Multiple account privacy
-
@BrutalBirdie Ha! I'm bouncing back and forth between this and another project right now. I appreciate all your help. Gives me a direction to play around with. Beer forthcoming

Encryption keys are stored only on the Nextcloud server, eliminating exposure of your data to third-party storage providers. The encryption app does not protect your data if your Nextcloud server is compromised, and it does not prevent Nextcloud administrators from reading user’s files. This would require client-side encryption, which this app does not provide. If your Nextcloud server is not connected to any external storage services then it is better to use other encryption tools, such as file-level or whole-disk encryption.

This is by design.
https://docs.nextcloud.com/server/23/admin_manual/configuration_files/encryption_configuration.html
The first big yellow warning.
ps: Thanks for the Beer! Cheers

-
Encryption keys are stored only on the Nextcloud server, eliminating exposure of your data to third-party storage providers. The encryption app does not protect your data if your Nextcloud server is compromised, and it does not prevent Nextcloud administrators from reading user’s files. This would require client-side encryption, which this app does not provide. If your Nextcloud server is not connected to any external storage services then it is better to use other encryption tools, such as file-level or whole-disk encryption.

This is by design.
https://docs.nextcloud.com/server/23/admin_manual/configuration_files/encryption_configuration.html
The first big yellow warning.
ps: Thanks for the Beer! Cheers

And here we go for another round ...
https://apps.nextcloud.com/apps/impersonateThis app is not compatible with instances that have encryption enabled.

But.... it is? Its working? Right now?
-
You can always encrypt before uploading.
Or use internxt.com which does ZK e2e for you.
-
And here we go for another round ...
https://apps.nextcloud.com/apps/impersonateThis app is not compatible with instances that have encryption enabled.

But.... it is? Its working? Right now?
Ok... this is getting into a convoluted mess.
Now I found out there should be a per-user-encryption:
https://docs.nextcloud.com/server/latest/admin_manual/configuration_files/encryption_details.html#key-type-user-keyFunny how this is missing in the doc for the encryption ooc commands...........
https://docs.nextcloud.com/server/23/admin_manual/configuration_server/occ_command.html#encryption-labelAnd also not mentioned in the main doc where they show and tell about the
Enabling users file recovery keys.

I've set up a new Nextcloud (with user managed by the app) and installed the
Default Encryption Modulethen went into the Nextcloud app web-terminal and did a:root@f6665ea8-5f0a-41f7-b8ae-be1719062c33:/app/code# sudo -u www-data php -f /app/code/occ encryption:disable-master-key Warning: Only perform this operation for a fresh installations with no existing encrypted data! There is no way to enable the master key again. We strongly recommend to keep the master key, it provides significant performance improvements and is easier to handle for both, users and administrators. Do you really want to switch to per-user keys? (y/n) y Master key successfully disabled.Then I enabled the server wide encryption.
Ok understandable because: https://docs.nextcloud.com/server/latest/admin_manual/configuration_files/encryption_configuration.html#enabling-users-file-recovery-keysSo I set a recovery key. Good? Ehhhh... with that I can decrypt files from a user if he allows it.
Wait... if the user allows it? By default it's not allowed.
So if I try this in the web-terminal:root@f6665ea8-5f0a-41f7-b8ae-be1719062c33:/app/code# sudo -u www-data php -f /app/code/occ encryption:decrypt-all eha Disable server side encryption... done. You are about to start to decrypt all files stored in eha's account. It will depend on the encryption module and your setup if this is possible. Depending on the number and size of your files this can take some time Please make sure that no user access his files during this process! Do you really want to continue? (y/n) y prepare encryption modules... Prepare "Default encryption module" You can only decrypt the users files if you know the users password or if he activated the recovery key. Do you want to use the users login password to decrypt all files? (y/n) n No recovery key available for user eha Module "Default encryption module" does not support the functionality to decrypt all files again or the initialization of the module failed! aborted. Server side encryption remains enabledSo now I impersonate the user... and allow it?

Please no....

Please don't tell me now that I can decrypt the user files afterwards.root@f6665ea8-5f0a-41f7-b8ae-be1719062c33:/app/code# sudo -u www-data php -f /app/code/occ encryption:decrypt-all eha Disable server side encryption... done. You are about to start to decrypt all files stored in eha's account. It will depend on the encryption module and your setup if this is possible. Depending on the number and size of your files this can take some time Please make sure that no user access his files during this process! Do you really want to continue? (y/n) y prepare encryption modules... Prepare "Default encryption module" You can only decrypt the users files if you know the users password or if he activated the recovery key. Do you want to use the users login password to decrypt all files? (y/n) n Please enter the recovery key password: done. starting to decrypt files... finished [============================] Files for following users couldn't be decrypted, maybe the user is not set up in a way that supports this operation: eha /eha/files/allowed_recovery.md /eha/files/deny_recovery.md Server side encryption remains enabledthank god.
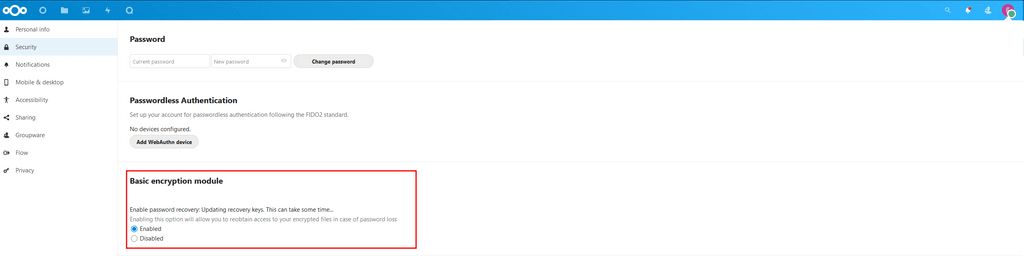
If I now look into the security tab as the user:
This looks bugged.
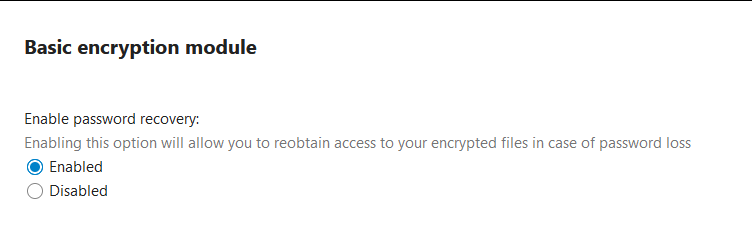
So disable it again:
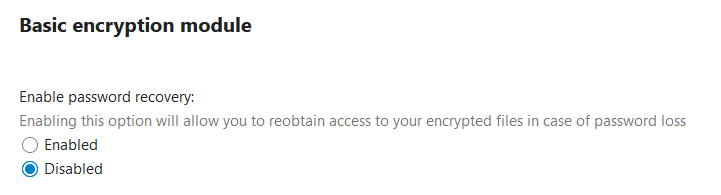
and enable it again:
Hmmm thisRecovery Key enableddid never happen as impersonated user.
So this could be used as an indicator if an admin tried to decrypt your files... good to know I guess.So now I can decrypt the user files with the recovery password?
root@f6665ea8-5f0a-41f7-b8ae-be1719062c33:/app/code# sudo -u www-data php -f /app/code/occ encryption:decrypt-all eha Disable server side encryption... done. You are about to start to decrypt all files stored in eha's account. It will depend on the encryption module and your setup if this is possible. Depending on the number and size of your files this can take some time Please make sure that no user access his files during this process! Do you really want to continue? (y/n) y prepare encryption modules... Prepare "Default encryption module" You can only decrypt the users files if you know the users password or if he activated the recovery key. Do you want to use the users login password to decrypt all files? (y/n) n Please enter the recovery key password: done. starting to decrypt files... finished [============================] all files could be decrypted successfully! Server side encryption remains enabledYep worked.
...
Okay I will write that down a bit clearer tomorrow. (And try this again with LDAP instead of user management by the app)My head is smoking.
This documentation of Nextcloud is a nightmare! -
Ok... this is getting into a convoluted mess.
Now I found out there should be a per-user-encryption:
https://docs.nextcloud.com/server/latest/admin_manual/configuration_files/encryption_details.html#key-type-user-keyFunny how this is missing in the doc for the encryption ooc commands...........
https://docs.nextcloud.com/server/23/admin_manual/configuration_server/occ_command.html#encryption-labelAnd also not mentioned in the main doc where they show and tell about the
Enabling users file recovery keys.

I've set up a new Nextcloud (with user managed by the app) and installed the
Default Encryption Modulethen went into the Nextcloud app web-terminal and did a:root@f6665ea8-5f0a-41f7-b8ae-be1719062c33:/app/code# sudo -u www-data php -f /app/code/occ encryption:disable-master-key Warning: Only perform this operation for a fresh installations with no existing encrypted data! There is no way to enable the master key again. We strongly recommend to keep the master key, it provides significant performance improvements and is easier to handle for both, users and administrators. Do you really want to switch to per-user keys? (y/n) y Master key successfully disabled.Then I enabled the server wide encryption.

Ok understandable because: https://docs.nextcloud.com/server/latest/admin_manual/configuration_files/encryption_configuration.html#enabling-users-file-recovery-keysSo I set a recovery key. Good? Ehhhh... with that I can decrypt files from a user if he allows it.
Wait... if the user allows it? By default it's not allowed.
So if I try this in the web-terminal:root@f6665ea8-5f0a-41f7-b8ae-be1719062c33:/app/code# sudo -u www-data php -f /app/code/occ encryption:decrypt-all eha Disable server side encryption... done. You are about to start to decrypt all files stored in eha's account. It will depend on the encryption module and your setup if this is possible. Depending on the number and size of your files this can take some time Please make sure that no user access his files during this process! Do you really want to continue? (y/n) y prepare encryption modules... Prepare "Default encryption module" You can only decrypt the users files if you know the users password or if he activated the recovery key. Do you want to use the users login password to decrypt all files? (y/n) n No recovery key available for user eha Module "Default encryption module" does not support the functionality to decrypt all files again or the initialization of the module failed! aborted. Server side encryption remains enabledSo now I impersonate the user... and allow it?


Please no....

Please don't tell me now that I can decrypt the user files afterwards.root@f6665ea8-5f0a-41f7-b8ae-be1719062c33:/app/code# sudo -u www-data php -f /app/code/occ encryption:decrypt-all eha Disable server side encryption... done. You are about to start to decrypt all files stored in eha's account. It will depend on the encryption module and your setup if this is possible. Depending on the number and size of your files this can take some time Please make sure that no user access his files during this process! Do you really want to continue? (y/n) y prepare encryption modules... Prepare "Default encryption module" You can only decrypt the users files if you know the users password or if he activated the recovery key. Do you want to use the users login password to decrypt all files? (y/n) n Please enter the recovery key password: done. starting to decrypt files... finished [============================] Files for following users couldn't be decrypted, maybe the user is not set up in a way that supports this operation: eha /eha/files/allowed_recovery.md /eha/files/deny_recovery.md Server side encryption remains enabledthank god.
If I now look into the security tab as the user:

This looks bugged.
So disable it again:

and enable it again:

Hmmm thisRecovery Key enableddid never happen as impersonated user.
So this could be used as an indicator if an admin tried to decrypt your files... good to know I guess.So now I can decrypt the user files with the recovery password?
root@f6665ea8-5f0a-41f7-b8ae-be1719062c33:/app/code# sudo -u www-data php -f /app/code/occ encryption:decrypt-all eha Disable server side encryption... done. You are about to start to decrypt all files stored in eha's account. It will depend on the encryption module and your setup if this is possible. Depending on the number and size of your files this can take some time Please make sure that no user access his files during this process! Do you really want to continue? (y/n) y prepare encryption modules... Prepare "Default encryption module" You can only decrypt the users files if you know the users password or if he activated the recovery key. Do you want to use the users login password to decrypt all files? (y/n) n Please enter the recovery key password: done. starting to decrypt files... finished [============================] all files could be decrypted successfully! Server side encryption remains enabledYep worked.
...
Okay I will write that down a bit clearer tomorrow. (And try this again with LDAP instead of user management by the app)My head is smoking.
This documentation of Nextcloud is a nightmare!@BrutalBirdie Man, what a mess! I didn't have time to look into it today as deeply as you did. Can't thank you enough!
-
Basically, what you want for this is end-to-end encryption (and I know a bit about this, it's literally my job to implement E2EE ^^).
The problem is that the nextcloud app that provides E2EE is bad, like really bad, like "my files just disappeared, i have no idea why" bad.
So, long story short, there is no simple way for you to provide this service to your friend with nextcloud with you not being able to look at their files.
-
Basically, what you want for this is end-to-end encryption (and I know a bit about this, it's literally my job to implement E2EE ^^).
The problem is that the nextcloud app that provides E2EE is bad, like really bad, like "my files just disappeared, i have no idea why" bad.
So, long story short, there is no simple way for you to provide this service to your friend with nextcloud with you not being able to look at their files.
-
As an alternative, I know that https://www.seafile.com/ is a file storage solution which offers end2end encryption, but when I last tried it (admittedly a few years ago) the client software was

@mehdi I moved my file storage/sharing from Nextcloud to Seafile.
Nextcloud works well but is just bloat-ware if you don't use the collab features.
Seafile is working well for me.
Sadly self-hosted on another VPS instead of Cloudron at this stage (until some nice brave person packages it for Cloudron!)
Maybe I'm cheap and easy to please but client software (on Mac) works fine for me, as both syncing client and remote drive client.Having said all that, I haven't explored the E2E encryption on multi-user basis.
-
@mehdi I moved my file storage/sharing from Nextcloud to Seafile.
Nextcloud works well but is just bloat-ware if you don't use the collab features.
Seafile is working well for me.
Sadly self-hosted on another VPS instead of Cloudron at this stage (until some nice brave person packages it for Cloudron!)
Maybe I'm cheap and easy to please but client software (on Mac) works fine for me, as both syncing client and remote drive client.Having said all that, I haven't explored the E2E encryption on multi-user basis.
@timconsidine said in Multiple account privacy:
Seafile is working well for me.
Sadly self-hosted on another VPS instead of Cloudron at this stage (until some nice brave person packages it for Cloudron!)Upvote here:
https://forum.cloudron.io/post/1237 -
Thanks for everyone for their input on this. I love the community here. It's really surprising to me that this functionality isn't clear/straightforward. I've moved forward with a straightforward solution. I just installed another instance of Nextcloud for my friend. A little clunky but it works. It's just my personal Cloudron server anyway.
-
Thanks for everyone for their input on this. I love the community here. It's really surprising to me that this functionality isn't clear/straightforward. I've moved forward with a straightforward solution. I just installed another instance of Nextcloud for my friend. A little clunky but it works. It's just my personal Cloudron server anyway.
@Ropyro said in Multiple account privacy:
I just installed another instance of Nextcloud for my friend
If this relieves his privacy concerns... well. OK I guess

You are still the admin and can view the data..
(alt: There is no cloud, just other people's computers - Sticker by fsfe.org)But still, there must be a solution for this.
I don't want to believe Nextcloud has no good solution for this.. -
@Ropyro said in Multiple account privacy:
I just installed another instance of Nextcloud for my friend
If this relieves his privacy concerns... well. OK I guess

You are still the admin and can view the data..
(alt: There is no cloud, just other people's computers - Sticker by fsfe.org)But still, there must be a solution for this.
I don't want to believe Nextcloud has no good solution for this..@BrutalBirdie Ha -- it didn't. I figured out after I set it up I still had access to his files

