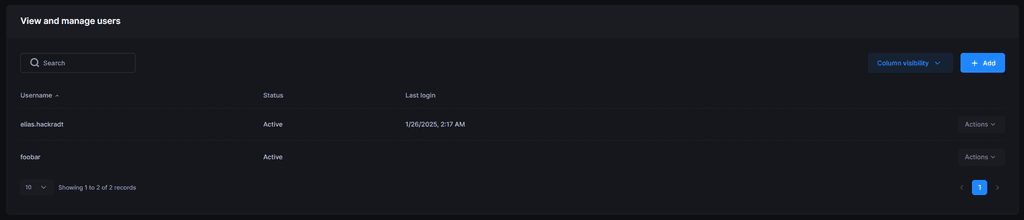
Writing a hotfix

Fixed with0.0.12:- user spam via ftp clients or other clients is no longer possible.
Time for sleep

-
Image 0.0.13
Changelog:- Added
/app/data/oidc.iniwhich allows some control of the/app/code/oidc.pygetting called onpre_login_hook
[OIDC] # Enable / Disable OIDC dynamic user Creating output to /app/data/oidc.log DEBUG=False # Should Users that login via OIDC be created CREATE_USER=True # Should the User be enabled - 1 Enabled 0 Disabled USER_ENABLE=1 # The default dir where user homes will be created with his username - NO TRAILING BACKSHLASH AND NO SINGLE OR DOUBLE QUOTES HOME_DIR=/app/data/userdata - Added
-
Image 0.0.14
Changelog:
- Added SMTP Config
-
Is this ready for an "unstable" release?
-
i managed to install sftpgo from the @BrutalBirdie repository. while the server kept on working the webinterface is banned - restarting doesn't resolve this.
{"level":"debug","time":"2025-02-24T12:24:20.019","sender":"dataprovider_postgresql","message":"ban time updated for ip \"172.18.0.1\", increment (minutes): 15"}and to be honest i don't get how to update to the mentioned versions above 0.0.9 as they don't seem to be available?
-
i managed to install sftpgo from the @BrutalBirdie repository. while the server kept on working the webinterface is banned - restarting doesn't resolve this.
{"level":"debug","time":"2025-02-24T12:24:20.019","sender":"dataprovider_postgresql","message":"ban time updated for ip \"172.18.0.1\", increment (minutes): 15"}and to be honest i don't get how to update to the mentioned versions above 0.0.9 as they don't seem to be available?
@jkammerer Hmmm this means the build in defender banned you for some reason.
Did you try to log in in the normal dashboard with the admin credentials or vice versa?i don't get how to update to the mentioned versions above 0.0.9 as they don't seem to be available?
There is no other version yet. 0.0.9 is latest.
How to update? Simply get the newest CloudronManifest.json and run the update command.
Example:cloudron update --app $LOCATION --image brutalbirdie/$IMAGENAME:$IMAGETAG -
I have published an initial version but it needs some fixes. Hopefully, in a better state in a day or two. Thanks @BrutalBirdie .
Tests are being added as well. https://git.cloudron.io/packages/sftpgo-app is the new location .
-
 G girish locked this topic on
G girish locked this topic on
-
 G girish marked this topic as a question on
G girish marked this topic as a question on
-
 G girish has marked this topic as solved on
G girish has marked this topic as solved on

