If Redis is the worker, and the most recent update is:
"
Package Updates
wrote 6 days ago
last edited by
#118
[5.6.6]
Fix worker configuration
"
it is very much not fixed 
If Redis is the worker, and the most recent update is:
"
Package Updates
wrote 6 days ago
last edited by
#118
[5.6.6]
Fix worker configuration
"
it is very much not fixed 
Feb 04 22:15:18 RedisException: OOM command not allowed when used memory > 'maxmemory'. in /app/code/lib/private/Memcache/Redis.php:75
It just loops.
Feb 04 22:23:35 Stack trace:
Feb 04 22:23:35 #0 /app/code/lib/private/Memcache/Redis.php(75): Redis->setex()
Feb 04 22:23:35 #1 /app/code/lib/private/AppConfig.php(1373): OC\Memcache\Redis->set()
Feb 04 22:23:35 #2 /app/code/lib/private/AppConfig.php(284): OC\AppConfig->loadConfig()
Feb 04 22:23:35 #3 /app/code/lib/private/AppConfig.php(1832): OC\AppConfig->searchValues()
Feb 04 22:23:35 #4 /app/code/lib/private/Memcache/Factory.php(121): OC\AppConfig->getAppInstalledVersions()
Feb 04 22:23:35 #5 /app/code/lib/private/Memcache/Factory.php(160): OC\Memcache\Factory->getGlobalPrefix()
Feb 04 22:23:35 #6 /app/code/lib/private/Server.php(936): OC\Memcache\Factory->createLocking()
Feb 04 22:23:35 #7 /app/code/lib/private/AppFramework/Utility/SimpleContainer.php(169): OC\Server->OC\{closure}()
Feb 04 22:23:35 #8 /app/code/3rdparty/pimple/pimple/src/Pimple/Container.php(122): OC\AppFramework\Utility\SimpleContainer->OC\AppFramework\Utility\{closure}()
Feb 04 22:23:35 #9 /app/code/lib/private/AppFramework/Utility/SimpleContainer.php(136): Pimple\Container->offsetGet()
Feb 04 22:23:35 #10 /app/code/lib/private/ServerContainer.php(154): OC\AppFramework\Utility\SimpleContainer->query()
Feb 04 22:23:35 #11 /app/code/lib/private/AppFramework/Utility/SimpleContainer.php(45): OC\ServerContainer->query()
Feb 04 22:23:35 #12 /app/code/lib/private/Files/View.php(76): OC\AppFramework\Utility\SimpleContainer->get()
Feb 04 22:23:35 #13 /app/code/lib/private/Server.php(423): OC\Files\View->__construct()
Feb 04 22:23:35 #14 /app/code/lib/private/AppFramework/Utility/SimpleContainer.php(169): OC\Server->OC\{closure}()
Feb 04 22:23:35 #15 /app/code/3rdparty/pimple/pimple/src/Pimple/Container.php(122): OC\AppFramework\Utility\SimpleContainer->OC\AppFramework\Utility\{closure}()
Feb 04 22:23:35 #16 /app/code/lib/private/AppFramework/Utility/SimpleContainer.php(136): Pimple\Container->offsetGet()
Feb 04 22:23:35 #17 /app/code/lib/private/ServerContainer.php(154): OC\AppFramework\Utility\SimpleContainer->query()
Feb 04 22:23:35 #18 /app/code/lib/private/AppFramework/Utility/SimpleContainer.php(45): OC\ServerContainer->query()
Feb 04 22:23:35 #19 /app/code/lib/private/Server.php(1272): OC\AppFramework\Utility\SimpleContainer->get()
Feb 04 22:23:35 #20 /app/code/lib/base.php(635): OC\Server->boot()
Feb 04 22:23:35 #21 /app/code/lib/base.php(1192): OC::init()
Feb 04 22:23:35 #22 /app/code/console.php(31): require_once('...')
Feb 04 22:23:35 #23 /app/code/occ(33): require_once('...')
Feb 04 22:23:36 #24 {main}
Feb 04 22:23:36 box:tasks updating task 11284 with: {"percent":100,"message":"Done"}
Feb 04 22:23:36 box:tasks updating task 11284 with: {"completed":true,"result":null,"error":null,"percent":100}
Feb 04 22:23:36 box:tasks setCompleted - 11284: {"result":null,"error":null,"percent":100}
Feb 04 22:23:36 box:taskworker Task took 1.954 seconds
Why not use the excellent MiroTalk for this functionality?
Awesome! Would love to help with SSO. Any pointers where to start for hacking on that?
This appears to just be an SES wrapper?
why not use element/matrix? already packaged for cloudron.
Any update on this ? Where is the roadmap being set ? How can i help hack on this and send a PR?
Would it be possible to allow the policy to be set period ? That way sites with higher security requirements can meet federal / enterprise standards ?
@james Oh is this something that actually needs to be changed in the app json to make OIDC integration work at all?
I am attempting to get a brand new installation of VaultWarden working with Cloudron OIDC SSO.
I have already very carefully read over:
https://docs.cloudron.io/user-directory/#openid-connect
https://github.com/dani-garcia/vaultwarden/wiki/Enabling-SSO-support-using-OpenId-Connect
to produce the below (redacted) config.json..
https://my.knownelement.com/openid/.well-known/openid-configuration/
https://my.cloudron.example/.well-known/openid-configuration
https://my.cloudron.example/openid/.well-known/openid-configuration
SSO_AUTHORITY : the OpenID Connect Discovery endpoint of your SSO
Should not include the /.well-known/openid-configuration part and no trailing /
$SSO_AUTHORITY/.well-known/openid-configuration should return the a json document: https://openid.net/specs/openid-connect-discovery-1_0.html#ProviderConfigurationResponse
{
"domain": "https://passwords.knownelement.com",
"sends_allowed": true,
"incomplete_2fa_time_limit": 3,
"disable_icon_download": false,
"signups_allowed": false,
"signups_verify": false,
"signups_verify_resend_time": 3600,
"signups_verify_resend_limit": 6,
"invitations_allowed": false,
"emergency_access_allowed": true,
"email_change_allowed": false,
"password_iterations": 600000,
"password_hints_allowed": false,
"show_password_hint": false,
"admin_token": "heavily-redacted :) ",
"invitation_org_name": "KNEL Password Vault",
"ip_header": "X-Forwarded-For",
"icon_redirect_code": 302,
"icon_cache_ttl": 2592000,
"icon_cache_negttl": 259200,
"icon_download_timeout": 10,
"http_request_block_non_global_ips": true,
"disable_2fa_remember": false,
"authenticator_disable_time_drift": false,
"require_device_email": false,
"reload_templates": false,
"log_timestamp_format": "%Y-%m-%d %H:%M:%S.%3f",
"admin_session_lifetime": 20,
"increase_note_size_limit": false,
"dns_prefer_ipv6": false,
"sso_enabled": true,
"sso_only": true,
"sso_signups_match_email": true,
"sso_allow_unknown_email_verification": false,
"sso_client_id": "redacted",
"sso_client_secret": "redacted",
"sso_authority": "https://my.knownelement.com",
"sso_scopes": "openid email profile",
"sso_pkce": true,
"sso_callback_path": "https://passwords.knownelement.com/identity/connect/oidc-signin",
"sso_auth_only_not_session": true,
"sso_client_cache_expiration": 0,
"sso_debug_tokens": false,
"_enable_yubico": true,
"_enable_duo": true,
"_enable_smtp": true,
"use_sendmail": false,
"smtp_host": "mail",
"smtp_security": "off",
"smtp_port": 2525,
"smtp_from": "passwords.app@knownelement.com",
"smtp_from_name": "Vaultwarden",
"smtp_username": "passwords.app@knownelement.com",
"smtp_password": "redacted",
"smtp_auth_mechanism": "Plain",
"smtp_timeout": 15,
"smtp_embed_images": true,
"smtp_accept_invalid_certs": true,
"smtp_accept_invalid_hostnames": true,
"_enable_email_2fa": false,
"email_token_size": 6,
"email_expiration_time": 600,
"email_attempts_limit": 3,
"email_2fa_enforce_on_verified_invite": false,
"email_2fa_auto_fallback": false
}
I suppose I can increase logging to see if that helps.
Vaultwarden keeps asking for a master password, even though I've disabled that and set sso only.
As I have said, I'm deploying a FLO stack (with Cloudron at the core) into a startup that I'm building (as CIO/CTO). We have to be CMMC compliant. Making sure Cloudron works on a 100% compliant base system is the first milestone. While you may not consider them issues, they do need to be addressed to be compliant. That's "my problem". If a fully compliant base system causes an issue in Cloudron , that's "our problem". 
While you, and many Cloudron users may not care about CMMC/HIPPA/SOC/PCI compliance, I (and my board) do. I'm also building a small side business which will sell Cloudron as a service (pre setup/configured, all applications have admin password changed, admin passwords stored in Bitwarden) (the new Bitwarden SSO makes that possible without bootstrapping issues) and it will have CMMC/SOC/PCI/HIPPA compliance (at the higher tier).
As I mentioned, I'll be applying Ansible playbooks to bring the base system to 100% compliance.
I never said these were Cloudron issues. I said that I would be testing Cloudron on a 100% compliant base system and fixing anything that is broken. I don't expect any issues. Because, as you mentioned, these are all base system config tweaks.
Cloudron runs everything 100% in Docker images.
Where I suspect change may be needed, is at the Cloudron container level when I start scanning everything with Trivy.
Do you use hardened Docker base images?
I have uploaded it here: https://staticbits.reachableceo.com/CloudronWazuhReport-2025-30-12.csv
Is there a way to upload a text file to the forum? I have a csv of the wazuh report exported.
I’ll see about getting the full list exported to a text file and posted.
This is the out of the box results on a fully patched/updated Cloudron per Wazuh (as of about 90 seconds ago).
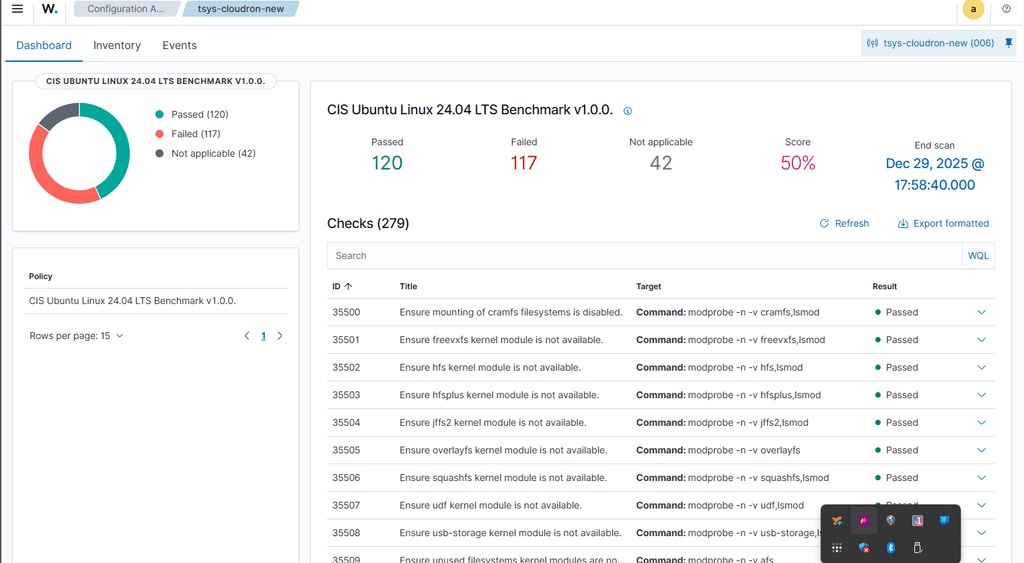
I will be deploying a test instance of Cloudron on a VM with a set of CIS/NIST ansible playbooks to get the node to 100% compliance and see if anything breaks.
Any possibility of getting NTP configuration (via API/GUI) into Cloudron 10 roadmap?
Oh also, ideally, syslog configuration settings should be possible in GUI/API. I believe that anything done in the GUI is also available via API? I think the GUI uses the API behind the scenes?
Any update on logging configuration? Can we get this on the roadmap for Cloudron 10?
Would love to see more enterprise/compliance focused features in Cloudron 10. Happy to help implement. I've been going through the Cloudron github in anticipation of sending pull requests.
Right now I'm working on configuring all CIS benchmarks and passing CMMC with Cloudron, so that's taken time away from my packaging of ~50 new applications for Cloudron (I can't use the applications in an un-certified environment). I'll spin up a dedicated topic on Ansible/CIS/CMMC compliance shortly.
I am working on packaging up a very large number of applications for Cloudron this week/by end of January (finally) so I'll post updates in that topic soon.
Hello everyone. I've been busy with the physical facility buildout of my business. That has now wrapped up (I have one more weekend of punchlist work). Anyway, I am now packaging up the things from my list! Using a combination of claud/gemini.
See the git repo here : https://git.knownelement.com/KNEL/KNELProductionContainers/src/branch/integration/