Linode Abuse - DoS Attack Originating from my server?
-
@nicolas Are your wordpress instances up to date? Do you have plugins installed in those instances?
That's where my mind goes immediately.
@iamthefij Thanks - it seems to be have been one of the wordpress instances (this memory spike corresponds to the same times the CPU spiked for the attack).
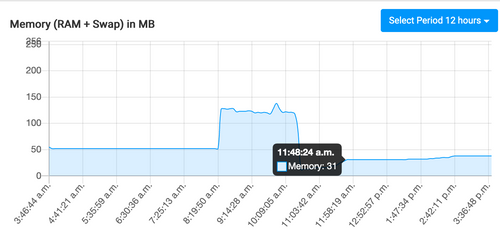
However, it's a Managed wordpress instance and so autoupdates are disabled (as cloudron does these updates) - I have no plugins installed on it. -
@nicolas Are your wordpress instances up to date? Do you have plugins installed in those instances?
That's where my mind goes immediately.
@Nicolas and anyone with a Wordpress issue and not access to developers I recommend the following steps:
- If your site doesn't change much, it is usually a good idea to roll back to the oldest backup you have that is still what you want. You might be lucky and get to a point before any breach.
- Change all Admin user passwords immediately. Might not be that but it's a process of elimination. Most hacks I've seen keep getting back in because they have a compromised Admin account one way or another.
- Run updates for core and all plugins.
- Deactivate and remove all plugins that don't update.
- Run the free version of this: https://wordpress.org/plugins/gotmls/
- Run the free version of this: https://wordpress.org/plugins/wp-cerber/
- Run the free version of this: https://wordpress.org/plugins/wordfence/
- This plugin is old but still works for evaluating any plugin you are unsure of the code quality for, maybe run on a clone just to be safe: https://wordpress.org/plugins/plugin-inspector/
GOTMLS should catch anything and is deep and fast to do and see results, it's the one I've seen most managed Wordpress vendors use and recommend as 1st thing to do when contacting them. It used to scan the core for free but honestly, it's worth the donation for the quality, speed and updates they offer.
Cerber & Wordfence I've had mixed results and speed with but they can't do any harm, and are safe to leave installed and running on the free versions.
-
@iamthefij Thanks - it seems to be have been one of the wordpress instances (this memory spike corresponds to the same times the CPU spiked for the attack).

However, it's a Managed wordpress instance and so autoupdates are disabled (as cloudron does these updates) - I have no plugins installed on it.@nicolas I have seen legit plugins behave like malware too, hence Plugin Inspector can be very revealing.
Basically, with WP plugins, you have to be very, very fussy. If in doubt, create a post with links to any plugin you want experienced opinions on in here as there's a lot of experience that may help and many of us have further contacts if unsure.
-
@iamthefij Thanks - it seems to be have been one of the wordpress instances (this memory spike corresponds to the same times the CPU spiked for the attack).

However, it's a Managed wordpress instance and so autoupdates are disabled (as cloudron does these updates) - I have no plugins installed on it.@nicolas Also note, your theme is also effectively a plugin, so Theme Check is good for reviewing the quality of that:
I also like Simple History for auditing recent events:
-
Looking at the logs they sent, this is either a spoofed IP or someone found a way to proxy from your IP.
I'm assuming you don't run X11 on your VPS, hence it cannot be a browser doing that from the host OS.
While user agents can be spoofed easily, the one in the logs is an odd choice for blending in, hence likely the actual user agent from the Linux desktop user apparently bouncing through your system.
There are amplification attacks that change the low level packet source address of the payload and hence just make it look like your IP and thousands of others are attacking the one destination. Can't do much there.
Check your WP and Cloudron logs or post them here during the CPU spike to see if it's leaning on spoof traffic or exploited bounce traffic.
-
Looking at the logs they sent, this is either a spoofed IP or someone found a way to proxy from your IP.
I'm assuming you don't run X11 on your VPS, hence it cannot be a browser doing that from the host OS.
While user agents can be spoofed easily, the one in the logs is an odd choice for blending in, hence likely the actual user agent from the Linux desktop user apparently bouncing through your system.
There are amplification attacks that change the low level packet source address of the payload and hence just make it look like your IP and thousands of others are attacking the one destination. Can't do much there.
Check your WP and Cloudron logs or post them here during the CPU spike to see if it's leaning on spoof traffic or exploited bounce traffic.
I have to double check, but I did have yesterday a WordPress test instance I seldom use that took a lot of resource on the server and was contacting tons of website.
I just deleted it without inspecting further but it matches a DDOS or bruteforce behavior.
I probably still have the app as part of a backup, so should be able to revive it for research purpose.
-
I have to double check, but I did have yesterday a WordPress test instance I seldom use that took a lot of resource on the server and was contacting tons of website.
I just deleted it without inspecting further but it matches a DDOS or bruteforce behavior.
I probably still have the app as part of a backup, so should be able to revive it for research purpose.
-
@Nicolas and anyone with a Wordpress issue and not access to developers I recommend the following steps:
- If your site doesn't change much, it is usually a good idea to roll back to the oldest backup you have that is still what you want. You might be lucky and get to a point before any breach.
- Change all Admin user passwords immediately. Might not be that but it's a process of elimination. Most hacks I've seen keep getting back in because they have a compromised Admin account one way or another.
- Run updates for core and all plugins.
- Deactivate and remove all plugins that don't update.
- Run the free version of this: https://wordpress.org/plugins/gotmls/
- Run the free version of this: https://wordpress.org/plugins/wp-cerber/
- Run the free version of this: https://wordpress.org/plugins/wordfence/
- This plugin is old but still works for evaluating any plugin you are unsure of the code quality for, maybe run on a clone just to be safe: https://wordpress.org/plugins/plugin-inspector/
GOTMLS should catch anything and is deep and fast to do and see results, it's the one I've seen most managed Wordpress vendors use and recommend as 1st thing to do when contacting them. It used to scan the core for free but honestly, it's worth the donation for the quality, speed and updates they offer.
Cerber & Wordfence I've had mixed results and speed with but they can't do any harm, and are safe to leave installed and running on the free versions.
@marcusquinn Thanks for this. I deactivated even the add-ons that felt trustworthy and moved to a default theme (since that wordpress is really more of an archive than an active site). I also ran the scan you suggested and found that one add-on that I deactivated, and a theme, were both had scripts in them with known issues.
I wonder if a suggestion for the cloudron managed wordpress package is rate limiting external calls?
-
@marcusquinn Thanks for this. I deactivated even the add-ons that felt trustworthy and moved to a default theme (since that wordpress is really more of an archive than an active site). I also ran the scan you suggested and found that one add-on that I deactivated, and a theme, were both had scripts in them with known issues.
I wonder if a suggestion for the cloudron managed wordpress package is rate limiting external calls?

