Anyone else see many connections denied due to "Mail from domain <domain> is not allowed from your host" repeatedly from spammy IPs?
-
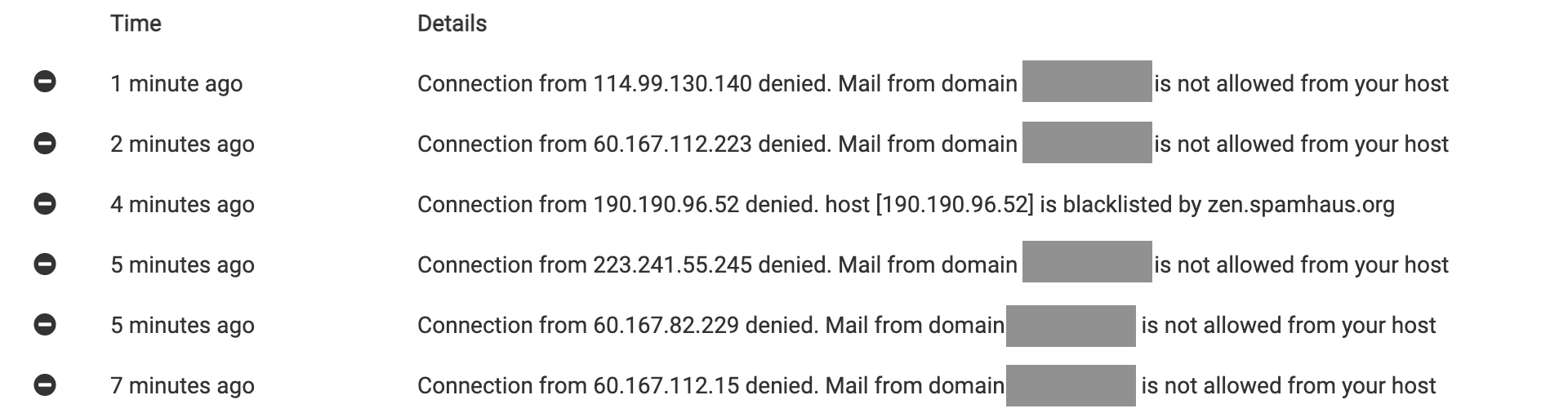
I keep seeing this message recently (a bit ago it was several different attempts in less than 10 minutes for the same domain, image below) and it seems to be growing in popularity in the logs over the past month or so, today in particular seems extra bad. I know the SPF record for the domain in question is correct.
The IP addresses are different but similar in range, and I see them on the blacklists check too so they're definitely spammy IPs.
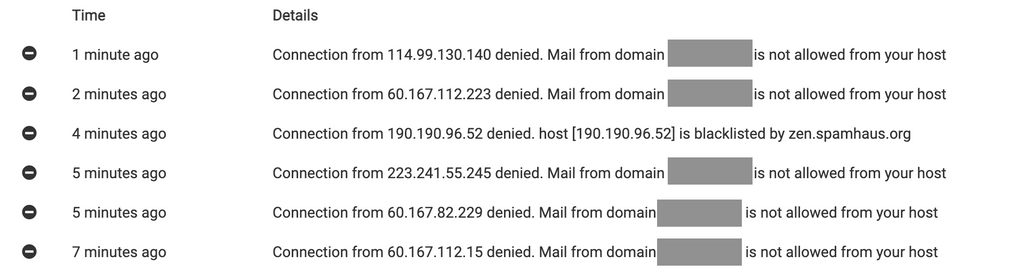
Here is the top example:
{ "ts": 1617145926606, "type": "denied", "direction": "inbound", "uuid": "5D744873-5B50-49C7-A471-8E4DCFB5961B.1", "remote": { "ip": "114.99.130.140", "port": 57217, "host": "NXDOMAIN", "info": "NXDOMAIN", "closed": false, "is_private": false, "is_local": false }, "authUser": null, "mailFrom": "<{username}@{MyClientsHostedDomainOnCloudronServer}>", "rcptTo": [], "details": { "relaying": false, "pluginName": "rcpt_to.in_host_list", "errorCode": 902, "message": "Mail from domain 'drjaver.com' is not allowed from your host", "rejectionCountLastHour": 0 } }I found this in the Haraka docs: https://github.com/haraka/Haraka/blob/master/docs/plugins/rcpt_to.in_host_list.md
I just want to make sure I understand the workflow here. I believe the issue here is somebody is trying to spoof the email address of an email address I host on my mail server, coming from some spammy IP. Is that correct?
I guess if that's correct then there's not much I can do though here except try and report the spam to the abuse@ contacts for the network, which doesn't really do anything in most cases anyways. Or I guess just outright block the IPs from my server completely.
I'm curious though too why there's no value for
rcptTo, is that expected behaviour? It almost makes it look like there's an email address sent to no particular email address, which can't be right.I ultimately am wanting to understand:
- If others have seen an increase in this type of spam caught by Haraka in Cloudron
- If I understand the workflow correctly in that it's an incoming spam message pretending to be from an email address domain I host which means per the SPF record it cannot possibly come from the originating IP so gets denied... right? The lack of a
rcptToin particular confuses me though.
-
To give a better idea of the extent of this for my mail server... this is how much of this I've seen just in the last hour for the same domain. Almost every IP I looked up is coming from the same ASN
#4134 - Asia Pacific Network Information Centre. This is far from the usual (I'll maybe see this between 2 and 10 times a day, not almost 40 in a single hour). Looks like the "attack" started about 3 hours ago when I go further back in the logs. Seems the Haraka engine is doing fine though, I hope this doesn't impact my other clients on the same server email-wise. Should be okay, plenty of memory available anyways.I'd normally try to just revoke the IP CIDR range, but when I look it up the one has over 2 million IPs in the CIDR and since about 20% of the traffic to three different client's websites comes from China for business (COVID-19 testing for essential travel), I don't think I can outright block the ASN (yet) unfortunately.
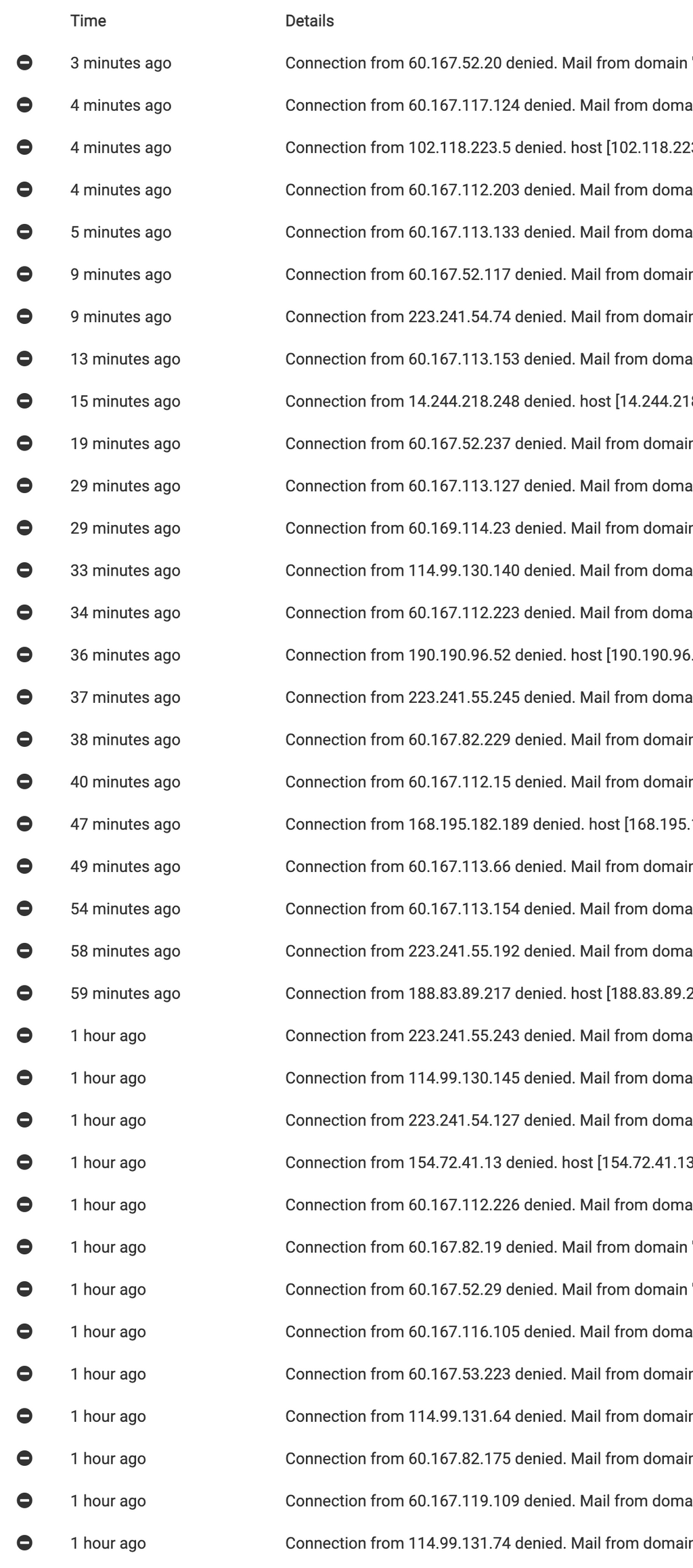
EDIT: I decided to block at the IP level for now but did some CIDR calculations to have less false-positives. Blocked the following ranges temporarily (I'll remove them tomorrow and see if the issue continues):
60.167.0.0/17
114.99.128.0/21
223.241.48.0/20 -
I keep seeing this message recently (a bit ago it was several different attempts in less than 10 minutes for the same domain, image below) and it seems to be growing in popularity in the logs over the past month or so, today in particular seems extra bad. I know the SPF record for the domain in question is correct.
The IP addresses are different but similar in range, and I see them on the blacklists check too so they're definitely spammy IPs.

Here is the top example:
{ "ts": 1617145926606, "type": "denied", "direction": "inbound", "uuid": "5D744873-5B50-49C7-A471-8E4DCFB5961B.1", "remote": { "ip": "114.99.130.140", "port": 57217, "host": "NXDOMAIN", "info": "NXDOMAIN", "closed": false, "is_private": false, "is_local": false }, "authUser": null, "mailFrom": "<{username}@{MyClientsHostedDomainOnCloudronServer}>", "rcptTo": [], "details": { "relaying": false, "pluginName": "rcpt_to.in_host_list", "errorCode": 902, "message": "Mail from domain 'drjaver.com' is not allowed from your host", "rejectionCountLastHour": 0 } }I found this in the Haraka docs: https://github.com/haraka/Haraka/blob/master/docs/plugins/rcpt_to.in_host_list.md
I just want to make sure I understand the workflow here. I believe the issue here is somebody is trying to spoof the email address of an email address I host on my mail server, coming from some spammy IP. Is that correct?
I guess if that's correct then there's not much I can do though here except try and report the spam to the abuse@ contacts for the network, which doesn't really do anything in most cases anyways. Or I guess just outright block the IPs from my server completely.
I'm curious though too why there's no value for
rcptTo, is that expected behaviour? It almost makes it look like there's an email address sent to no particular email address, which can't be right.I ultimately am wanting to understand:
- If others have seen an increase in this type of spam caught by Haraka in Cloudron
- If I understand the workflow correctly in that it's an incoming spam message pretending to be from an email address domain I host which means per the SPF record it cannot possibly come from the originating IP so gets denied... right? The lack of a
rcptToin particular confuses me though.
@d19dotca said in Anyone else see many connections denied due to "Mail from domain <domain> is not allowed from your host" repeatedly from spammy IPs?:
I just want to make sure I understand the workflow here. I believe the issue here is somebody is trying to spoof the email address of an email address I host on my mail server, coming from some spammy IP. Is that correct?
I think your analysis is correct. Someone is trying to send mails to Cloudron, with FROM address set to a domain that you host. Cloudron then rejects it saying this is not allowed because after all only itself and other SPF listed servers can send mail with that FROM address.
A bit of a wild guess: mail from is usually
<>for bounce mail. So, this seems like some poor denial of service or maybe those IPs know that some mail software misbehaves with such carefully crafted mail. -
@d19dotca said in Anyone else see many connections denied due to "Mail from domain <domain> is not allowed from your host" repeatedly from spammy IPs?:
I just want to make sure I understand the workflow here. I believe the issue here is somebody is trying to spoof the email address of an email address I host on my mail server, coming from some spammy IP. Is that correct?
I think your analysis is correct. Someone is trying to send mails to Cloudron, with FROM address set to a domain that you host. Cloudron then rejects it saying this is not allowed because after all only itself and other SPF listed servers can send mail with that FROM address.
A bit of a wild guess: mail from is usually
<>for bounce mail. So, this seems like some poor denial of service or maybe those IPs know that some mail software misbehaves with such carefully crafted mail.@girish said in Anyone else see many connections denied due to "Mail from domain <domain> is not allowed from your host" repeatedly from spammy IPs?:
A bit of a wild guess: mail from is usually <> for bounce mail. So, this seems like some poor denial of service or maybe those IPs know that some mail software misbehaves with such carefully crafted mail.
Ah very interesting, I appreciate that insight. It was definitely strange when I saw it happening - so many requests at once. I'll keep an eye out for it. Sounds like it's all good then as far as Cloudron is concerned.
 Thanks Girish.
Thanks Girish. -
I see the same behavior- someone is permanently trying to send as one specific sender (specificname@domain.com) from IPs such as:
2.133.95.174 2.135.199.137 5.126.117.216 31.169.30.190 89.237.194.133 91.98.60.233 103.234.25.66 103.71.59.198 113.185.92.35 125.212.159.28 125.212.158.246 149.54.6.150 178.217.173.123 195.158.14.27 213.230.96.66 213.230.92.146 213.230.126.9 213.230.80.33 213.230.93.109 217.29.22.198Is there any „comfortable“ or sensible way to block this?
In this context I just remembered: https://forum.cloudron.io/topic/3795/
-
Yes, there is a "network block"/filter in the UI. Just paste the networks and IPs like you have in that list.
There are other forum posts with that " " search term above.
@robi said in Anyone else see many connections denied due to "Mail from domain <domain> is not allowed from your host" repeatedly from spammy IPs?:
Yes, there is a "network block"/filter in the UI. Just paste the networks and IPs like you have in that list.
There are other forum posts with that " " search term above.
I know, I even linked my topic on the matter.

But currently, we don’t have a way to subscribe to- regularly updated- IP blocklists; and manually going through each blocked sending attempt and then copy&paste some IP (fruitless) or figuring out the relevant IP range doesn’t seem „comfortable“ or „sensible“ (to quote myself)…
And I thought there might even be some other way I‘m not aware of (e.g. spam filter rule) -
You can block by sender name. In my case, i have this advid guy who is really really persistent.
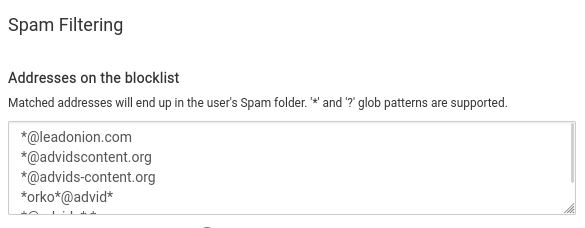
@girish said in Anyone else see many connections denied due to "Mail from domain <domain> is not allowed from your host" repeatedly from spammy IPs?:
You can block by sender name. In my case, i have this advid guy who is really really persistent.

The addresses you listed: Are those the ones the sender is trying to send as (i.e. the one showing up as
“mailFrom:“in the mail event log entry? -
@girish said in Anyone else see many connections denied due to "Mail from domain <domain> is not allowed from your host" repeatedly from spammy IPs?:
You can block by sender name. In my case, i have this advid guy who is really really persistent.

The addresses you listed: Are those the ones the sender is trying to send as (i.e. the one showing up as
“mailFrom:“in the mail event log entry? -
@necrevistonnezr Ah, sorry! I misread. In my case, the sender is just spamming the hell out of me for video content. Sender is not trying to spoof. I guess you have to block by IP in the network firewall.
@girish said in Anyone else see many connections denied due to "Mail from domain <domain> is not allowed from your host" repeatedly from spammy IPs?:
@necrevistonnezr Ah, sorry! I misread. In my case, the sender is just spamming the hell out of me for video content. Sender is not trying to spoof. I guess you have to block by IP in the network firewall.
Yeah, well, those IPs are never the same (see above) and even ranges are difficult to ascertain. Maybe an easy way to subscribe to a blocklist would help?
 (as suggested in my old topic linked above…)
(as suggested in my old topic linked above…)