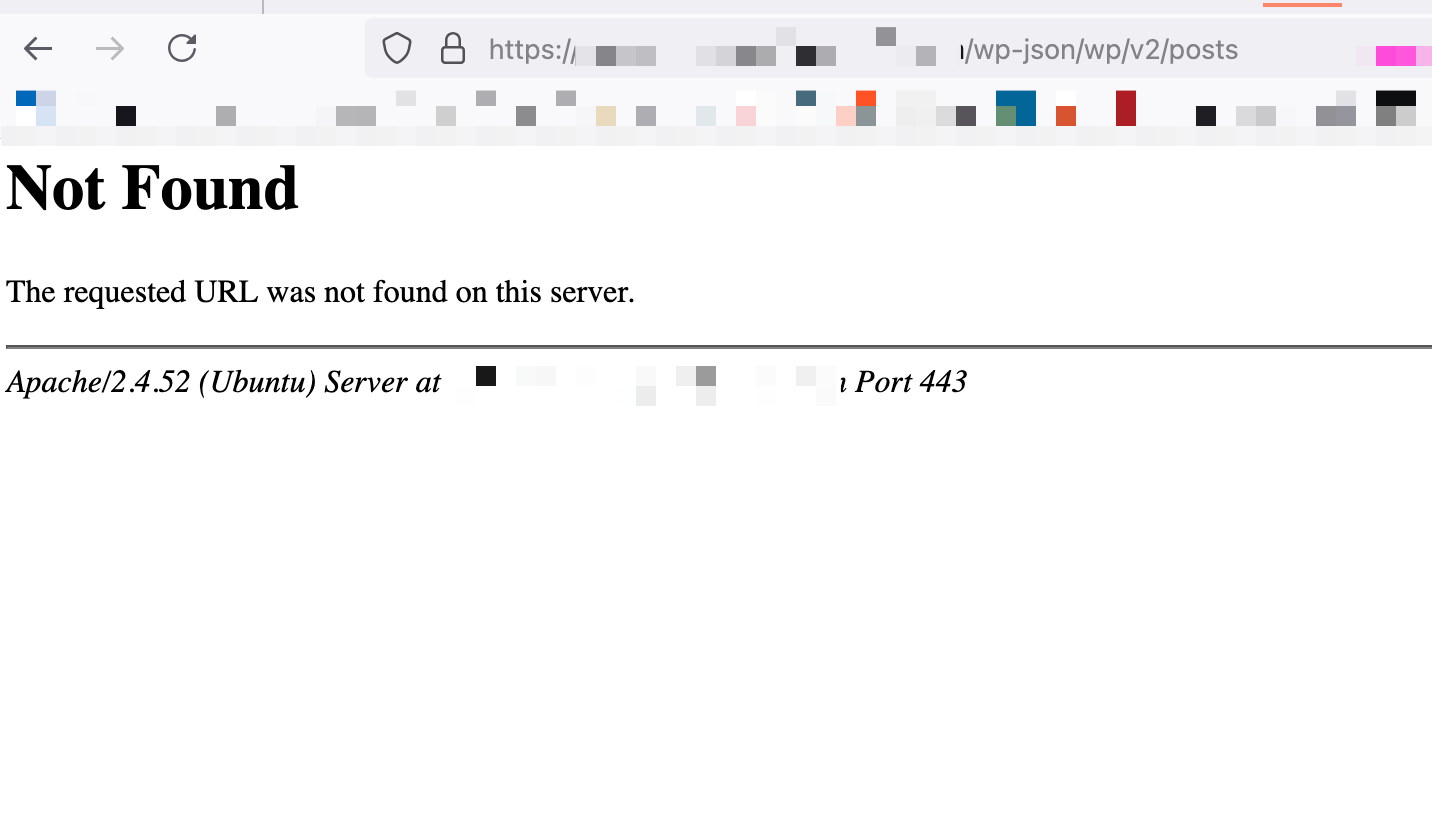
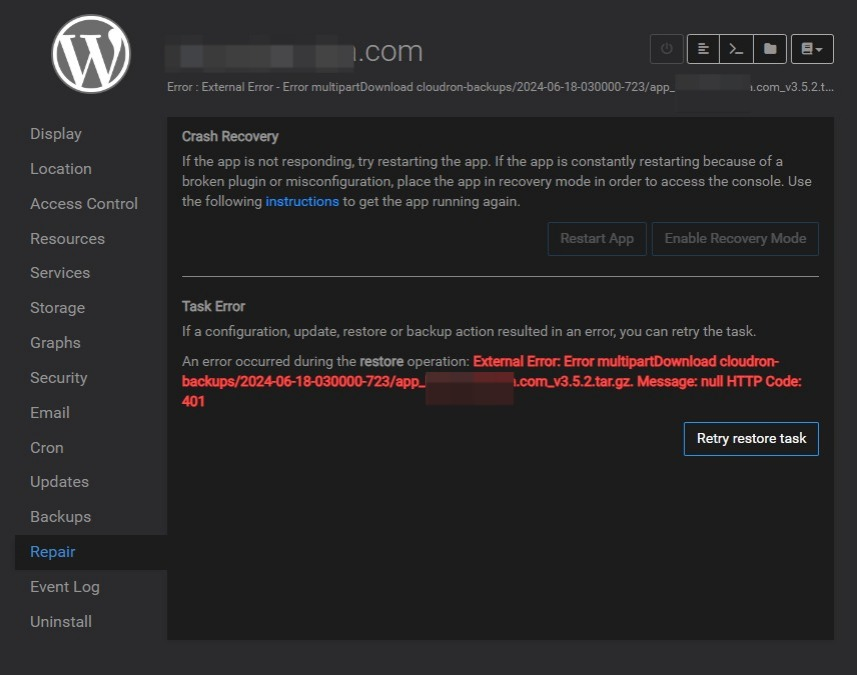
WordPress (Developer)
221
Topics
1.8k
Posts
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
FPDF Install
Moved -
-
-
-
-
... public folder?
Solved