Here we go fellow Cloudron enthusiasts!
Just wanted to share my experience with NetBird, and man, it's been quite a journey! 
Zerotier:
I use to have Zerotier installed, but it had a BIG learning curve (for me) when it comes to apply the Firewall rules at the Zerotier web-ui (controller-interface).
The whole idea with Zerotier worked well for me a couple of years, but i did not like the fact that clients connecting all together, had full acces all together, in both ways.
Sure, you could make different networks for different clients, but there's gonna be that time when you need some of them together for certain things.
Netmaker:
So i tried Netmaker for that particular reason, worked well for my needs.
But after a few updates, it had problems connecting the clients and i had to start all over again, no fun when you have SMB/NFS and so on setup for particular clients!!
Netbird 
Finally i stumbled across Netbird and thought.... let's give that a go, since it looked promising.
Like Netmaker, Netbird installs the coordination server on a cloud instance. This is the air traffic controller. Netmaker’s setup was easy, but with Netbird ’s clear installation instructions, it was even easier to setup.
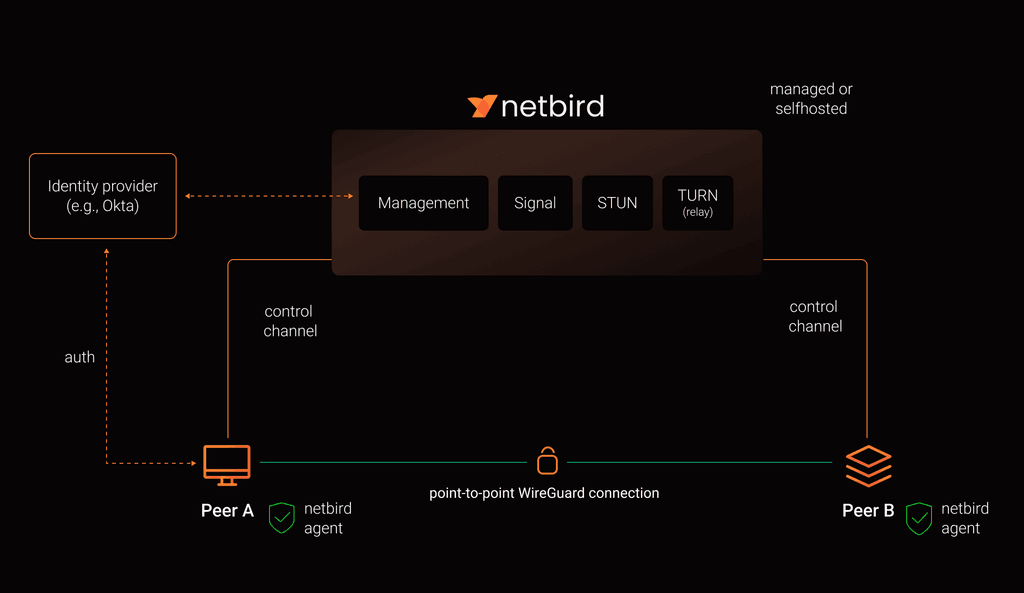
The initial deployment of NetBird was done on a:
Ubuntu 20.04.6 LTS (Hetzner-CX11)
1 VCPU
2GB RAM
20GB DISK
Pricing per month: €3.98/mo (as of feb-2024)
The VM should be publicly accessible on TCP ports 80, 443, 33073 and 10000; and UDP ports: 3478, 49152-65535.
Netbird-installation:
Install is done through the installer script (shoutout to the Netbird team for that ).
).
source --> https://docs.netbird.io/selfhosted/selfhosted-quickstart#quick-self-hosting-with-zitadel-id-p
Be aware that this is an "single-line setup script" with Zitadel
Actually i installed Netbird alongside with my existing Keycloak installation, and it was somewhat more advanced to setup.
source --> https://docs.netbird.io/selfhosted/selfhosted-guide
If anyone is really interested about the Keycloak integration with Netbird and how i did it? Just throw your questions here and i shall do my best to answer them.
I thought that my review otherwise would going to be to long, if i would explain that whole setup process with Keycloak.
for anyone interested, the documentation here is a good guide for succesfully installing it.
I use NetBird for:
- SNMP monitoring (where i only allow 1 direct connetion from server to client on port:161 UDP)
- Proxying apps that are installed on my homelab, they Proxy there way out through another VPS, also connected with Netbird.
- SMB/NFS for a Cloudron instance deployed on Hetzner (for example), that connects to my homelab and stores it's backups there through Netbird.
- Off-site backups from my Homelab to another location.
- Connecting to applications through mobile (Android) that are not publicly available.
and other things i may forget to mention here.....
Network routes:
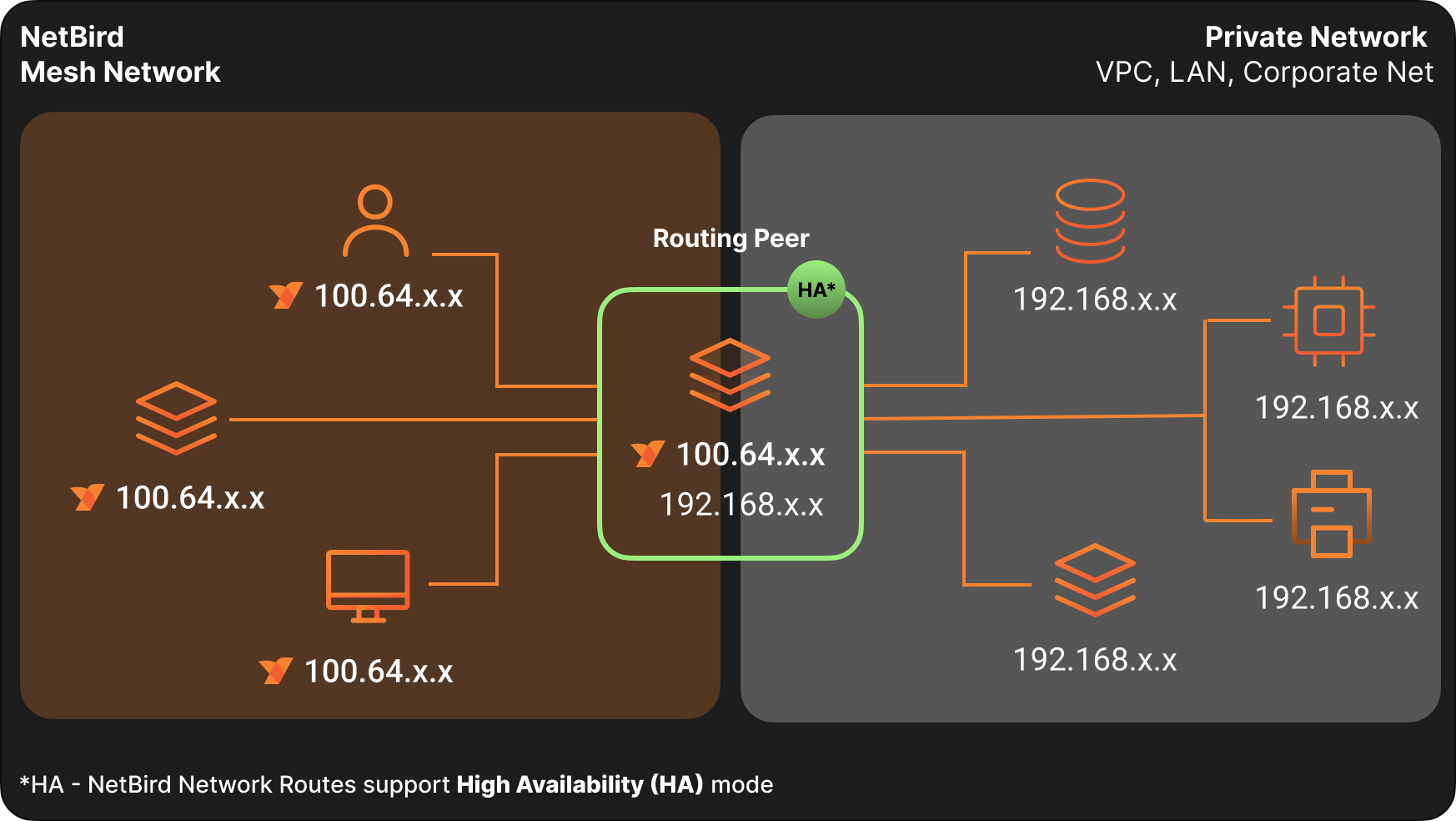
Also one really big thing were Netbird shines, is it's capability to use "Network routes".
source-->https://docs.netbird.io/how-to/routing-traffic-to-private-networks
Netbird supports egress servers — called network routes in Netbird — that allow you to access devices that don’t have the Netbird client on them, as if you and your computer were transported to wherever the egress server is.
At one time i had an VM at another location where it refused to install the Netbird client on 
But "Network routing" in Netbird helped me connecting the desired VM anyway, without the Netbird client installed on there.
Another situation i had is that where a Raspbery-pi acting as a dumb energy monitor, without the possibility of opening firewall ports on there, was now acting as my Network Route to all the devices listed on that network. Plus the other network was like 200 miles away from here, and working like it was all locally.
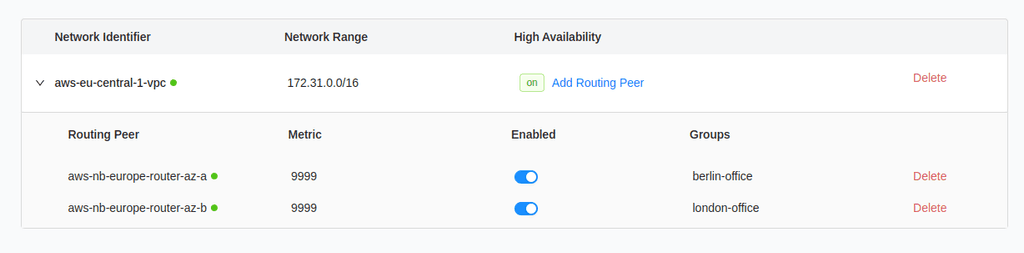
I also made that network route HA (High Availability) and did setup the appropriate ACL rules on it, so the whole network is not exposed to every client assigned to it.
Access Control (Firewall):
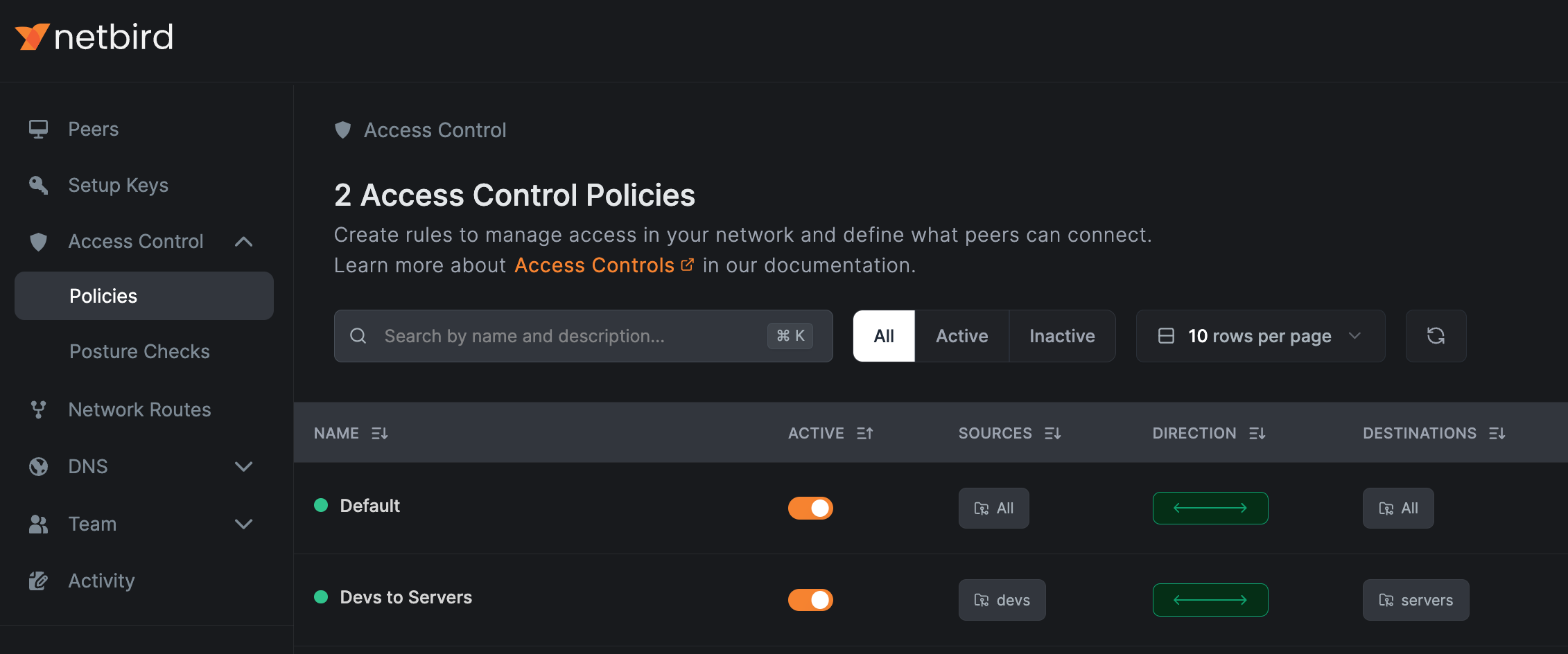
This is one of the main choices i did go for Netbird. Because connecting clients all together in a private network over the internet works great.
Still, if one client could get hacked, this has now full access to al private clients on that particular private network. Included access to all services like SMB/NFS and so on.
So what i did here is adding clients to groups and from there build my network in that way, only particular clients have particular access with the help of ACL rules on the Netbird main page.
So one example here;
i have a snmp monitoring (master) server and all clients reporting back to that server.
This all happens on port:161 UDP.
Now for the ACL rule i have setup a one way connection from the snmp server to my clients on port 161 UDP.
This way the snmp master server is allowed to connect to the clients for the status reports, but clients could never make an connection back to the master snmp server.
And also the clients together in the same network, can not see or ping each other, because there not allowed to, based on the ACL rules ️
️
Final word:
Overal Netbird is a game-changer for someone like me who doesn't want to spend hours on configurations for setups.
Also in terms of security, simplicity, and a bit of tech exploration, it's been a solid and steady choice for the last year.
Sure, i had one problem after an update of Netbird in the past, but when i noted this on their Github page, they were very helpful and motivated to catch the cause and solve that in a future update.
Like i said, this is probably one of the thirst ever review that i wrote in my whole tech savy life, but i hope it helps a bit to give you guys my experience about using Netbird....
 🥳
🥳




 and all of you the best wishes for 2023.
and all of you the best wishes for 2023.